ClickFix, FileFix, fake CAPTCHA — whatever you call it, users interacting with malicious scripts in their web browser is a fast-growing source of security breaches. To tackle this threat, Push now detects malware delivery in the browser, supporting a layered defense against endpoint attacks.
ClickFix, FileFix, fake CAPTCHA — whatever you call it, users interacting with malicious scripts in their web browser is a fast-growing source of security breaches. To tackle this threat, Push now detects malware delivery in the browser, supporting a layered defense against endpoint attacks.
One of the biggest security trends in the past year has been the emergence of the attack technique known as ClickFix. Various reports indicate that ClickFix is fast becoming one of the most prevalent attack techniques this year, with one study reporting that email-based ClickFix attacks have increased by 400% YOY, and another highlighting a 517% increase in the past 6 months.
ClickFix is known to be regularly used by the Interlock ransomware group and other prolific threat actors. A number of recent public data breaches have been linked to ClickFix attacks as the attack vector, such as Kettering Health, DaVita, City of St. Paul, Minnesota, and the Texas Tech University Health Sciences Centers (with many more breaches likely to involve ClickFix where the attack vector wasn’t known or disclosed).
Push’s latest feature, malicious copy and paste detection, tackles ClickFix-style attacks at the earliest opportunity through browser-based detection, with a universally effective control that works regardless of the lure delivery channel, or page style and structure.
Before we get into the specifics of the feature, let’s take a look at what ClickFix is and why it poses a detection and response challenge to security teams.
ClickFix 101
ClickFix attacks prompt the user to solve some kind of problem or challenge in the browser — most commonly a CAPTCHA, but also things like fixing an error on a webpage. The name is a little misleading though — the key factor in the attack is that they trick users into running malicious commands on their device by copying malicious code from the page clipboard and running it locally. (For simplicity we’ll keep calling it ClickFix, but we’re not happy about it.)
The copy action is either performed manually by the user, or automatically by the page. Manual copies typically include additional social engineering to lure the victim into hitting CTRL+C, while automatic copies are performed using JavaScript running on the page. Most ClickFix pages we've seen are automatic copies, which makes sense — fewer steps means the user is more likely to follow the instruction.
