How Push saved a company exec from a sophisticated Attacker-in-the-Middle phishing attack delivered via a LinkedIn direct message.
How Push saved a company exec from a sophisticated Attacker-in-the-Middle phishing attack delivered via a LinkedIn direct message.
Update 15th September:
Since releasing this article we have observed further attacks using almost identical TTPs across a number of Push customers, specifically targeting technology firm executives. We've also had a number of people that aren't Push customers reach out to us after seeing attacks that are clearly part of the same campaign. So, we've added some additional information to help other security teams to investigate whether they have also been targeted.
Push recently detected and blocked a high-risk phishing attack targeting a company executive's Google Workspace account.
This attack demonstrated a range of advanced detection evasion techniques designed to circumvent traditional detection controls.
Given this was a highly targeted attack against a company executive, the impact of a successful phish would have been extremely high. Push’s browser-based detection and response solution intercepted and blocked the phish in real-time, preventing the Microsoft session or credentials being captured by the attacker.
What happened
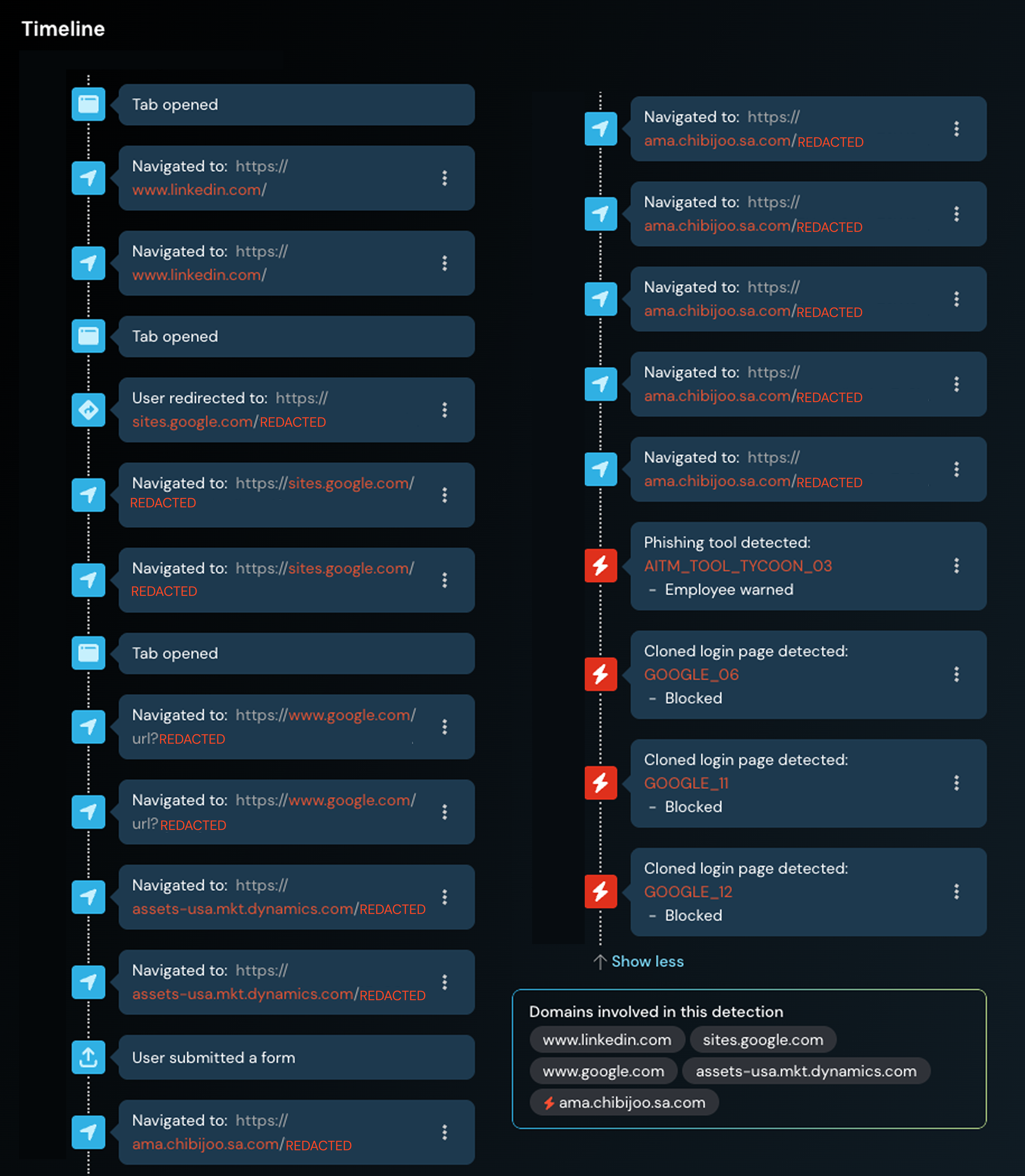
A Push customer’s exec was targeted on LinkedIn via a direct message from another exec about an investment opportunity. The sender’s account had been compromised and used to approach high-value targets.
