Push identifies session token theft by adding telemetry to the user agent string – using the power of our browser agent to create a new high-fidelity signal for your security team.
Push identifies session token theft by adding telemetry to the user agent string – using the power of our browser agent to create a new high-fidelity signal for your security team.
To detect session token theft, you need three things:
Robust logs that provide an identifier to help tie activity to a specific session
A well-oiled SOC to correlate observed activity in those logs
And telemetry to tie those logs to a trusted endpoint
The only problem? That third thing didn’t really exist. So we created it.
In this article, we’ll cover how Push’s recently released session theft detection feature works, why we built it, and why the unique control point provided by a browser agent unlocks new capabilities for blue teams fighting the effects of infostealer malware and other stolen credential-based attacks.
(You probably already know) Why this matters
Session token theft is a session hijacking technique where endpoint malware is used to extract sessions from an endpoint, and until recently it was relatively rare. It’s easier to gain access via a password than it is to steal a session cookie.
But there’s an inverse relationship between session-based attacks and MFA adoption. As MFA becomes widespread, adversaries turn to new effective methods of initial entry.
An increasingly common approach involves the use of infostealer malware, which can extract saved credentials, browser cookies, cryptowallets, and other valuable data from the infected endpoint.
Using stolen tokens, adversaries don’t need to bypass MFA directly. They can simply import the tokens into their browser and assume an already authorized session.
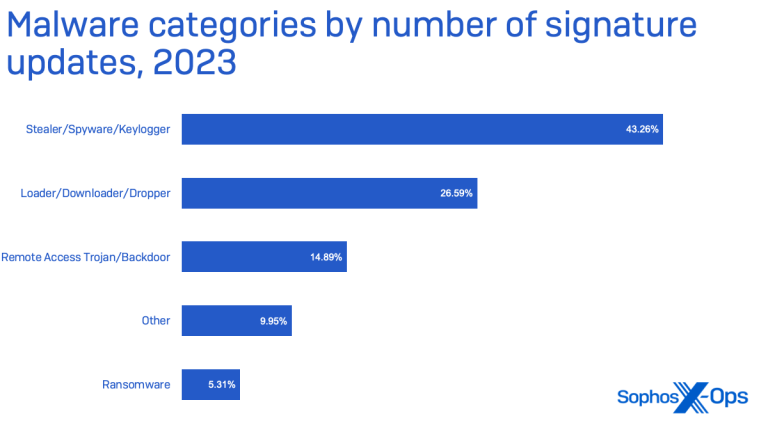
A few recent stats show the scope of the problem:
Nearly half of the malware detected last year by Sophos targeted victims’ data specifically, and the majority of that malware was classified as infostealers. Source: 2024 Sophos Threat Report
Information-stealing malware accounted for nearly 10 percent of activity that Red Canary was able to associate with named threats last year. They also found a rise in stealer malware targeting macOS compared to previous years. Source: 2024 Red Canary Threat Detection Report
Stolen credentials continued to rank as the top initial access method for breaches analyzed by Verizon. Source: 2024 Data Breach Investigations Report
The number of token replay attacks is increasing, with Microsoft detecting 147,000 attacks in 2023, a 111% increase year-over-year. Source: Microsoft Blog
What's missing from current defenses
When defending against infostealer malware or other forms of session and credential theft, there are a few common challenges that organizations may face:
Their endpoint security tooling doesn’t provide complete coverage across their device fleet, though they thought it did.
The malware is good enough to evade EDR detection, or it was able to execute and exfiltrate sessions or other data before it was stopped.
Existing approaches to detecting stolen sessions also pose a noisy problem. Relying on IP-based or geolocation-based signals can result in frequent false positives. (And not all identity provider logs include a session identifier that you can use to perform correlations in the first place.)
The missing piece is a trusted signal for legitimate sessions that you can use to correlate with other data in order to identify unexpected activity that indicates a compromised identity and device.
Generating unique telemetry via the browser
Push’s solution to detecting stolen sessions falls into the category of “so simple, why didn’t this already exist?”
