Enable plug-and-play detections and interventions in the browser using Push’s new security controls, or create your own automations from unique browser telemetry provided via API and webhooks.
Enable plug-and-play detections and interventions in the browser using Push’s new security controls, or create your own automations from unique browser telemetry provided via API and webhooks.
If someone asked you where you work, you probably wouldn’t answer, “My browser.” But that would be the truth.
(Threat actors already know where you work, of course, and they’ve been capitalizing on the massive shift to cloud-based workforces. Just look at any of the latest threat research reports on identity-based attacks to see how good a job they’ve been doing.)
To get visibility of your infrastructure in order to build a strong detection and response program, the equation used to look something like:
Network traffic + Logs + Endpoints = Profit!
But now there’s a missing piece, as identity infrastructure sprawls across IdPs, core apps, shadow SaaS and third-party integrations: Browser telemetry.
As a browser agent, Push is uniquely positioned to provide telemetry you can’t easily get anywhere else. We believe that this missing piece is the key to stopping identity attacks by providing the context both for first-class detections and security controls, as well as key correlations for events you observe in traditional log sources.
Now we have a better way to bring Push’s data to life to solve meaningful security challenges:
Plug-and-play security controls, accessible from the new Controls page in the Push platform
Choose-your-own-adventure tooling, including a REST API, webhooks, and a new Events page to help you visualize and build custom detections and automations.
Let’s take a closer look.
Plug-and-play controls
Security visibility without security control is a recipe for a stress headache, so we’re big believers in providing meaningful interventions that are easy to use.
With the new Controls page in the Push admin console, you can now find these preconfigured detections and interventions in one place. They cover use cases that any organization can benefit from, and take a unique browser-based approach to solving some thorny issues.
These controls include:
Phishing tool detection
Detect and block when employees visit webpages that use advanced phishing tools such as Evilginx or EvilNoVNC, among others. These adversary-in-the-middle (AitM) toolkits can mimic legitimate login screens, such as an Okta login page, to steal credentials and MFA codes.
Push emits a webhook event when the browser agent detects attributes of these malware. You can also set Push to Warn or Block mode to display a customizable message to end-users when they encounter a phishing site.
More about phishing tool detection
SSO password protection
Prevent employees from reusing their corporate SSO password on any page that doesn’t belong to the identity provider, including phishing sites. This means that even if that employee was the first person to get phished using a new attacker site, Push still detects it and blocks it.
Customize the message that end-users see in Warn or Block mode, or start out in Monitor mode to catch any false positives before you enforce the control.
This feature supports the following identity providers: Okta, Microsoft 365, Google Workspace, JumpCloud, Duo, and Ping Identity.
Push will also emit a webhook event when an SSO password is used, and if an employee clicks through the warning screen.
More about SSO password protection
URL blocking
When you find malicious sites you want to block, such as when responding to a phishing incident, add them to a blocklist and prevent other employees from accessing those sites.
URL blocking can be used in tandem with Push’s anti-phishing controls, so that as you discover malicious sites, you can block them from a central blocklist. This offers a kind of herd immunity where you can block other users from visiting a malicious site as soon as you have a single incident.
You can programmatically manage the blocklist using the Push REST API or sync to other threat intelligence sources you consume.
More about URL blocking
Session token theft detection
Inject a unique marker provided by the Push browser agent into the User Agent string of sessions that occur in browsers enrolled in Push.
By analyzing logs from your IdP, you can identify activity from the same session that both has the Push marker and that lacks the marker. This can only ever happen when a session is extracted from a browser and maliciously imported into a different browser.
This is a high-fidelity signal that a session token has been stolen and is being used.
More about session token theft detection
App banners
Add guardrails to employees’ use of SaaS apps with in-browser app banner messages you customize with your own text. You can require users to acknowledge having read a message before they can access an app, or even require them to submit a reason for using an app before they can log in.
More about app banners
Choose your own adventure
Want to do something creative? We've got you covered. Push provides a wealth of raw telemetry via the Push REST API and webhook events. Use this data to build both proactive and reactive security operations workflows, or add missing context to other sources, such as your IdP, application, or endpoint logs.
You can use this browser telemetry to:
Harden identities and reduce account compromise, such as alerting you when passwords are identified in public data breaches or when employees are using an unapproved app or when an SSO app is accessed via local account.
Monitor for suspicious activity or high-risk changes, such as checking for MFA method changes, or flagging when employees reuse corporate SSO passwords or visit sites running phishing malware.
Investigate indicators of compromise, such as correlating login events with platform logs, searching for recent signups to risky apps, or identifying post-compromise lateral movement opportunities.
In the “make my life easier” category, you can also use Push telemetry to:
Automate a workflow showing you all the accounts and apps used by an offboarded employee, and their account login methods.
Automate a workflow to revoke licenses on SaaS after a period of inactivity, saving money.
