ChatOps topic guide: Potential account compromises
Use ChatOps to send your security team alerts when an employee who was contacted via chat about a suspicious mail rule confirms that they didn’t create the rule. This allows your team to begin investigating as soon as possible.
This ChatOps topic works together with the employee topic Suspicious mail rules. You must enable both the employee and the security team topics in order to receive suspicious mail rule alerts in your security team channel.
What kind of messages are sent?
If an employee contacted via chat confirms that they do not recognize a suspicious mail rule, Push will send a message to your designated security team channel to indicate a potential account compromise.
If an employee indicates they didn't create the mail rule, it's a strong indicator that an attacker may have compromised their account and created a malicious mail rule, and you'll get an alert that looks like this:
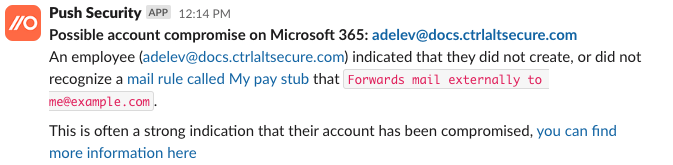
Refer to our ChatOps topic guide for suspicious mail rules to understand the end-user experience an employee will see.
Which platforms are supported?
We support Google Workspace and Microsoft 365 for mail rule detection.
Note that Google workspace calls mail rules “mail filters,” but they are very similar. Unfortunately mail filters cannot be disabled, and so we take no automated action on that platform, as deleting the rule automatically would limit the ability to investigate the incident.
Can’t I just disable mail forwarding to mitigate risk?
You can, but we wouldn’t recommend it. Employees often have valid reasons and use cases for mail forwarding, so it might be frustrating for your coworkers. We’ve written a short article on this topic that’s worth reading if you’re considering disabling mail forwarding options: Should you disable external email auto-forwarding?