Streamline investigations with our new Detections page, enforce strong passwords in the browser, and more
Streamline investigations with our new Detections page, enforce strong passwords in the browser, and more
What's new this month:
Streamline investigations with Detections page
New Labs feature: Employee verification codes
Enforce strong passwords with in-browser guardrails
Merge related employee records
Customize your webhook events
Create rules for phishing tool detection and MFA enforcement
New integration for Microsoft Sentinel
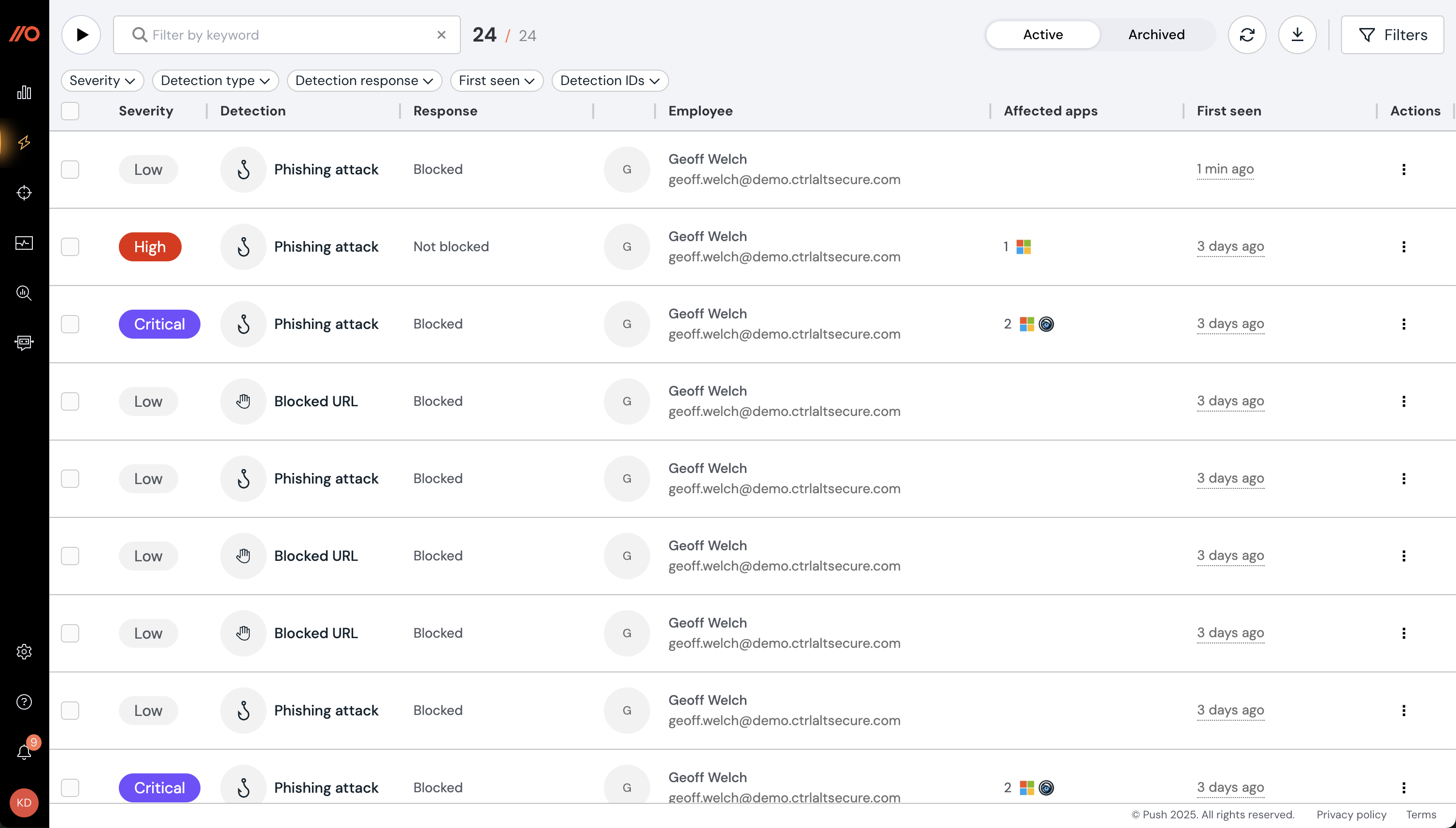
Streamline investigations with Detections page
You can now receive and triage detections in the Push admin console (or get them via the Push REST API, webhooks or ChatOps), giving you a single view of all the security events that Push has detected, such as AiTM phishing, stolen creds, or blocked URLs being visited by employees.
Use the additional telemetry about each detection, such as timestamp, detection URL, type of phishkit detected, Push response action, etc., to understand how to triage the incident.
New Labs feature: Employee verification codes
Employees can now get a 6-digit verification code via the Push browser extension that you can use to validate that your help desk is speaking to someone from your organization.
The verification code is the same for all employees at a given organization, and resets every 24 hours. If your help desk needs to verify that they’re speaking to an employee, they can ask them to open the details tray for their Push extension and verify the code.
Employee verification codes is a Labs feature, which means it’s available on an early-access basis and we're particularly interested in hearing from you if this is a problem you're interested in solving using Push.
You can enable Labs features by going to the Settings page of the Push admin console and choosing the Labs tab.

