We’ve published our latest resource for security teams breaking down the techniques that modern phishing attacks are using to evade detection.
We’ve published our latest resource for security teams breaking down the techniques that modern phishing attacks are using to evade detection.
Almost two years ago, we released our SaaS attacks matrix on GitHub. At the time, our research into modern attack patterns showed us that attackers were increasingly relying on cloud-native techniques, taking advantage of the shift in business IT from traditional on-premise networks to a web of third-party services accessed over the internet.
As part of our work in maintaining and updating the SaaS attacks matrix in line with our own research and attacks in the wild, we identified that:
The fastest growing category since day 1 has been initial access, which is entirely driven by identity-based techniques (i.e. logging into apps).
Phishing in various forms is the most widely used, and generally effective, of all the initial access techniques we encounter.
It’s increasingly difficult to reflect a lot of the research we’re doing within the parameters of the SaaS attacks matrix when attackers are doing so much (and to varying levels) in how they architect their phishing sites, distribute links and lures, and find novel ways around authentication and access controls.
Equally, while there’s a huge amount of valuable research and deep-dive analysis of how individual phishing kits are behaving produced by security firms, there’s a gap in how we’re bringing together this knowledge and understanding the broad strokes of why and how phishing attacks are still so successful.
We come across so many phishing attacks on a daily basis that it’s impossible to write a deep-dive teardown on every one — and to some extent it wouldn’t be useful to do so. What’s arguably more valuable is understanding the patterns and commonalities across phishing campaigns that can help us to understand, generally, how malicious tooling and tradecraft is evolving.
So, we decided to create a new resource giving phishing the space to breathe that it deserves.
How phishing has evolved
It’s easy to write off phishing as unsophisticated and simplistic, particularly when we think back to the first generation of phishing attacks — static HTML pages purely designed to steal your username and password, linked directly from an email.
Modern phishing has changed a lot in the past decade or so. MFA-bypassing Attacker-in-the-Middle (AitM) kits are table stakes — anyone can pick up a copy of Evilginx and immediately blow past most email and network security solutions on the market.
But the most sophisticated attacks — the ones that usually hit the headlines in the form of major breaches — are doing much more than this. The latest generation of fully customized AitM phishing kits are dynamically obfuscating the code that loads the web page, implementing bot protection through custom CAPTCHA, and using runtime anti-analysis features, making them increasingly difficult to detect by the tools most enterprises are using to combat the problem.
The techniques used by attackers to deliver phishing lures are also more sophisticated. Groups like Scattered Spider have been seen using malvertising techniques, delivering phishing links via paid Google ads, while phishing campaigns are frequently encountered in IM apps (such as Slack and Teams), as well as public messaging services like LinkedIn messenger and Reddit — bypassing email altogether.
The latest trends indicate that attackers are responding to increasingly hardened IdP/SSO configuration by using alternative phishing techniques that circumvent MFA and passkeys, either by downgrading to a backup (less secure) authentication method, or sidestepping the legitimate auth process entirely through methods like consent phishing.
