Analysing the latest Scattered Lapsus$ Hunters (SLH) phishing campaign targeting hundreds of organizations.
Analysing the latest Scattered Lapsus$ Hunters (SLH) phishing campaign targeting hundreds of organizations.
Scattered Lapsus$ Hunters are running a large-scale hybrid vishing plus AiTM phishing campaign across several industry verticals, targeting Okta, Entra, and Google SSO platforms.
The attacks begin with the attacker calling their victim, impersonating IT staff from their company. They offer to help the employee set up passkeys for logging into the enterprise SSO service, tricking the victim into visiting a specially crafted adversary-in-the-middle phishing site that captures their SSO credentials, MFA codes, and ultimately live session access.
Once an account is stolen, the attacker logs in to the SSO dashboard to see which platforms they have access to and then proceeds to steal data from them — with the ultimate goal of extorting victims.
What we know
To date, 100+ companies have been targeted, with infrastructure and domains impersonating their brand to be used in legit-looking campaigns against them. The reality is that the list of targets could be more extensive, and will continue to increase over time.
SLH claims to be using data stolen in previous breaches, such as the widespread Salesforce data theft attacks reported in 2025, to identify and contact employees. This data includes phone numbers, job titles, names, and other details used to make the social engineering calls more convincing.
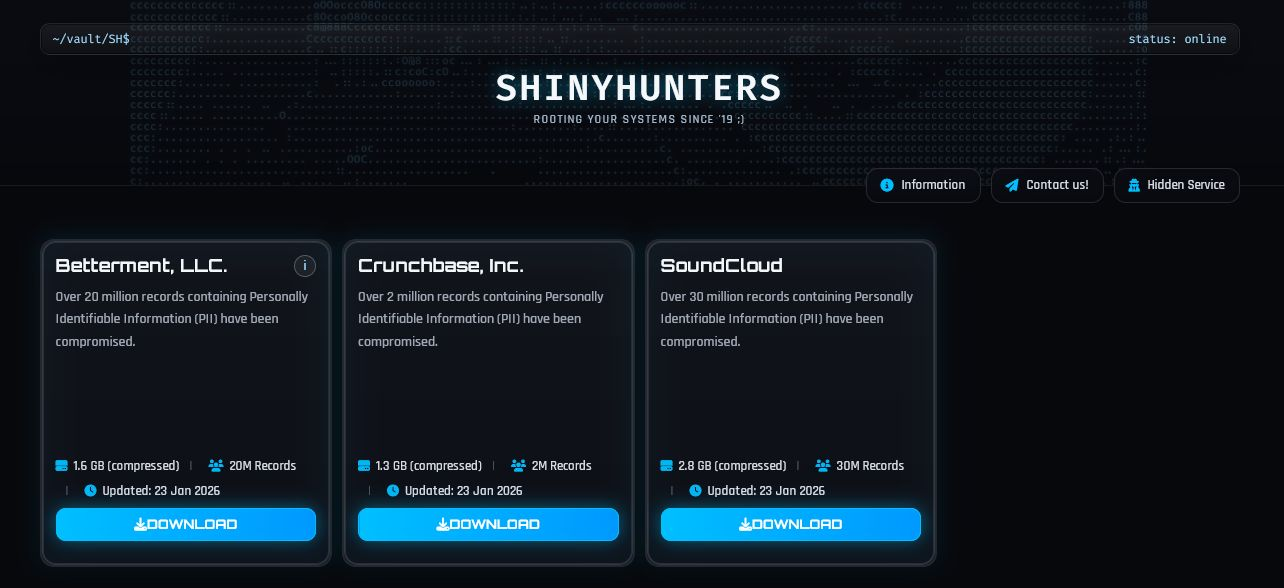
The group recently relaunched its Tor data leak site, which currently lists breaches at Betterment (20 million records containing PII), Crunchbase (2 million records containing PII), and SoundCloud (30 million records containing PII).
What’s new?
The best of both worlds? Vishing + AiTM phishing
SLH and threat actors affiliated with “The Com” are no stranger to voice phishing (vishing) or the use of MFA-bypassing Attacker-in-the-Middle (AitM) phishing kits.
