How does Push help detect session token theft?
Push provides a security control configurable by administrators that allows you to inject a unique marker into the User Agent string of sessions that occur in browsers enrolled in Push. This feature is powered by the Push browser agent.
By analyzing logs in the target app, you can identify sessions that both have the Push marker and that lack the marker, indicating the session is being used from both a machine with the extension and a machine without and therefore the session token may have been stolen.
Note: While Push can inject the unique marker into sessions on any domains you specify, the identity provider or application must provide a server-side session identifier so that you can determine which activity belongs to the same session, and then identify whether a marker is absent from activity on Push-enrolled browsers where you expect it to be present.
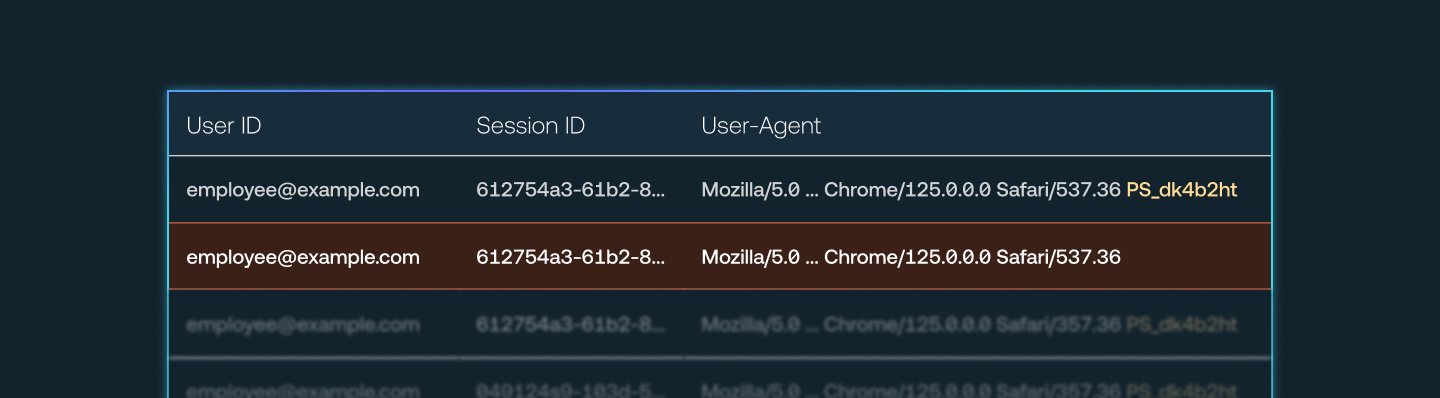
Any “unmarked” activity in the same session should be treated as a high-fidelity signal of session token theft, also known as session hijacking.
How to configure session token theft detection
You can enable session token theft detection in the Push admin console by going to Controls > Session token theft detection.
From the slideout panel, you can generate or refresh a unique marker to monitor for.
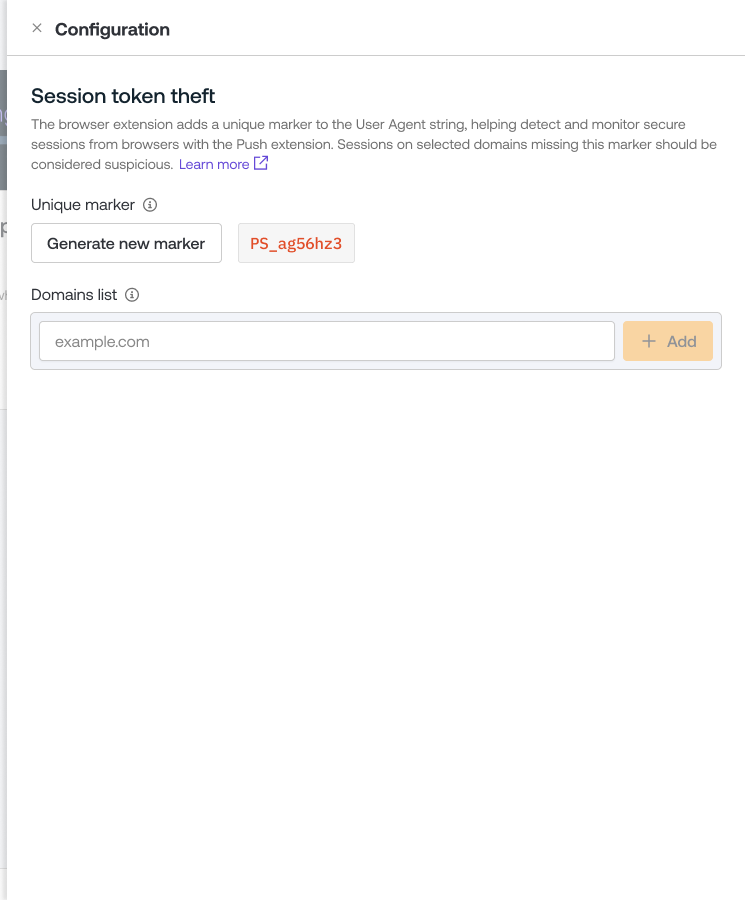
Then add the list of domains where you wish to inject the marker into sessions, such as your identity provider or other important applications that provide both a server-side identifier and the User Agent in logs.
Push’s research has identified that Okta and Microsoft both provide logs that display the User Agent and a server-side identifier.
If you use a custom domain for Okta, be sure to add <your subdomain>.okta.com to the list of configured domains.
To find a list of Microsoft domains, refer to Microsoft’s documentation.
Using wildcards
When adding URLs to your domains list, you can use a wildcard * (star / asterisk character) to partially match website domains.
For example, *.example.com will catch any subdomains in example.com.
Note: URL match patterns do not support the syntax .example. You must use the syntax *.example.com or *.example.org if you wish to have a wildcard for subdomains.
Example
Here is an example User Agent string showing the Push marker appended:
Mozilla/5.0 (Macintosh; Intel Mac OS X 10_15_7) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/124.0.0.0 Safari/537.36 PS_dk4b2ht