It’s been a year since Push announced our Series A round. We wanted to take a minute to share some highlights of what we’ve built over the last year on our mission of stopping identity attacks and tell a bit of the behind-the-scenes story of why.
It’s been a year since Push announced our Series A round. We wanted to take a minute to share some highlights of what we’ve built over the last year on our mission of stopping identity attacks and tell a bit of the behind-the-scenes story of why.
As we look back at a year of building on the Product team at Push, three big themes stand out:
Cloud identities are increasingly under attack
A big focus for us this year was to deepen our understanding of the landscape of adversarial techniques in the world of emerging SaaS-first attacks that don’t touch the endpoint or network, and it’s clear they are becoming both more prevalent and more advanced.
Credential stuffing is the internet’s most prolific attack vector today. In December 2023, Microsoft reported that attempted password attacks against Entra have increased to an average of 4,000 per second. This is a tenfold increase from the same time period in 2022.
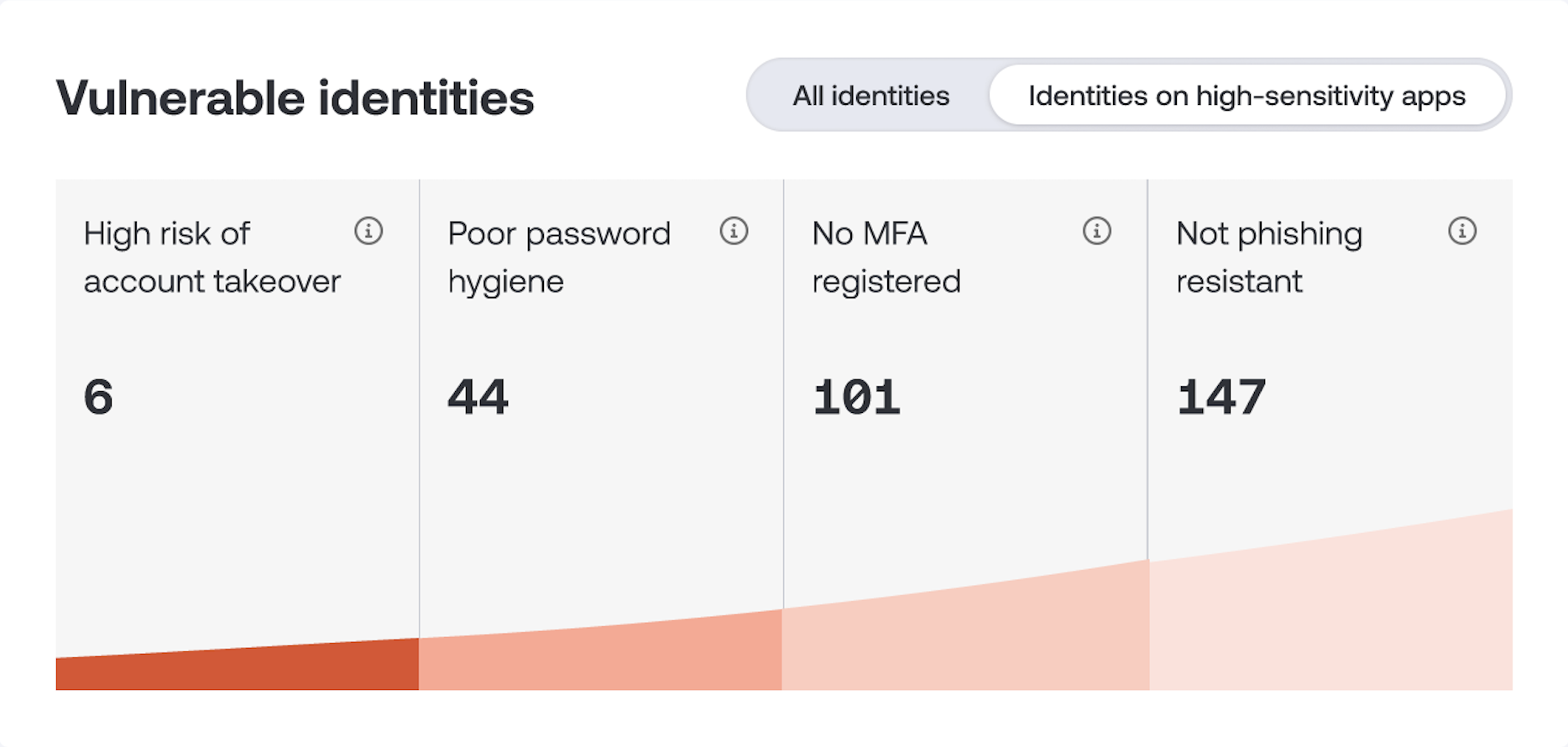
To help address this, our app helps you quickly determine which accounts are at highest risk of attack by highlighting which use passwords (as opposed to SSO), have a weak or leaked password, and don’t have MFA. We built a dashboard that brings all this together, allowing you to quickly zero in on at-risk accounts — you can even filter it by the apps that house sensitive data to have a focused starting place.