SLH and it’s precursor groups leveraged vishing to great success in the form of help desk impersonation and password/MFA reset attacks as seen in the high profile Marks & Spencer, Co-Op, and Jaguar Land Rover attacks in 2025, as well as the Caesars and MGM attacks in 2023. MFA-bypassing phishing techniques have also long been a part of their arsenal, from the 2022 0ktapus phishing campaign to more recent use of modern AiTM phishing kits.
But until now, we haven’t seen them used together.
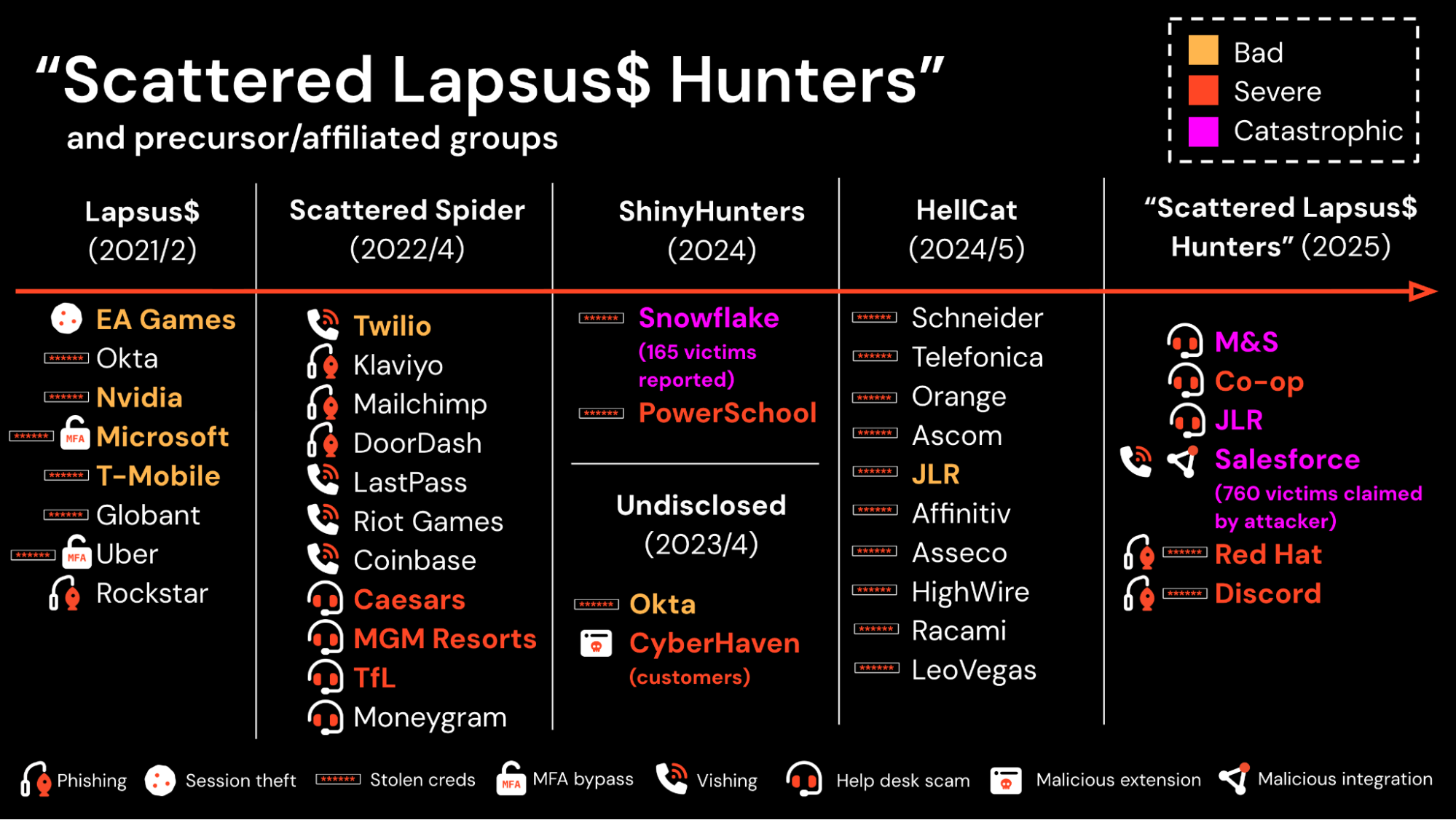
Get the background on Scattered Lapsus$ Hunters, and how they relate to Scattered Spider, Lapsus$, ShinyHunters, and other Com-affiliated groups in our recent deep dive, unpacking related breaches dating back to 2021 in our recent blog post.
