Our latest development sprint focused on providing important context on the unique telemetry provided by the Push platform; expanding core functionality for both security controls and app management; and adding Arc to our list of supported browsers, so you can continue to deploy Push anywhere your employees like to work.
Our latest development sprint focused on providing important context on the unique telemetry provided by the Push platform; expanding core functionality for both security controls and app management; and adding Arc to our list of supported browsers, so you can continue to deploy Push anywhere your employees like to work.
What’s new this month:
New Events page
Arc browser support
Warn and block modes for phishing tool detection
Admin audit events now available
Add custom labels to apps
Improved Browsers page
Get a snapshot of your Push activity with Events
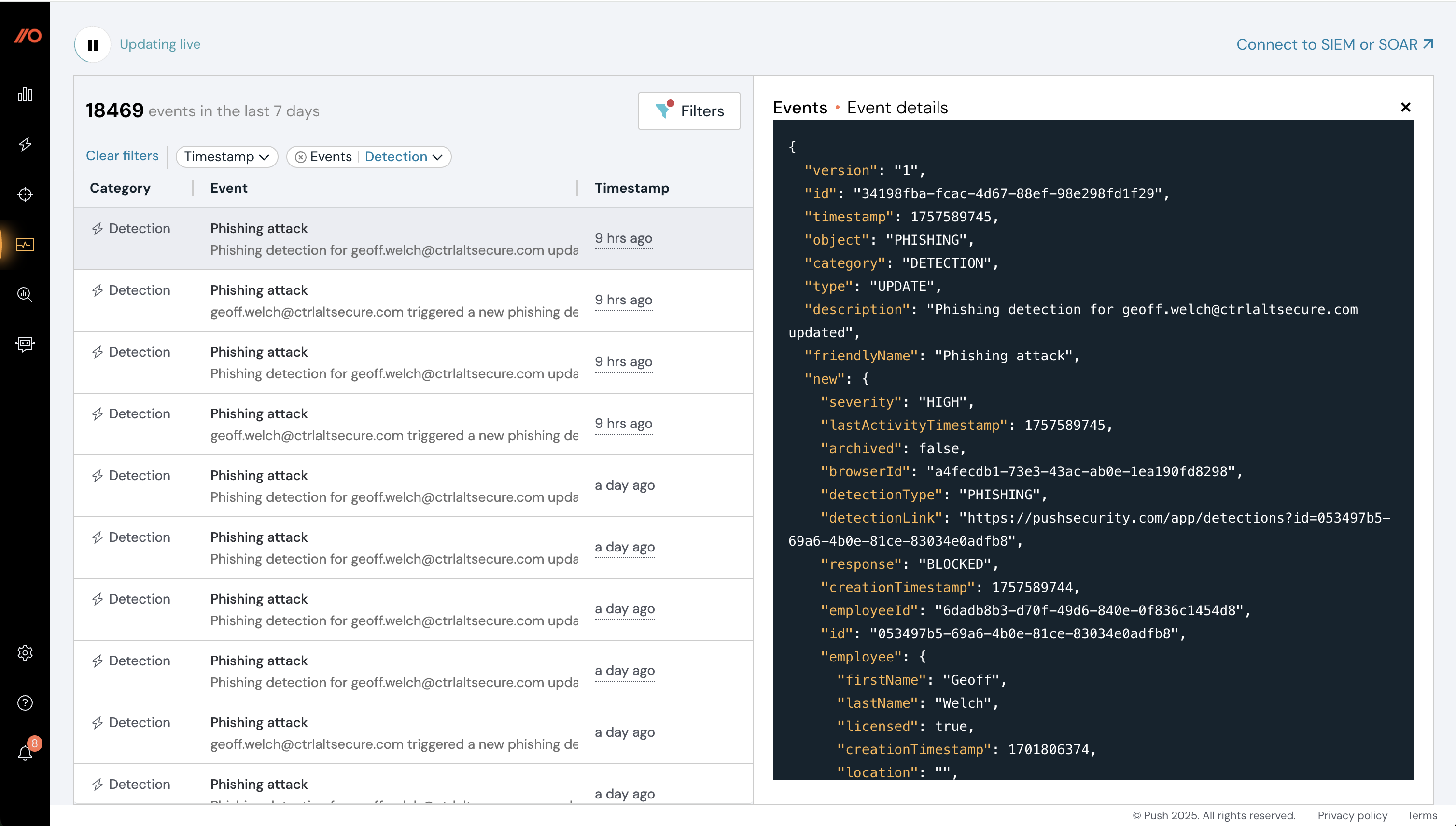
To help you visualize and plan how you can use Push telemetry, we now provide an Events page in the Push admin console. It shows a rolling 7-day snapshot of all the events in your environment, including security controls being activated, new apps being discovered, and more.
