Attackers are going out of their way to target Google Ad Manager accounts, powering malvertising scams. Here’s what you need to know.
Attackers are going out of their way to target Google Ad Manager accounts, powering malvertising scams. Here’s what you need to know.
In recent months, we’ve seen a significant increase in the number of attacks targeting ad manager accounts. These attacks range from phishing campaigns against marketing professionals to malicious sites impersonating legitimate marketing tools — ultimately serving up an Attacker-in-the-Middle (AITM) phishing page designed to steal the victim’s Google account.
Most recently, we reported on:
A campaign running fake malvertising ads for “Google Ads” in Google Search.
A campaign using sophisticated Calendly-themed phishing lures targeting marketing professionals.
A continuation of the Google Ads malvertising campaign, this time impersonating Ahrefs.
Why are attackers targeting ad manager accounts?
Ad Manager accounts on platforms like Google, Facebook, and LinkedIn have become lucrative targets for cybercriminals. By compromising these accounts, attackers can exploit the digital advertising ecosystem in various ways for financial gain.
The ad industry’s scale makes it attractive to fraud. Estimates suggest digital ad fraud cost advertisers tens of billions, potentially nearing $100 billion or more, with projections reaching $172 billion by 2028.
A hijacked Google Ad Manager account gives attackers access to significant ad spend and account data which can be monetized. The tactics range from stealthy ad fraud to overt abuse like malicious ads or extortion schemes.
Here’s how attackers can profit from a compromised ad manager account — and how it impacts your business.
Malvertising
Arguably the most dangerous use of a compromised ad manager account is to conduct malvertising – inserting malicious ads or redirects in place of legitimate advertisements.
Malvertising scams happen across lots of different sites, but the most common platform we see targeted is Google Search. This takes advantage of users browsing to find a website and clicking the first link that appears — in this case a fake sponsored link taking you to the attacker’s page.
The goal here is usually to compromise more devices and accounts, via:
AITM phishing sites looking to hijack sessions on valuable accounts — usually enterprise SSO accounts such as Google or Microsoft, but also many high-value SaaS services, as well as logins for banking and cryptocurrency sites..
Deploying infostealer malware, harvesting credentials and user sessions from the compromised device to enable broad access to apps via compromised accounts.
Running ClickFix-style social engineering scams prompting users to perform a malicious action (typically running code on their device, although a new browser-native version of this attack in the form of ConsentFix was recently discovered by Push researchers).
