Browser extension visibility, ClickFix detection, RBAC and more.
Browser extension visibility, ClickFix detection, RBAC and more.
What's new this month:
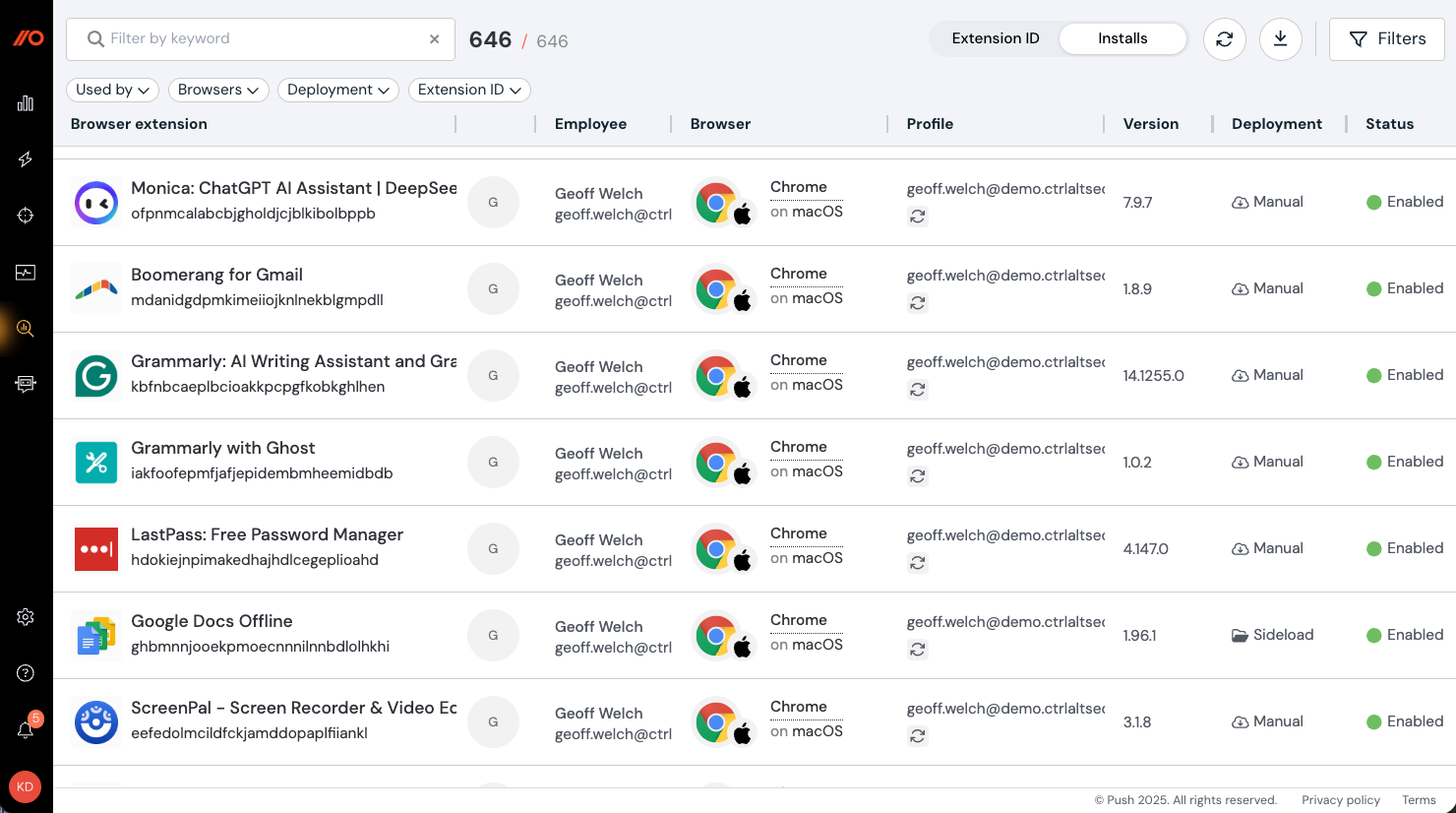
Get visibility for all installed browser extensions in your environment
New detection for ClickFix-style malicious copy-paste attacks
New Labs feature: Experimental detections
RBAC for the Push admin console
URLscan.io and domain registration enrichment for detections
Filter events by entities
And a few other things …
Get visibility for all installed browser extensions in your environment
You can now use Push to see other browser extensions installed on your employees’ browsers.
