One key question we get is "we're already monitoring network and web traffic, so why do we need to be in the browser too?". Here are the key differences.
One key question we get is "we're already monitoring network and web traffic, so why do we need to be in the browser too?". Here are the key differences.
Defense used to start at the network perimeter
If you've been working in security for any length of time, you know where defense starts: the network. Long before cloud-first or SaaS-first became default, the perimeter was where defenders had leverage: visibility, enforcement, and control over traffic moving in and out of the organization.
That mental model hasn’t disappeared. Secure Web Gateways, Cloud Access Security Brokers, and the converged Security Service Edge architecture exist because the problem they solve is still real. Organizations generate an enormous volume of web traffic, and someone has to monitor it, filter it, and enforce policy at scale. These tools sit inline, log metadata, apply categorization, and block what’s already known to be dangerous. Without them, the environment quickly becomes unmanageable and extremely difficult to secure.
They are very good at what they were designed to do: securing the wire. But what happens over the wire is not the full picture.
Traffic isn't the whole picture anymore
A significant amount of activity happens locally, inside the browser, beyond the visibility of network controls. Modern webpages are effectively complicated web apps that are rendered client-side via JavaScript — and not everything that happens on the page is traffic-generating.
That distinction matters more than it used to. Authentication, data access, administrative actions, almost all of it now happens inside a browser tab. As a result, the browser has become a central point of both productivity and risk.
Network tools still see the pipeline of traffic moving back and forth. But attackers have adapted to operate within that pipeline rather than around it. They don’t need to break the connection or trigger obvious anomalies. They target the content rendered inside the browser and the user interacting with it.