Most commonly, these attacks are used to deliver remote access software or infostealer malware using stolen session cookies and credentials to facilitate attacks on business apps and services. From there, the attacker simply dumps the data and holds the victim to ransom for its deletion — often dropping ransomware afterwards for double the extortion.
The attack gives the victim instructions that involve clicking prompts and copying, pasting, and running commands directly in the Windows Run dialog box, Terminal, or PowerShell in order to “fix” the fake problem that they’re experiencing. Variants such as FileFix have also emerged which instead use the File Explorer Address Bar to execute OS commands.
Links to malicious ClickFix pages are distributed over various delivery channels, with attacks shifting from traditional email-based delivery to social media, instant messaging apps, malicious ads in places like Google Search, and using in-app notifications and messages across numerous SaaS services.
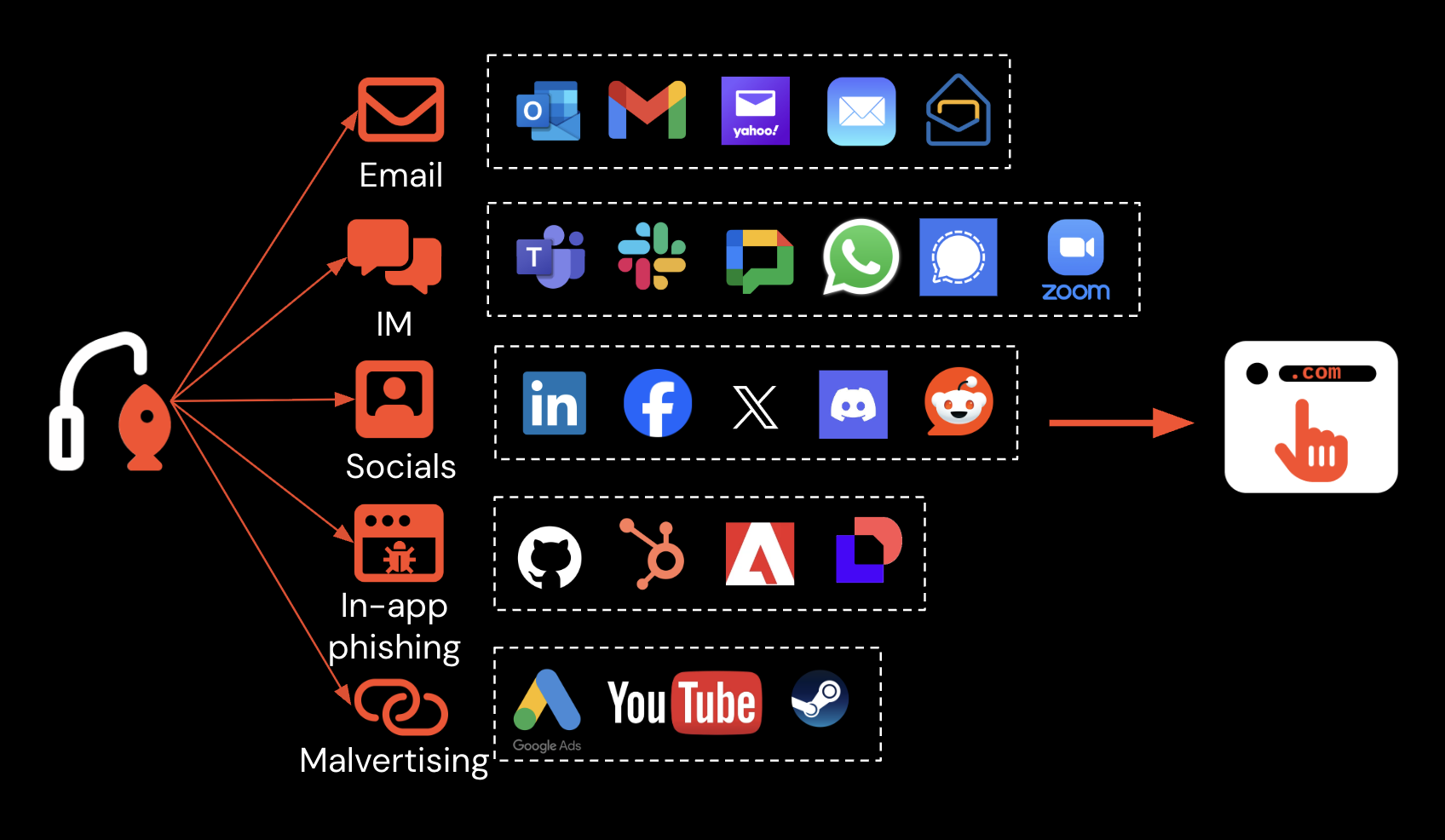
ClickFix comes in a variety of lures, including impersonating CAPTCHA, Cloudflare Turnstile, simulating an error loading a webpage, and many more. They have also been observed targeting a wide range of services to execute code.
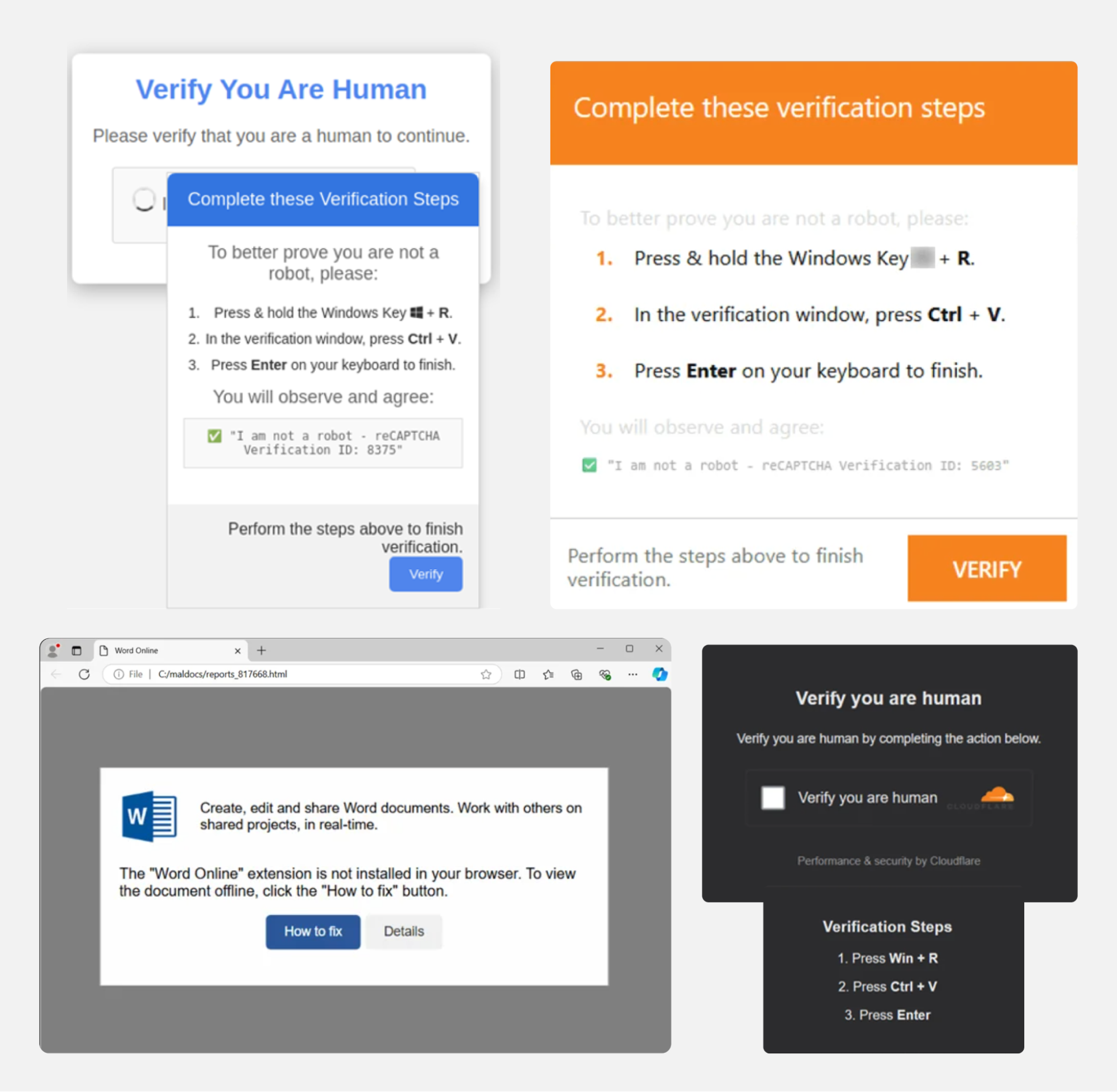
Why are ClickFix attacks so effective?
To understand the effectiveness of ClickFix-style attacks, we need to look more closely at the mechanisms that security teams have at their disposal to counter these attacks.
Detection challenges during delivery
We’ve written extensively about the evolution in phishing techniques and tooling, and what this means for the reliability of traditional detections at the network and endpoint layer.
The latest generation of phishing pages are dynamically obfuscating the code that loads the web page, implementing custom bot protection (e.g. CAPTCHA or Cloudflare Turnstile), using runtime anti-analysis features, and using legitimate SaaS and cloud services to host and deliver phishing links to cover their tracks.