You can enable this feature by going to Settings > Organization in the Push admin console and toggling on Browser extension visibility. There is no end-user impact when you enable this feature.
You’ll see browser extension data populate a new Browser extensions page in the admin console under Investigate. With this information, you can see:
Which extensions have been installed for each employee and browser.
How they were installed (e.g. by policy, manually, or sideloaded).
Which permissions they have.
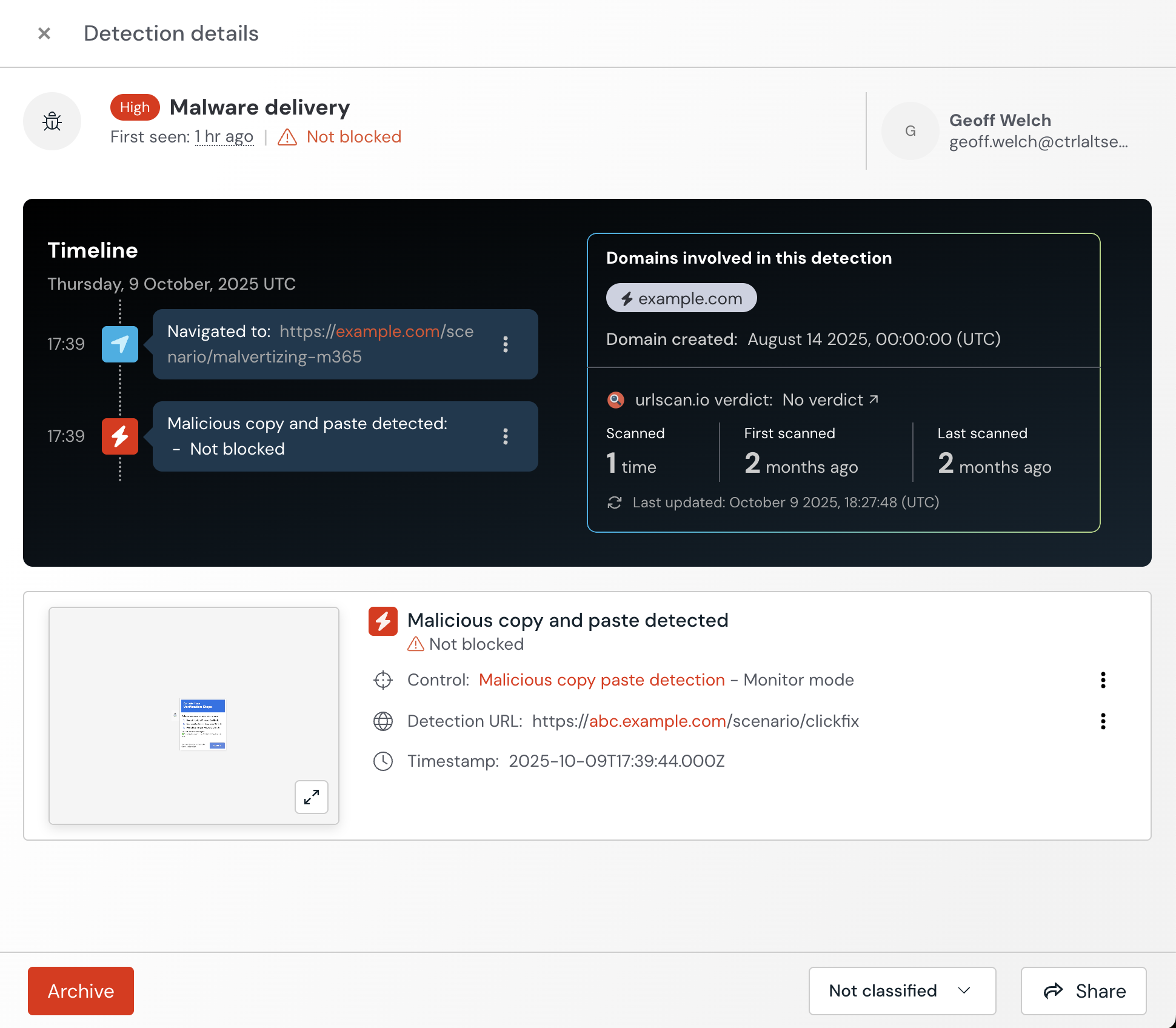
New detection for ClickFix-style malicious copy-paste attacks
Push can now detect malicious copy and paste attacks like ClickFix, FileFix, and other fake CAPTCHA-style techniques.