That leaves security teams with noisy traffic visibility and very little insight into the actual attack unfolding inside the browser session.
Traffic visibility vs. in-browser context
The modern attacker's playbook is built on a simple idea: stay inside the network’s line of sight without triggering detections or enforcement. Containing operations to the browser layer provides attackers with an easy bypass of many traditional network controls without ever needing to break or evade them outright.
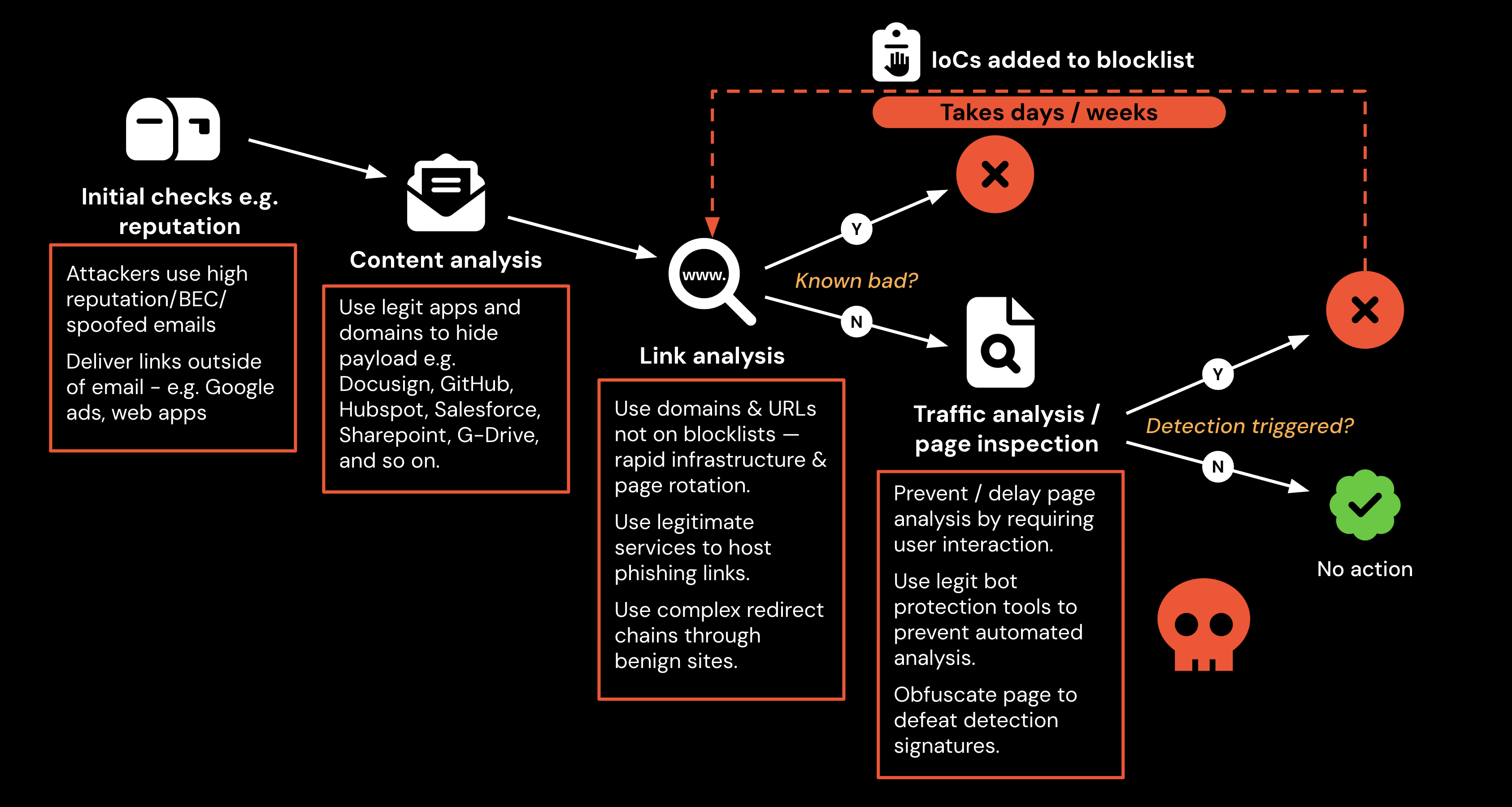
They do this by staying ahead of known-bad detection models, constantly rotating domains and URLs, using anti-analysis techniques, and delivering phishing lures through channels that bypass traditional network ingress points like the email gateway (like social media or SMS). In many cases, the link is never evaluated by perimeter controls at all.
This creates a fundamental visibility gap. Network security tools can see a request going to a legitimate-looking destination, but they can’t observe what happens once the page executes client-side in the browser. Malicious scripts and phishing elements often don’t appear until after the page loads and a user interacts with it, leaving nothing obviously known-bad for network controls to detect.
Blocklists don’t help much here either. Domains rotate constantly, and the window between a phishing site going live and being categorized as malicious is more than enough time for an attacker to succeed. Until that happens, the traffic appears benign and the user is free to interact with the page. And to make matters worse, attackers are leveraging detection evasion techniques designed to frustrate these detections — meaning most bad pages aren't spotted until it's way too late.
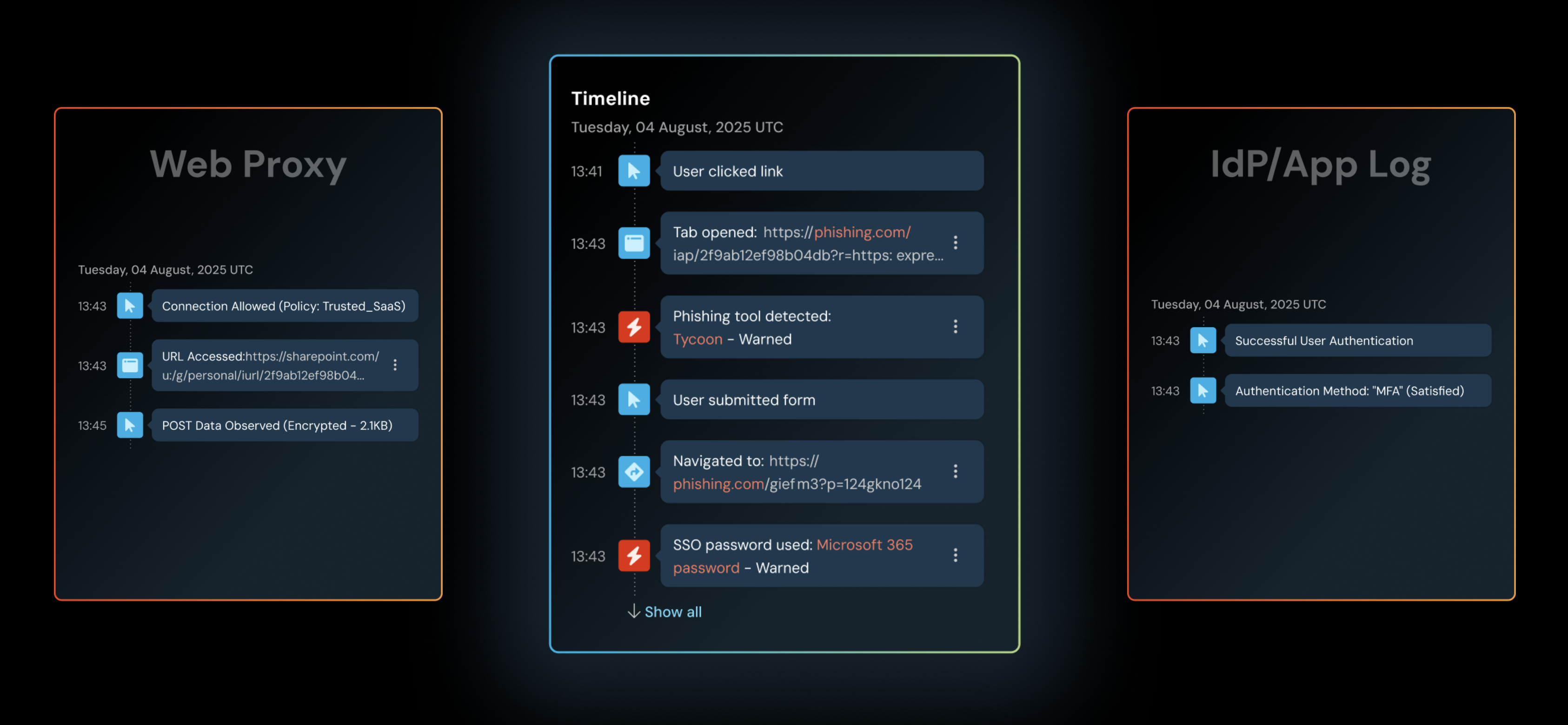
Consider attacker-in-the-middle phishing. From the proxy’s perspective, everything looks clean: user → reputable domain → “standard” web traffic. The phishing infrastructure is often hidden behind redirects or conditional logic designed to screen out proxies and scanners. Inside the browser session, however, credentials are intercepted, session tokens are harvested, and MFA is bypassed in real time.
