Breaking down the most sophisticated ClickFix page we’ve seen in the wild — and what it tells us about the future of malicious copy-and-paste attacks.
Breaking down the most sophisticated ClickFix page we’ve seen in the wild — and what it tells us about the future of malicious copy-and-paste attacks.
ClickFix attacks have skyrocketed in the last year. This social engineering attack has established itself as a key part of the modern attacker’s toolkit, tricking victims into running malicious code on their device.
As we showcased in our last webinar and at our threat briefing in London earlier this month, ClickFix is evolving fast, in terms of the web pages themselves, the delivery mechanisms by which they are sent to victims, and the nature of the payload and its execution.
One particular example stood out to us in our research. So, is this the most advanced ClickFix you’ve seen?
Let’s break it down further.
How ClickFix pages are evolving
The CloudFlare-based lure is a great example of how ClickFix pages themselves are evolving — and becoming increasingly convincing to users.
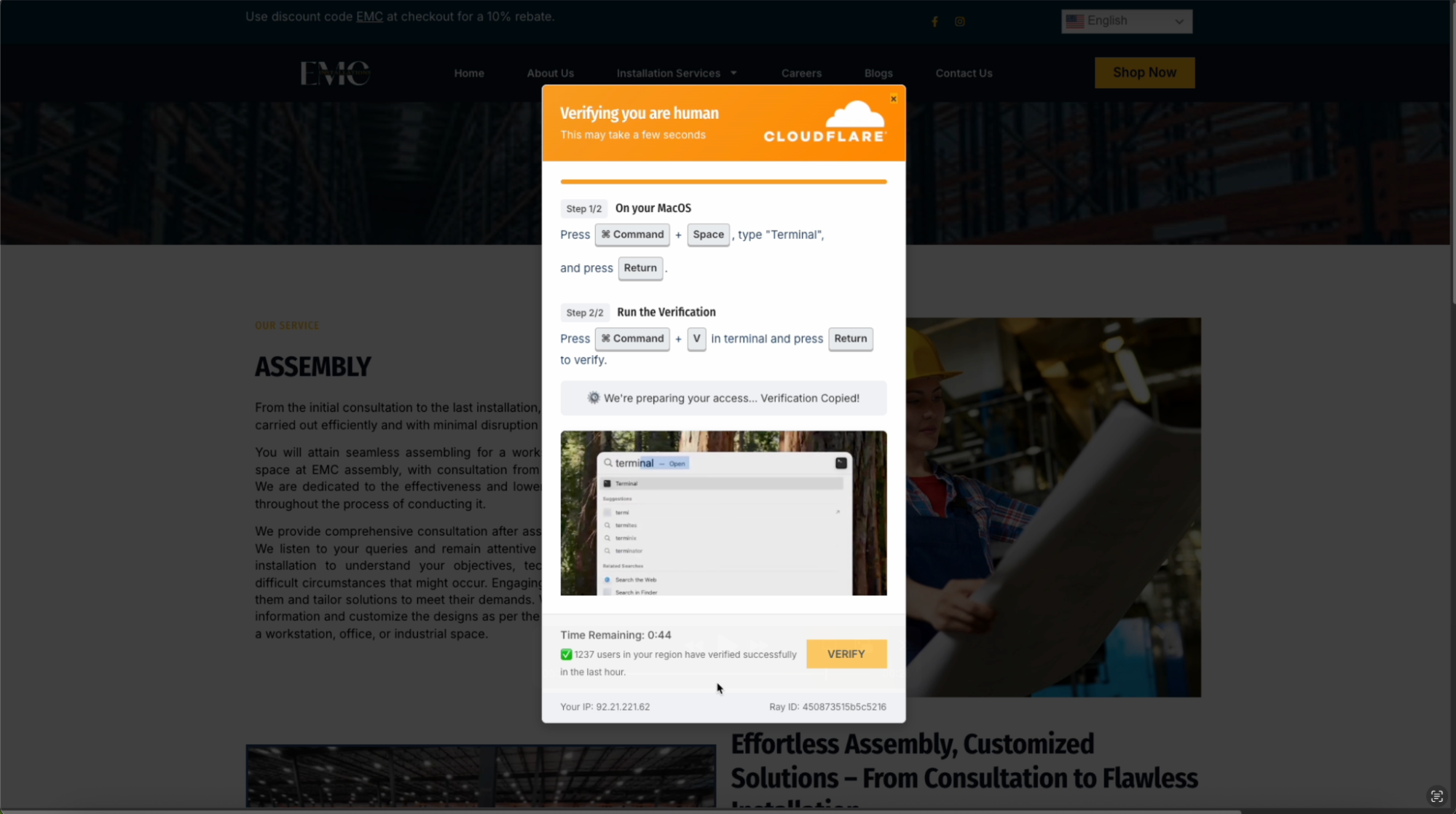
This is an incredibly slick example — it almost looks like Cloudflare shipped a new kind of bot check service. The embedded video, countdown timer, and counter for “users verified in the last hour” all serve to increase the sense of authenticity, and put extra pressure on the victim to complete the check.
