The alert fatigue epidemic has reached crisis proportions, fueled by an expanding attack surface and telemetry gaps. But it's not all doom and gloom: the browser presents security teams with a net-new data source that is objectively better at detecting early-stage indicators of attack. Here's what you need to know.
The alert fatigue epidemic has reached crisis proportions, fueled by an expanding attack surface and telemetry gaps. But it's not all doom and gloom: the browser presents security teams with a net-new data source that is objectively better at detecting early-stage indicators of attack. Here's what you need to know.
After more than two decades in cybersecurity, I’ve witnessed the evolution (and at times, devolution) of detection and response capabilities. I’ve sat in countless SOCs watching analysts drown in a sea of alerts, spent hours chasing false positives, and seen talented security professionals burn out from the relentless noise of low-fidelity detection systems.
It’s a problem that’s reached crisis proportions, and it’s exactly why our approach to browser security represents not just a technological shift, but a philosophical one.
The alert fatigue epidemic
Early in my career, getting any alert felt like a victory. We were flying blind outside of our small windows of network traffic. But as the industry matured, something troubling happened: we began equating volume with value. Vendors started competing on how many alerts they could generate, how much data they could collect, and how comprehensive their “visibility” could be.
Security teams followed suit with operational metrics that captured how many alerts they’d resolved, how many “attacks” they’d stopped, and how many tickets they’d opened and closed in a given work cycle. But as many teams have now realized, volume is a vanity metric; fidelity is what keeps you safe.
In my course on Building and Leading Security Operations teams, we discuss the importance of analytic outcomes and addressing ineffective alerts to continuously improve fidelity. My students often find it hard to believe how much time and effort it takes to audit alert quality and implement continuous improvements on a large scale. This isn’t just an operational problem — it’s an existential threat to effective security. When everything is an alert, nothing is.
And while we have been busy focusing on more (and occasionally, better) detections at the endpoint and network layers, attackers have shifted to infrastructure that isn’t as well-instrumented: SaaS and the browser.
The browser: a new frontier in detection and response
Today, the browser is the place where most cyber attacks happen. It’s where users interact with the applications that your business runs on, handle sensitive data, and unfortunately, where they encounter sophisticated phishing campaigns, credential harvesting attacks, and malicious downloads.
Yet for most security teams, the browser remains a black box, obscured from the view from the network and the endpoint. Even worse, attack models often applied to detection engineering for endpoint or network-centric threats don’t really apply; modern identity attacks skip entire phases of the attack chain, eliminating many detection opportunities along the way. The modern attack path doesn’t need to touch the endpoint or your network at all — it can happen entirely over the internet.
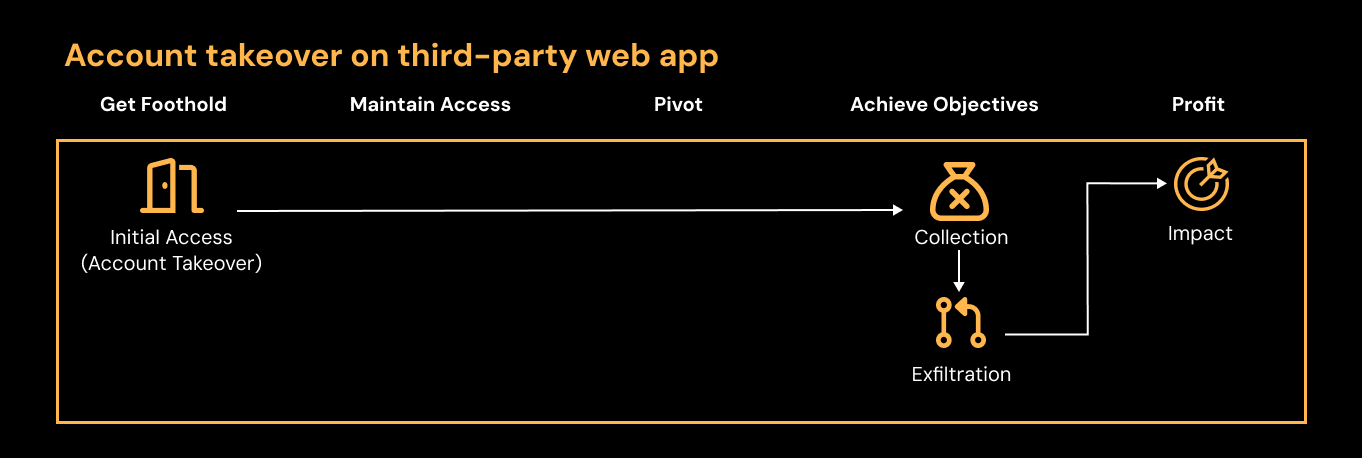
Attackers are exploiting the detection gap
You only need to look at in-the-wild breaches such as last year’s Snowflake attacks, or the recent Salesforce breaches to see the impact that attackers can have by executing attacks entirely over the internet, without touching traditional network devices or user endpoints.