It makes sense to combine these methods. AiTM phishing kits are flexible, highly customizable, and can be used to target a broad range of apps — including all of the major IdP platforms used for SSO. Vishing on the other hand is proven to increase the effectiveness of social engineering attacks when performed by an effective operator — which SLH are proven to be (helped by predominantly native English speakers making up their membership, along with the use of effective voice phishing tools).
Both vishing and AiTM phishing are identity-first methods that consciously evade traditional security tools and detection controls at the endpoint and network layer. This makes them highly effective in today’s IT environment.
A new kind of operator-driven AiTM kit
Another unique part about this campaign is that it uses a “live phishing panel” — i.e. a customizable phishing page controlled by the attacker in real time. This enables attackers to dynamically change what a victim sees on a phishing site while speaking to them on the phone. This allows them to guide victims through each step of the login and MFA authentication process.
This is principally to increase the victim’s likelihood of engaging with the phishing page. As you can see in the image below, there are several options that can be presented to the victim — including not just the normal phishing stages of entering credentials and passing MFA checks, but also post-compromise actions (e.g. creating a passkey that would then be controlled by the attacker for persistent access even if an account password is reset).
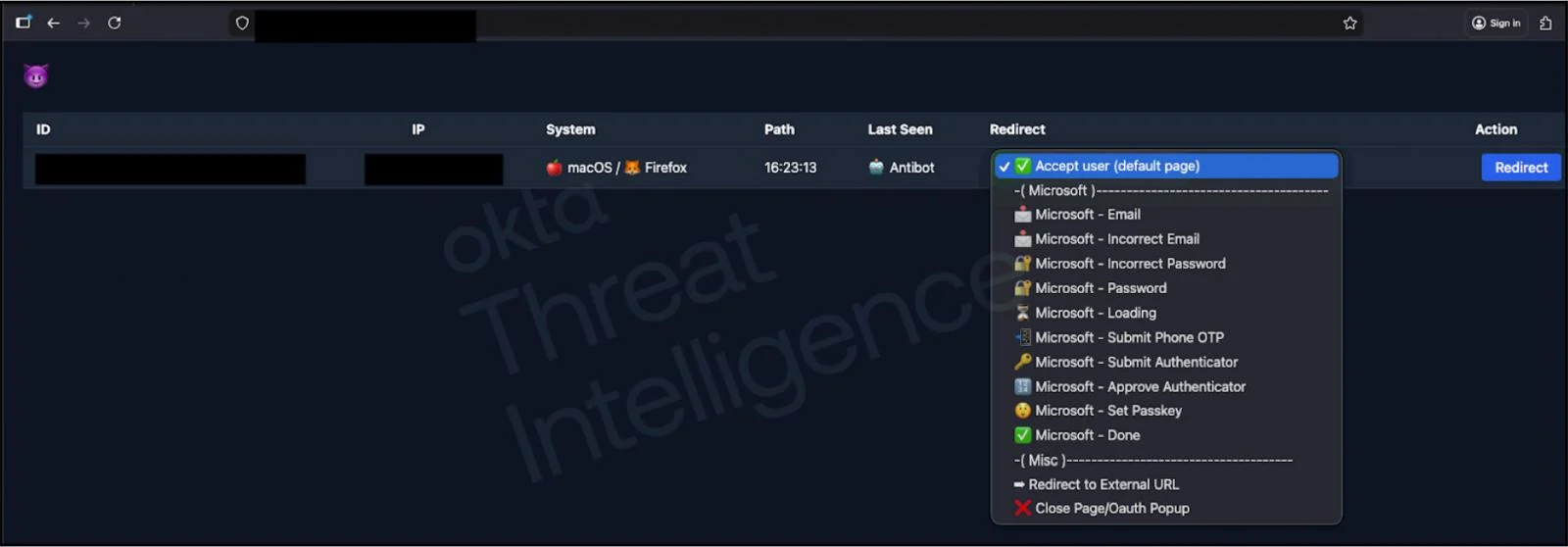
At the end of the authentication flow, the threat actor can choose to redirect their target to a “support ticket" closure screen. This allows the threat actor to manually terminate the session once the compromise is complete while providing the targeted user with context that matches the "IT support" ruse. This further reduces the likelihood of post-hoc reporting by a suspicious victim.
