Can I use Push to detect phishing tools like Evilginx, Modlishka, NakedPages, or Muraena?
Yes. The Push browser agent can detect when employees visit websites that are using phishing toolkits such as Evilginx, Modliskha, NakedPages, Muraena, and others. Based on your configuration, Push can then warn or block employees from accessing those phishing sites.
These kinds of Adversary-in-the-Middle (AitM) toolkits can mimic legitimate login screens in order to steal credentials and bypass MFA.
You can enable Phishing tool detection on the Controls page of the Push admin console.
Learn more about how Push can help you detect and prevent phishing attacks in this related article.
How does phishing tool detection work?
The Push browser agent analyzes the behavioral attributes of phishing tools, e.g. “something the toolkit does” vs. just a static signature like a URL path or domain.
When Push detects a phishing tool in use on a website that an employee is trying to access, Push will enforce the Phishing tool detection settings set by an administrator.
Note: The browser agent will ignore flagging any scenarios in which the webpage is in the company domain(s), is on the ignore list under Settings > Advanced, or is in a private IP address space, including localhost.
What will end-users see?
If the feature is in Monitor mode, employees will not be notified that a phishing tool was detected and they will not be blocked from accessing the website. The Push platform will emit a webhook event that administrators can ingest into a SIEM or other monitoring tool.
In Warn mode, employees who attempt to access a website where Push detects a phishing tool in use will immediately see a custom warning message. They must click the acknowledgement button to proceed if they are sure the site is trusted.
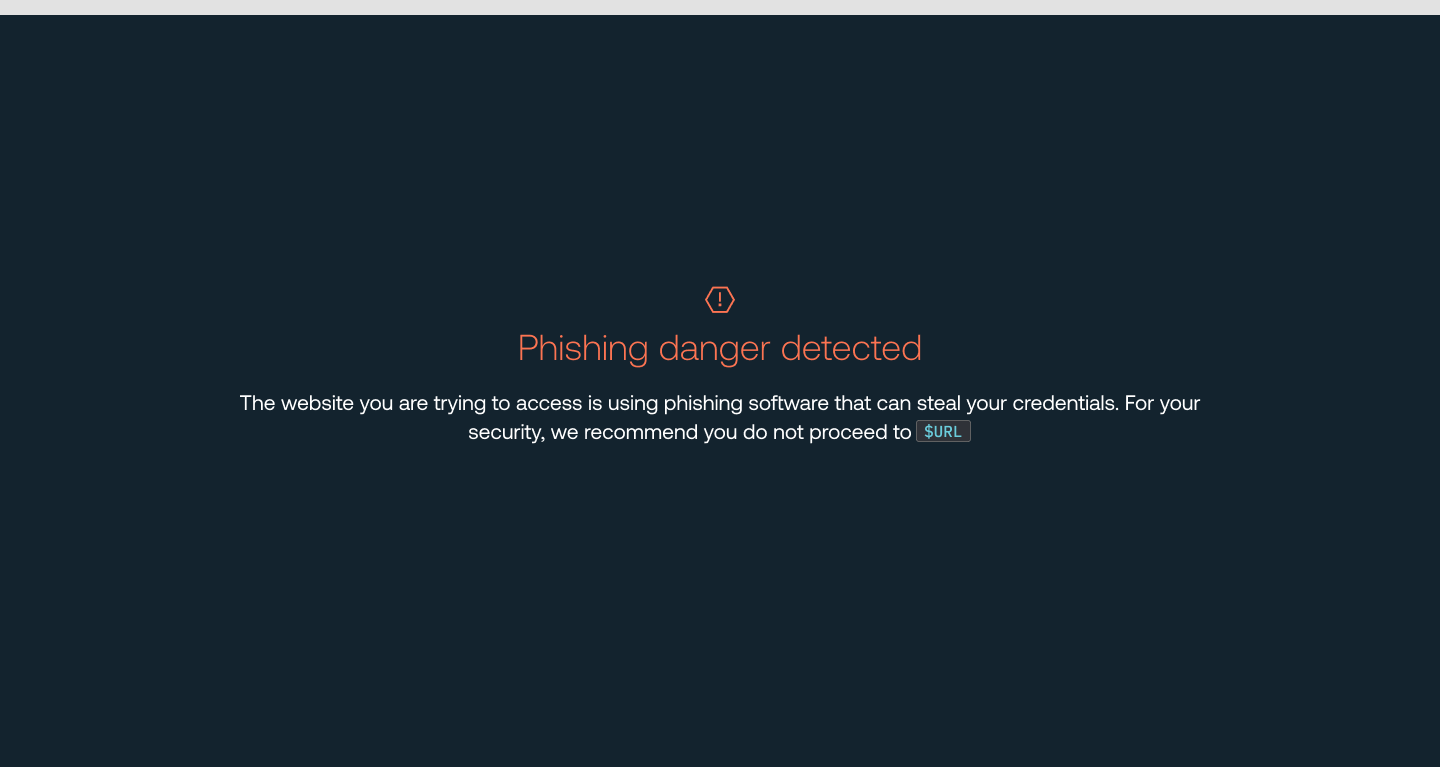
If the feature is in Block mode, employees will immediately see a block page with your custom block message and be unable to access the site.