But even in the context of more “conventional” attacks (e.g. the classic route of compromising an endpoint, moving laterally through an environment, taking control of a domain, and deploying ransomware), most of the time, these attacks begin in the browser with identities and cloud apps rather than exploit-driven initial access — such as with the recent attacks on Marks & Spencer, Co-op, and Jaguar Land Rover.
While the attack cycle and similar mental models are valuable for planning in-depth detections of sophisticated, multi-stage attacks, focusing too heavily on them can lead to overlooked scenarios. These high-profile incidents have demonstrated the opportunity cost of neglecting visibility into attacks that don't perfectly align with these models.
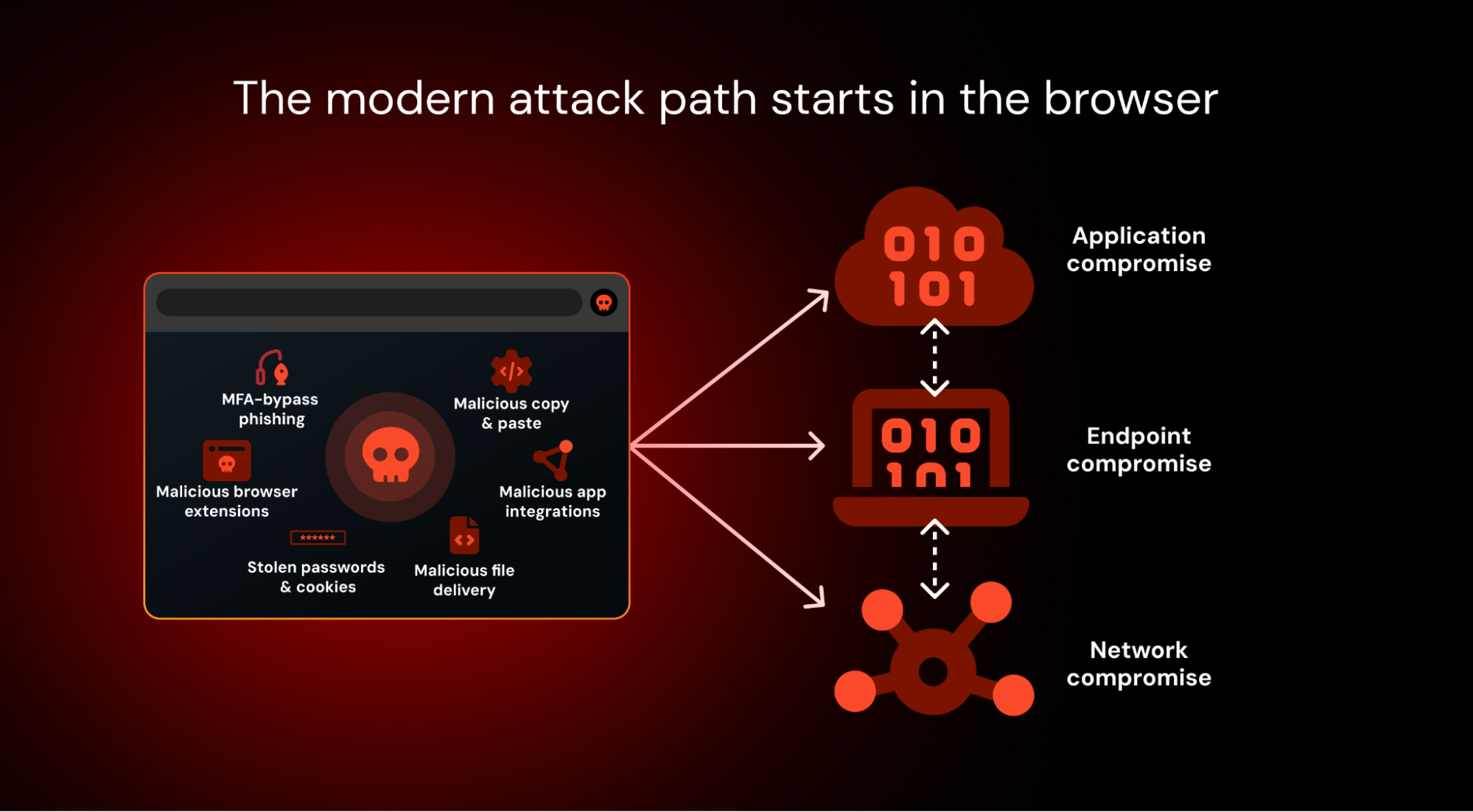
Just as endpoint detection and response revolutionized host-based security by providing visibility and control directly at the point of attack, browser-based security platforms can do the same for web-borne threats. It’s an important addition to the detection and response stack that illuminates a “missing middle” in modern attack investigations, and intervenes in real time, much like traditional EDR did for the endpoint years ago.