Infecting machines with malicious software to siphon compute power for cryptomining or adding the device to a botnet used in DDOS attacks.
Harvested data can be used by the attacker directly to conduct cyber attacks, but is more commonly sold on to other criminals further up the supply chain. So, attackers are using compromised ad accounts, to take over more accounts used to manage ads, to take over even more accounts… You can see how this can quickly snowball into something hugely profitable for attackers.
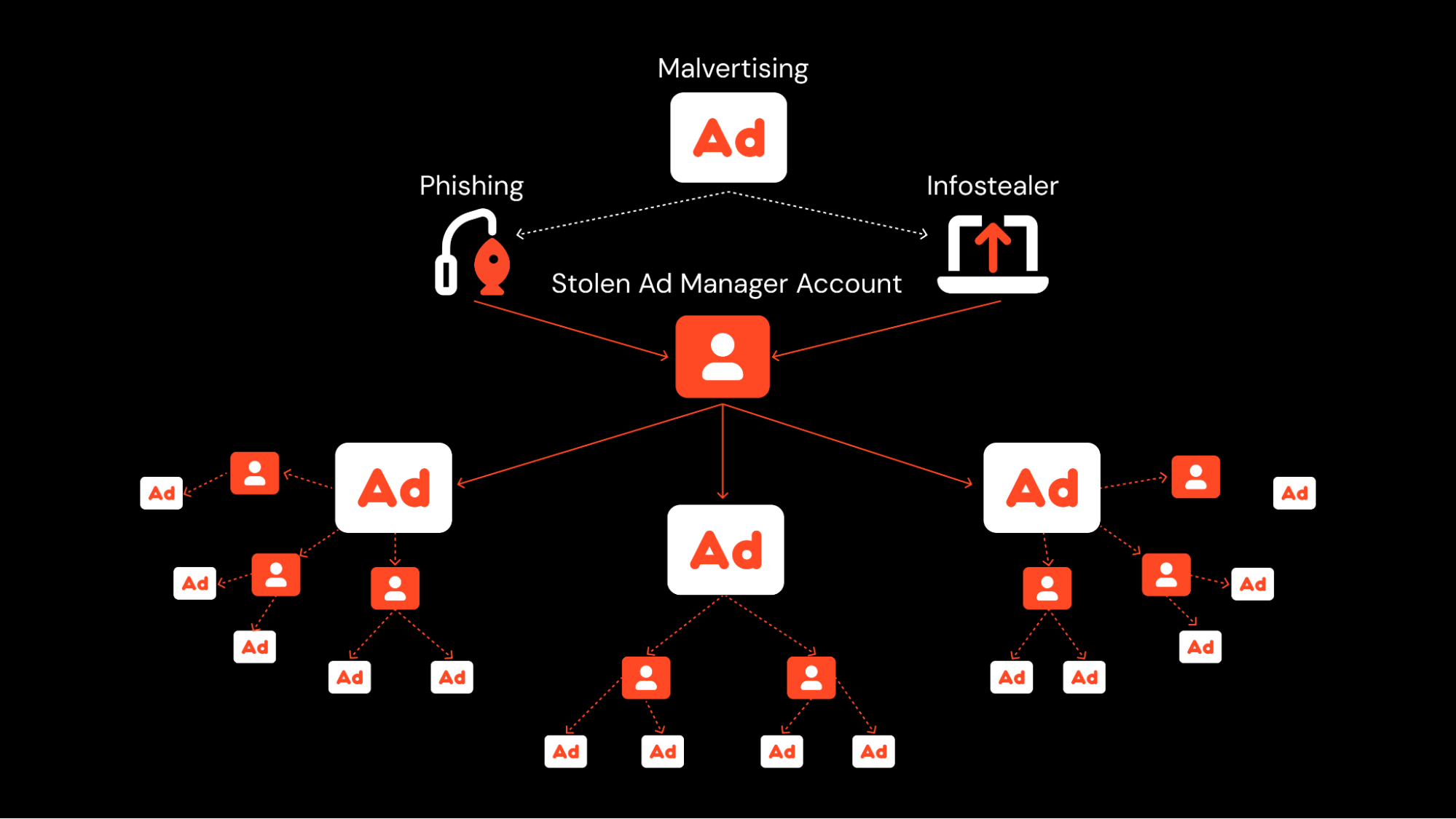
Malvertising scams don’t just target ad manager accounts either. They can be found targeting all manner of sites. But all malvertising scams are underpinned by ad spending — so it makes sense that attackers are looking to harvest account access and make use of the pre-allocated marketing spend of their victims.
Large enterprises spend vast amounts on Google Ads, often starting at $20,000+ per month, with major brands sometimes spending $40 to $50 million annually, depending heavily on their competitive industry. So, there’s a lot to play with for an attacker — and it might be some time before a discrepancy is noticed by the victim.
Ad fraud
One of the most common motives for hacking ad accounts is ad fraud – generating fake ad impressions or clicks to illicitly collect advertising revenue. By hijacking a Google Ad Manager account, criminals can direct the account’s ad spend to their own fraudulent web pages.
When a Google Ads/Ad Manager account is compromised, attackers can create new campaigns or modify existing ones. By directing traffic to websites the criminals control (often low quality sites made specifically for advertising) the victim’s ad budget can be funnelled into the attackers’ pockets as ad revenue.
The hijacked ad accounts provide a means to introduce fraudulent traffic into legitimate ad ecosystems, often escaping immediate detection thanks to the account’s established trust or high spending thresholds. For example, a compromised account with a large budget can run thousands of ads pointing to fraudulent sites before being flagged.
This is often abused as a channel for money laundering. An attacker can inject dirty money into the ad ecosystem (for example, using a compromised advertiser account’s billing) and then receive clean money out the other end (as payments to a publisher or ad partner account they control).
In late 2025, agencies noticed a surge of Google Ads account takeovers where hackers ran unauthorized campaigns until budgets were exhausted. Google’s Threat Analysis Group found a cluster of Vietnamese actors who hijacked marketing accounts to “either sell ads to other actors, or sell the accounts themselves” for profit.