The answer: Because you need to be in the browser to do it. The Push browser agent sits in a unique position that we can leverage to provide telemetry that otherwise would be extremely difficult to create.
Here’s how it works:
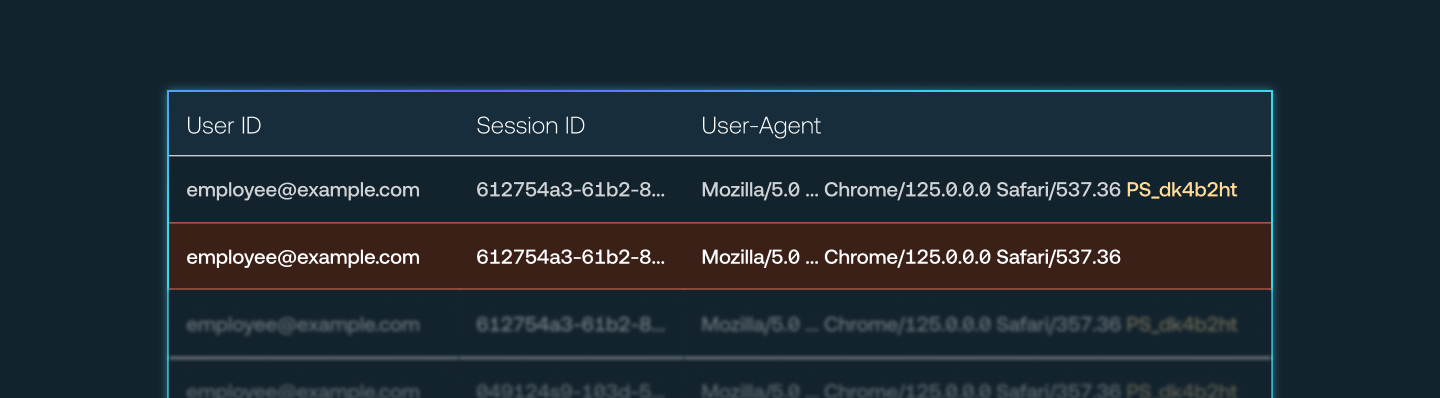
Via the Push browser agent, Push injects a unique marker into the user agent string of sessions that occur in browsers enrolled in Push.
Administrators then add the list of domains where they wish to inject the marker into sessions, such as an identity provider like Okta or Microsoft.
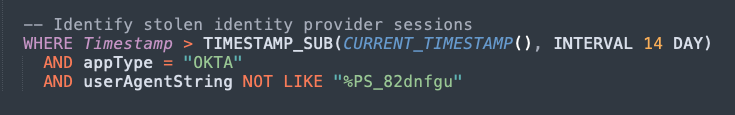
By analyzing logs from the IdP, you can identify activity from the same session that both has the Push marker and that lacks the marker. This can only ever happen when a session is extracted from a browser and maliciously imported into a different browser.
This is a high-fidelity signal that a stolen session token is in use.
Learn more about configuring this feature in our Help Center.
Unlocking new capabilities for blue teams
As we’ve said before, we see browser telemetry and browser-based controls as the missing piece in security strategies to stop identity attacks — particularly for modern organizations with complex identity ecosystems that span IdPs, SaaS apps, OAuth-connected apps, and more.
Where the browser agent approach particularly shines is that it’s application-agnostic.
As long as the app you want to monitor provides robust logs, you can inject the Push-supplied marker into any session on any app.
This allows you to detect suspicious activity even on internal corporate assets, such as an intranet.
A tidy side effect is that you can also use this feature to identify unmanaged devices accessing sensitive corporate internal resources because they will lack the Push browser agent-supplied marker.
There are probably a few other creative use cases for this feature, so we look forward to seeing what you come up with!
Try it for yourself
You can try Push by creating a free account on pushsecurity.com. You can also book a demo. We’ll be happy to show you this feature, along with how we discover all the apps your employees are using, even the ones not behind SSO, and how we detect vulnerable identities and stop identity attacks with browser-based controls.


