One of the key questions we often hear is, "We've already got CSPM/CNAPP, so why do we need to be in the browser too?" Well, here's the answer!
One of the key questions we often hear is, "We've already got CSPM/CNAPP, so why do we need to be in the browser too?" Well, here's the answer!
Cloud security tools ensure secure configurations
If you’re a cloud security architect, you probably don’t think in terms of firewalls and perimeters anymore. You think in control planes. Your job isn’t protecting a box or a subnet; it’s governing a sprawling web of IAM roles, service principals, APIs, and permissions that exist mostly as configuration and code. In this world, the boundary isn’t physical or even networked, it’s defined entirely by how your environment is configured.
The way most teams approached that problem was pragmatic. As cloud environments scaled, it became impossible to secure it by inspection or tribal knowledge. Cloud Security Posture Management tools and, later, Cloud Native Application Protection Platforms emerged to solve a very real problem: visibility and control over cloud configuration at scale. They gave teams a way to continuously assess infrastructure, track misconfigurations, and understand risk across accounts, regions, and services without drowning in raw provider logs.
That capability is important. Without it, cloud security simply doesn’t function.
CSPM and CNAPP answer the question of “is my cloud environment configured securely?”. They tell you whether an IAM role is too permissive, whether a resource is exposed, or whether a policy violates best practice. They tell you when a user or account is trying to do something they shouldn’t.
What they don’t answer is a different, increasingly important question: “What happens when attacker behavior is indistinguishable from legitimate user behavior?”
But they can’t stop “legitimate” actions
The gap (or lack of) between legitimate user behavior and malicious abuse is becoming more relevant as cloud breaches change shape.
In many of today’s incidents, attackers aren’t exploiting misconfigurations or abusing the cloud control plane directly. They’re compromising users. Once an authentication has occurred through illegitimate means, whether phishing, session hijacking, or token theft, the attacker operates entirely within an approved session.
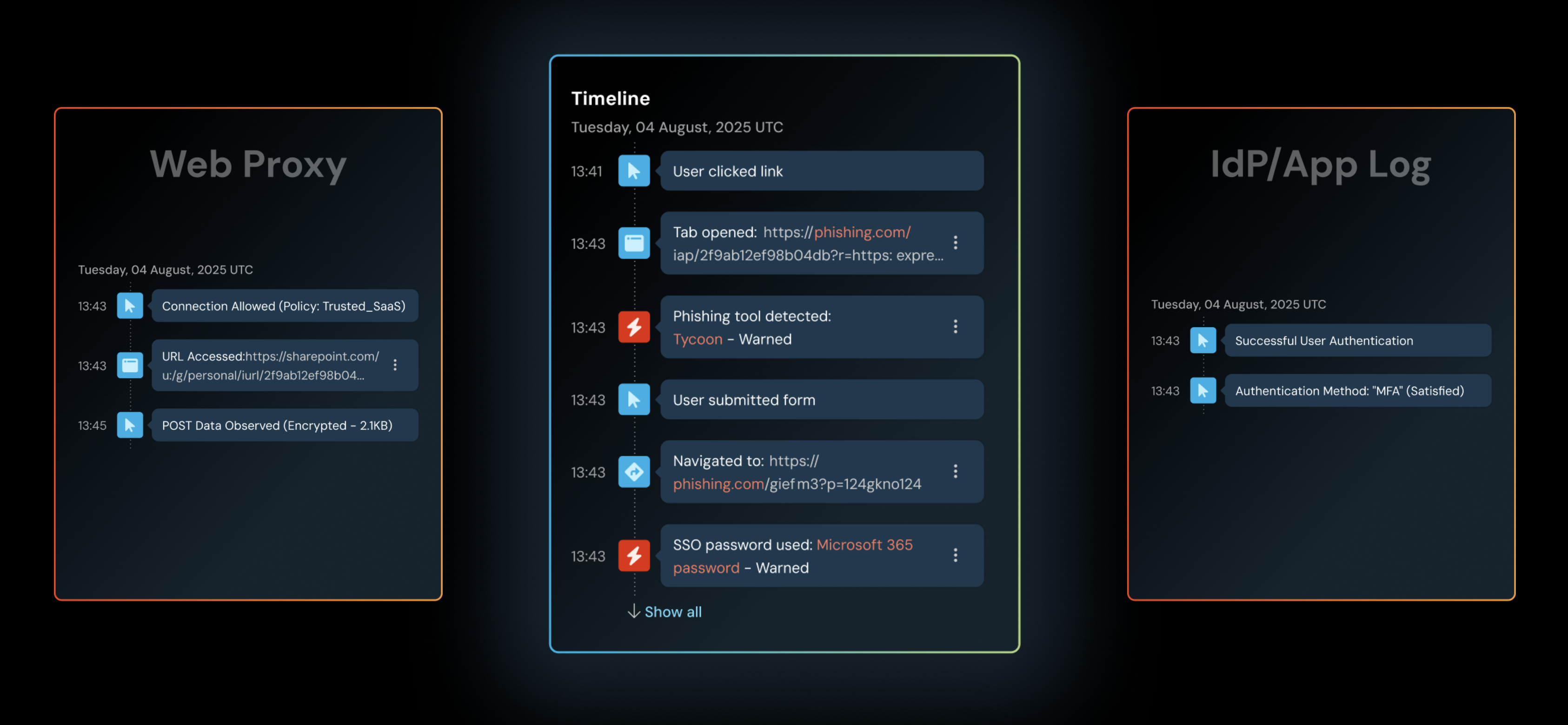
From the perspective of cloud security tooling, very little looks wrong. The identity is valid. The access patterns appear expected. The infrastructure remains correctly configured. As long as the attacker operates within the bounds of what looks “normal”, no alarms are triggered. Meanwhile, sensitive actions are carried out through the browser, using the same interfaces and workflows as a real user.
