ClickFix protection
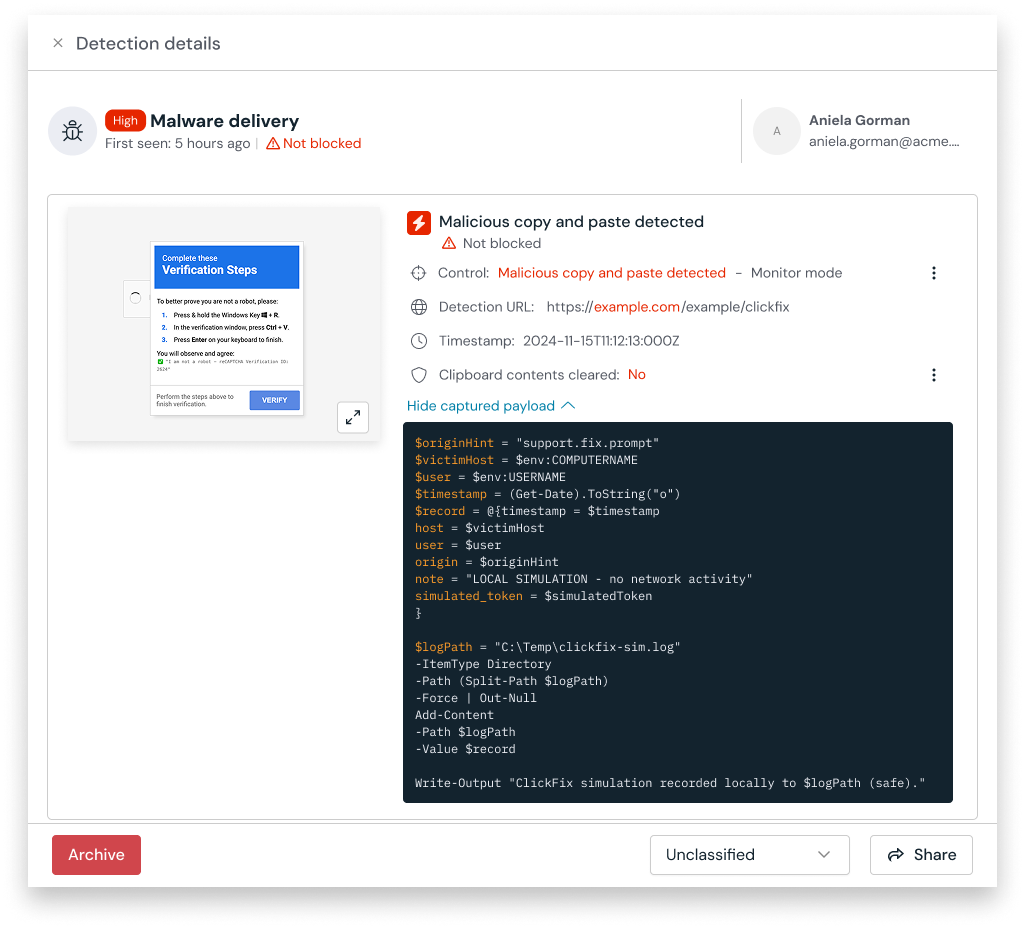
ClickFix attacks are one of the fastest-growing threats, tricking users into copying malicious code from a webpage and running it locally. This technique bypasses traditional EDR, email gateways, and network filters, leading directly to ransomware and data theft. Push stops this attack at the source, in the browser, by detecting and blocking the malicious behavior before the user can ever paste the code.
Stop ClickFix-style attacks before they become a breach
Traditional security tools are blind to malicious copy and paste attacks because the attack exploits a gap between the browser and the endpoint. EDR only sees the payload after it runs, and network tools see only part of the picture.

Discover lures at the source
Push inspects page behavior to identify ClickFix attacks as they happen. By inspecting the page, its structure, and how the user interacts with it, Push can detect and block these in-browser threats in real time. This deep, TTP-based inspection spots the trap even on novel pages that are built to bypass traditional web filters and blocklists.

Block the malicious action
When Push detects a malicious script, it intercepts the user's action and blocks the code from being copied to the clipboard. The user is protected, the attack is stopped, and no malicious code ever reaches the endpoint. Unlike broad DLP tools, this action is surgical, targeting only malicious behavior without disrupting normal work.

Accelerate ClickFix investigations
When an attack happens, knowing what the user saw or did is critical. Push provides rich browser session data for rapid investigation and containment. Security teams get detailed telemetry on which users were targeted, what lure they were served, and when the block occurred. This enables defenders to reconstruct what happened and respond quickly, even when other tools miss the activity entirely.