Attackers are increasingly sending phishing lures via non-email delivery channels like social media, instant messaging apps, and search engines. In this article, we’re diving into the latest sophisticated LinkedIn phishing campaign intercepted by Push.
Attackers are increasingly sending phishing lures via non-email delivery channels like social media, instant messaging apps, and search engines. In this article, we’re diving into the latest sophisticated LinkedIn phishing campaign intercepted by Push.
Push recently detected and blocked a high-risk LinkedIn phishing attack that demonstrated a number of crafty (and increasingly common) detection evasion techniques.
Phishing via LinkedIn is increasingly common, although it often goes undetected and unreported. This is to be expected when most of the industry’s data on phishing attacks comes from email security vendors and tools. In contrast to email-centric reporting, 34% of the phishing attacks intercepted by Push last month came through non-email channels like social media, IM platforms, malicious search engine ads, and in-app communications.
This is the second blog post we’ve released on LinkedIn-based phishing attacks — read our last report to learn about a sophisticated spear-phishing campaign targeting tech company executives.
Phishing via LinkedIn is a great way to catch victims unawares and evade traditionally email-based anti-phishing controls. While often used for work and commonly accessed from corporate devices, it sits outside the purview of enterprise security tools, exploiting a visibility and control blind spot.
Let’s break it down.
Phishing attack breakdown
The victim was sent a malicious link via LinkedIn DM relating to a fake investment opportunity for executives to join the executive board of a newly created "Common Wealth" investment fund.
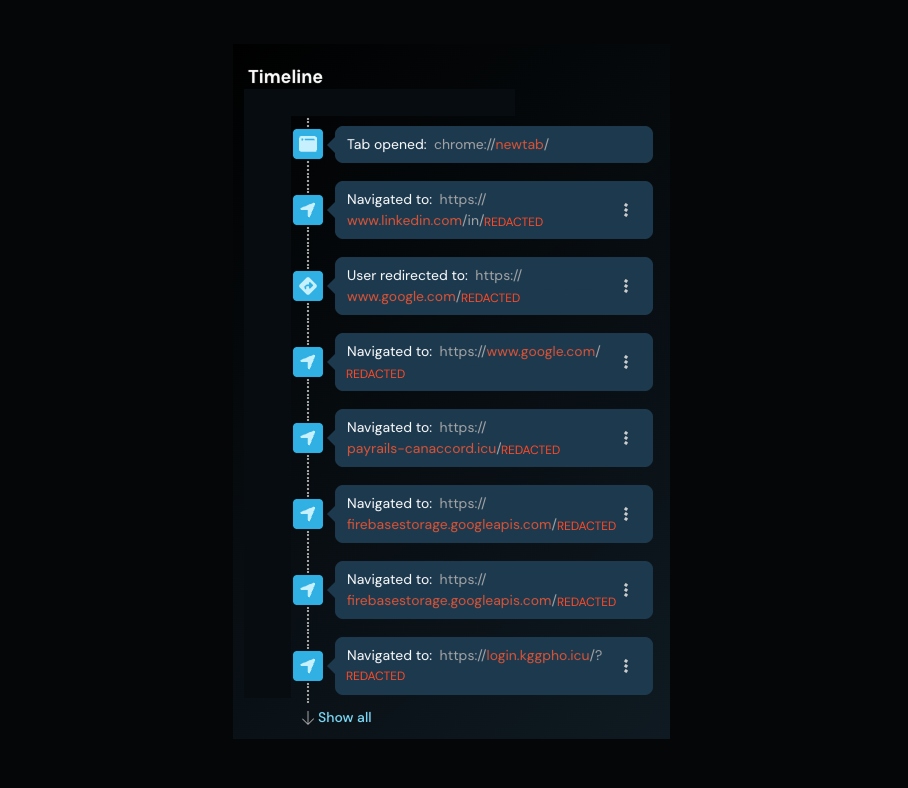
After clicking the link, they were redirected three times — via Google Search, and then payrails-canaccord[.]icu/(redacted) — before being sent to a custom landing page hosted on firebasestorage.googleapis[.]com/(redacted).