The gap between the IdP and the final API call — the “missing middle” in your security stack
The browser session sits outside the telemetry and control model of infrastructure-focused cloud security tools. We call this the "missing middle." It’s the space between the IdP login and the final cloud API call.
In theory, you could try to close the gap by stitching together logs from every SaaS application in your environment. In practice, anyone who’s attempted this knows how quickly it falls apart.
Each integration is brittle and expensive to maintain, and many applications don’t expose the level of telemetry you actually need, even if you’re willing to fork out for the top Security++ product tier. When you’re dealing with hundreds of apps per enterprise, each with their own configuration complexity, there’s a good chance that your solution focused on “core” cloud apps doesn’t actually have visibility of the full attack surface.
When logs do exist, they rarely show what you actually need. To a CSPM or CNAPP, it looks like an authorized user doing authorized things. A file was accessed or a setting was changed. What those tools can’t see is that the browser session itself was being manipulated in real time.
For modern, cloud-native threat groups, this lack of session-level visibility is their greatest advantage. They bypass the strong configuration and identity controls you’ve already implemented by simply stepping into the authorized stream. And by the time infrastructure-level signals suggest something is wrong, the attacker has already accomplished what they came for.
Secure everything, still lose
At some point, this forces a hard realization: you can do everything “right” at the cloud and identity layers and still lose.
You can lock down infrastructure-as-code, tighten IAM policies, enforce conditional access, and pass every posture check you care about. But none of that changes where access actually happens. When users work in cloud services, they do it through a browser. And once a session is established, that browser session becomes the real control plane.
That’s the shift cloud security teams are running into. The problem isn’t that CSPM or CNAPP failed, it’s that they can’t see the full picture. Bridging the missing middle means treating the browser session itself as something you can inspect and defend.
Why moving detection and response to the browser is the solution
First, detection has to move into the browser. Modern cloud attacks don’t announce themselves with known indicators or suspicious IPs; it’s all about behavior. A phishing kit rendering inside a login page. A session token being silently exfiltrated. A user interacting with a page that looks legitimate but isn’t. You only see those signals by inspecting the page, the scripts, and the user’s interaction, in real time, inside the tab, before any cloud API ever gets touched.
Second, posture can’t stop at the IdP or cloud configuration. It’s not enough to enforce MFA and SSO at a handful of centrally managed apps and assume the rest of the estate follows suit. Shadow SaaS breaks that assumption immediately. Local accounts, duplicate identities, and MFA gaps undermine cloud access controls, even when your AWS or Azure configuration is otherwise airtight. If a sensitive app allows password-only access, that weakness propagates straight back into your cloud environment.
Finally, when something does go wrong, teams need more than a login timestamp and an IP address. They need to know what the user actually saw and did. Click-by-click browser session data is what allows responders to understand intent, scope impact accurately, and determine whether a session was abused or simply used.
Visibility into the browser session holds the answers
If the browser session is where cloud access actually happens, then treating it as a black box is no longer viable.
This is where Push Security fits. Push is designed to cover the missing middle, not by replacing your existing cloud security stack, but by extending it into the one place it can’t reach on its own: the live browser session.
CSPM and CNAPP remain the right tools for securing cloud configuration and infrastructure. They tell you whether IAM policies are sane, resources are exposed, and guardrails are in place. Push addresses a different problem. It focuses on what happens once access is granted, when identity moves from configuration into motion.
Push does this by deploying a browser-native agent, like EDR operates at the host level. That agent gives defenders direct visibility into the application session itself like the page structure being rendered, the user’s interaction with it, and the behaviors attackers rely on when they hijack sessions in real time.
That visibility changes how cloud access can be defended.
Real-time detection in the browser: Detect in-browser attacker techniques as they happen, left of boom. Phishing kits rendering inside login flows, session tokens being intercepted, credential submission into lookalike pages — Push observes these behaviors directly and can block them before any cloud API is touched or a console is reached.
Complete visibility into cloud access paths: Build an accurate inventory of how users are actually accessing cloud services. Push surfaces every application in use, including shadow SaaS, and shows which accounts are local, duplicated, missing MFA, or bypassing SSO — crucial visibility that falls between the cracks of application and identity provider.
Active hardening at the point of access: Enforce secure login behavior across the entire application surface, not just centrally managed apps. Push can steer users toward using MFA and SSO and block risky credentials on unmanaged tools, closing identity gaps before they’re exploited.
Session-level context for rapid response: When something does go wrong, Push provides the missing ground truth. Instead of stitching together partial logs or relying on brittle app-level integrations, responders can see exactly what the user saw and did in the browser (from context generated directly from the browser session itself) making it possible to understand intent, assess scope accurately, and contain a compromised session quickly.
Want to learn more about Push? Check out our latest product overview, visit our demo library, or book some time with one of our team for a live demo.