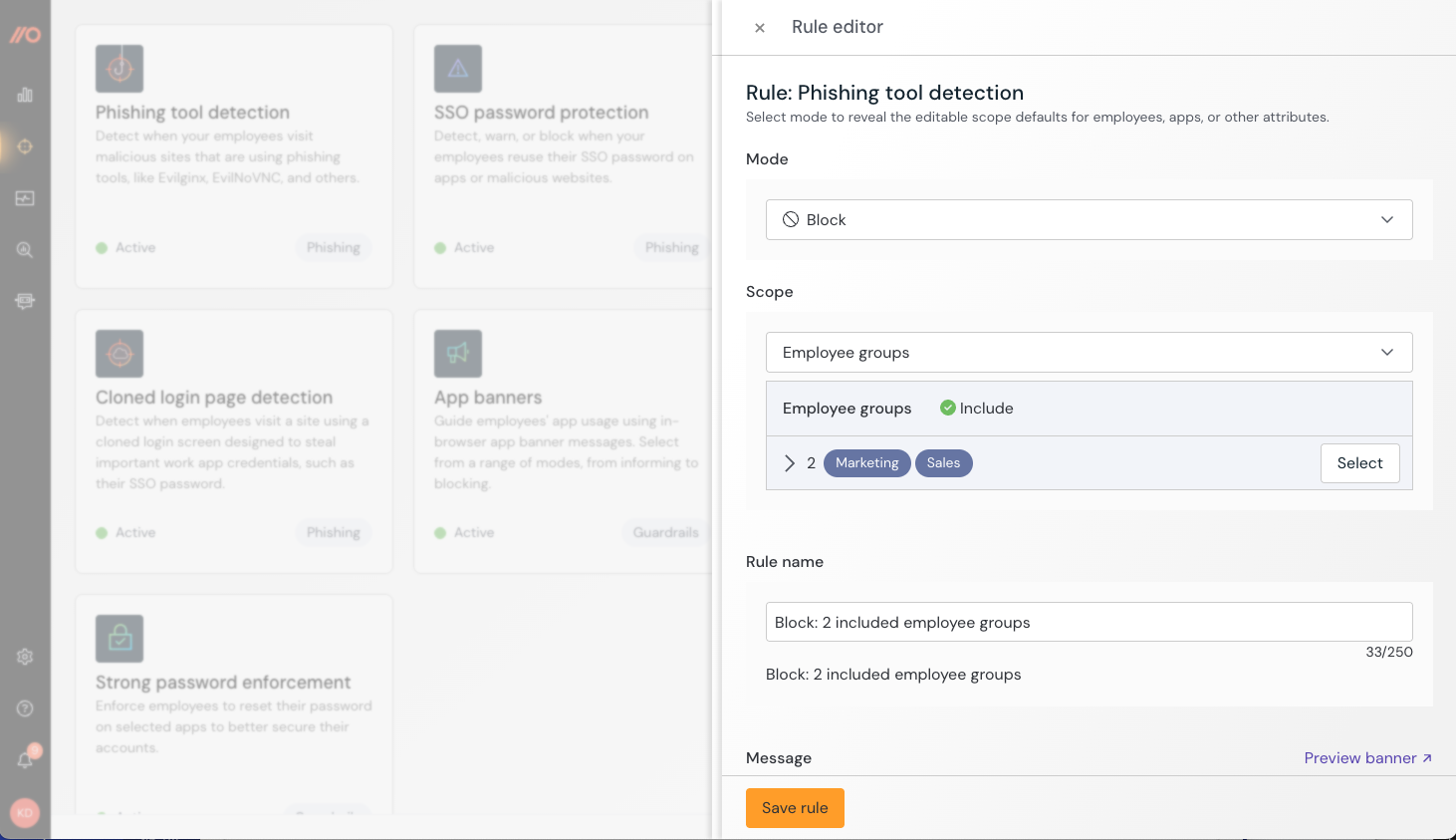
How to create a configuration rule
You can configure this control to apply to all employees, employee groups, or just specific individuals. You can also create an exception for specific employees or employee groups who will be exempted from this control.
When you enable the control, you’ll create a configuration rule that sets the Mode (Disable, Monitor, Warn, or Block) and Scope (all employees, specific groups, or specific individuals).
To exempt an individual or group, create a rule where the Mode is set to Disable and then choose the group or people who should be exempted.
Recommendations on using Warn and Block mode
By default, this feature is in Monitor mode for all employees. We recommend running the detection in Monitor for a little while to discover any exceptions in your environment. You can add exceptions to the Ignore specific domains list under Advanced settings on the configuration slideout.
Then, when you’re ready, enable Warn or Block mode with your custom end-user message.
Markdown for styling custom message
The custom message field for the block page supports link and email syntax using markdown, but no other formatting.
Example markdown:
[Push Security](https://pushsecurity.com)
[Steph](mailto:steph@ctrlaltsecure.com)
How do I get alerts about detected phishing tools?
Phishing tools that Push detects will trigger a detection on the Detections page, as well as a webhook event.
Read more in our developer documentation.