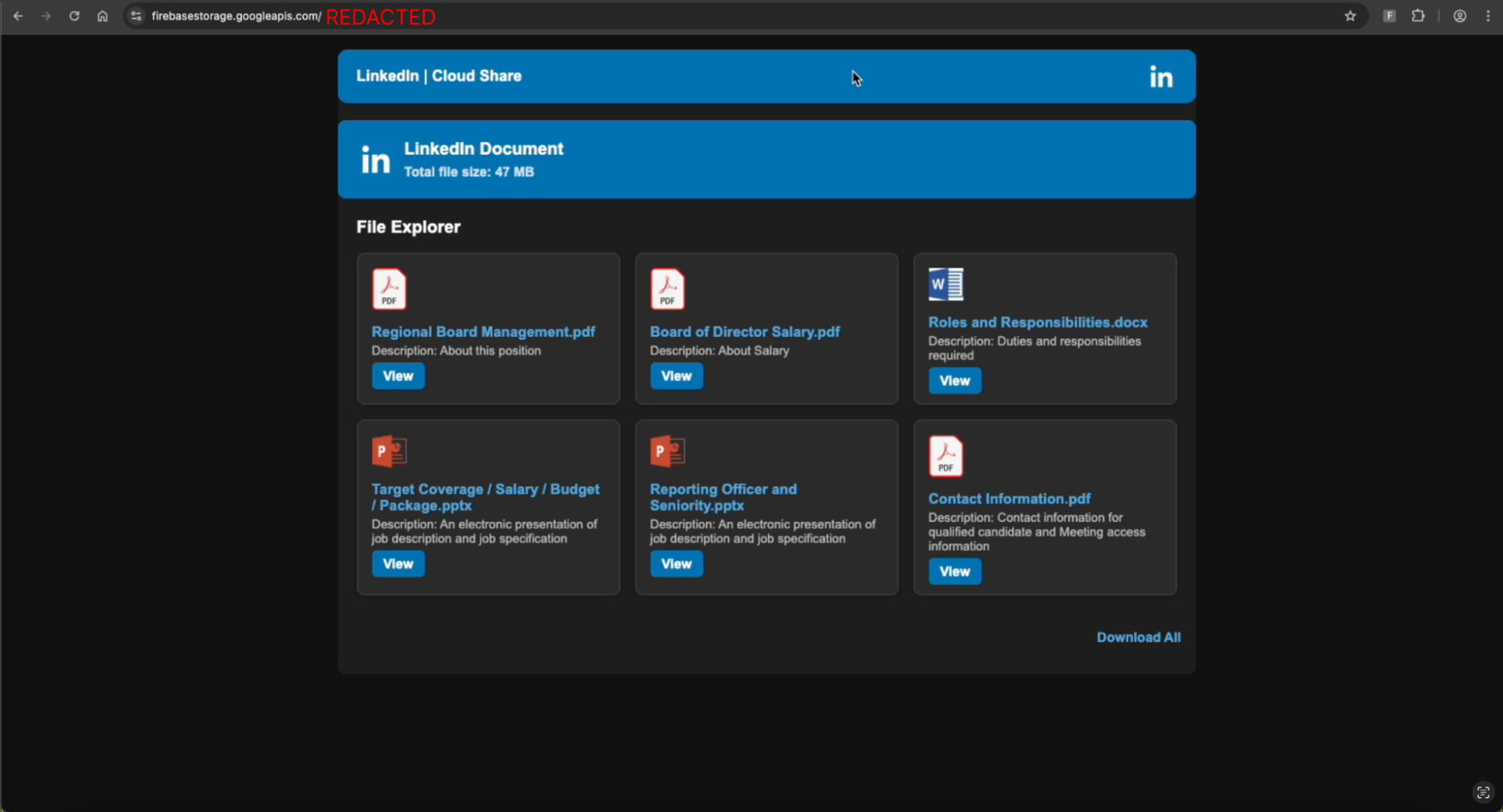
Upon clicking on one of the document links on the page, the victim is prompted to “view with Microsoft”.