Attackers have also realized how much valuable data exists in Shadow SaaS highlighted by major SaaS breaches impacting apps like Snowflake. This is driving broader targeting against apps like Slack, Mailchimp, Postman, GitHub, and other commonly-used business apps directly — bypassing IdPs (MS, Google, Okta, etc.) that typically have more robust authentication controls in place.
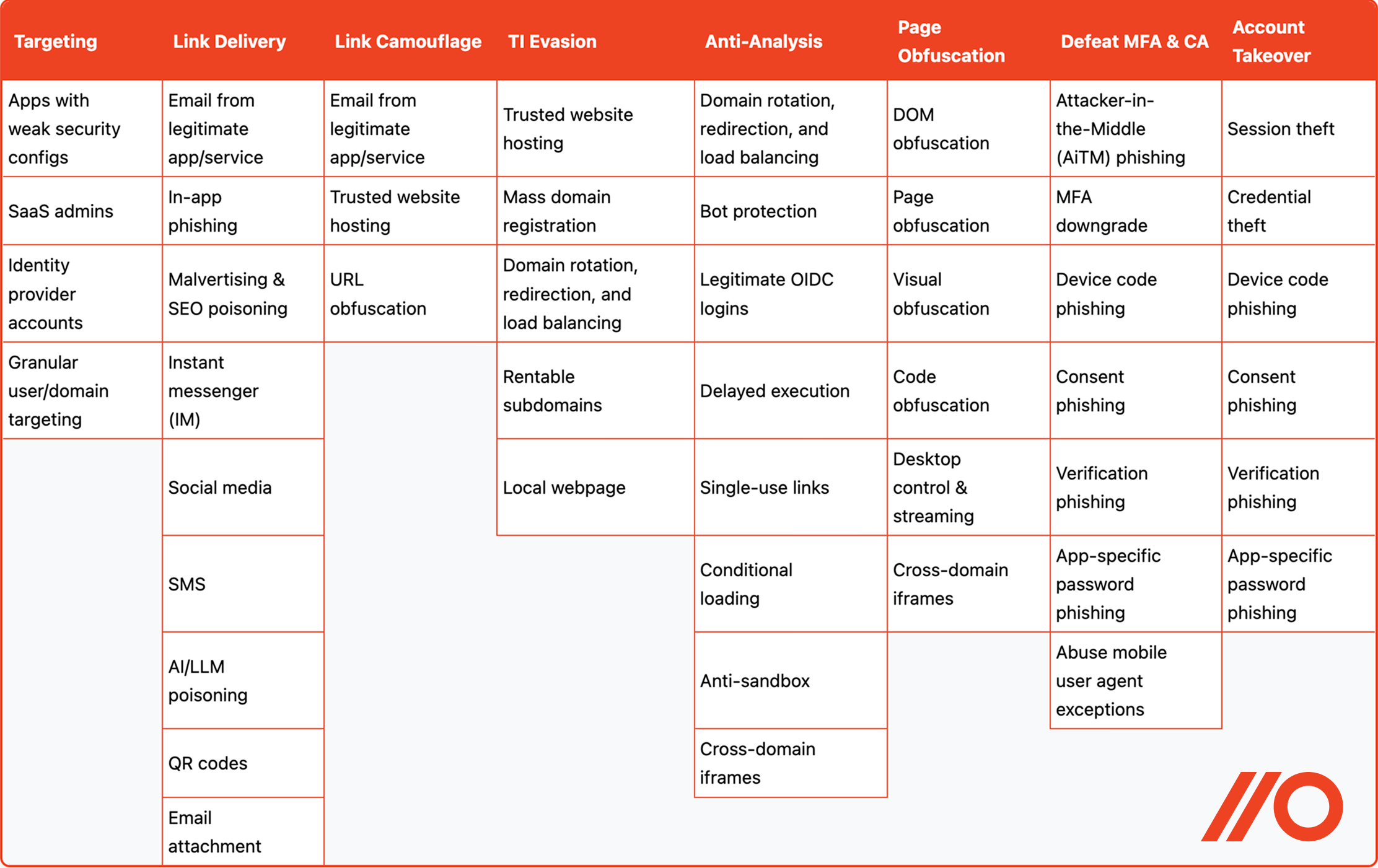
Using the phishing detection evasion techniques matrix
With so much attacker innovation happening in the phishing space, it’s tricky for security teams and solution vendors to have a big picture view of the subtle changes attackers are making to their phishing attacks, and precisely why they’re doing it — or more specifically, which detection techniques they’re evading.
If you look at one of the many phishing kit teardowns found in security blogs online (including our own) it can be hard to see the wood for the trees when it comes to understanding why a phishing page behaves in the way it does — why is it behaving in this way? What control exactly is this trying to get around?
By creating a simple framework breaking down the categories of a phishing attack into phases, each with its own specific attacker objective, we can better understand phishing kit behavior and track meaningful changes over time. This ensures that we understand how we need to adapt to as an industry in order to detect and block these attacks.
The matrix covers the following categories:
Phase 1: Targeting — Identifying apps and users to evade security controls and achieve the shortest time-to-impact of a phishing attack.
Phase 2: Link delivery — Deliver links using phishing vectors that evade traditional security controls.
Phase 3: Link camouflage — Masking malicious links to prevent detection at the email, network proxy, or safe browsing layer.
Phase 4: TI evasion — Preventing TI feeds from flagging and blocking known-bad domains by masking or changing elements likely to be flagged.
Phase 5: Anti-analysis — Techniques to defeat automated “sandbox” analysis tools by preventing security teams and bots from accessing the page.
Phase 6: Page obfuscation — Obfuscating page elements to break detection signatures analysing page content and code.
Phase 7: Defeat MFA & CA — Defeat authentication and access controls in order to successfully execute the phishing attack.
Phase 8: Account takeover — Achieve a form of account takeover and conclude the identity attack, enabling further exploitation to take place.
Combining techniques and approaches from these categories is what enables attackers to bypass the majority of phishing detection controls they encounter today. You typically find that the more advanced the phishing kit / attacker, the more techniques they’ll leverage. And as phishing infrastructure becomes increasingly templated and commodified with as-a-Service or for-hire models, the average phishing attack will employ more of these measures to counter security controls.
Learn more
If you want to learn more about the research that led us to this point, and our take on how and why phishing attacks have evolved, you can also check out our latest whitepaper.
Get involved!
Like the SaaS attack matrix, we’d love to see the security community using and helping us to maintain this resource to ensure it stays up to date with techniques as they evolve.
Unlike the SaaS matrix, which we’ve seen mostly leveraged by offensive security practitioners, phishing detection evasion techniques are most useful to blue teamers looking to assess current detection capabilities and understand why certain attacks got through existing defenses.
If you’d like to add techniques you’ve observed or examples that you think demonstrate them, get involved on GitHub!