We also spent the last year going deep into emerging methods that are powerful but lesser-known, publishing our SaaS attack matrix project on Github.
Just a few months after publishing the project, we’ve seen increasingly regular headlines from organizations battling cloud-native attacks that target insecure identities. It’s abundantly clear that we are seeing real-world attacks shifting to an organization’s cloud and SaaS attack surface.
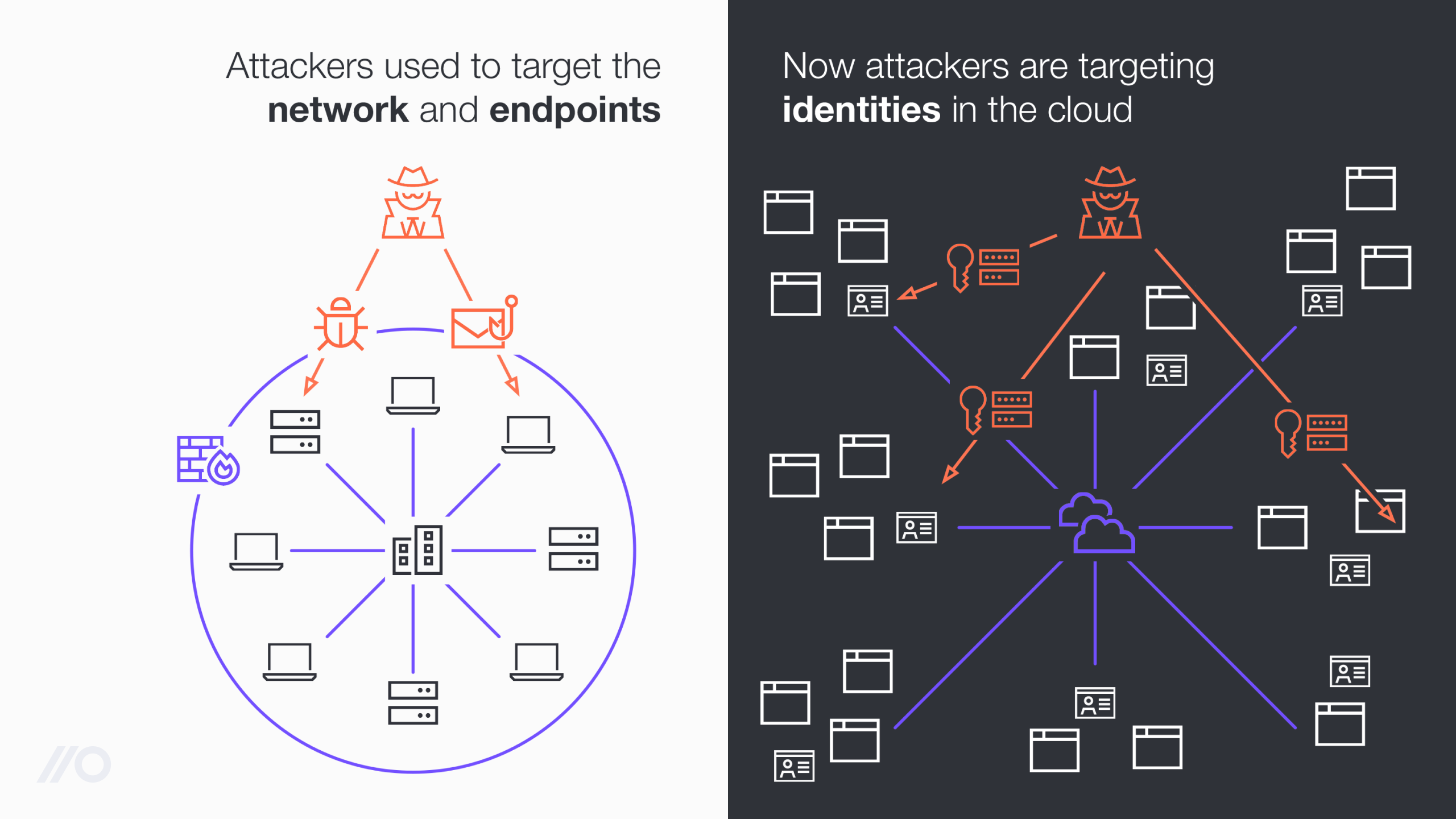
As a product, Push will continue to leverage its privileged position in the browser to do even more to prevent and detect identity-based attacks in the coming months.
Being in the browser is invaluable for securing identities — and we’re going to push the power further
Beyond providing the most reliable telemetry for managing identity security posture, being in the browser means that Push can engage directly with end-users to encourage security best practices.
Over the last year in conversations with customers, we kept hearing a phrase repeated: “I just need to add some guardrails to help employees.”
The idea was born for our most popular feature to date: The app banner.
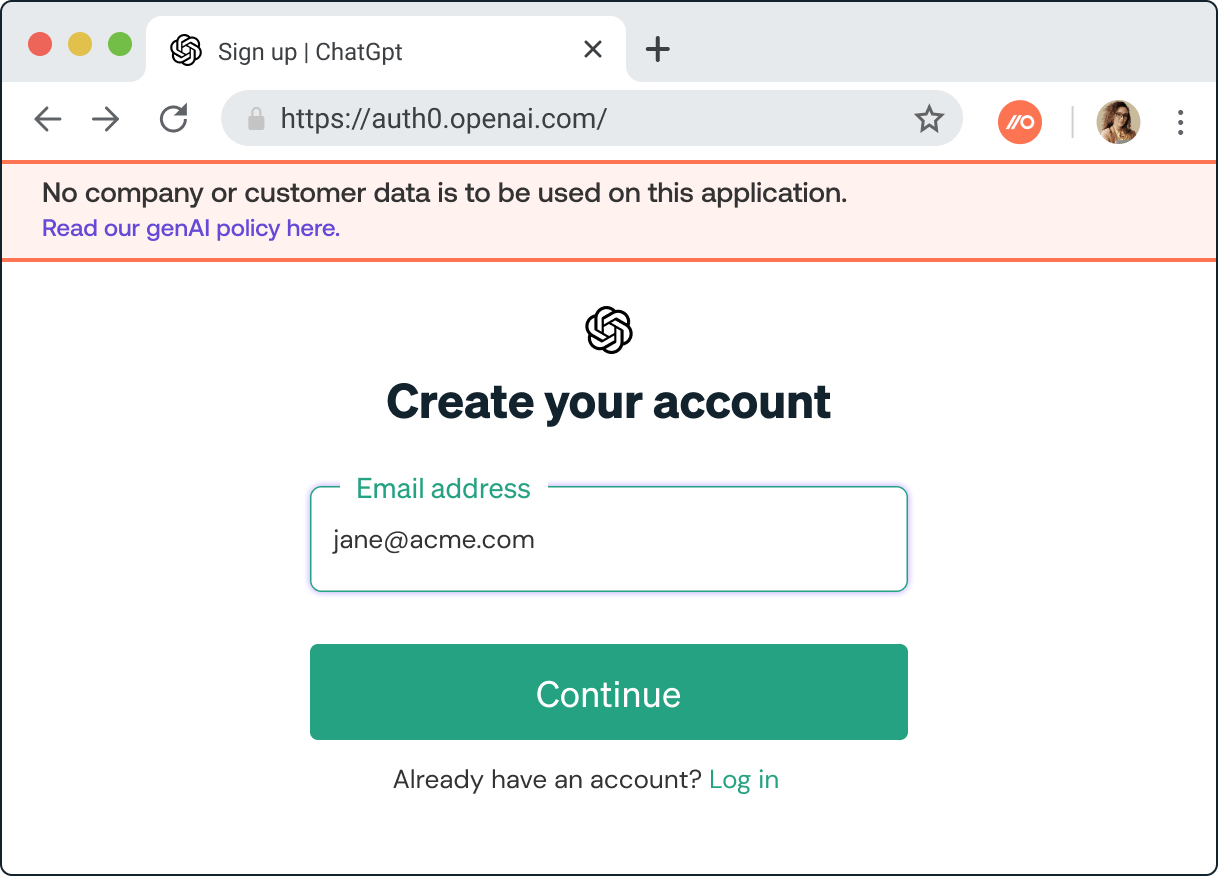