The victim was sent a link to a basic page hosted on sites.google.com, styled as a landing page for a private equity fund investment opportunity. The page had buttons to handle both Microsoft and Google users.
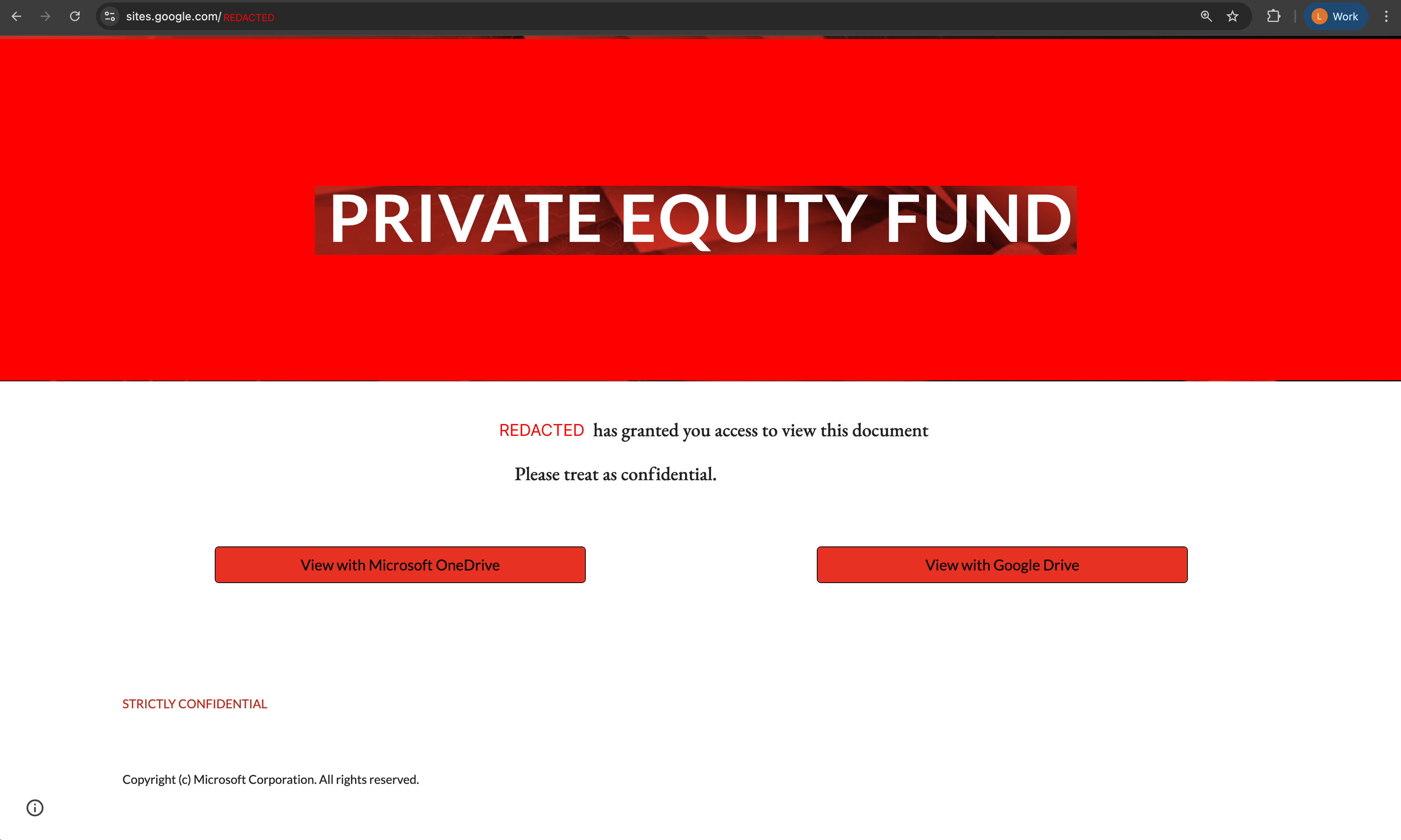
Upon clicking a button, Google Search was used as a redirect before taking the victim to a second page hosted on Microsoft Dynamics. This page was styled to look like Google Drive, where the victim was prompted to enter their last name and email into the form.