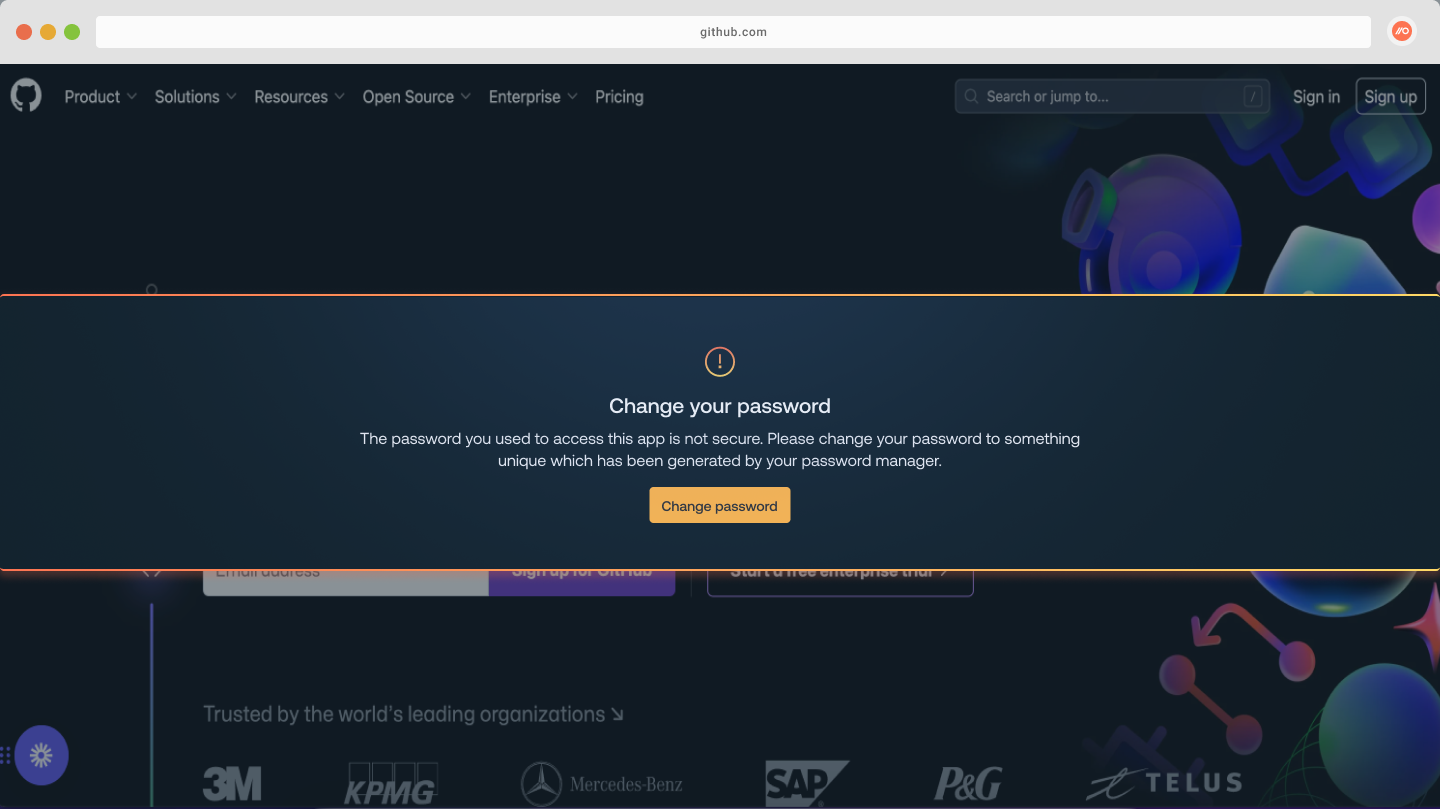
Enforce strong passwords with in-browser guardrails
Prompt your employees to change an insecure password using Push’s new in-browser guardrail, Strong password enforcement.
You can select which password security issues you want to remediate, and which apps you want to target using the configuration rules for this control. Then, when Push observes a password issue, it will automatically display a banner to end-users prompting them to change their password.
Merge related employee records
If you have employees using multiple email addresses, you can now merge those records in the Push platform so they can be treated as a single employee.
A common use case for merging employee records is when you have employees with a user account and an administrator account. By merging records in cases like this, you can resolve incorrect shared account findings and correct your license usage so only the primary employee record consumes a license.
You can also merge records programmatically via the Push REST API. This is helpful if you have a predictable pattern for usernames you're mapping.

Customize your webhook events
You can now select which events you want when creating a webhook in the Push platform. For example, if you want to build an automation around specific Push events or send only Push detection alerts to your SIEM, you can elect to send just those events to your configured destinations.
You can select which events you want to consume when configuring a new webhook via the Push admin console.

Create rules for phishing tool detection and MFA enforcement
We’re continuing to add configuration rule capabilities to security controls in the Push platform, including for phishing tool detection and MFA enforcement.
With these config rules, you can scope a control to specific employees or employee groups, and carve out exemptions if you like. You can also set the control to apply to specific apps, or set the Mode (e.g. Monitor, Warn, or Block), where applicable.

New integration for Microsoft Sentinel
Push now offers a Microsoft Sentinel integration to make it easier to send Push data to your Sentinel SIEM. You can start setting up your integration by going to Settings > Integrations in the Push admin console and selecting the Sentinel tile.