There are a couple of extra things happening under the hood here, too:
The page is adapting to the device that you’re visiting from, serving up instructions specific to the user’s Mac (increasingly common as ClickFix expands to support different Operating Systems).
The page is automatically copying the malicious code to the user’s clipboard via JavaScript (which we see in 9/10 cases).
For the past decade or more, user awareness has focused on stopping users from clicking links in suspicious emails, downloading risky files, and entering their username and password into random websites. It hasn’t focused on opening up a program and running a command — so it’s no surprise that this kind of highly convincing page is so effective at duping victims into following the instructions.
How ClickFix delivery methods are evolving
There’s also the fact that this page wasn’t accessed via email. The top delivery vector for ClickFix attacks that we’ve observed is, in fact, Google Search — in the form of poisoned search results and malicious advertising (malvertising). Attackers are either taking over legitimate sites (there’s a steady supply of website hosting and CMS vulnerabilities to take advantage of) or simply vibe-coding their own sites and optimizing them for various search terms.
Of the ClickFix pages intercepted by Push where the delivery vector was observed, 4 in 5 were accessed via Google Search. While other examples may have been stopped by controls such as email before the page could be loaded by the user, this shows a significant monitoring gap when it comes to non-email delivery vectors.
And because most anti-phishing controls are implemented via email, by using non-email delivery vectors, an entire layer of detection opportunity is cut out.
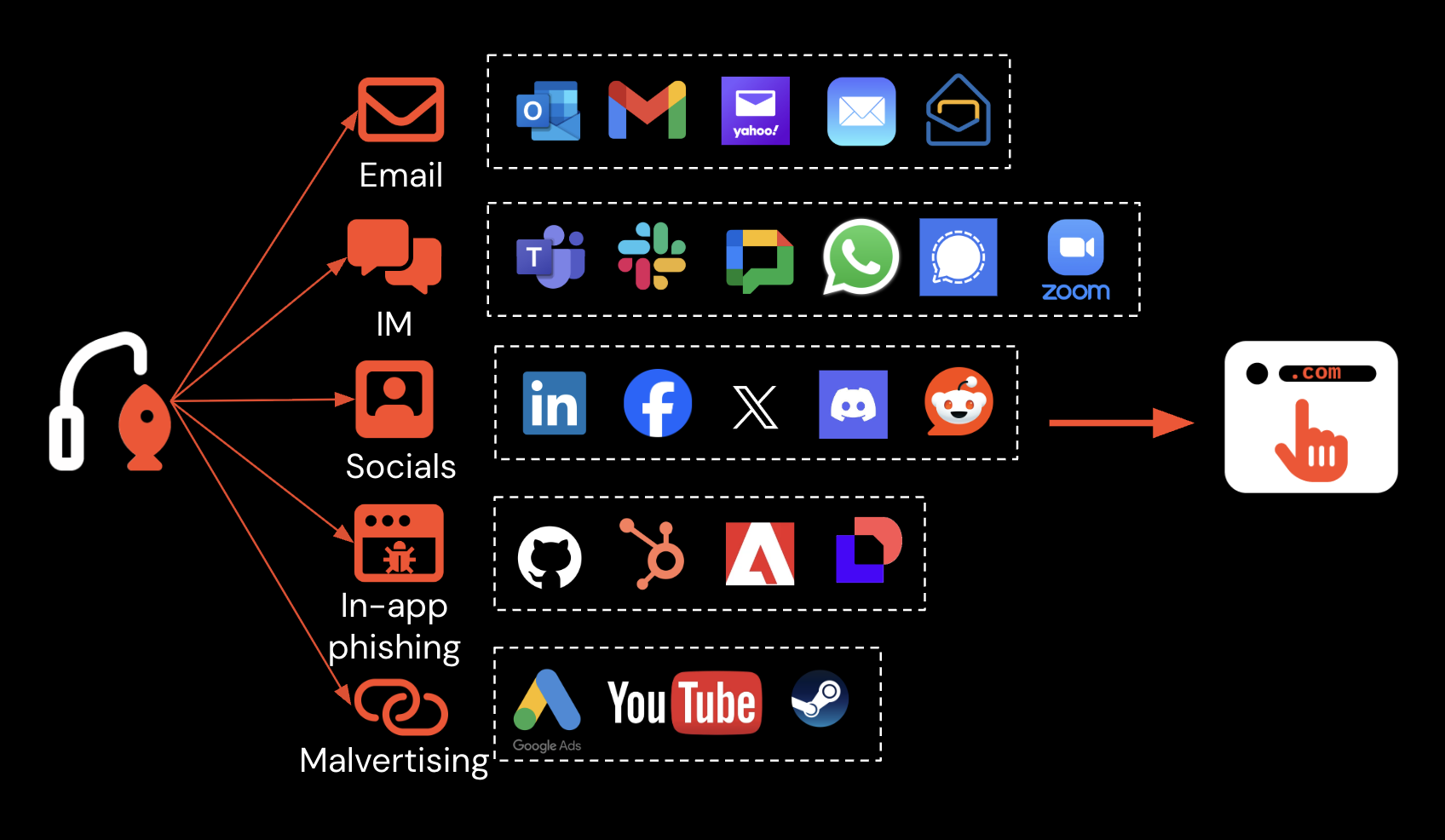
But even when they are sent via email, ClickFix pages, like other modern phishing sites, are using a range of detection evasion techniques that prevent them being flagged by security tools — from email scanners, to web-crawling security tools, to web proxies analyzing network traffic. Detection evasion mainly involves camouflaging and rotating domains to stay ahead of known-bad detections (i.e. blocklists), using bot protection to prevent analysis, and heavily obfuscating page content to stop detection signatures firing.