App banners are custom messages that appear on the signup and login pages of an app and provide quick contextual guidance to employees. They’re fully customizable to match an organization’s policies and voice – even their preferred language (we’ve got at least 1 customer using bilingual app banners).
We’ll be continuing to iterate on this feature, with more ideas in store.
Other features we shipped this year that rely on Push’s position in the browser:
Assuring password quality:
Ability to detect leaked passwords by comparing a k-anonymized salted hash of a password and the corresponding username to the Have I Been Pwned data set.
Ability to flag passwords that use restricted terms, such as the company name. Administrators can customize this word list.
Guiding end-users at the point of need:
Ability to set inline browser prompts that alert end-users when they’re signing up or logging in to an app with a weak or reused password and provide them with guidance on fixing the issue.
Organizations don’t need more ‘data’ — they need context and control
A big puzzle we set out to solve this year was how to give customers the context they needed to identify risks and enact decisions about their cloud identities and SaaS estate, without contributing to the noise so commonly associated with legacy tools.
Here’s how we are approaching the solution and what we built this year.
Focus on showing core work apps — but make it possible to see everything: We recently added the ability to see all apps that employees access with their company credentials so customers can get a fuller picture of their identity and app sprawl. This improves the coverage of their app estate. But we also made a conscious choice to segment out those “other apps” (which could be unrelated to work) from the main data tables in the Push platform so the noise is minimal.
Similarly, Push also now supports the ability to monitor all email domains an employee might use to access work apps, filling in the gaps for users who may be accessing company assets with personal accounts.
Give important context by surfacing login methods: One data point we’ve made a point of enriching in Push this year is login methods. We can now detect if an employee is accessing an app using SAML, OIDC, or local password.
First, this information helps security teams understand where users are actually using apps (unlike legacy solutions that only show network traffic). Second, it helps security teams gauge their progress toward reducing identity sprawl by reducing the use of unmanaged accounts — important context for achieving security goals.
We’re now turning our attention to continue providing meaningful controls — building on the success of our employee guardrails, like app banners, as well as new features for detecting attacks, blocking malicious sites, and preventing phishing. Lots more to come!