Given that this modular, operator-controlled phishing kit is reportedly available “as a service” for criminals, we should expect to see much more of this in future.
0ktapus 2.0?
As we mentioned earlier, Scattered Spider made their reputation launching phishing attacks against Okta accounts in the 2022 0ktapus campaign.
The vast majority of phishing attacks target IdP accounts because of the widespread access to downstream apps they grant via SSO.
This comes at the same time as attackers running campaigns to target LastPass master passwords. This provides a similar level of access to apps in the form of credentials (and sometimes saved passkeys).

Not only is this a goldmine for attackers looking to steal data or pivot to other systems to be able to launch further attacks (e.g. pivoting to cloud and on-prem services for ransomware deployment) but it’s a nightmare for incident responders. If an attacker can access an app and create a backdoor login method (AKA. a ghost login) it can be very difficult for a security team to identify and clean them up.
Mandiant has reported how the attacker opportunistically pivots across accessible SaaS platforms (SharePoint, Salesforce, DocuSign, Slack), hunting for specific strings like “poc,” “confidential,” “salesforce,” and “vpn.” Notable tradecraft includes using ToogleBox Recall to delete MFA enrollment notifications from victims’ inboxes and leveraging PowerShell to bulk-download SharePoint content routed through commercial VPN services like Mullvad, Oxylabs, and NetNut. Check out their blog post for some example SaaS activity logs that can be used to investigate a potential compromise.
Check out the excerpt from one of our recent webinars below for more information.
Impact analysis
This combination of methods is likely to increase the success of these malicious campaigns as well as reducing the likelihood of detection.
It’s well documented that modern phishing attacks use a wide and ever-expanding range of detection evasion techniques — from implementing legitimate bot protection technologies to prevent analysis, to only loading pages if the correct parameters are met — such as coming through a specific URL redirect path, and adhering to “normal” browser configs (excluding unusual browser window sizes and the presence of security analysis tools).
In this case, the malicious payload will only trigger in the event that the delivery is approved by an operator in real time. This means that anyone attempting to find and proactively block a phishing page based on indicators of known-bad is going to have a tough time finding and flagging them. If you haven’t got a community of security analysts sharing and tagging samples of malicious pages, it makes it really hard to find and block them at scale before they hit a victim. And if these convincing attacks aren’t being reported, they’re even less likely to be investigated. This is what we mean when we say that most phishing attacks today are effectively zero-day.
In this case, it’s worth pointing out that the phone call is essentially the delivery vector for the phishing page. This means there’s no email to intercept and analyse. This isn’t new — non-email vectors now account for more than 1 in 3 phishing attacks intercepted by Push, LinkedIn and Google Search being the top culprits. This effectively cuts out the primary phishing detection surface for most organizations.
All this means that unless you’re able to detect and block these attacks in real time, organizations will find themselves unable to counter this evolving threat.
The best/only way to do that is to be in the browser.
How Push stops the attack
As a browser-based detection and response tool, Push is perfectly positioned to detect and block attacks like this in real-time.
Push harnesses deep browser telemetry to detect and block phishing based on behaviors, not static indicators. By analyzing how phishing pages behave and how users interact with them, Push uncovers fake pages, attempted credential theft, and phishing kits the moment they load in the browser — regardless of the delivery mechanism, and even when the attack has never been seen before.