Finally, because the code is copied inside the browser sandbox, typical security tools are unable to observe and flag this action as potentially malicious. This means that the last — and only — opportunity for organizations to stop ClickFix is on the endpoint, after the user has attempted to run the malicious code.
Although there are ways to block web pages from performing copy to clipboard via device settings or group policy, the practical reality of ClickFix means that these methods are not effective. Because ClickFix is a user gesture initiated paste event (some form of user interaction such as a button press is required on the page before loading the ClickFix lure) it cannot be blocked from the host.
How ClickFix payloads are evolving
It’s not just the ClickFix page and delivery mechanisms that are evolving — the services where code is being run, and the type of payload, are also increasingly varied.
While the main payloads observed by Push are mshta and PowerShell, attackers are abusing a wide range of LOLBINS targeting different services across Operating Systems.
While it is possible to disable the Win+R dialog box and limit the applications that can be run from the File Explorer address bar, it is not possible to similarly restrict users from interacting with other legitimate services to run malicious commands.
Another recent example termed cache smuggling was also identified by security researchers. This technique combines a ClickFix approach with JavaScript that caches a malicious file posing as a JPG. This means that the ClickFix command executes locally — effectively getting an entire zip file onto the local system without the PowerShell command needing to make any web requests.
Finally, it’s worth considering the future of ClickFix. The current attack path straddles browser and endpoint — what if it could take place entirely in the browser and evade EDR altogether?
