Push is excited to partner with Panther to help security teams correlate Push’s unique browser telemetry with existing log sources to detect and stop identity attacks, including session token theft and adversary-in-the-middle phishing toolkits.
Push is excited to partner with Panther to help security teams correlate Push’s unique browser telemetry with existing log sources to detect and stop identity attacks, including session token theft and adversary-in-the-middle phishing toolkits.
While Push’s official mission is to stop identity attacks, our unofficial motto might be described as “don’t make security teams log into another tool if they don’t have to.”
To that end, we’re thrilled to announce a new integration with Panther that makes it possible in a few clicks to:
Ingest Push logs into your Panther SIEM.
Use preconfigured data schemas for these logs without having to create your own.
Enable ready-made detections for Push webhook events, including session token theft and adversary-in-the-middle (AitM) phishing toolkits.
The combination of Push’s unique telemetry, powered by the Push browser agent, and Panther’s correlation and log normalization capabilities was a perfect match, explains Panther’s Head of Partnerships, Andrew Dooley.
“As a SIEM, we’re looking for where we can find the most impactful security information in our customers’ environments to bring into Panther,” Dooley says.
“With identity-based attacks being so common and impactful, identity telemetry data directly from users' browsers is exactly the kind of high-impact logs we want to support our customers’ threat detection and investigation workflows.”
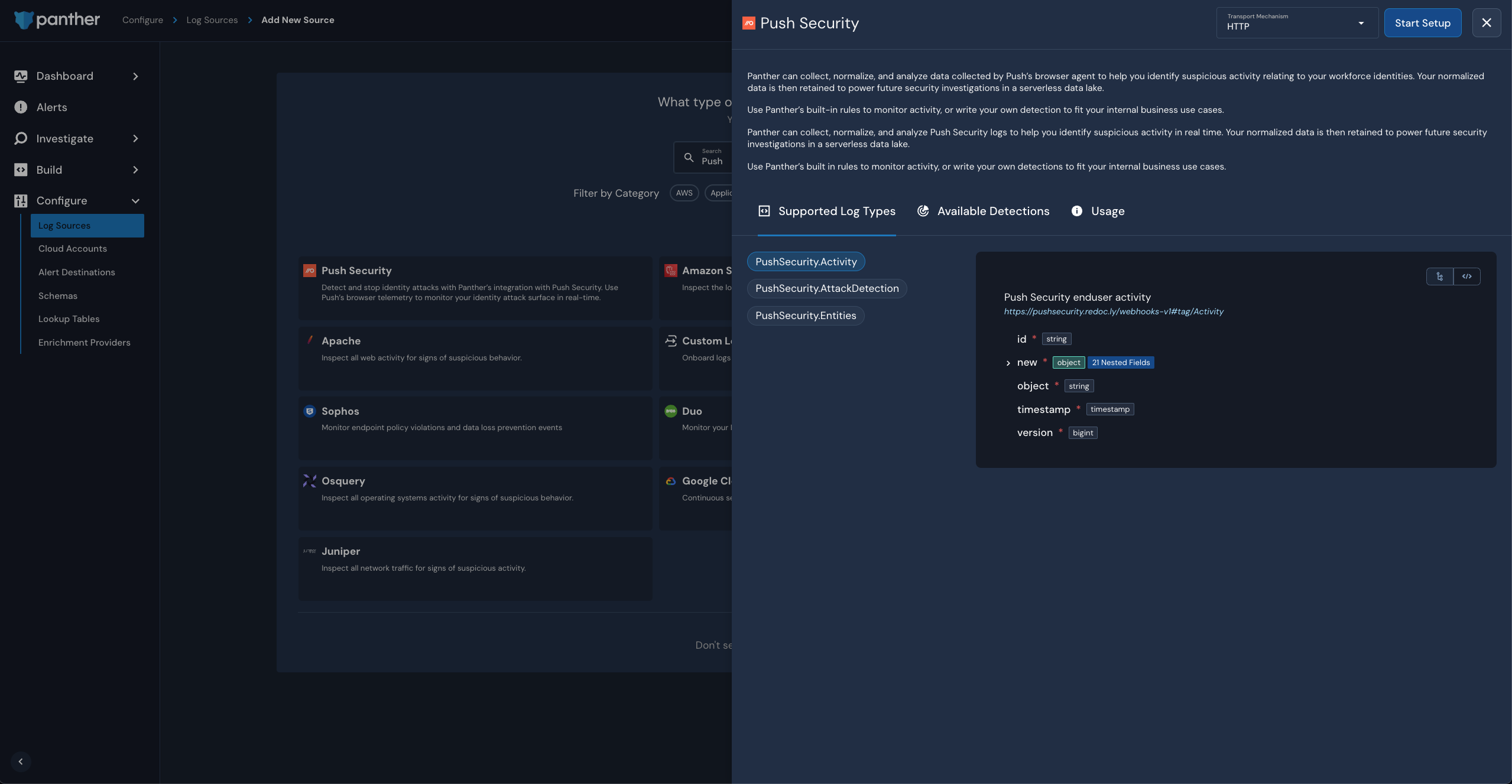
In this article, we’ll highlight some of the use cases you can achieve with the Push-Panther integration. Or, if you prefer, you can dive into the docs right away.