Click on an event to see its attributes and then ingest this data into your SIEM or other platform to create your own custom detections or automations.
Push now supports Arc browser
In keeping with our philosophy of securing users wherever they like to work, we’ve added support for the increasingly popular Arc browser. You can now install the Push browser agent on Arc, and do a managed deployment to Arc on macOS using your MDM. (Push already supports all major browsers. You can find the list in our Help Center.)
Are there other browsers you’d like Push to support? Let us know!
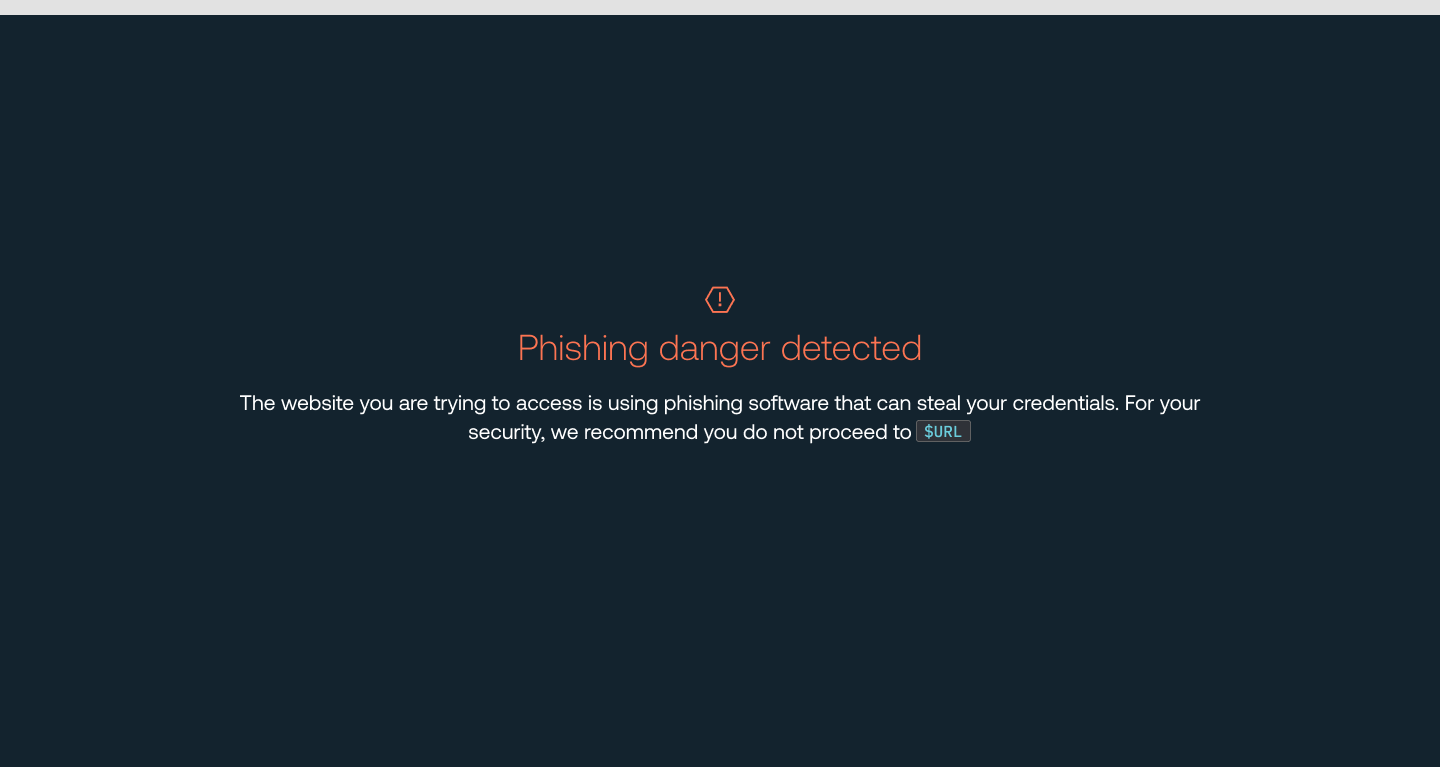
Warn or block users when Push detects phishing toolkits
You can now set a Warn or Block mode on Push’s Phishing toolkit detection feature. Phishing toolkit detection identifies when employees visit webpages that use advanced phishing tools such as Evilginx, EvilNoVNC, and others. These adversary-in-the-middle (AitM) tools can mimic legitimate login screens, such as an Okta login page, to steal credentials and MFA codes.
