Ingesting events using Splunk Cloud
Configure Splunk Cloud to allow for ingesting Push webhook logs.
Configure the log source in Splunk Cloud
To use the HTTP Event Collector (HEC), you must configure at least one token. Splunk Cloud distributes the token across the deployment. Note that the token will not ready for use until distribution is complete.
In the Splunk Cloud console, go to Settings > Data inputs.
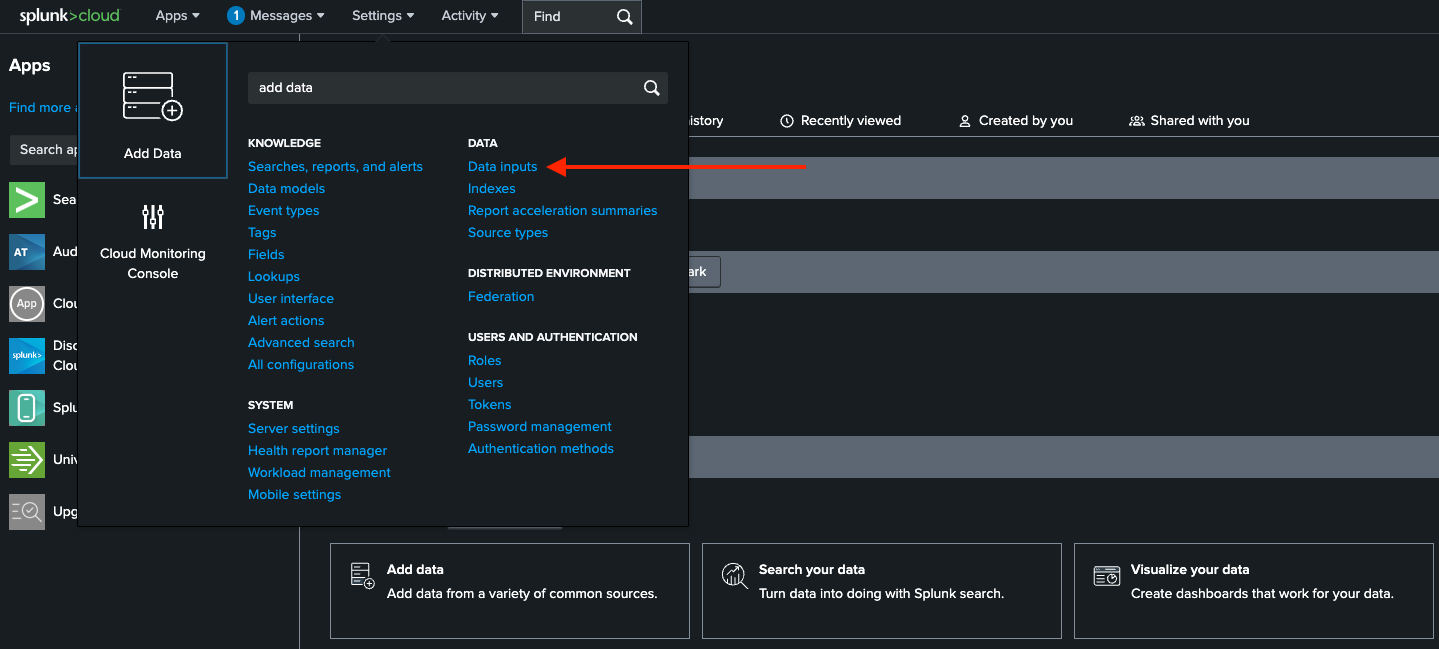
Choose HTTP Event Collector.