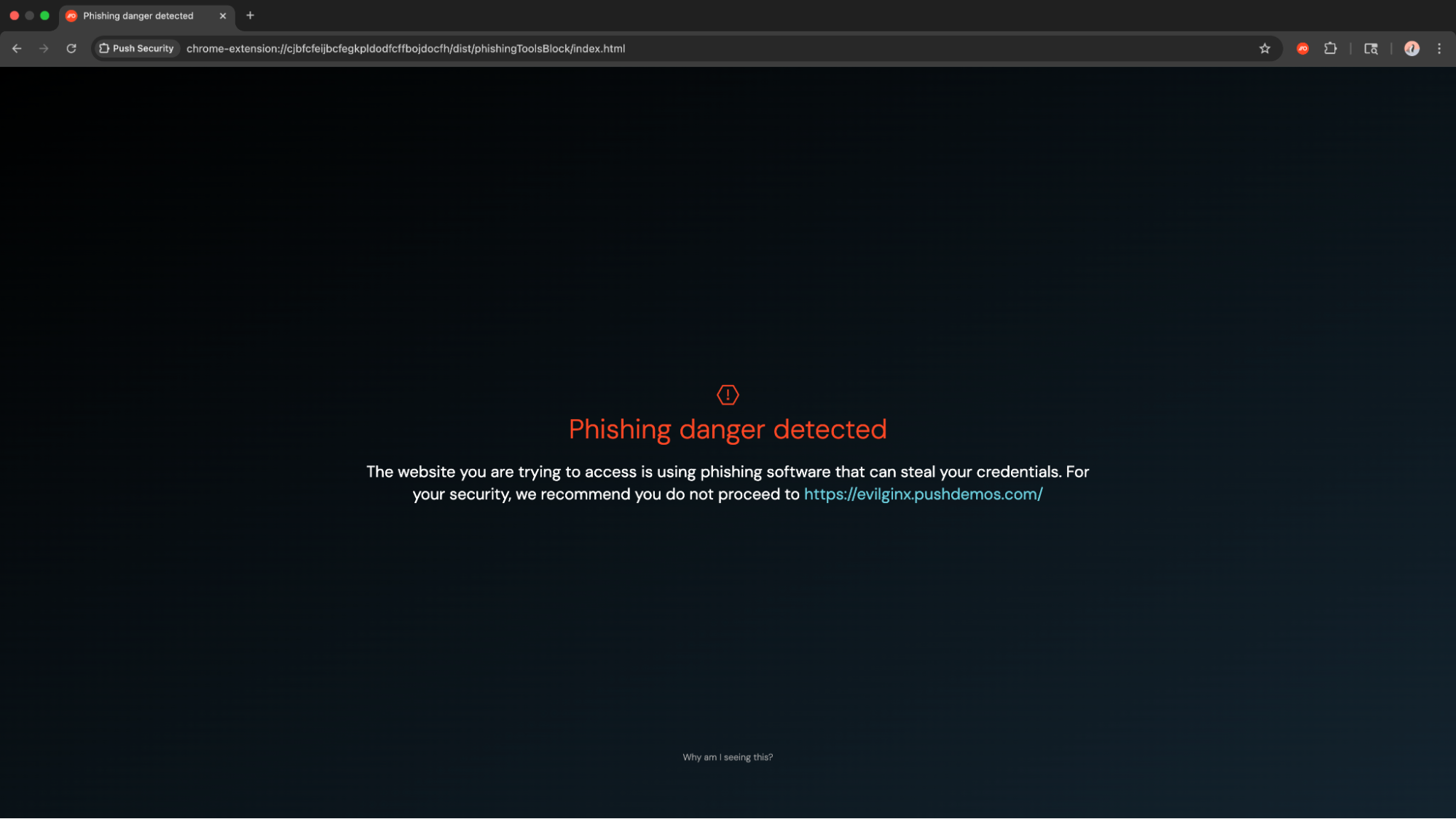
This even includes brand new techniques that have never been seen in the wild — such as ConsentFix, which we blocked the first time it was seen targeting our customers, before even realizing it was a new kind of attack.
Push's browser-based controls include:
Fingerprinting high-risk app passwords so they can only be used on a specific domain. Any attempt to reuse this password elsewhere (such as on a phishing site) results in the attempt being blocked.
Multiple browser-based checks looking for indicators of bad, such as cloned elements from legitimate websites, and an ever-growing number of detections relating to phishing kit behaviors and attributes as they are rendered on a page.
Because Push observes every login made in the browser, you can also use Push to find identities susceptible to phishing attacks, such as those not using phishing-resistant authentication methods (e.g. passkeys), to proactively improve your account hygiene and reduce your attack surface.