How to detect session token theft with Push and Panther
A key use case we set out to solve with the Push-Panther integration is detecting session token theft, a session hijacking technique where endpoint malware such as an infostealer is used to extract sessions and other valuable data from a device.
Using stolen tokens, attackers don’t even need to bypass MFA; they can just log in by importing the session cookie into their browser.
In the past, writing high-fidelity detections for session token theft has been extremely challenging because there was only squishy ground to stand on: IP-based or geo-based signals are noisy and frequently inaccurate.
Push recently released our session token theft detection feature, which uses the Push browser agent to inject a unique marker into the user agent string of sessions that occur in browsers enrolled in Push.
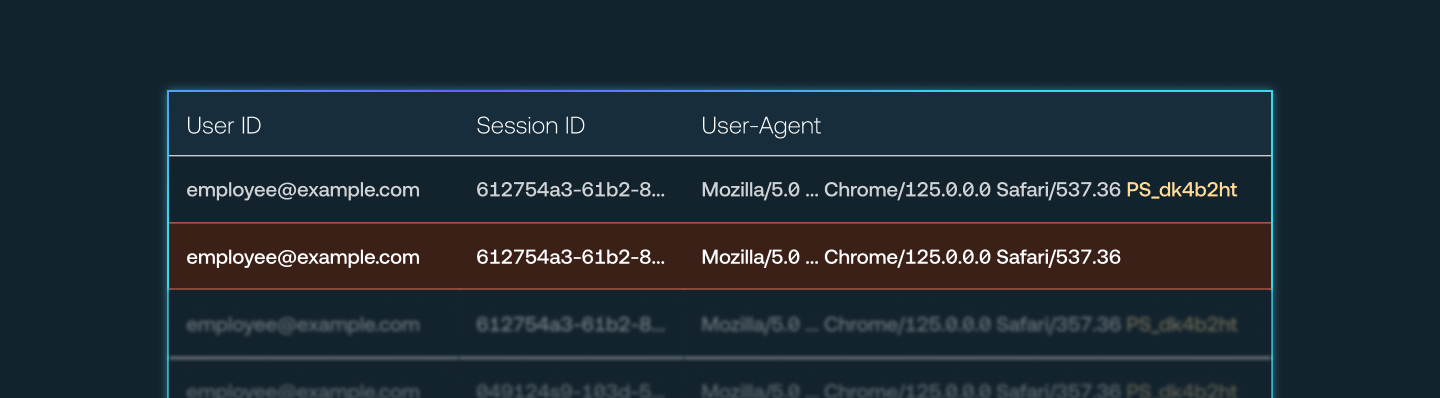
Things get interesting when you plug Push telemetry into Panther’s new Correlation Rules feature (or perform a correlation in your other SIEM of choice). By analyzing logs from your IdP, you can identify activity from the same session that both has and that lacks the Push marker, a high-fidelity signal that a stolen session token is being used by an adversary.
“Being able to correlate high-fidelity browser telemetry data with IdP logs and even more traditional endpoint logs is a powerful enabler for our users in catching bad actor behavior fast and early,” says Dooley, Panther’s Head of Partnerships.
Check out this video demo from Joe Stanulis, solutions engineer team lead at Push, and Nicholas Hakmiller, senior engineering manager at Panther, to see how Push and Panther combine their powers to detect session token theft.
As Dooley explains, “Push’s approach of generating visibility as well as security findings aligns well with Panther’s approach of centralizing customers’ security alerts but also combining multiple signals from different sources into one finding. For example, the Push agent can block phishing attacks when in Block mode, but when in Monitor mode, those findings can be sent to Panther to be correlated with other activity like unusual Okta logins to create a single alert that tells a more complete story of a user being compromised.
“Similarly, the Push user agent string marker leaves a very visible fingerprint in logs from other systems, making it easy to incorporate this Push feature into Panther detections across a variety of log sources and use cases.”
What else can you do with Push and your SIEM?
As a browser agent, Push is uniquely positioned to provide telemetry on your identity infrastructure that you can’t easily get elsewhere. This data is a key element to stopping identity attacks and account takeover by providing the context security teams need to write detections and to perform correlations with existing log sources, such as an identity provider.
General use cases for ingesting Push data into your SIEM include:
Detecting phishing attempts from AitM phishing tools like Evilginx or EvilNoVNC.
Monitoring for suspicious activity or high-risk changes such as MFA method changes or reuse of corporate SSO passwords on other apps.
Hardening identities and flagging poor hygiene behaviors, such as logging into SSO-protected apps with local accounts or reusing passwords across business applications.
Detecting the use of stolen session tokens, indicating a compromised identity and device, as discussed earlier.
Try it for yourself
You can try Push by creating a free account on pushsecurity.com. You can also book a demo. We’ll be happy to show you our session theft detection feature, along with how we discover all the apps your employees are using, even the ones not behind SSO, and how we detect vulnerable identities and stop identity attacks with browser-based controls.
For technical setup details on the Push-Panther integration, refer to the Panther documentation.