When you configure a Warn or Block mode for this control, you can add your custom message to end-users on the warn/block page. Then get alerted to positive detections using Push’s webhook events.
Stay on top of admin actions
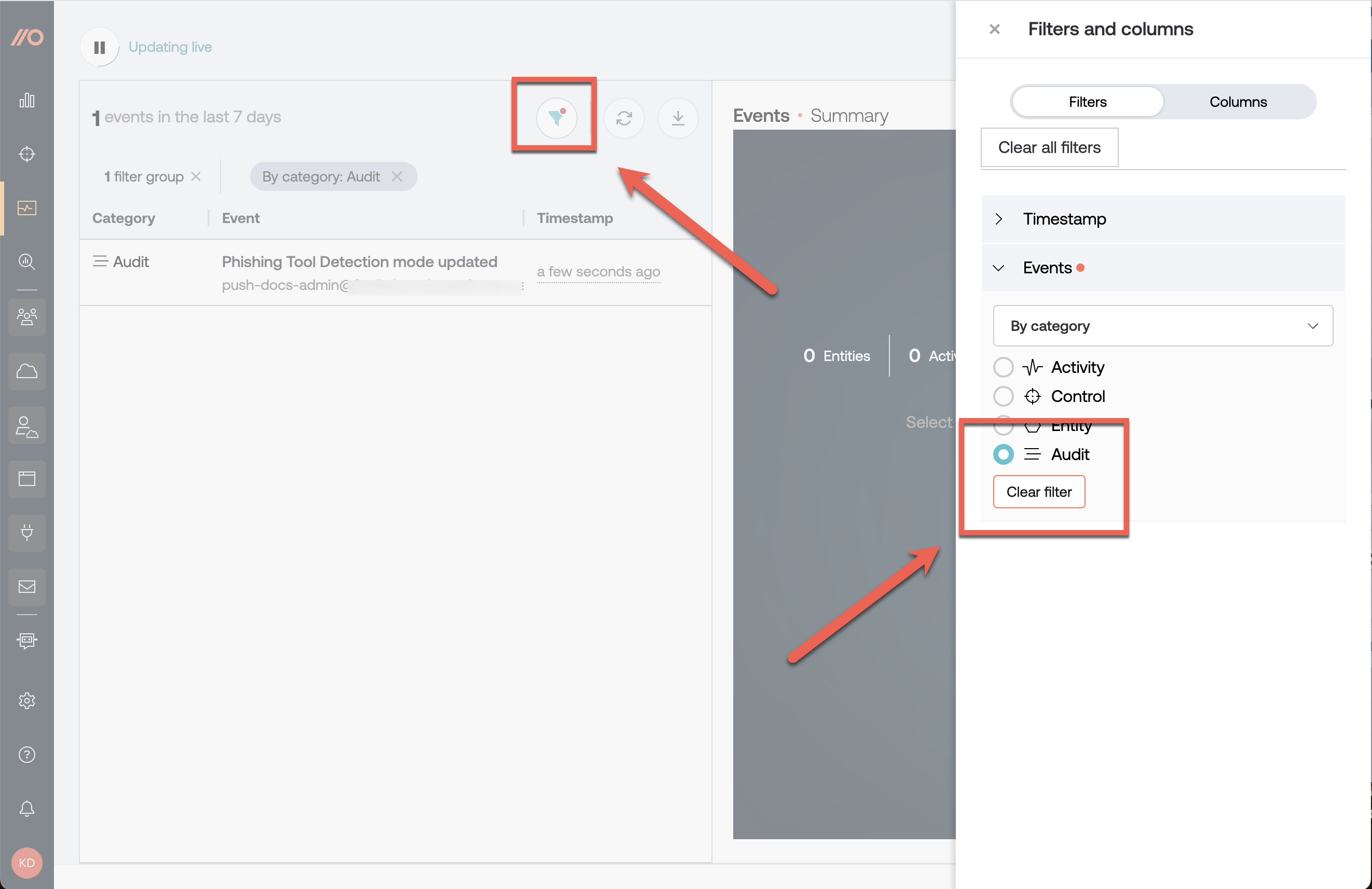
We recently added events for administrative actions on the Push platform, so you can get visibility when admins assign or remove licenses, configure security controls, or add or remove API keys, among other actions.