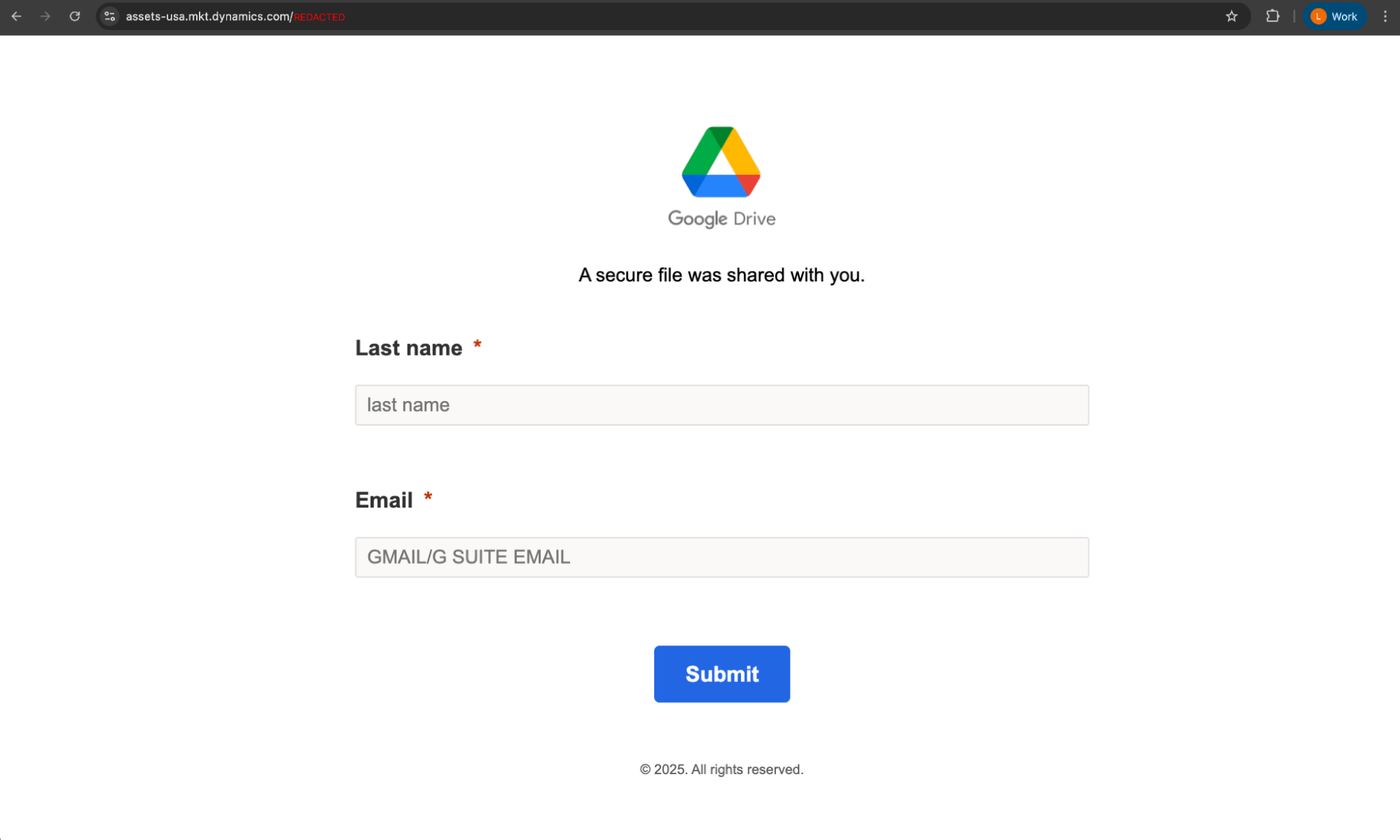
Upon entering their details and clicking submit, the victim was finally sent to an Attacker-in-the-Middle (AitM) phishing page.
