Getting started
Overview
Push Security helps you prevent, detect, and block identity attacks using an agent deployed as an extension to employee browsers.
Push generates telemetry using data collected in the browser. This enables you to:
Detect and block identity attacks, including advanced phishing techniques.
Proactively enforce end-user security controls that reduce identity security risks.
Map and monitor your identity attack surface by observing all logins to managed and unmanaged apps, including local password accounts, non-SSO apps, free-tier apps, and other shadow IT.
Uncover and automatically harden vulnerable workforce identities.
Push also syncs with your identity provider to enrich the data collected by the browser extension.
Key features
Browser extension: Push is deployed as a browser extension using an MDM, Google Admin console, Microsoft Group Policy, or manual enrollment. This agent observes employee logins and signups to cloud accounts using federated and unfederated identities. The browser extension then actively interrogates the collected data to detect common attack techniques, block phishing attempts, enforce end-user security controls, and uncover account security issues.
Identity provider integration: You can also integrate Push via API with your identity provider to sync data on employees, SSO-supported apps, third-party OAuth integrations, and OIDC logins.
API / webhooks: Integrate Push’s security insights and browser telemetry into your existing tools such as SIEM, SOAR, XDR, compliance, automation, and spend management platforms using the Push REST API and webhooks.
Admin console: Administrators can configure and manage the Push platform through an admin console, which provides a dashboard for reporting, a table of detected security events such as phishing incidents, as well as detailed data tables for all your apps, accounts, and employees and their associated security findings.
Chat platform integration: Receive real-time notifications in Slack or Microsoft Teams of newly discovered apps, accounts, and security findings. You can also enable chat messages to guide employees to fix simple account security issues.
How does it work?
Push captures work account logins to any apps used with a company email address. When an employee enrolled in Push signs up to or logs in to an app, the extension checks for the presence of a login field on the page and observes the user’s email address and login method. Learn more.
For 3,000-plus popular work apps, Push will also perform analysis of employees’ security posture, such as the security of their password and their MFA methods, and provide additional context around the apps in use.
You can configure Push to monitor cloud identities and apps for either:
Your specified company-owned domains only.
All domains used by employees to access work apps, including personal accounts.
Administrators can configure their domain monitoring preferences in the Push admin console. By default, Push does not monitor for logins by personal accounts.
Company domain logins to any apps that Push does not recognize as work apps appear in a separate list in the Push admin console for investigation. If you find apps you use for work in this list, request support for them by contacting the Push team.
Try Push for free
Push is free to use for up to 10 employees. You can sign up at pushsecurity.com to get full access to every feature, or request a demo first.
Administrator accounts on the Push platform do not consume a license for billing purposes unless you wish to also enroll those administrators as end-users in order to protect their accounts.
You can buy additional employee licenses on a monthly or annual basis. Note that administrators have full control over which employees are licensed in Push. Employees without a license are not counted for billing purposes.
Where to begin
The following steps apply to new administrators of Push. If you use Push as an employee end-user, refer to our employee documentation for help.
Setting up Push takes about 10 minutes. Complete your setup with these four steps:
1. Install the Push browser extension on employee browsers. You can deploy the extension silently to selected groups using an MDM and automatically license employees to enroll them in Push. The extension supports all major browsers, including Chrome, Edge, Firefox, Opera, Safari, Brave, Arc, and Island.
2. Configure Push’s security controls. Enable guardrails for employee activity, detect common identity attacks, prevent IdP credential phishing or reuse, and more.
3. Integrate with your identity provider to enrich the data provided by the extension and to provide a view into SSO apps, third-party OAuth integrations, and MFA usage on your core platform. You can also sync employees to Push using this integration and manually assign licenses if you prefer. Push integrates via API with Microsoft 365, Google Workspace, and Okta.
4. Turn on real-time notifications for your security team using Push’s ChatOps feature to send alerts on security findings and changes to your identity infrastructure (new accounts, new OAuth integrations, etc.).
You’ll see some data immediately after completing a setup task. Other data will populate as your employees log into apps. Here’s what to expect as a new administrator on the Push platform:
The browser extension observes real-time activity. You’ll see data for employee accounts and apps when logins are observed.
The identity provider integration will immediately import third-party OAuth integrations and MFA usage data, as well as employee records if you are licensing employees via the IdP integration. If integrating with Okta, you’ll also see a list of apps behind SSO. After the initial integration, Push checks once an hour to update this data in the Push admin console.
When you’re ready, integrate Push with your existing security and IT tooling, such as SIEM, SOAR, compliance, IT support, or automation platforms, and create your own custom detections and controls.
Initial login
You can sign up for a Push administrator account on pushsecurity.com. Choose your username and password or use a social login to sign up.
We recommend you use a Microsoft 365 or Google Workspace social login when signing up to use Push, or use multi-factor authentication (MFA) protection for your administrator account if you are using a username and password.
1. To set up MFA, select the Settings icon in the left navigation and go to My account > Multi-factor authentication.
2. Then select Enable MFA.
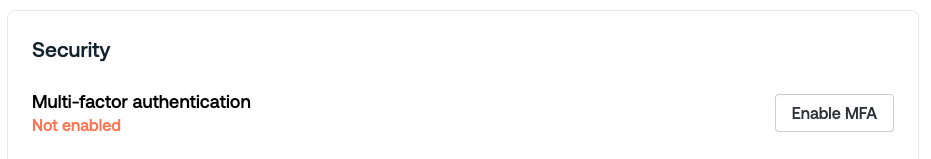
3. Use your preferred authenticator app to complete the setup and begin using one-time passcodes.
After signing up, the first administrator of the Push tenant will be prompted to install the Push browser extension and configure the tenant's monitored domains as part of the setup process.