You’ll see admin events show up on the Events page in the admin console. Send these events to your SIEM or other system to create custom alerts.
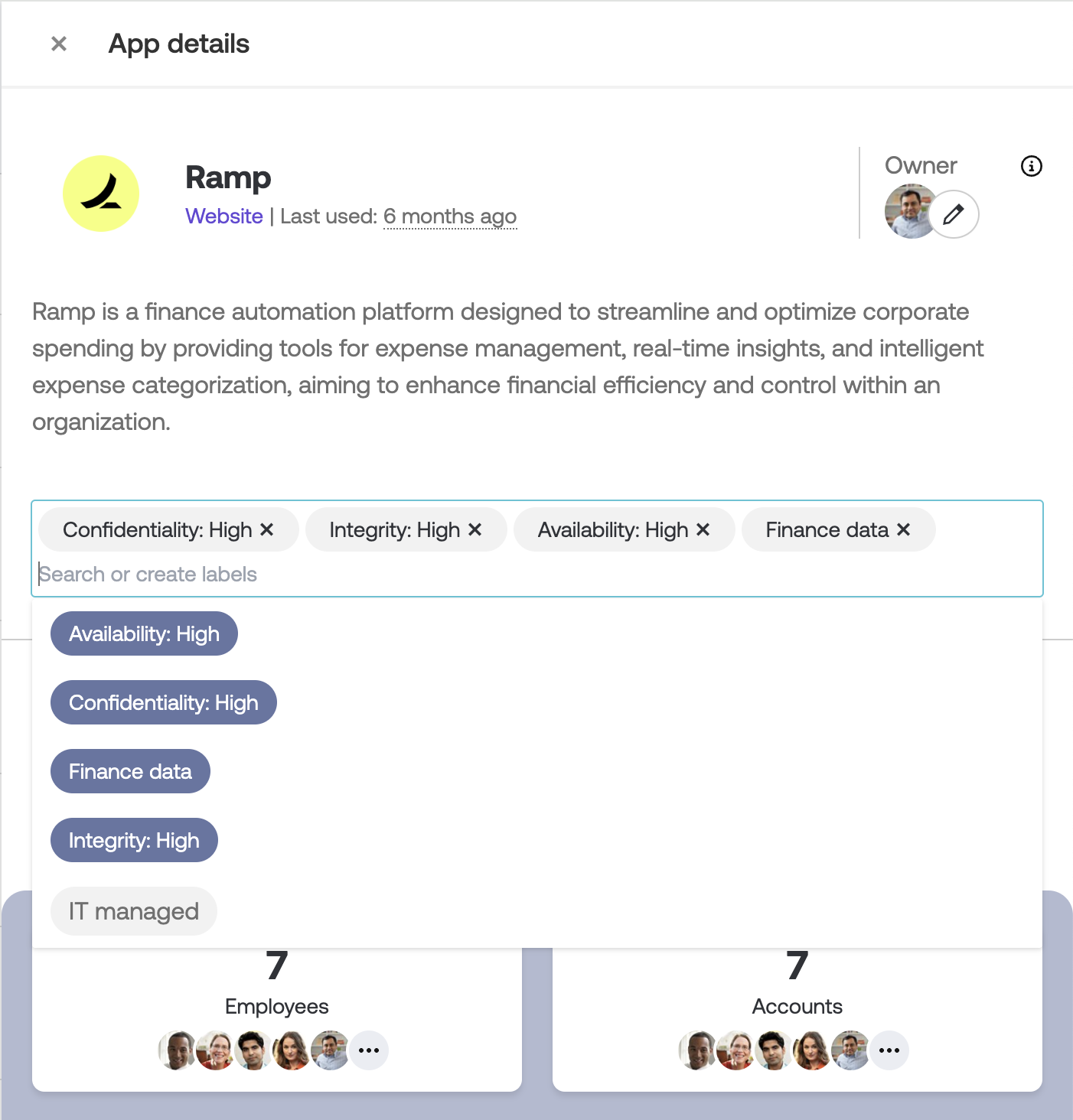
Custom labels to organize your app inventory
Create your own custom labels and apply them to apps in your inventory using our new Labels feature. This feature has been a popular request from customers, and we’re excited to get it into your hands.
