Our latest development sprint focused on extending the power of the Push browser agent to detect and prevent identity attacks that evade traditional security controls. We’ve also enhanced our popular app banners feature, and added more API and webhooks options for managing Push programmatically.
Our latest development sprint focused on extending the power of the Push browser agent to detect and prevent identity attacks that evade traditional security controls. We’ve also enhanced our popular app banners feature, and added more API and webhooks options for managing Push programmatically.
What’s new this month:
SSO password protection
Phishing tool detection
Session token theft detection
URL blocking
Require a reason for app usage
Expanded API and webhooks options
Prevent SSO password reuse
Instead of trying to detect phishing websites and domains that constantly change, Push can now detect (and block!) SSO password reuse based on directly observing user behavior in the browser.
Our SSO password protection feature detects and blocks when a user enters their identity provider password on a webpage that does not belong to the IdP (e.g. Okta, Google Workspace, Microsoft 365, etc.)
You can choose to warn or block SSO password reuse and customize the message that end-users see.
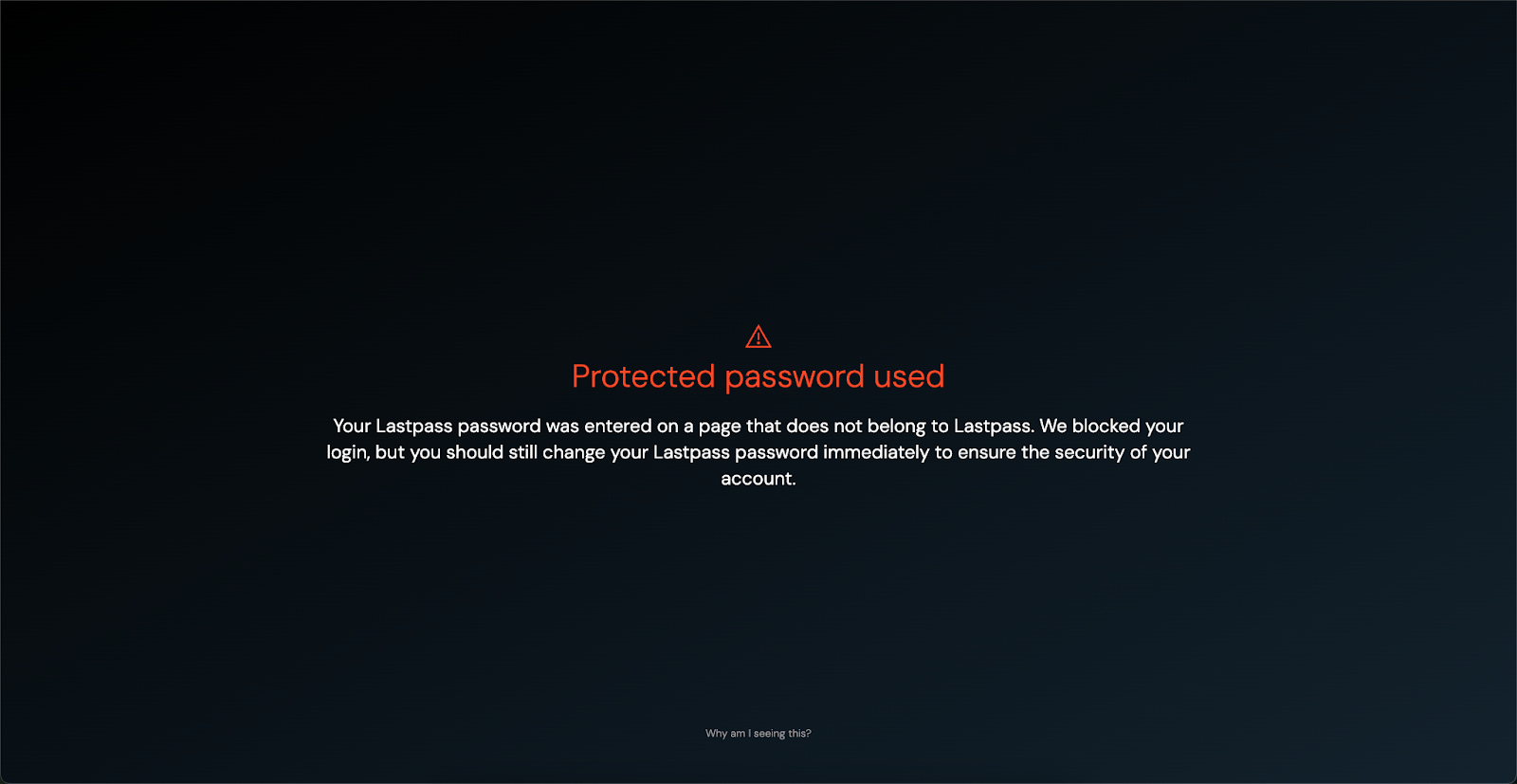
Detect Adversary-in-the-Middle phishing toolkits
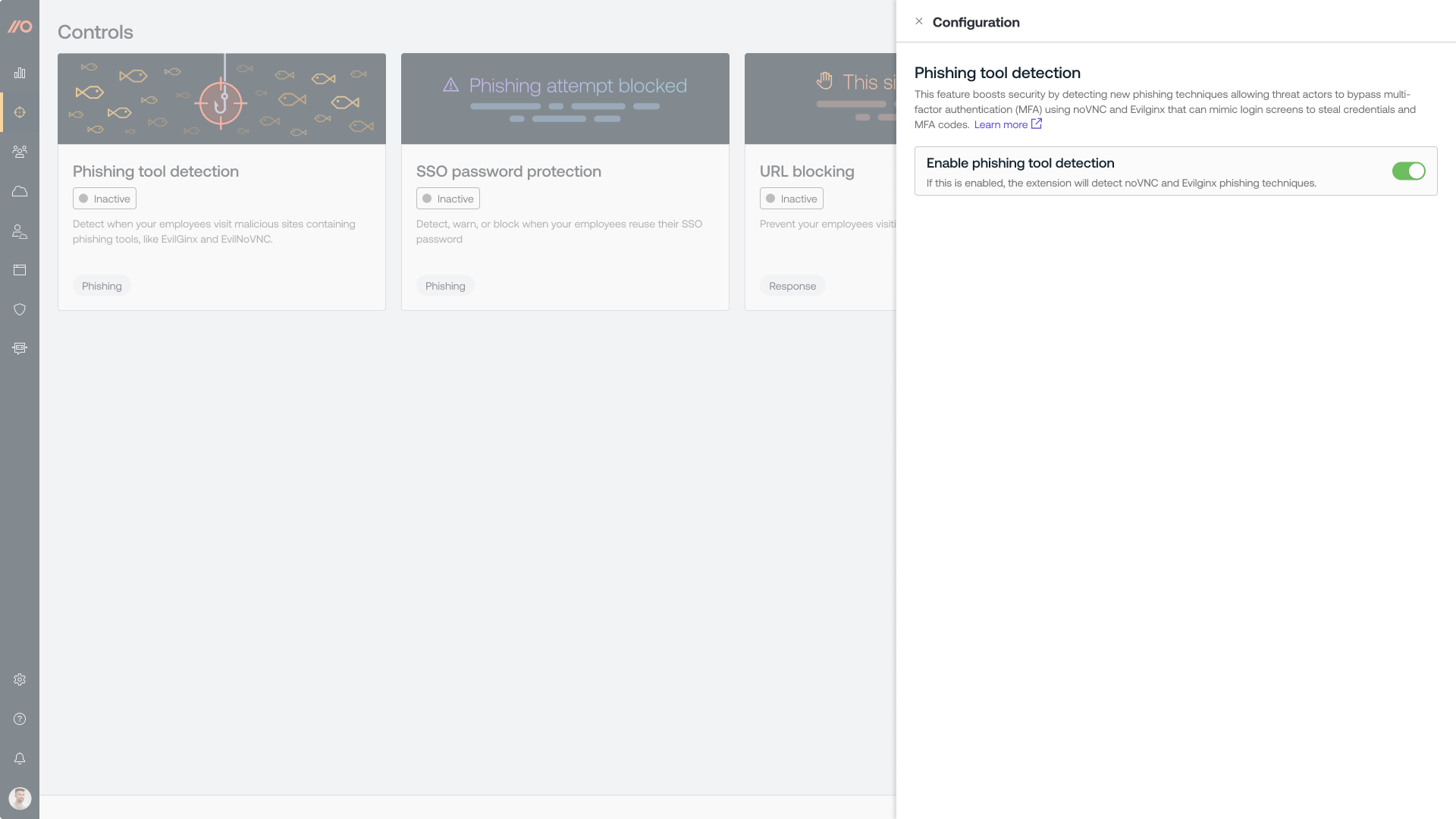
The Push browser agent can now detect when employees visit websites that are using phishing toolkits such as EvilNoVNC and Evilginx. These tools can mimic legitimate login screens in order to steal credentials and bypass MFA.
Send detections to your SIEM or similar monitoring tool and add malicious sites to a blocklist in Push.