To access the page, the victim had to solve a custom CAPTCHA challenge, which we’ve observed in a number of recent phishing attacks that we’ve linked to the Tycoon 2FA phishing kit.
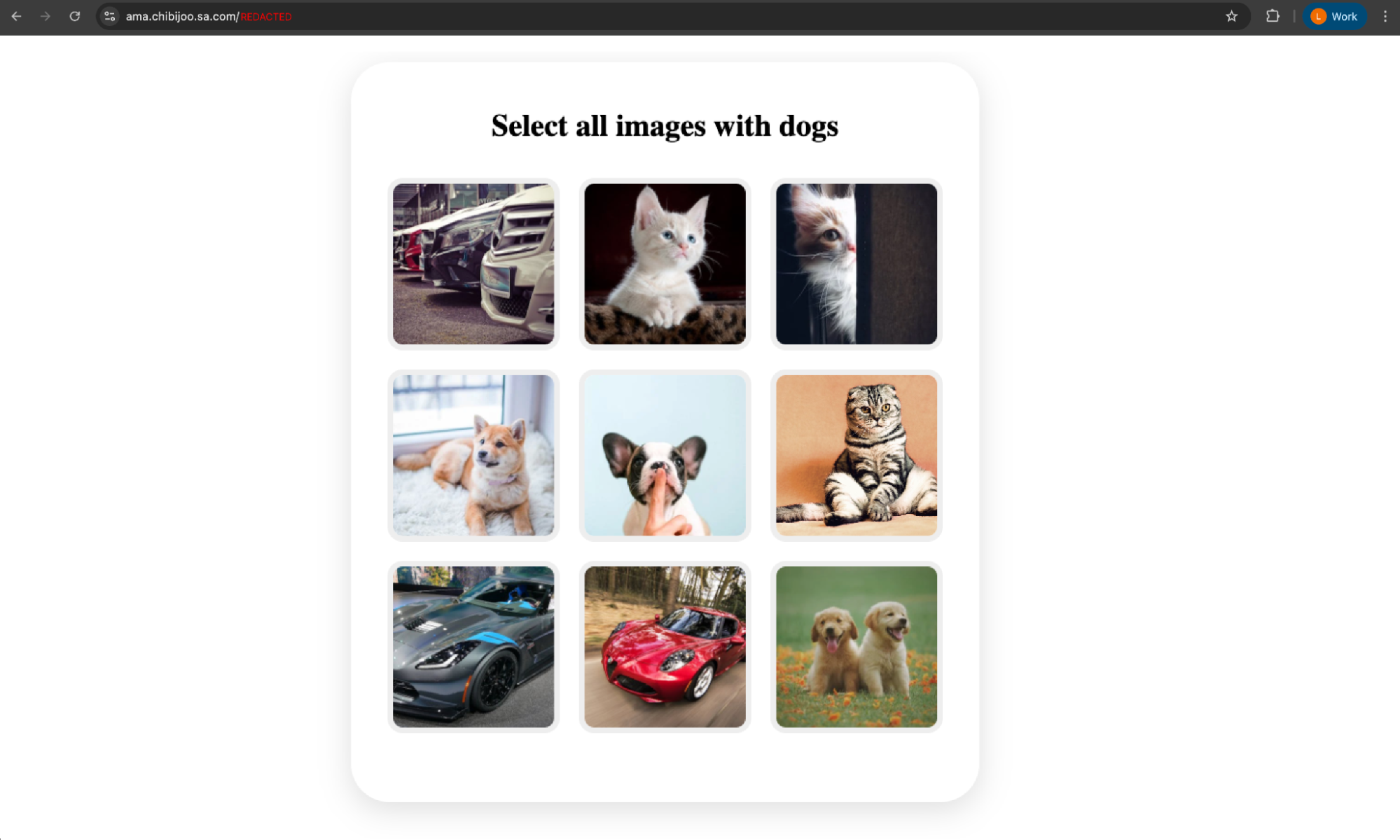
Because the customer had configured Push’s phishing tool detection control in block mode, the Push browser agent flagged the page as malicious to the user and prevented the attack from continuing.