To tackle attacks that are designed to evade traditional detection surfaces and take place mostly over the internet, we must integrate browser telemetry into our detection and response framework, and expand detection engineering and threat hunting processes to incorporate this new dataset.
High-fidelity detection: quality over quantity
Our design philosophy centers on a principle often overlooked in the security industry: prioritizing actionable problems for security teams. This involves differentiating between "events" – environment data that may or may not be useful – and "detections" – high-fidelity, actionable signals with a negligible false positive rate. We also empower our customers with the ability to intervene in real-time when there are high-confidence indicators of an attack. We focus on detecting not atomic indicators, but on attacker tooling and behaviors.
Compare this to traditional approaches that might generate alerts for:
Visiting domains with low reputation scores (but not necessarily malicious)
Downloading files that match certain heuristics (but may be legitimate)
Accessing new web applications (that may be approved, or tacitly allowed, shadow IT)
Employee usernames, passwords, and email addresses for sale on the dark web (which may no longer be valid)
These low-fidelity alerts create work without providing solutions. They force analysts to become investigators rather than responders, spending precious time determining whether an alert represents a genuine threat rather than focusing on mitigation and recovery.
This is what Ryan McGeehan called the “Law of the Lever” several years ago, and it still holds true today: The time spent creating a poor quality detection rule will likely create a significant amount of work for someone responding to the follow up alert. This doesn’t mean that only high fidelity analytics have value; we still need general environment telemetry to test investigative hypotheses and identify new use cases. But we can’t allocate sufficient resources to those tasks while also dealing with low quality alerts.
Poor quality detections also present an easy opportunity for security teams to commit a cardinal sin: disrupting users and business processes without a clear justification for doing so. User trust and support should always be treated as a finite resource, and every account locked, website blocked, and laptop reimaged chips away at that resource.
Likewise, the more disruptive, the more likely users will look for ways around said controls. If your users are actively working against you, and feel you are preventing them from doing their jobs, they’ll always find new and unexpected ways around security blocks.
The SOC analyst's perspective
The most successful SOC analysts share a common trait: they’re extraordinarily good at quickly distinguishing signal from noise. But this skill shouldn’t be required! It’s a failure of our detection systems that we’re forcing human analysts to perform pattern matching that our technology should handle.
But even for the most skilled analyst, it’s a tall order to ask your security team to also be experts in every cloud app your business relies on, making it even harder than normal to build context-driven alerts. Most of the time, the information required simply doesn't exist, with logs simply not available (generally, or at your product tier) or the work required to extract the logs and turn them into context-driven alerts hasn’t happened yet. If your team is under-resourced and drowning in low-fidelity alerts already, then realistically it might never happen.
Effective browser security changes this dynamic. Instead of presenting analysts with hundreds of “suspicious web activity” alerts that require investigation, our platform focuses on high-reliability indicators like whether a phishing kit was observed running on the page, or whether the page was cloned from a legitimate site. We even detect user behaviors that could indicate a risk in the context of a phishing attack, like when a user attempts to authenticate with credentials that have been previously used on another page — either a sign of credential reuse (bad) or a phishing attack (even worse) — at which point Push can be set to block the attack in real time.
