Attackers have moved their phishing attacks out of the mailbox and are finding ever more ways to defeat conventional email, network, and endpoint-based security controls. Here's how browser-based security platforms can level the playing field and help security teams to stay ahead of the never-ending barrage of phishing attacks.
Attackers have moved their phishing attacks out of the mailbox and are finding ever more ways to defeat conventional email, network, and endpoint-based security controls. Here's how browser-based security platforms can level the playing field and help security teams to stay ahead of the never-ending barrage of phishing attacks.
Phishing has undergone a radical transformation. The laughably bad emails and fake PayPal logins of the past have given way to sophisticated campaigns engineered to slip through even the most hardened security stacks.
Today’s phishing attacks are faster, more adaptable, and harder to catch with traditional tools. Email filters and threat intel still play an important role, but they’re often reacting to threats that are already in motion, and by the time a phishing link is flagged and blocklisted, someone has probably already clicked — and the attacker has moved onto their next set of links.
The problem isn’t that phishing has evolved. It’s that our defenses haven’t.
That’s where Push Security comes in. By embedding real-time detection directly into the browser, the very place where phishing attacks unfold, Push offers a fundamentally new way to stop phishing: as it happens, regardless of whether or not the exact attack has ever been seen before.
Check out the video to see how it works.
The modern phishing playground
Phishing attacks today look nothing like the blunt instruments of a few years ago. These are fast, customized, and often completely ephemeral. A phishing domain might go live at 9 a.m., compromise scores of credentials, and be gone before lunch, long before it ever hits a threat intel feed.
Modern attackers use:
Dynamic content and user-adaptive emails that can be easily changed based on the target’s identity and environment.
Obfuscated URLs hidden behind trusted services (like Google Sites), making reputation analysis less than reliable.
Real-time proxying tools to clone login flows and harvest credentials.
Rapid-fire infrastructure rotation, making the attack’s infrastructure almost impossible to track in time.
These attacks often bypass traditional defenses entirely, not because the tools are broken, but because they were designed for a different era, one where phishing pages lived for days or weeks, not minutes.
It’s not enough to know what was bad yesterday. You need to know what’s happening now.
Why blocklists and perimeter defenses are falling behind
The security ecosystem has long depended on reputation-based systems: block the known bad, allow the rest. That worked when attackers reused infrastructure and relied on mass campaigns. Today’s adversaries have adapted.
Consider a scenario similar to the one from our video:
A staff member receives an email appearing to be from Microsoft Teams. It includes dynamic content that mirrors their actual environment, including their username, company logo, and real collaboration data. The embedded link takes them to a cloned Microsoft login page hosted on a benign-looking subdomain. The site is brand new. It’s not on any blocklist. Your email filter passes it. The employee logs in. Credentials and session tokens? Gone.
And that’s just step one. The attacker now pivots to connected apps like Jira, Confluence, or AWS, moving laterally through your cloud environment using the compromised credentials.
Traditional tools often miss these threats not due to a lack of sophistication, but because they’re looking from the outside in. The browser is where the attack actually unfolds. Without visibility there, key indicators of compromise go undetected.
Rethinking where phishing defense happens
Push changes where phishing protection happens, from upstream detection to point-of-interaction control. Instead of chasing malicious links through email gateways or external threat feeds, Push embeds lightweight, always-on protection directly, as users go about their work in the browser.
Push monitors what’s happening in each session: how pages are built, how they behave, and how users interact with them. That means it can recognize when a login prompt doesn’t match your identity provider or when a script behaves like part of a phishing toolkit.
When Push identifies something suspicious, it takes action right away. Logins are interrupted before any data is exposed. Users get clear guidance in-browser. And security teams receive detailed telemetry that shows exactly what happened, who was targeted, and how the threat was stopped.