This means that traditional anti-phishing tools at the email and network layer are struggling to keep up, with many attacks evading email-based detections (or bypassing email altogether). At the same time, proxy-based solutions now see a garbled mess of JavaScript code without the necessary context of what is actually happening in the browser to be able to piece it together effectively. Even if they don’t realize it, this means many organizations are now relying solely on blocking known-bad sites and hosts — a wildly ineffective solution in 2025 with the rate that attackers refresh and rotate their phishing infrastructure.
In addition to the fact that ClickFix page styles and content can vary significantly, this means that detecting ClickFix delivery using traditional tooling is highly unreliable.
Detection challenges during execution
Most of the detection heavy lifting is being done at the endpoint, looking for user-level code execution and malware running on a device.
However, the number of ClickFix-related headlines in the news would indicate that endpoint controls are being routinely bypassed, or perhaps evaded altogether by targeting personal or BYOD devices.
Attacks on BYOD or personal devices are increasingly leading to corporate breaches where email accounts are being used to sign into corporate browser profiles. This results in corporate credentials inadvertently saved and synced across devices being exposed in the breach (the most well-known example of this being in Okta’s 2023 support case management system breach).
There are a number of reasons that endpoint-level ClickFix detections can be bypassed:
The step of downloading a file from the web is bypassed altogether. In a ClickFix/FileFix attack, the initial “dropper” is essentially a command string provided by the attacker and executed by legitimate system utilities. There is often no new executable file written to disk when the user runs the command. The final payload may be loaded directly into memory or injected into trusted programs (using living-off-the-land techniques). Without a file to quarantine, there's no "Mark of the Web" to make it appear suspicious.
From the EDR’s point of view, a trusted parent process is launching a script – which might not immediately be judged as malicious, especially if the command is obfuscated or uses allowed system functions. Since the action is initiated by the user, it blends in with normal user-driven administration tasks.
The PowerShell commands themselves might be obfuscated or broken into stages to avoid easy detection by heuristic rules. EDR telemetry might record that a PowerShell process ran, but without a known bad signature or a clear policy violation, it may not flag it immediately.