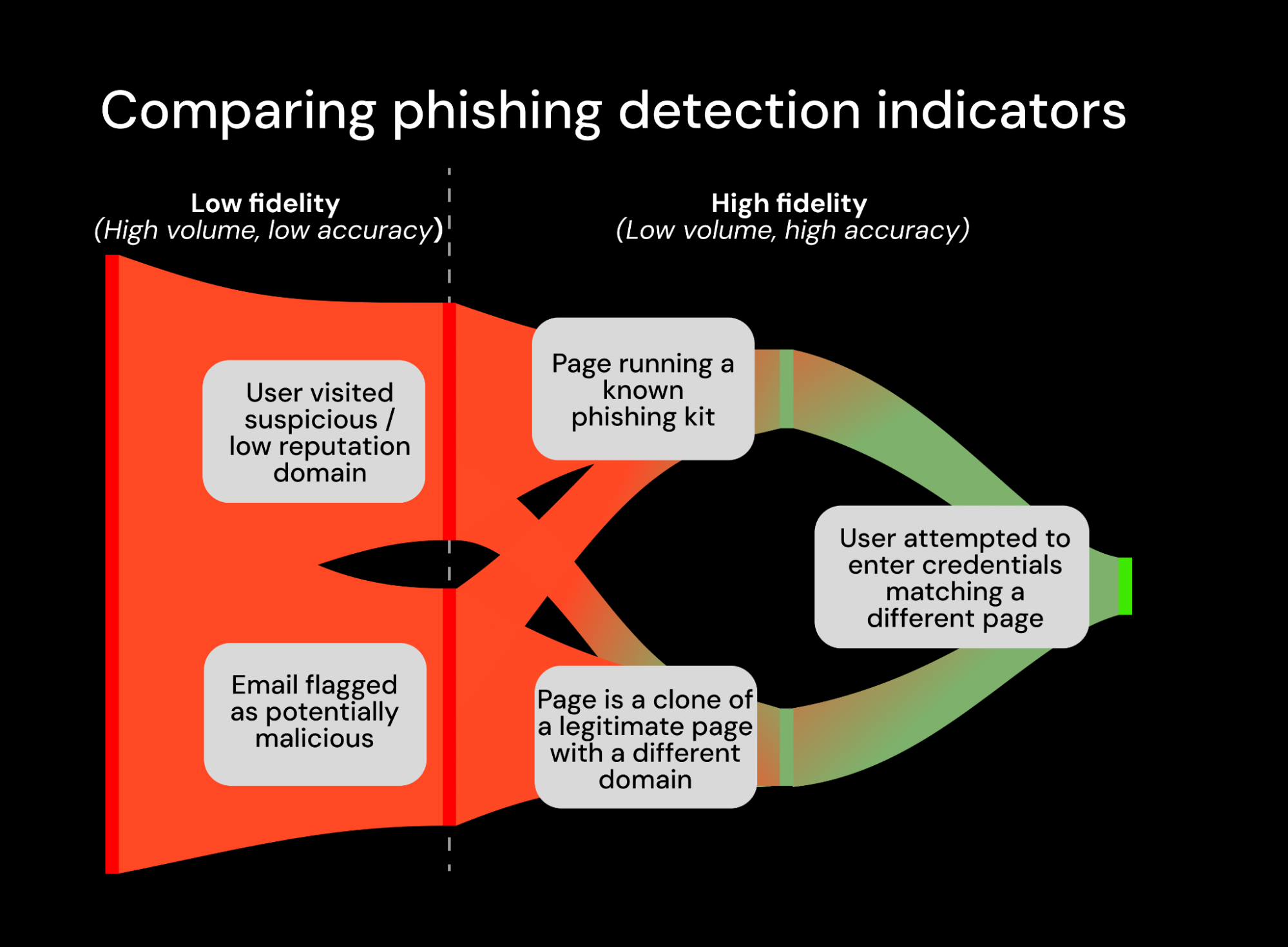
Browser security provides a new layer of protection, reducing the risk of breach
Attack detection has always been a cat-and-mouse game. For years, attackers have grappled with endpoint and network security vendors. And sometimes, the attackers win. The fact is that a lot of attacker innovation has gone into sandbox aware malware, breaking detection signatures, disabling security tools, and so on.
But with so many attacks now passing through the browser, defending it enables badness to be filtered out before it reaches the endpoint or network controls that attackers are looking to consciously evade. By preventing malware being delivered, or identities from being compromised, attacks otherwise crafted to evade traditional security controls can be intercepted early — making the crucial difference in whether a breach happens or not.