These techniques have become one of the most prevalent attack types this year, and rely on deceiving users into manually or automatically copying malicious code and running it locally.
You can enable Malicious copy and paste detection from the Controls page of the Push admin console. Add a configuration rule to set the detection to Monitor. You can also add an exception for any staff who routinely handle malicious scripts, such as security team members, or add domains to the ignore list as needed.
New Labs feature: Experimental detections
Get early access to new detections from the Push research team by enabling Experimental detections, a Labs feature.
Labs features are new features Push is testing before releasing them. Early access detections are designed to catch emerging attacker techniques, but may also produce more false positives while we finetune them. These early access detections do not block any user actions.
Enable Experimental detections by going to Settings > Labs in the admin console.
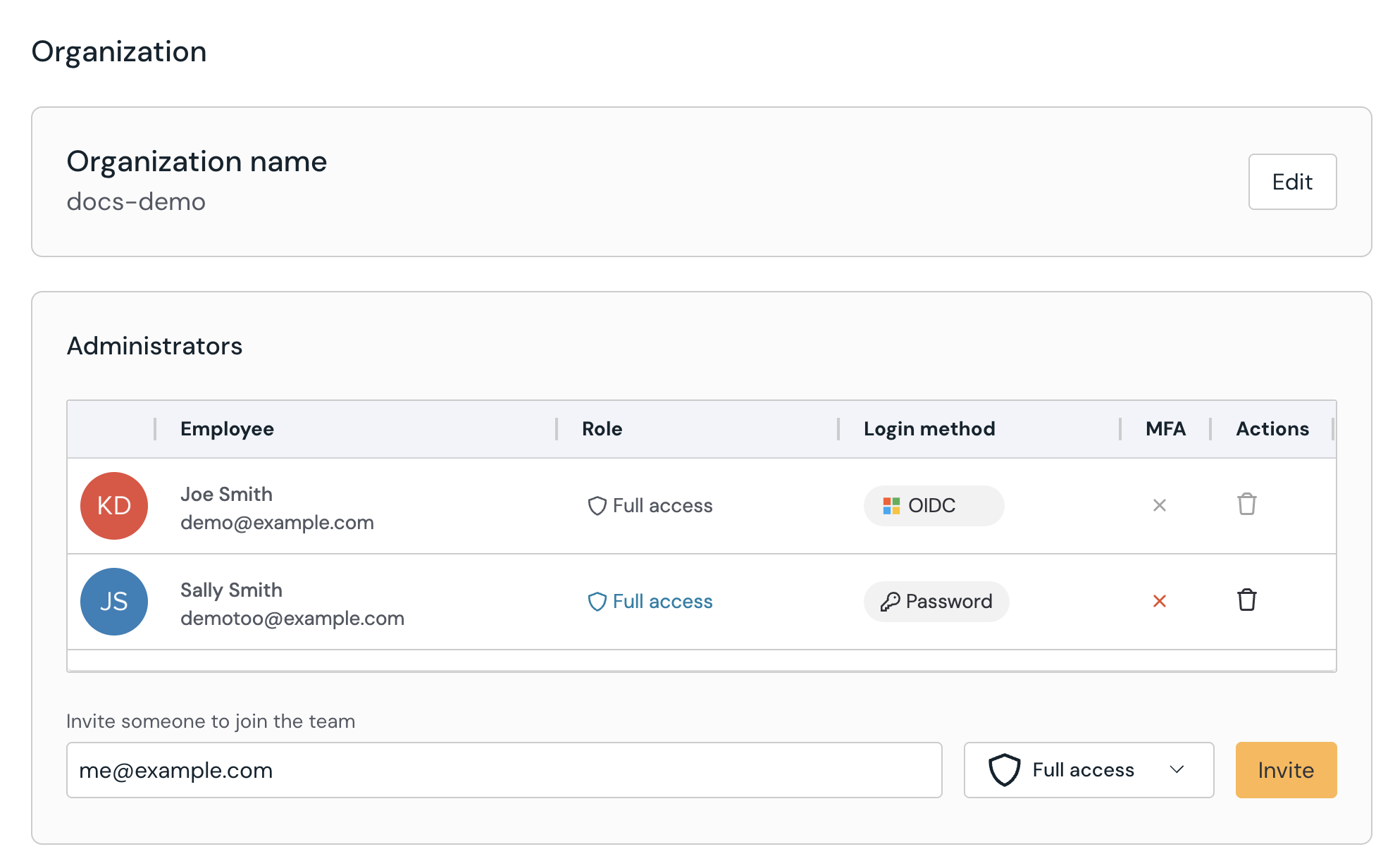
RBAC for the Push platform
You can now provide read-only access to the Push admin console to facilitate investigations, review detections, check app usage by department, help with employee offboarding — or anything else you need.