Identify session token theft
You can now use the Push browser agent to inject a unique marker to the user agent string of sessions that occur in browsers enrolled in Push. By analyzing logs from your identity provider (e.g. Okta, Microsoft 365, etc.) or other app, you can use the marker to help you find suspicious activity that indicates a stolen session cookie in use.
Detecting session hijacking is extremely difficult when relying on device-based monitoring using EDR and network traffic. But by giving legitimate sessions a stamp of approval using the Push browser agent, you can easily identify access to apps from untrusted devices.
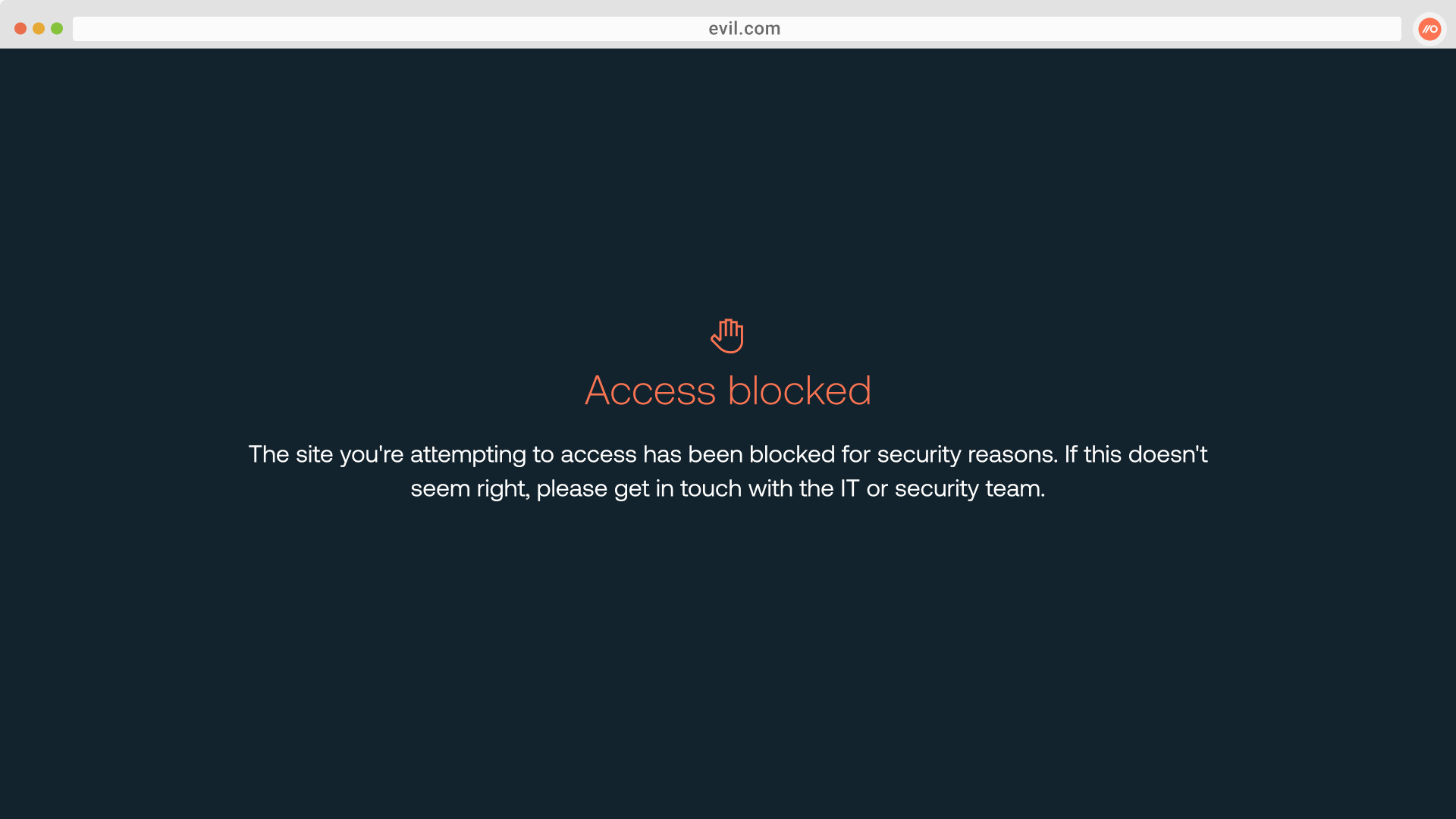
Configure a custom blocklist of URLs
Prevent employees from visiting malicious sites you detect by configuring a custom blocklist of URLs in Push using the URL blocking feature. You can customize the message shown to end-users by adding your own links and instructions. Use Push’s REST API to programmatically manage URL blocking as part of responding to a phishing incident.