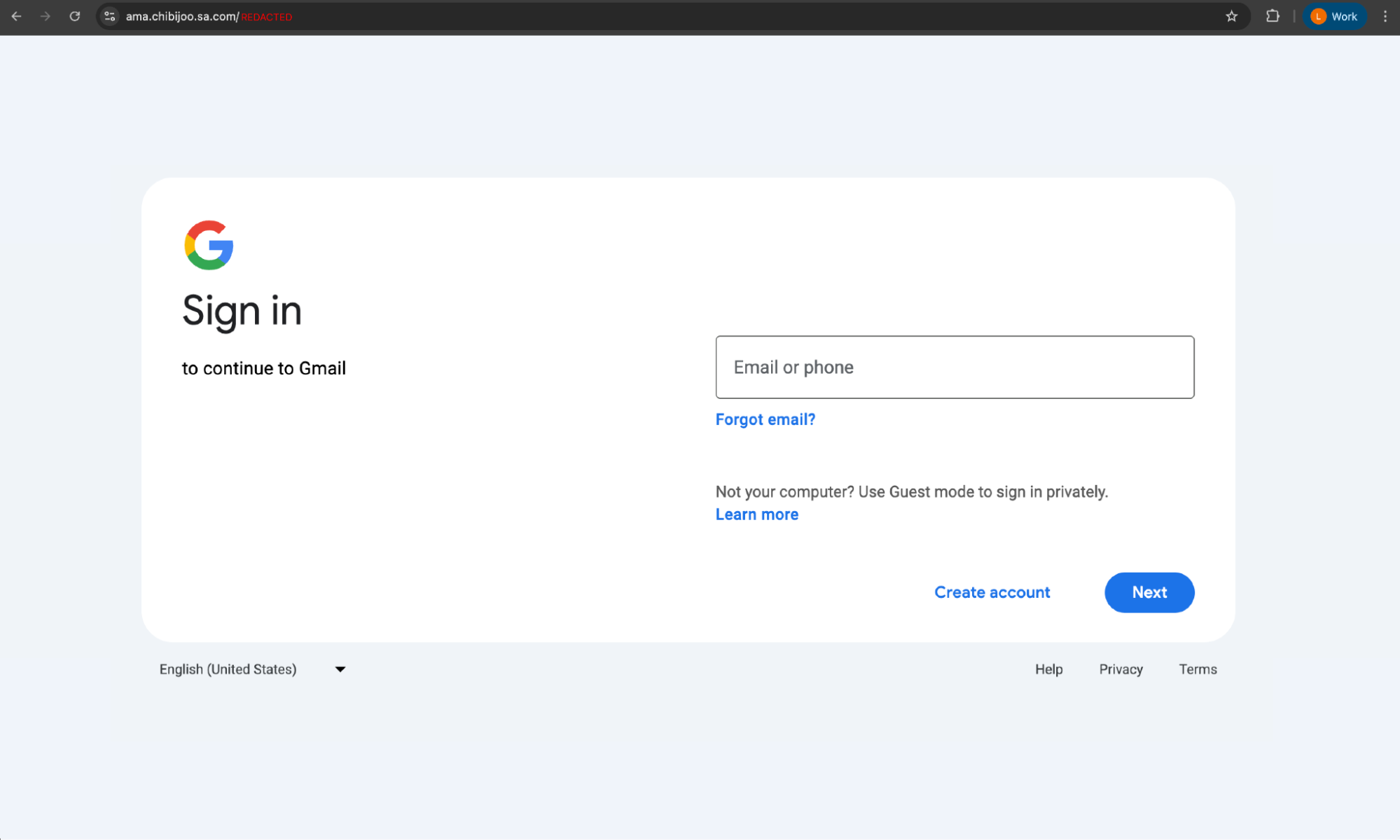
This detection was hooked by the customer’s security lake to trigger their security incident response workflow for further investigation. Push’s timelines feature ensured that the full chain of URLs accessed and actions performed on different pages could be analyzed by the security team.
Notable techniques
This attack featured a number of notable attacker techniques designed to evade common phishing detection controls.
Delivering the phishing lure via LinkedIn
Using social media sites like LinkedIn to deliver a phishing message has a number of advantages for the attacker. Generally, users are less alert to phishing attempts on social platforms, particularly those like LinkedIn which are used for personal as well as work purposes.