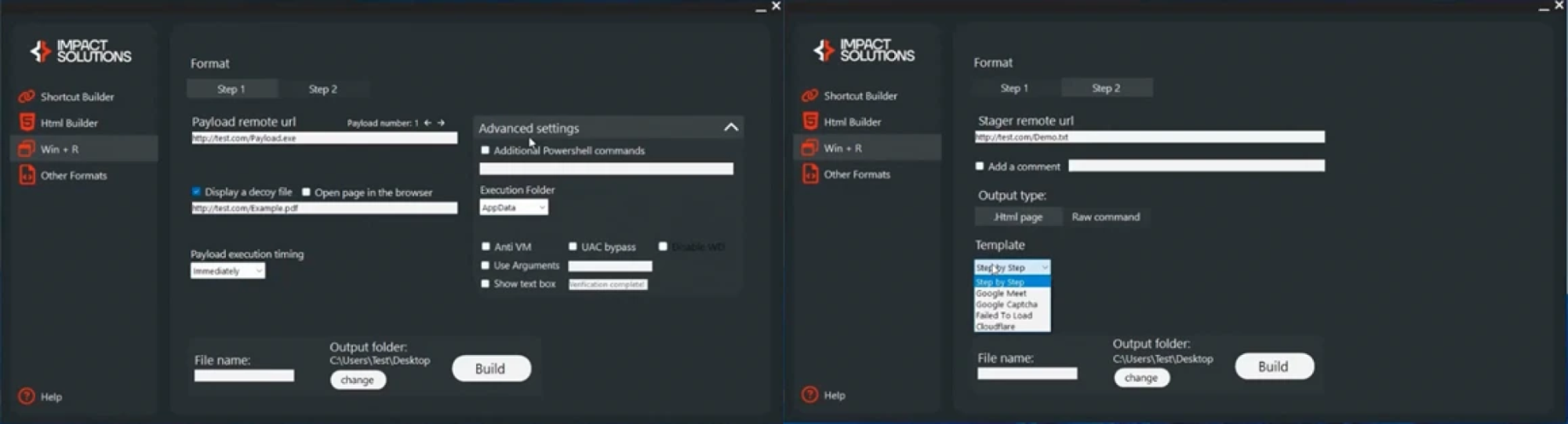
Accessing ClickFix-style capabilities is easier than ever
This capability is increasingly available to all levels of threat actor, with off-the-shelf options available in the form of ClickFix builders (also called “Win + R”) on popular hacker forums since late 2024.
Attackers are bundling ClickFix builders into their existing kits to:
Use pre-canned landing pages with various lures including Cloudflare.
Offer construction of malicious commands that users will paste into the Windows Run dialog.
These kits claim to guarantee antivirus and web protection bypass (some even promise that they can bypass Microsoft Defender SmartScreen), as well as payload persistence. The cost of subscription to such a service might be between US$200 to US$1,500 per month.
In short, these capabilities are increasingly accessible to the general population of hackers, and it is increasingly in the interests of malware developers to offer premium hacker tools designed to bypass current detections.
In any case, relying on just-in-time detection at the point of execution is increasingly unreliable and will always be at the mercy of the cat-and-mouse game between attackers and defenders. Organizations employing custom detections looking for specific malware behavior are likely to have better success than those relying on out-of-the-box EDR configs, but this requires continual maintenance to be effective.
Solving ClickFix detection in the browser with Push
Push’s latest feature, malicious copy and paste detection, tackles ClickFix-style attacks at the earliest opportunity through browser-based detection and blocking, with a universally effective control that works regardless of the lure delivery channel, page style and structure, or the specifics of the malware type and execution.
A key part of our design philosophy is to find ways to universally detect attacker TTPs by analyzing generic attacker actions that can’t be avoided by the attacker. One of our best prior examples of this is with our password protection feature, which detects and blocks phishing attacks by triggering when a user attempts to enter a password that belongs to one domain on a different domain.
In the case of ClickFix, every attack involves copying a malicious script from a page — a behavior the attacker can’t avoid.
Unlike heavy-handed DLP solutions that block copy-paste altogether, Push protects your employees without disrupting their user experience or hampering productivity.
Check out the video below to see Push in action.
Enable ClickFix detection in just a few clicks
Check out the help article for step-by-step instructions on how to enable the control.
Learn more about Push
Push provides last mile protection against browser-based attacks, adding a net-new layer of technical protection in the browser.
Right now, most organizations are left relying on user awareness. Faced with increasingly novel attack types, encountered all over the internet, users are being caught unawares — further reducing the efficacy of an already fragile control.
By seeing what the user sees in the browser, as they see it, as well as monitoring for risky behaviors, Push provides a strong backstop against an ever-expanding landscape of browser-based exploits.
Push’s browser-based security platform provides comprehensive identity attack detection and response capabilities against techniques like AiTM phishing, credential stuffing, ClickFixing, malicious browser extensions, and session hijacking using stolen session tokens. You can also use Push to find and fix vulnerabilities across the apps that your employees use, like ghost logins, SSO coverage gaps, MFA gaps, vulnerable passwords, risky OAuth integrations, and more to harden your identity attack surface.
To learn more about Push, check out our latest product overview or book some time with one of our team for a live demo.