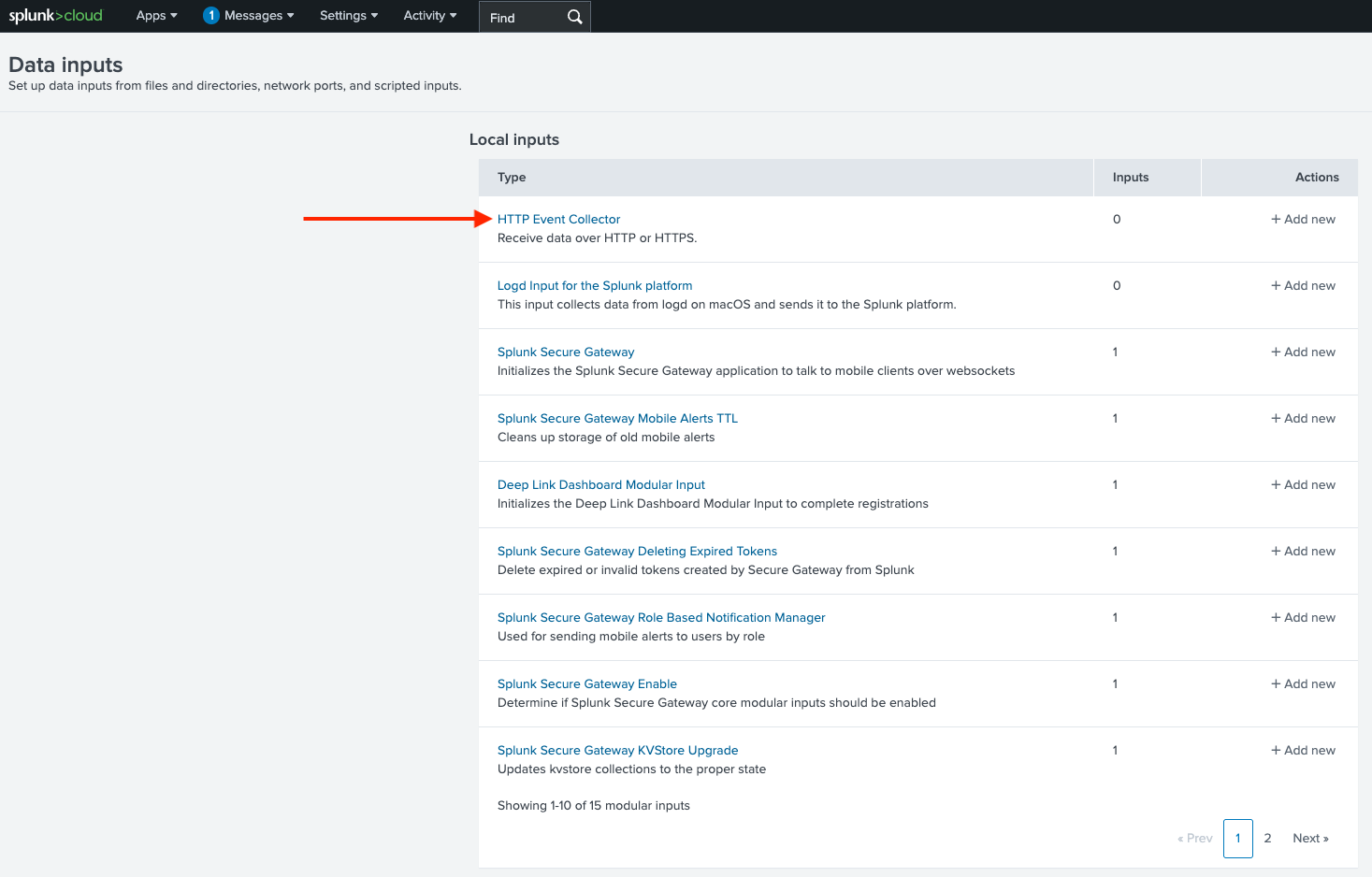
Select New Token in the top right and configure the token for your environment.
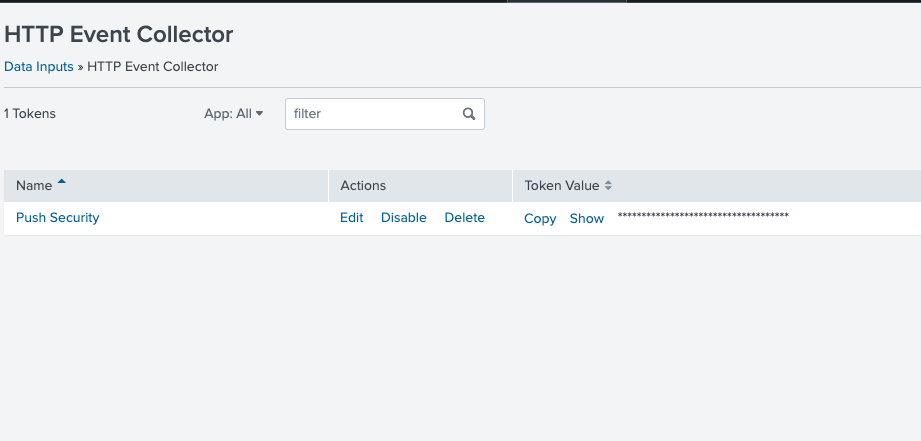
Then go back to the Data inputs page and copy the Token Value.