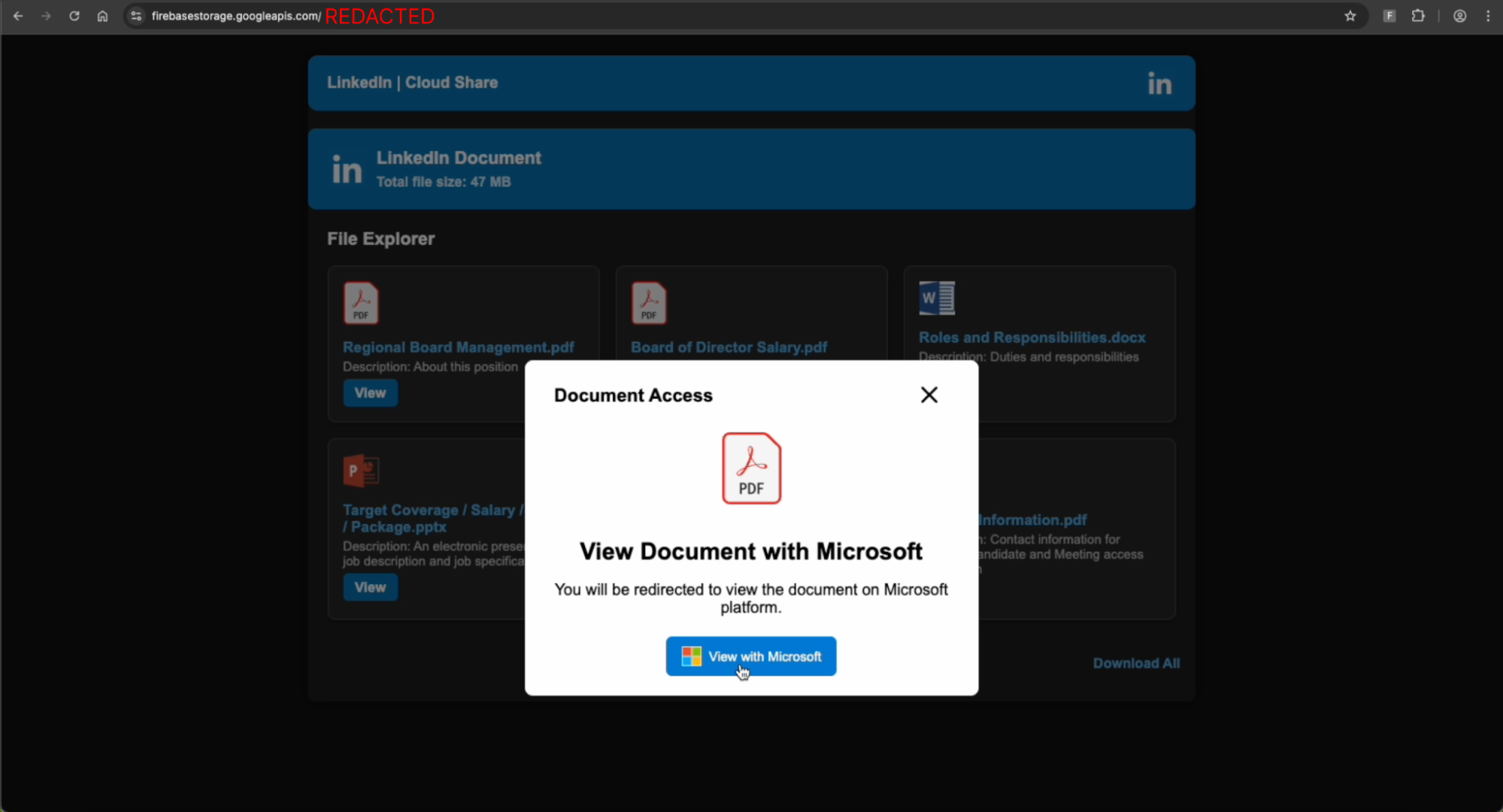
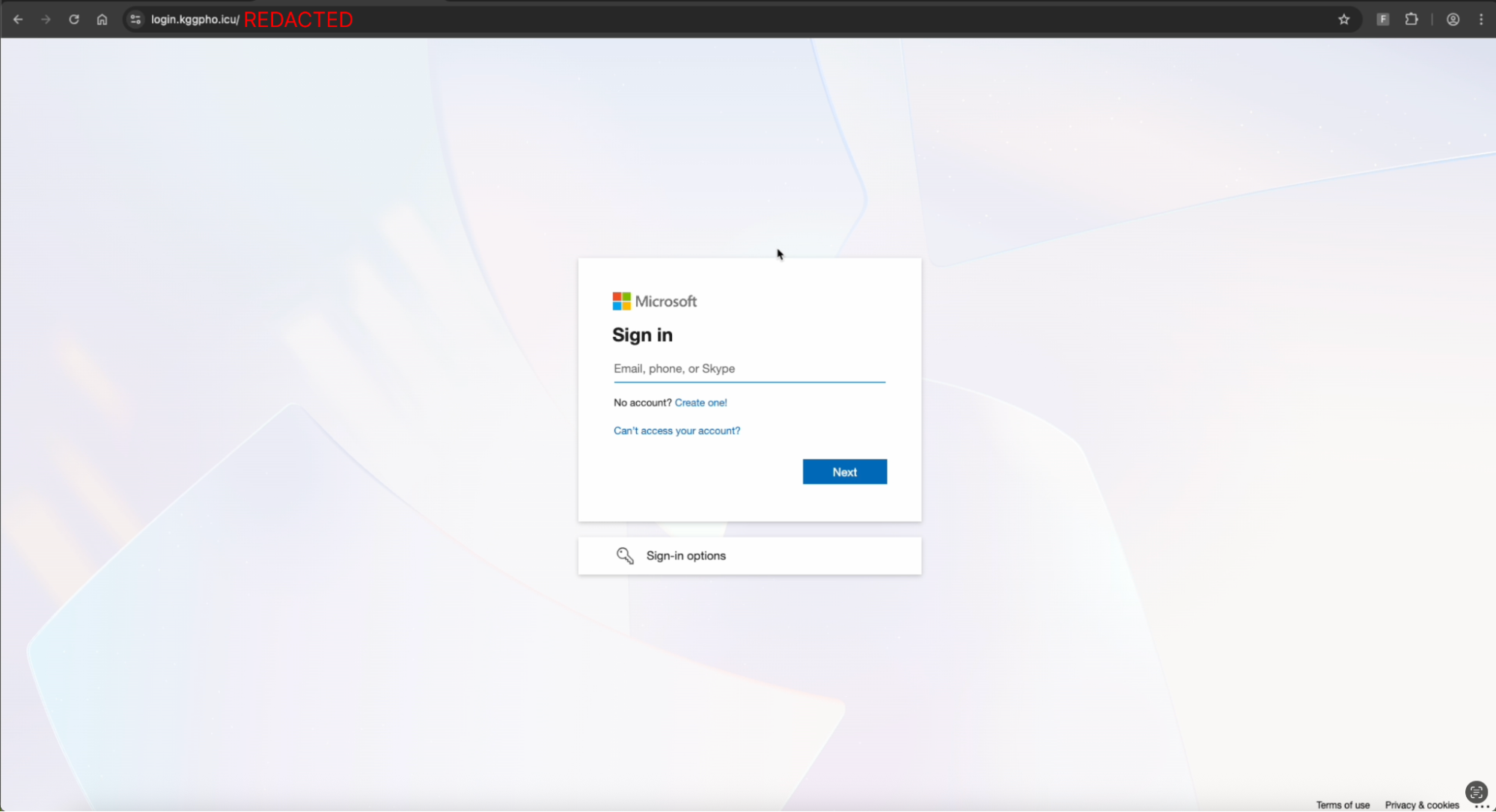
The user is then met with a Cloudflare Turnstile gate challenge at login.kggpho[.]icu before the page will fully render, and malicious content is loaded.