For modern threat groups, these obscured attack vectors lead directly to initial access and account takeover. The network is no longer the control point where the most consequential attacks can be reliably stopped.
Browser telemetry is key to detecting and blocking malicious content in real-time, rather than relying on blocklists using known-bad indicators like domains and IPs that go out of date as quickly as new entries appear.
What you see with traffic analysis | What you can see with browser telemetry |
|---|---|
HTTP request/response bodies | DOM structure fingerprints |
URLs and headers | User interaction metadata |
Cookie values in transit | Cookie names and attributes |
Static JS code | Script execution patterns and dynamic JS analysis |
Securing the browser session is key to stopping modern threats
If the browser is where users actually work, and where attackers actually operate, then that’s the layer that defenders need to understand and control.
Modern web-based attacks don’t succeed because traffic goes uninspected. They succeed because network inspection can’t follow the interaction far enough. Traffic shows where data went, not what the user actually saw or did, and in today’s attacks, that distinction matters.
To stop these threats, you have to see what the user is actually interacting with. Things like what scripts are loading, how the DOM is being manipulated, or whether the login form a user is using is legitimate or being proxied. Those are page-level signals, and they only exist inside the browser tab.
That same shift applies to control. Destination-based blocking breaks down when the destination itself appears legitimate. Effective intervention requires decisions based on behavior as it unfolds so teams can stop risky or malicious activity that would compromise an account.
And visibility can’t stop at centrally managed applications. Shadow SaaS breaks any assumption that access patterns are uniform or fully governed by the IdP. Local accounts, duplicate identities, and password-only logins don’t show up clearly in network telemetry, but they materially expand the attack surface. Seeing every login, across every app, directly from the browser is the only way to build an accurate picture of who has access to what.
Push provides the missing context for network security
At this point, the gap should be clear. Network security gives you strong control over traffic, but very little insight into what actually happens once that traffic lands in a user’s browser.
This is where Push can help.
The Push browser agent extends monitoring into the browser itself, providing the visibility and control that perimeter-based tools can’t deliver. It doesn’t replace SSE, SWG, or CASB. Those tools remain the right way to manage traffic and enforce policy at the edge. Push complements them by operating in the one place they can’t: inside the live browser session.
Push does this by deploying a browser-native agent, similar in spirit to how EDR works at the host level. That agent gives defenders direct insight into what the network can’t see like the page being rendered, how the user is interacting with it, and the attack techniques that play out entirely within the tab.
With Push deployed, teams gain:
Real-time, in-browser threat detection: Detect and stop attacks like AiTM phishing and session hijacking based on what’s actually happening in the browser. Instead of relying on blocklists or downstream signals, Push identifies attacker behavior as it unfolds and can intervene before credentials or session tokens are stolen.
Complete visibility into SaaS access: Build a true inventory of user identities and authentication methods across every application in use, including shadow SaaS. Push fills the gaps left by network and IdP logs, giving teams a real picture of where access exists and how it’s being granted.
Streamlined hardening at the point of access: Use the browser as a control point to enforce secure login behavior everywhere it matters. Mandate MFA, steer users toward SSO, and block risky credentials on unmanaged apps, shifting from reactive cleanup to continuous, preventative hardening.
The result is a unified model and real defense in depth. Network tools secure the pipeline, and Push secures the user moving through it.
Want to learn more about Push? Check out our latest product overview, visit our demo library, or book some time with one of our team for a live demo.