Configure the integration in Push
In the Push admin console, go to Settings > Integrations and select the Splunk Cloud tile.
Input the Token Value and your Splunk Cloud HTTP Event Collector URL.
Your URL should be similar to https://your-instance.splunkcloud.com:443/services/collector/event
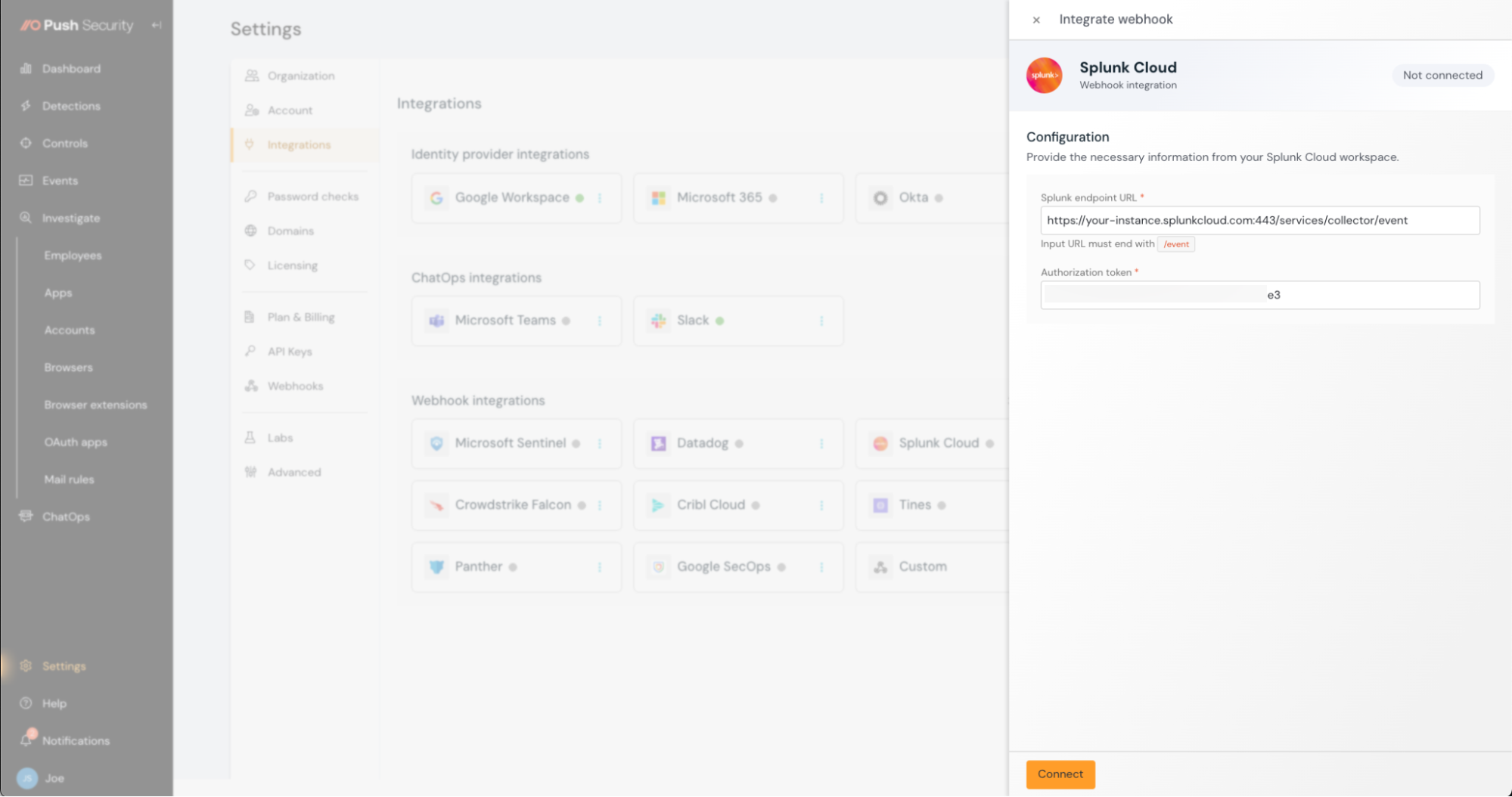
When you've entered those values, click Connect.