Build an approved apps list in your company wiki, synced from Push’s source of truth.
Force-reset an IdP password if Push finds a compromised password on an employee account.
To help you visualize and plan how you will use this telemetry, Push also provides an Events page in the admin console with a rolling 7-day snapshot of all the events in your environment.
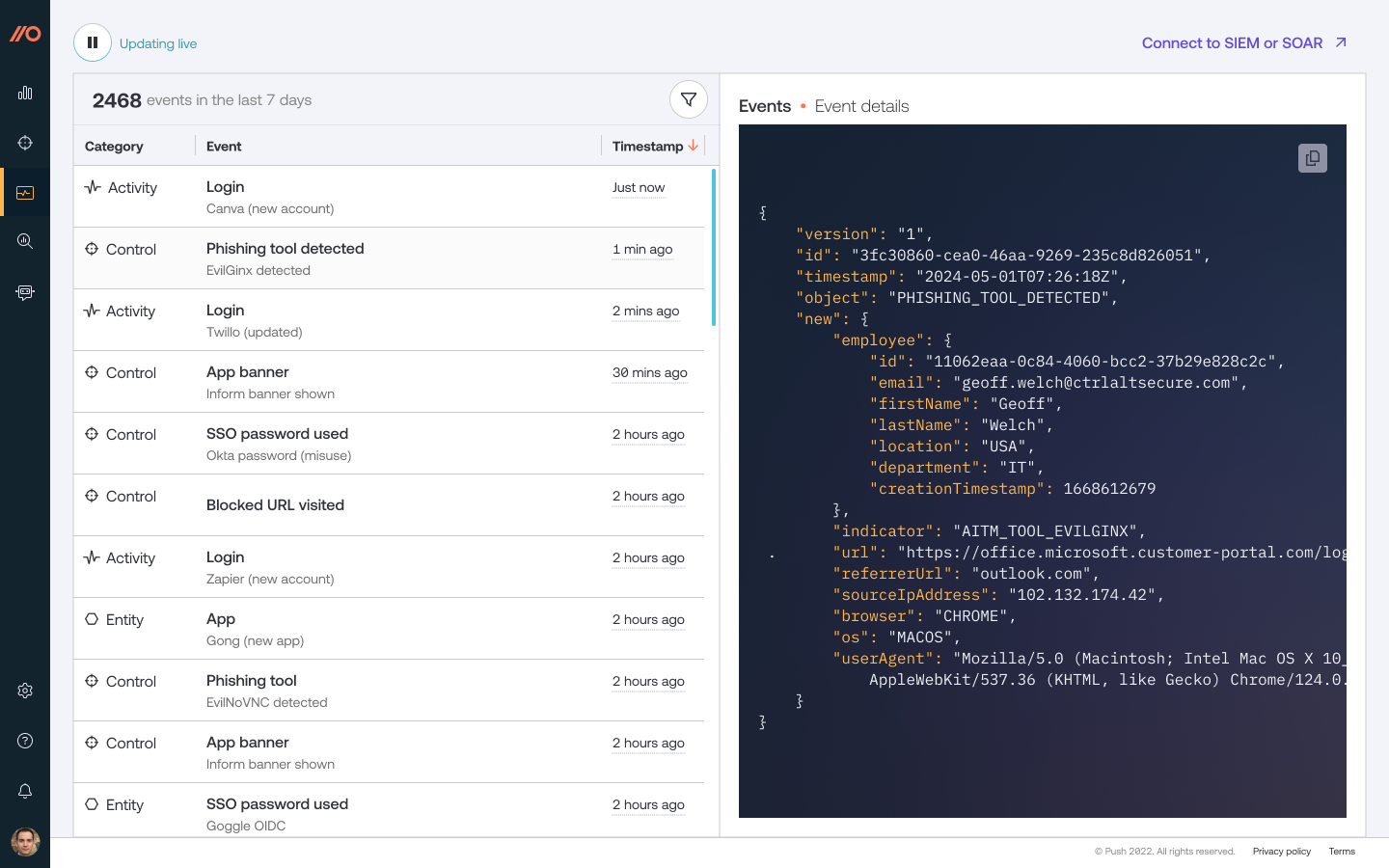
The Events page can help you see real-world examples, understand the attributes of each event, and gauge event volume before you ingest data into a SIEM or other platform.
What if you don’t have a SIEM?
While you’d need a SIEM for writing detections and performing log correlations, you can still get a lot of value out of Push telemetry if you don’t have one.
Use Push’s webhook events to send alerts directly to your Slack, Teams, or other chat platform, or build workflows that hook into your ticketing system or SOAR platform.
Review our webhooks documentation for a list of events.
Try it for yourself
You can try Push by creating a free account on pushsecurity.com. You can also book a demo. We’ll be happy to show you these features, along with how we discover all the apps your employees are using, even the ones not behind SSO.