A few ideas on how you might want to use app labels: To designate what kind of data is stored in an app; to note the confidentiality, integrity, and availability status of an app; to capture whether an app is IT-managed, or anything else you can think of!
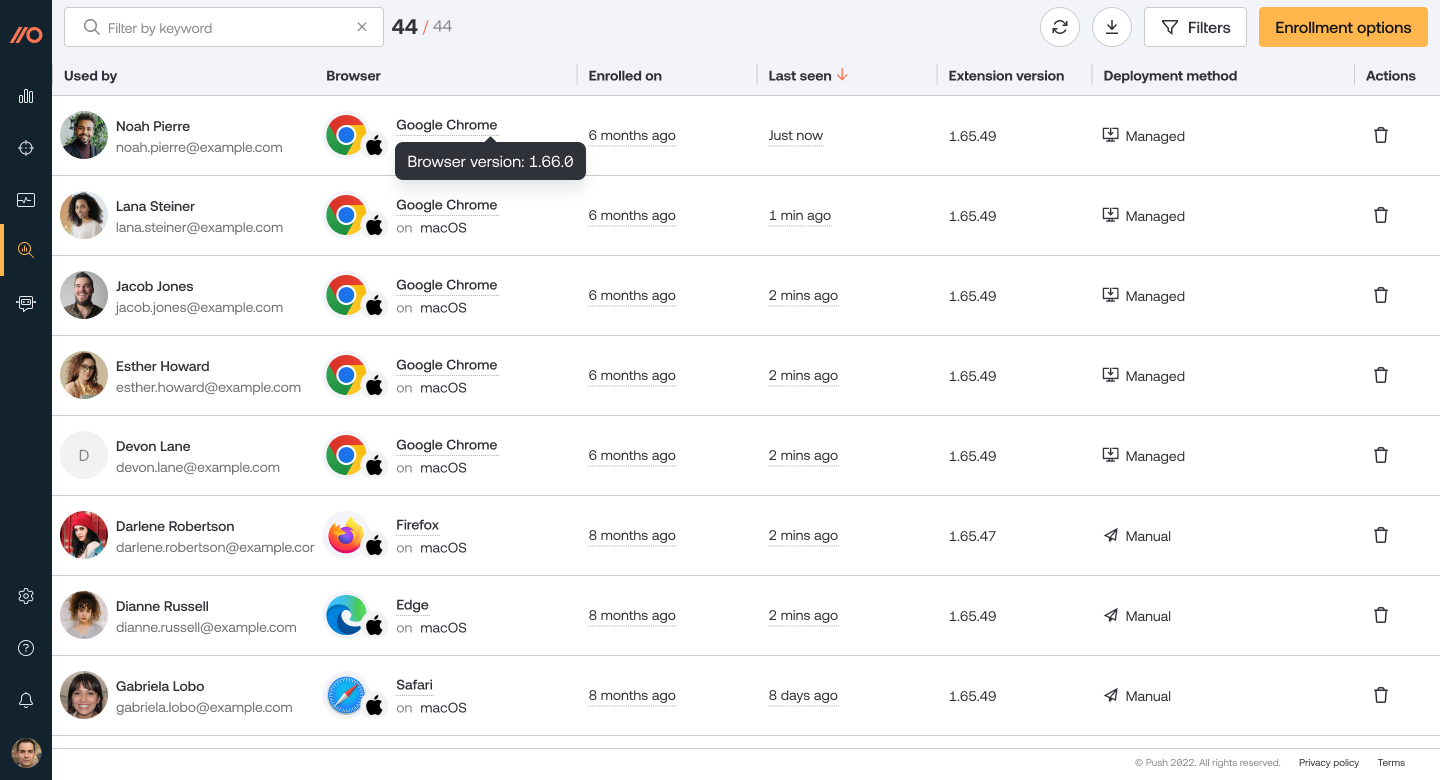
Redesigned Browsers page
We’ve updated the Browsers page in the admin console to make it possible to filter and export the data, as well as to help you better extract useful information about enrolled browsers, such as their extension version, first and last check-in dates, and browser types.
This page also now appears as a data table, similar to the other pages in the Investigate section of the platform.