To add a read-only admin, go to Settings > Organization in the admin console. Enter the email address of the admin you want to invite and set the role to Read only.
Note that existing Push admins now have the role of Full access. You can adjust that role as needed from the Organization page, too.
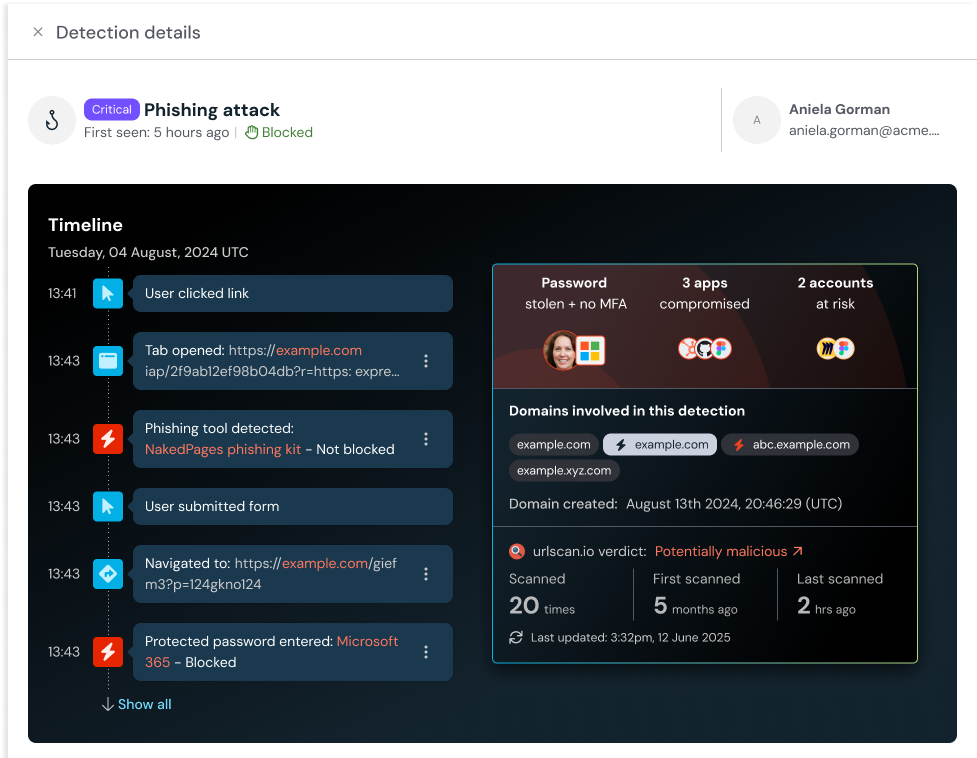
URLscan.io and domain registration enrichment for detections
You can now enrich detections in Push with information from urlscan.io, and see when the domain was first registered. This information gives you domain-relevant context to support investigations.
To enable this feature, go to Settings > Advanced > Domain enrichment in the Push admin console or enable it from any existing detection event.
With this enrichment, you can quickly see:
The timestamp for when a domain was first registered
The number of times a domain was scanned on urlscan
The first time a domain was scanned
The last time a domain or IP was scanned
A urlscan verdict (e.g. “potentially malicious”)
You’ll see the enrichment data on the details slideout for an individual detection.
Filter events by entities
You can now filter the Events page in the Push admin console by entities such as employees and apps to make triage more efficient.
With this option, you can do quick searches such as:
See all recent events associated with an employee
See all recent logins for a given app
From the Events page, go to Filters > Entity type.
And a few other things …
Other new features or improvements to the platform include:
You can now configure exceptions for MFA findings and reused password findings. This is useful if you purposefully reuse passwords between systems or enforce MFA through a third-party provider.
We’ve added several first-class SIEM integrations. Learn more.
We’ve expanded the limit for URLs you can block using the URL blocking control to 2,000.
You can now set a time period after which to automatically un-license inactive employees, to make license management easier. Learn more.
Push now supports Prisma Access browser.