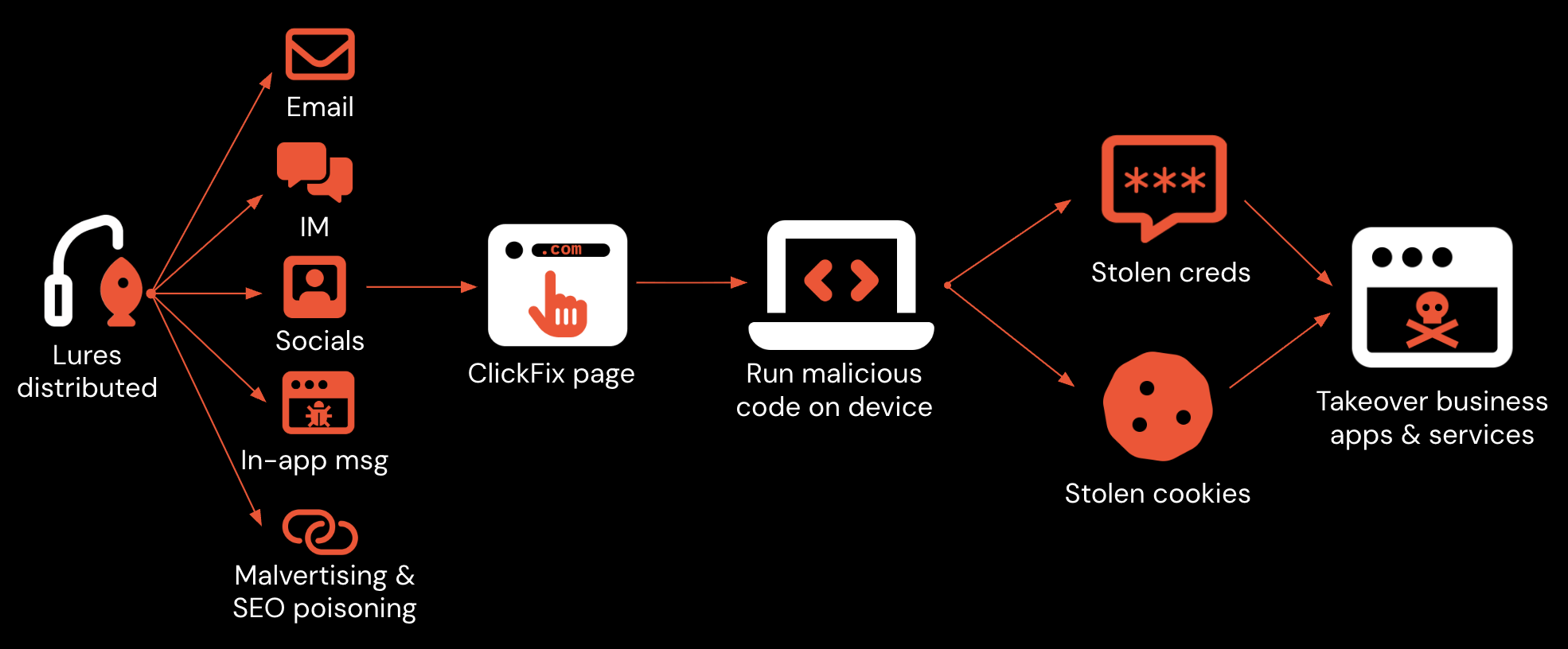
What’s the impact of ClickFix evolution?
To summarize:
ClickFix pages are becoming increasingly sophisticated, making it more likely that victims will fall for the social engineering.
ClickFix delivery is evading traditional monitoring controls at the email layer to reach victims.
ClickFix payloads are becoming more varied and are finding new ways to evade security controls.
This means that EDR-based interception of malware execution is the last — and only — real line of defense for most organizations, kicking in after the initial script has been run (typically acting as a stager for the real malware).
Malware execution can and should be intercepted by EDR, but it’s not foolproof.
Attackers are constantly developing new tools and capabilities to bypass EDR in the cat-and-mouse game between attackers and defenders.
Because ClickFix attacks are user initiated, context might be missing that lead to the alert being misclassified. This can mean the difference between the level of priority alert that is raised, and whether or not it is automatically blocked.
If you’re an organization that allows employees and contractors to use unmanaged BYOD devices, there’s a strong chance that there are gaps in your EDR coverage.
This is why attackers are doubling down. According to the 2025 Microsoft Digital Defense report, ClickFix was the most common initial access method in the last year, accounting for 47% of attacks. That's a pretty significant stat.
47% of attacks started with ClickFix in the last year, according to Microsoft.
Ultimately, organizations are leaving themselves relying on a single line of defense — if the attack isn’t detected and blocked by EDR, it isn’t spotted at all.
Don’t gamble on a single point of failure
Push Security’s latest feature, malicious copy and paste detection, tackles ClickFix-style attacks at the earliest opportunity through browser-based detection and blocking. This is a universally effective control that works regardless of the lure delivery channel, page style and structure, or the specifics of the malware type and execution.
Unlike heavy-handed DLP solutions that block copy-paste altogether, Push protects your employees without disrupting their user experience or hampering productivity.
By adding a new layer of protection in the browser, security teams can reduce the strain on their EDR and reduce the risk of host-based controls being bypassed through misconfiguration or attacker innovation.
Learn more
If you want to learn more about ClickFix attacks and how they’re evolving, check out our latest webinar (now available on-demand!) where we dive into real-world ClickFix examples and demonstrate how ClickFix sites work under the hood.
To learn more about Push, check out our latest product overview or book some time with one of our team for a live demo.