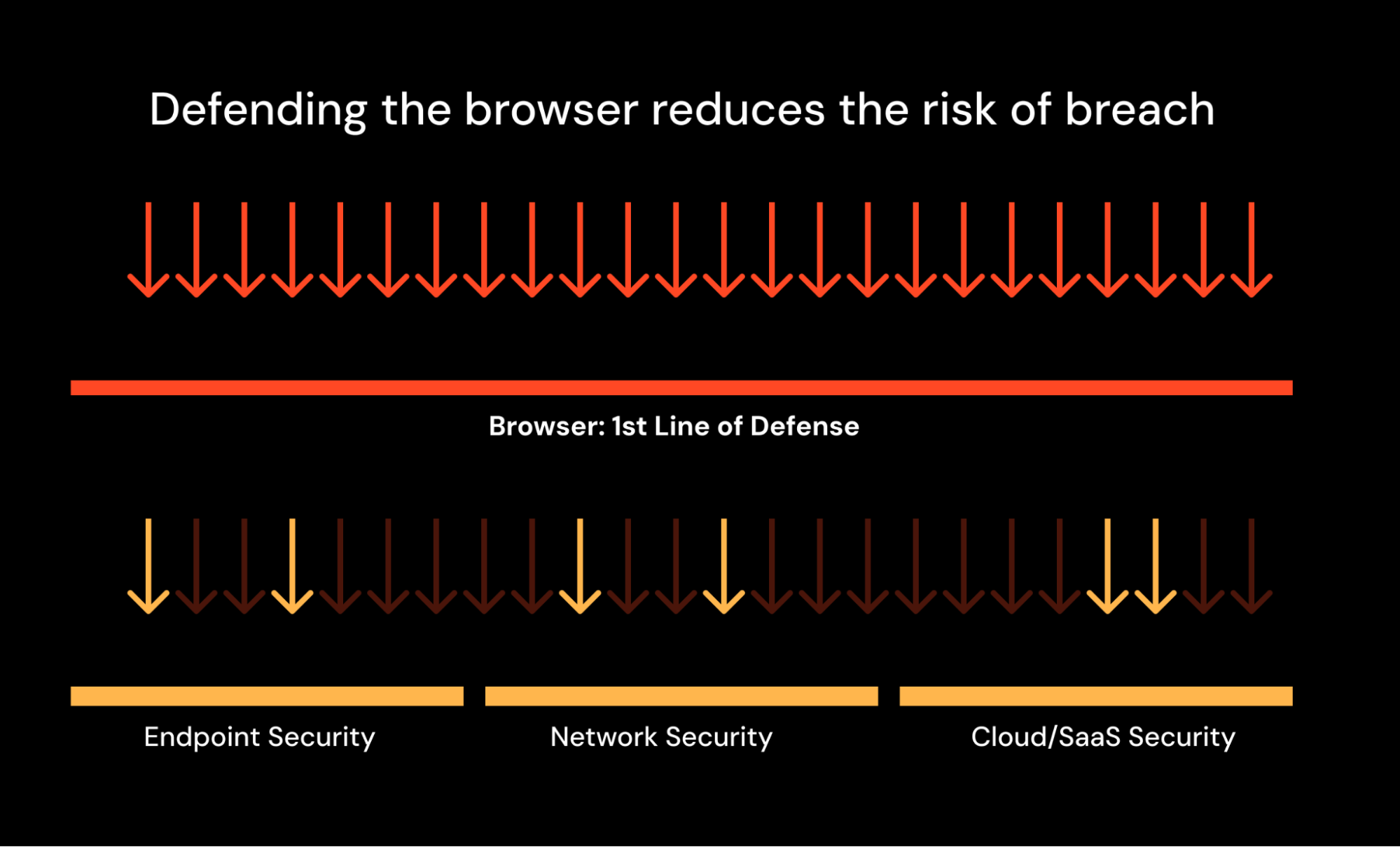
And when it comes to the cloud-centric attacks that attackers are finding so much success with today, this is in effect a net new capability.
The psychological impact of this shift cannot be overstated. When analysts know that every alert represents a genuine threat that was successfully mitigated, their job satisfaction increases, burnout decreases, and the overall security posture improves dramatically.
Learn more about Push Security
The browser represents one of the most significant opportunities in cybersecurity today. As we continue to expand our browser-based security capabilities, we remain committed to this high-fidelity approach. We’re building features that not only detect and prevent attacks but also provide security teams with the rich telemetry they need to develop custom queries and detections.
Push Security’s browser-based security platform provides comprehensive detection and response capabilities against techniques like AiTM phishing, credential stuffing, ClickFixing, malicious browser extensions, and session hijacking using stolen session tokens. You can also use Push to find and fix vulnerabilities across the apps that your employees use, like ghost logins, SSO coverage gaps, MFA gaps, vulnerable passwords, risky OAuth integrations, and more to harden your identity attack surface.
To learn more about Push, check out our latest product overview or book some time with one of our team for a live demo.