Inviting administrators
We strongly recommend having at least two administrators on your account. This will help your organization maintain access to the Push admin console in the event of staff departure. You should also routinely audit the administrators who have access to your Push admin console.
To invite other administrators to the admin console, go to Settings > My team to send an invitation via email.

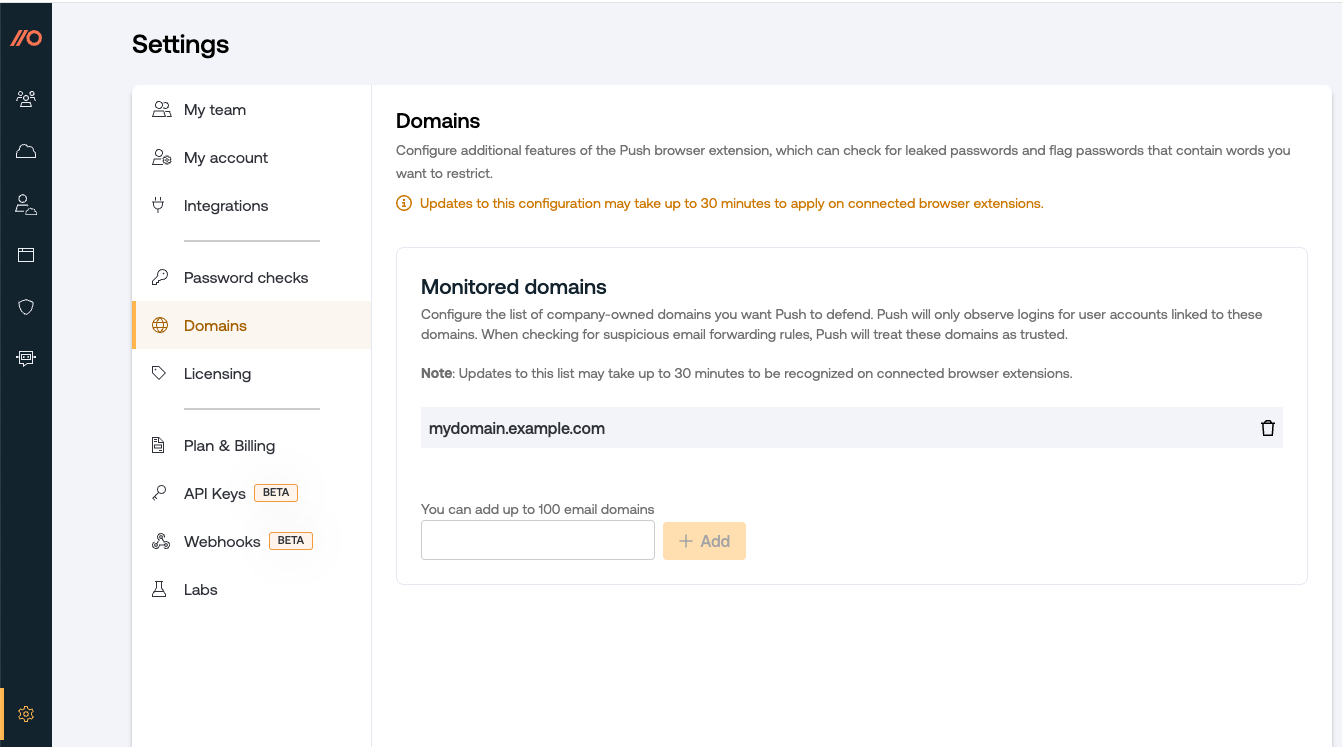
Enter your company domains
On the Settings page, you'll need to configure the list of company-owned domains you want Push to defend. Push will observe logins for user accounts linked to these domains. When checking for suspicious email forwarding rules, Push will treat these domains as trusted.
In the admin console, go to Settings > Domains.
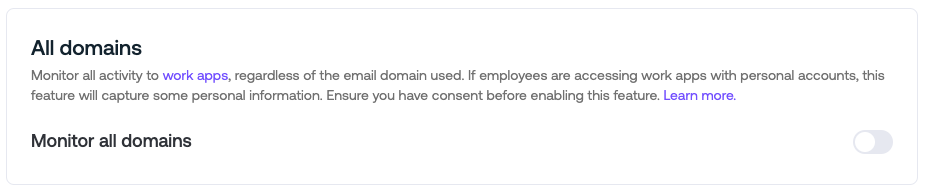
All domains option: If you wish to monitor all activity for work apps used in your environment, regardless of the email domain used, you can enable monitoring of all domains. Ensure you have consent before enabling this feature. Learn more.
Privacy and security
The sole reason Push exists is to improve security, so protecting your personal data is a top priority. We make considerable efforts to secure your personal information and we aim for full transparency on how we gather and use your personal information within our service.
Refer to our privacy policy for more details.
API and webhooks
Push provides a REST API to programmatically administer the platform, as well as webhooks to support real-time updates for platform events. Refer to our developer documentation for details.
Help
We’re always happy to hear from customers and are here to help. To find answers yourself, check out our Help Center articles. Or contact us to talk to a human.