However, the primary benefit of delivering phishing over LinkedIn is to evade email-based detection controls. With modern email security tools conducting various stages of analysis, such as analysing the URL, attempting to inspect the page in a web sandbox, and analyzing the written content of an email for possible malicious intent, it can be easier for attackers to simply bypass email altogether.
With modern work communications now happening over several platforms, sites like LinkedIn where users can be directly messaged by people outside the organization, but are often accessed from work devices, are a prime target.
Using legitimate, trusted sites to host links
Attackers are increasingly using legitimate sites to host their phishing links and perform redirections. Fronting phishing attacks with pages hosted on legitimate sites, in combination with lengthy redirect chains, can make it harder for security tools which rely on analysing the initial page served to the victim. In this example, Google Sites, Google Search, and Microsoft Dynamics were used.
Using bot protection to defeat sandbox analysis tools
Email and proxy security tools rely on loading a page in a web sandbox to analyze it for properties matching their detection signatures. However, dynamic elements that require user interaction to proceed are known to break these sandboxes. The most common way of attackers doing this is by using legitimate bot protection technologies such as CAPTCHA and CloudFlare Turnstile.
Performing layered redirects at different stages
As already mentioned, the chain of redirects across different sites was particularly notable in this case (you can see this in the timeline screenshot provided above). To maximize the lifespan of a malicious domain, attackers are known to use various redirection tricks (often though legit sites that are often excluded from scanning tools). Using several redirections before serving the malicious page to break referrer-based checks that are common in proxy solutions and prevent the initial URLs seeded out from being discovered. By obfuscating the initial URL delivered to victims, and both masking and rotating the phishing URLs, it is much harder for organizations to blocklist known-bad sites effectively.
Indicators of Compromise
Static IoCs are of limited value in this case due to the use of disposable pages designed to be used once and then rotated. In this case, the page hosting the malicious AITM kit has now been flagged by Google after being reported. This makes blocking specific malicious subdomains hosted on otherwise legitimate sites difficult. However, we have observed a consistent pattern in the attacks identified by Push:
Phishing lure delivered over LinkedIn
Link to sites.google.com page (e.g. sites.google.com/view/<INVESTMENTCOMPANY>-ai/home)
Link to Microsoft Dynamics page (e.g. [assets-usa.mkt].dynamics.com/...)
Link to (*).sa.com phishing page
Given the targeted nature of the attack, we recommend hunting for executive-level users accessing some combination of these URLs (and variants) in a short timespan.
We also recommend informing your executive team about the rise in LinkedIn phishing attacks and the specific nature of the investment opportunity lure.
Impact analysis
There aren’t many more valuable accounts than those belonging to your company executives. Compromising a Google Workspace account doesn’t just give the attacker access to the Workspace tenant, emails, chat, etc. — it also grants access to any accounts on downstream apps configured for SSO. The blast radius of such a compromise is pretty widespread, giving plenty of scope for further exploitation for an attacker with a clear idea of what they want to achieve.
In short, stopping this attack at the earliest opportunity was a significant benefit. Even if the attack had been later stopped following the compromise and the stolen account reset, unpicking the web of potentially compromised downstream accounts that may have been accessed and backdoored by the attacker (such as by configuring stealthy persistence mechanisms like evil twin integrations, API keys or other ghost login methods) presents a sizable overhead for the security team.
Learn more about Push
Two key features played a part in this detection, which you can read more about below:
Push doesn’t detect the redirect tricks or rely on outdated domain TI feeds. The reason we detect these attacks (which make it through all the other layers of phishing protection) is that Push sees what your users see. It doesn’t matter what delivery channel or camouflage methods are used, Push detects and blocks attacks by identifying the attack in real time, as the user loads the page in their web browser.
This isn’t all we do: Push’s browser-based security platform provides comprehensive detection and response capabilities against the leading cause of breaches. Push blocks browser-based attacks like AiTM phishing, credential stuffing, password spraying and session hijacking using stolen session tokens. You don’t need to wait until it all goes wrong — you can also use Push to find and fix vulnerabilities across the apps that your employees use, like ghost logins, SSO coverage gaps, MFA gaps, vulnerable passwords, risky OAuth integrations, and more to harden your identity attack surface.
If you want to learn more about how Push helps you to detect and stop attacks in the browser, book some time with one of our team for a live demo.