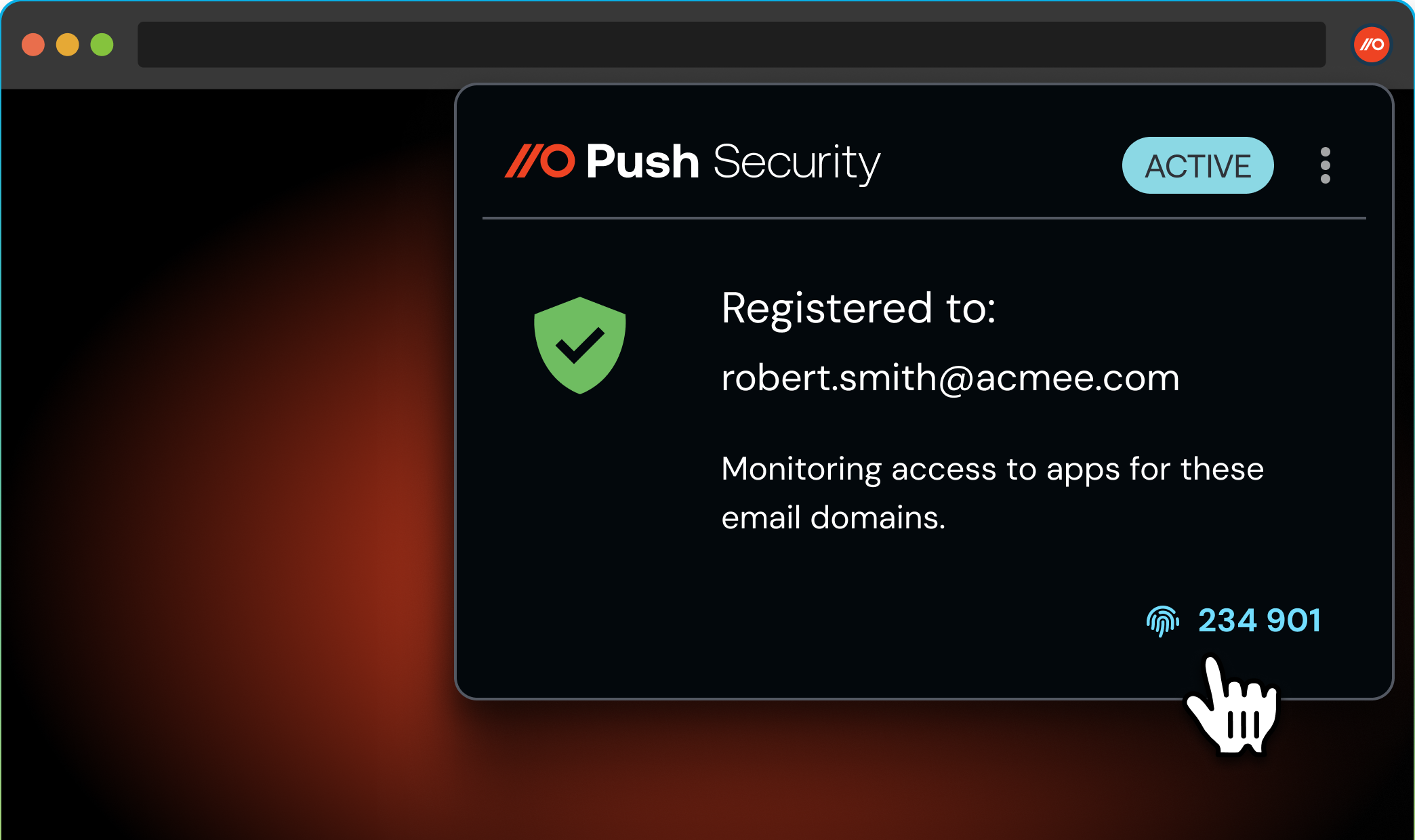
Finally, you can also use our employee verification codes feature as part of a layered defense — a simple, browser-based identity check that gives your employees a reliable way to confirm they’re talking to another employee from your organization. It enables employees to quickly verify that a caller is who they say they are by relaying a rotating 6-digit verification code displayed in every employee's browser via the Push extension. This is an effective way of combating help desk scams too — another favorite of SLH.
Want to learn more about Push? Check out our latest product overview, visit our demo library, or book some time with one of our team for a live demo.