The Microsoft-impersonating AITM phishing page is then served to the victim. Entering credentials and completing the MFA check will result in their Microsoft session being stolen by the attacker.
You can see the full timeline of events in the Detection Timeline below.
Detection evasion techniques observed
The attacker used a number of detection evasion techniques to prevent the phishing site being analysed and detected by security tools.
Learn more about phishing detection evasion techniques in our recent whitepaper: The Evolution of Phishing Attacks.
LinkedIn delivery
As we mentioned above, sending phishing lures via social media apps like LinkedIn is a great way to reach employees in a place that they expect to be contacted by people outside of their organization. By evading the traditional phishing control point altogether (email) attackers significantly reduce the risk of interception.
Lengthy redirect chain through trusted sites
Attackers use lengthy redirect chains in combination with hosting pages on legitimate, trusted sites (in this case Firebase, Google’s app development platform). This is a technique we see a lot, with various Google and Microsoft sites cropping up time and again, including Google Forms, Google Sites, Google Script, Google AMP, Microsoft Dynamics, SharePoint, Azure Front Door, and many more, all used by attackers as part of their phishing attacks.
Legitimate services are less likely to be flagged by link analysis tools and effectively cloak the initial URL delivered to the victim to increase the chance of successful delivery of and access to the link, while many services are excluded from page scanning tools owing to their association with trusted domains.
Bot protection
Attackers are using common bot protection technologies like CAPTCHA and Cloudflare Turnstile to prevent security bots from accessing their web pages to be able to analyse them (and therefore block pages from being automatically flagged). This requires anyone visiting the page to pass a bot check/challenge before the page can be loaded, meaning the full page cannot be analysed by automated tools.
Page obfuscation
Phishing pages change and even randomize elements of the page to avoid static fingerprints and defeat comparison-based checks against real pages. This includes the page title, text, images, backgrounds, logos, favicons, etc. — all of which may be signatured components using web page analysis tools. These elements can even be embedded in an encoded form so it isn’t present in the initial HTML, and is instead dynamically set at runtime when loaded. As an example, you can see that the page randomly generated the tab header text.
Impact analysis
We’re seeing many phishing campaigns pivoting to social media apps like LinkedIn and organizations should be on guard against this attack vector, which is highly effective at evading common anti-phishing controls.
Just because the attack happens over LinkedIn doesn’t lessen the impact — these are corporate credentials and accounts being targeted, even if it is nominally a “personal” application. Taking over a core identity like a Microsoft or Google account can have wide-ranging consequences, putting data at risk in both core apps and any downstream apps that can be accessed via SSO from the compromised account.
How Push stopped the attack
Push doesn’t detect the redirect tricks or rely on outdated domain TI feeds. The reason we detect these attacks (which make it through all the other layers of phishing protection) is that Push sees what your users see. It doesn’t matter what delivery channel or camouflage methods are used, Push shuts the attack down in real time, as the user loads the malicious page in their web browser.
This isn’t all we do: Push’s browser-based security platform provides comprehensive detection and response capabilities against the leading cause of breaches. Push blocks browser-based attacks like AiTM phishing, credential stuffing, malicious browser extensions, malicious OAuth grants, ClickFix, and session hijacking. You don’t need to wait until it all goes wrong — you can also use Push to proactively find and fix vulnerabilities across the apps that your employees use, like ghost logins, SSO coverage gaps, MFA gaps, vulnerable passwords, and more to harden your identity attack surface.
Check out the demo below to see Push detect and block this attack in real-time.
To learn more about Push, check out our latest product overview or book some time with one of our team for a live demo.