Similarly, a series of attacks on companies managing ads reported that their accounts had been hacked as early as January 2025. These attacks were linked to South American scam operations by MalwareBytes — likely the same group behind the attacks we recently identified.
Selling or sharing access with other criminal groups
Stolen advertising accounts themselves have become a commodity in the underground economy. Instead of (or in addition to) exploiting the account personally, a hacker might sell access to the compromised Ad Manager account on criminal forums.
There is strong demand for reputable ad accounts because they come with advantages: high spending limits, established credit card billing, a history of compliance (making them less likely to be flagged by Google’s fraud detection), and existing relationships with ad networks or clients. In other words, a hijacked account is a ready-made vehicle for anyone looking to run malicious ad campaigns without going through the usual vetting.
Access to a Google Ads account (especially one with a good track record or high credit threshold) can fetch a significant price in criminal markets. Compromised Google ad accounts have shown up for sale on hacker forums and darknet markets, often advertised with details like the account’s age, billing history, or spend limit. For example, a hacker on one forum might sell or rent a “2-year-old Google Ads account with $50k monthly spend history” for a price commensurate with its potential yield.
The previously mentioned Vietnamese threat group would “either sell ads to other actors, or sell the accounts themselves to other actors to monetize”. This means an attacker could use a compromised account as a platform to sell fraudulent ad placements (e.g. “pay us and we’ll run your ads via this legitimate account for X days”). If not, they just sell the whole account login to the highest bidder.
It’s also worth noting that a Google Ad Manager account is also an enterprise SSO account that can be used to access broader Google Workspace services, and any SaaS apps accessible via SSO.
Even if the victim isn’t predominantly a Google shop, a Google account using the same email as a different identity provider account (e.g. Microsoft) can still be used to access downstream apps via SSO. This is because most apps use the email itself as the identifier, while 3 in 5 allow you to access an account using a new login method without doing any further verification checks. Read our blog post on cross-IdP impersonation for more information.
Data theft and extortion
Most ad accounts contain valuable data – like audience lists, conversion data, or payment info. Attackers could exfiltrate this data and extort the victim by threatening to leak it or sell it (though this borders on a data breach scenario, it’s another way to extort via an ad account hack, especially for large advertising agencies handling many clients’ data).
An attacker might also threaten to manipulate the account in ways that hurt the victim financially. For instance, they could create fake campaigns that burn through the budget on useless traffic (driving up costs with nothing to show, or even causing overcharges). They could also threaten to click-bomb the victim’s ads (if it’s an advertiser account) so that Google’s systems detect invalid activity and suspend the account.
For the victim, the cost of reputational damage or lost advertising time can far exceed the ransom demand, which is why some might contemplate paying. A large brand could lose consumer confidence or partner relationships if their ads serve malware for even a short time. Agencies managing several client ad accounts could face client complaints and legal liability if an attack spreads offensive ads via their accounts – such agencies have noted the “serious financial threats” and client dissatisfaction resulting from ad account breaches.
Conclusion
Pretty much every enterprise today advertises their services via Google ads — this makes attacks on these accounts a unanimous problem. Agencies managing numerous client accounts are put further at risk. For example, if an attacker can compromise an MCC account (used to manage several ad accounts) they get full access to the agency’s customer portfolio.
Organisations need to be on guard against both attacks on accounts used to manage ads, and malvertising in general — which is an incredibly prevalent threat and one of the top delivery vectors for phishing attacks today. Malvertising attacks delivered over channels like Google Search are a great way to catch victims unawares while also evading typically email-based anti-phishing controls.
There’s a tendency to see malvertising as a more random attack, but Google Ads can be tuned to searches coming from specific geographic locations, tailored to specific email domain matches, or specific device types (e.g. desktop, mobile, etc.). If you know where your target organization is located, you can tailor the ad to that location. Even more precise ad targeting can be achieved on social media platforms.
Because these attacks completely circumvent the traditional phishing detection surface (email) and often happen entirely over the internet (meaning no endpoint security controls can come into play) the only way to reliably detect and stop these attacks is to intercept them where they happen — in the user’s web browser.
To learn more about how Push tackles browser-based threats, check out our latest product overview or book some time with one of our team for a live demo.