You can use this alongside other Push features like phishing tool detection to block access to known-bad sites you find.
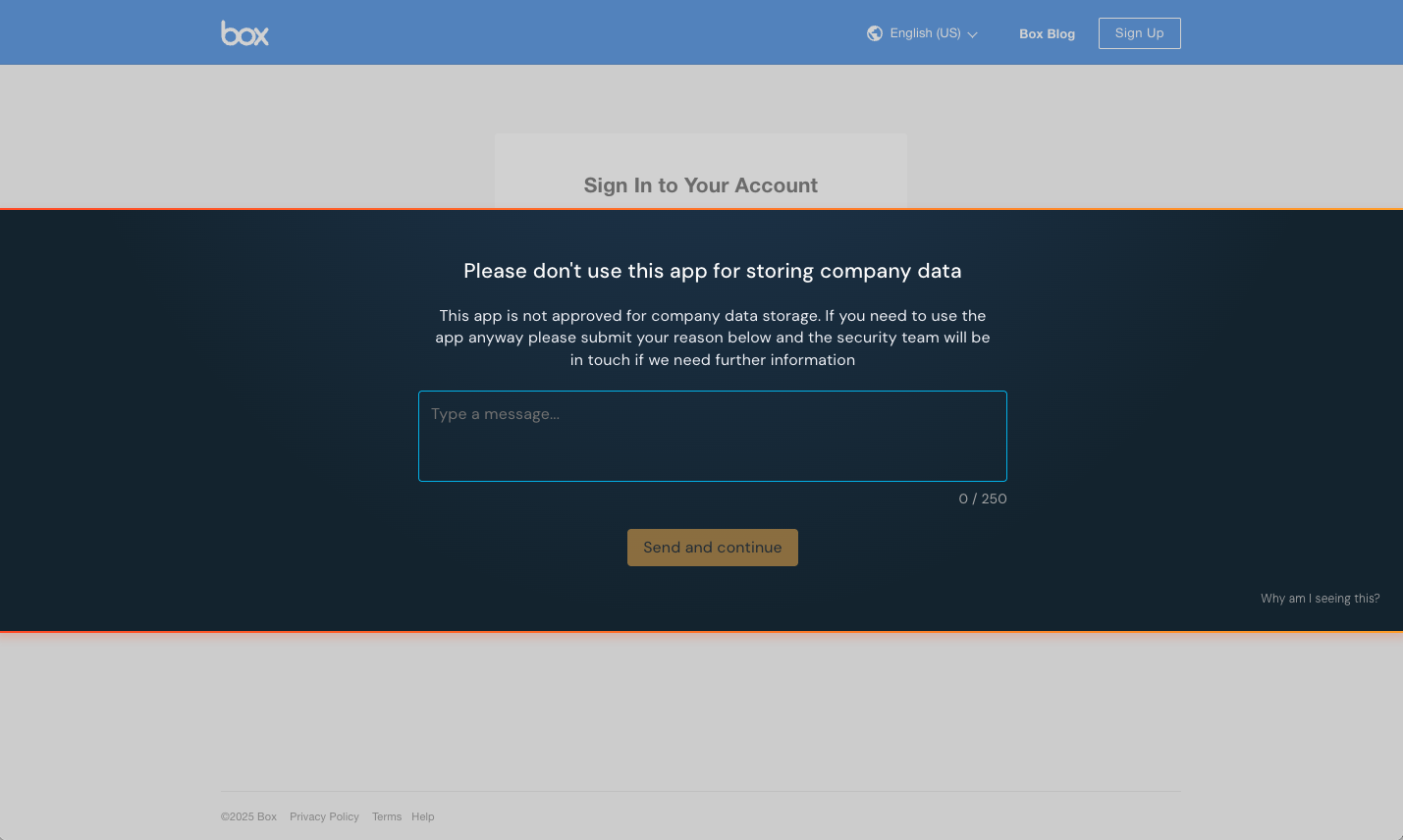
Require end-users to submit a reason when using an app
We’ve expanded our popular app banners feature to include a Reason mode that allows you to configure a custom message and require employees to submit a reason why they need to use a specific app before they can proceed to log in.
Monitor ‘other apps’ list via Push API and webhooks
You can now keep a closer eye on all new observed cloud apps by using the Push API and webhooks to notify you of new entries on the “other apps” list or to retrieve specific details about accounts on these apps. The “other apps” list consists of apps accessed by employees that Push doesn’t recognize as work apps but that may still be relevant to your operations.