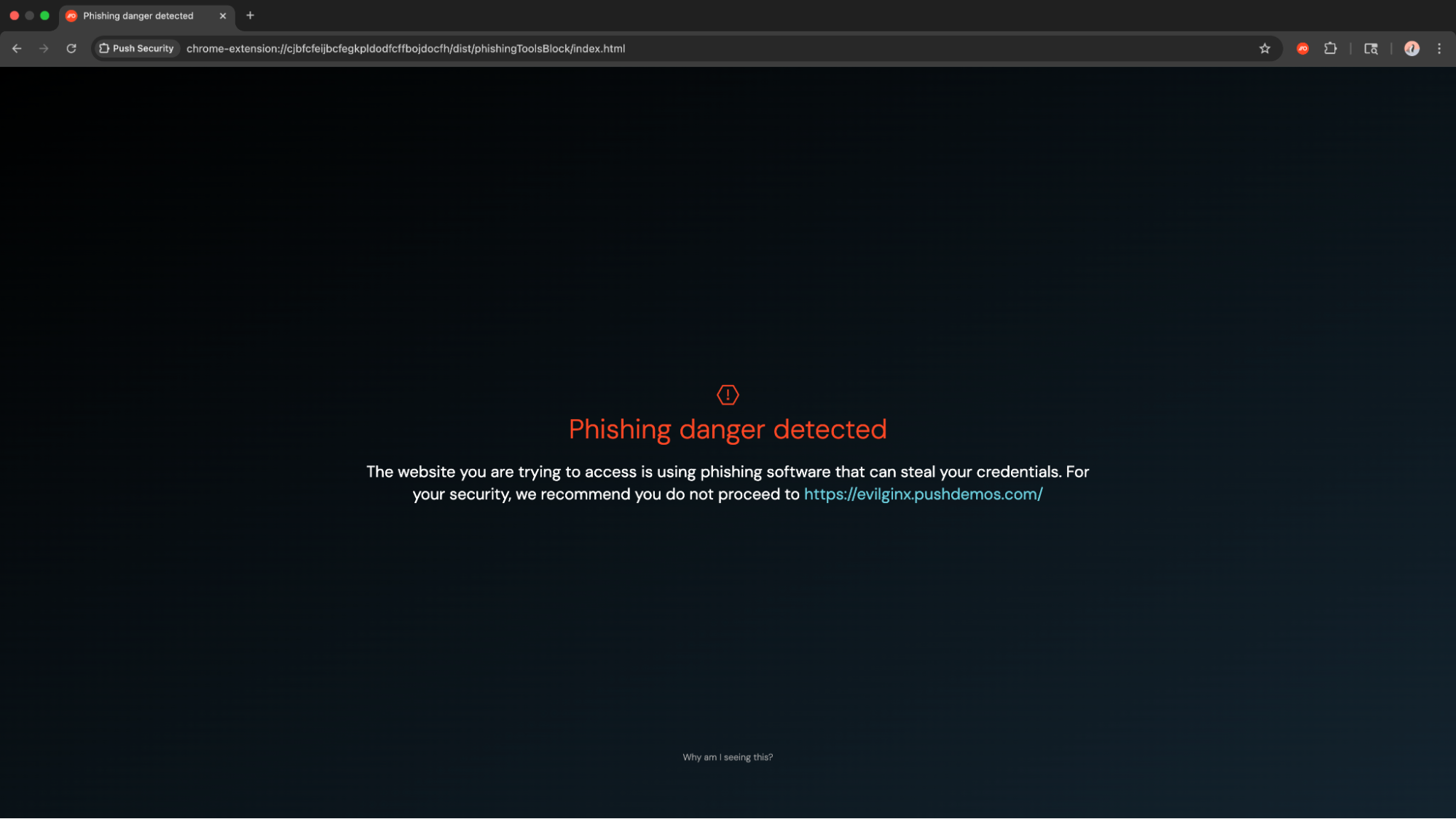
The benefits of browser-native phishing defense
True zero-day protection
Push doesn’t rely on known indicators of compromise. It evaluates the actual behavior and context of every session in real-time. Whether the phishing site was created 5 months ago or 5 minutes ago is irrelevant — Push detects it and shuts it down.
Contextual threat detection
Because Push operates in the browser, it sees everything:
The page layout
Where the user came from
The password they enter (as a salted, abbreviated hash)
What scripts are running
And where credentials are being sent
This context enables Push to stop even well-camouflaged phishing attempts, including AitM attacks that bypass MFA.
Real-time interception of malicious activity
As soon as a phishing attempt is confirmed, the response is immediate:
Credential entry is halted.
Sessions are revoked.
The user is protected without delay.
Reduced incident response overhead
Most phishing attacks end in hours of IR and expensive cleanup. With Push, attacks don’t escalate beyond the initial click. That means fewer compromised accounts, fewer escalations, and less fatigue on your security team.
Empowered, educated users
Push doesn’t just block phishing; it helps users learn from it. When someone interacts with a suspicious page, they get clear, actionable feedback right in the browser. Over time, these in-the-moment cues help build stronger phishing awareness across your workforce. Employee-facing messages are fully customizable to match the tone and style of your organization.
A new paradigm for identity security
While phishing detection is core, Push also helps you defend your entire browser-based identity attack surface. That means protecting against other common forms of account compromise, like:
Employees using breached or reused passwords
Missing or misconfigured MFA
Ghost logins that bypass your identity provider
Token-based session hijacking
Shadow SaaS usage
Because Push runs directly in the browser, it gives you visibility across every app your employees access, whether it’s officially managed or not. And it doesn’t just alert, it actively helps you fix the issues, guiding users to take action when risks are found.
Modern phishing requires a modern defense
Phishing is no longer an email problem. It’s not even just a domain reputation problem. It’s an identity attack problem, and the only place you can see those attacks in action is inside the browser.
Push Security gives you a new advantage: proactive, in-browser protection against modern phishing campaigns — even those with never-before-seen phishing sites.
See the phish happen.
Stop it in real time.
Keep your workforce identities safe.
Want to see Push in action? Book a demo and watch a real-time phishing attack get stopped mid-flow.


