Attackers like Scattered Spider are tricking help desks into reseting MFA on sensitive apps. Find out how Push can stop them in the browser.
Attackers like Scattered Spider are tricking help desks into reseting MFA on sensitive apps. Find out how Push can stop them in the browser.
Scattered Spider has shown the world the devastating effects attackers can achieve by socially engineering IT help desks into performing MFA resets so they can take over accounts on sensitive corporate apps.
That’s why we’re introducing Employee Identity Verification Codes — a simple, browser-based identity check that gives your help desk a reliable way to confirm they’re talking to someone from your organization.
Push now provides your employees with a rotating 6-digit verification code in their browser via the Push Security extension. When an employee contacts your IT help desk to request an MFA reset or access recovery, the help desk can ask for this code to verify their identity — ensuring it’s really them, and not an attacker.
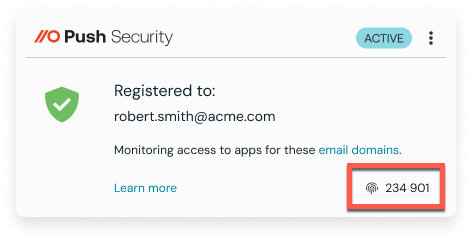
The employee identity verification codes are:
Session-aware - generated in users’ browsers and only visible to them when they click on the Push Security extension icon in their browser toolbar.
Rotating: they change every 24 hours
Lightweight: no additional apps or devices required
It’s a fast, simple verification method — directly in the employee’s browser — that addresses a real-world threat.
We think it’s swell, but don’t just take our word for it …
Eric Rubin — a Senior Manager in GitLab’s Corporate Security team — has already rolled out Employee Identity Verification Codes across his workforce. Here’s what he had to say about it:

Thank you, Eric!
Why are help desk identity verification methods so hot right now?
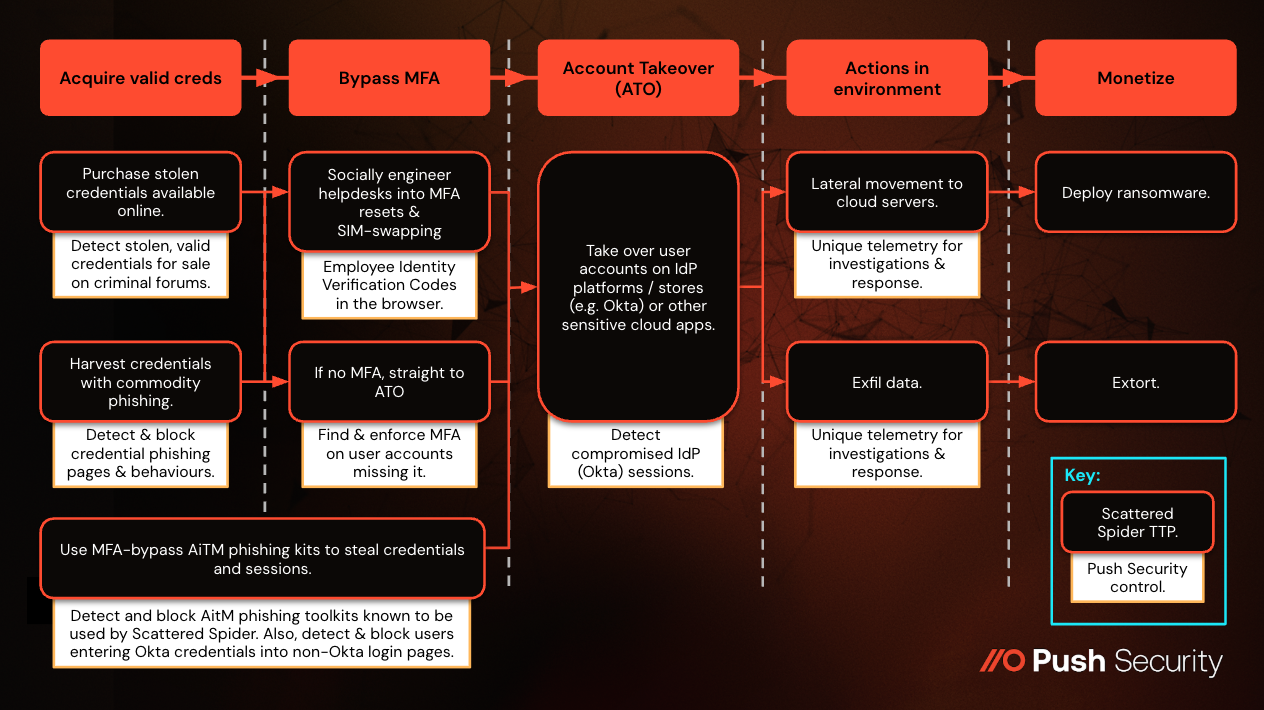
A number of the high-profile incidents attributed to the Scattered Spider cybercriminal group saw them socially engineer IT help desks into resetting MFA on employee accounts that they had already acquired valid credentials for. These compromised accounts were typically on IdP systems like Okta providing SSO access to large numbers of downstream applications.
Case study: The MGM Resorts breach
One of Scattered Spider’s most notorious and well-documented attacks was against MGM Resorts. Scattered Spider socially engineered MGM Resorts’ help desk personnel to bypass MFA and log in to accounts for which they had acquired valid login credentials via credential phishing and historical infostealer compromises.
They specifically targeted accounts with Super Administrator privileges within MGM Resorts’ Okta tenant, which they then used to register a second, attacker-controlled IdP via inbound federation. This then enabled them to impersonate any user within the Okta tenant.
The attackers were then able to abuse SSO access to downstream apps and platforms from various accounts, culminating in deployment of ransomware to around 100 ESXi servers and data exfiltration.
The breach resulted in a 36-hour outage, a $100M hit to its Q3 results, one-time cyber consulting fees in the region of $10M, and a class-action lawsuit later settled for $45M.
Reassessing help desk verification processes
Scattered Spider’s high-profile attacks — including its most recent against UK retailers Marks & Spencer’s and the Co-op — has prompted many security teams to reassess the verification processes used by their IT help desks when an employee requests an MFA reset or access to sensitive applications.
Initial guidance from across the industry included the use of call-back verification for any MFA or credential changes requested by an employee. However, Scattered Spider are also known to use SIM-swapping to trick mobile carriers into transferring a victim’s phone number to a SIM card controlled by the attacker - thereby allowing them to intercept verification calls.
Simple verification using your employees’ browsers
Push already provides several controls that directly align to the other TTPs used by Scattered Spider. They include detecting stolen credentials, cloned login pages, AitM toolkits and compromised IdP sessions.
(BTW, if this piques your interest, you can stream our latest webinar where we deep-dive into Scattered Spider, how their TTPs are evolving in 2025, and what Push is doing to protect organizations against them.)
But to provide our customers with an additional layer of defense against the Scattered Spider attack chain, we wanted to see how we could make it harder for attackers to socially engineer IT help desks into gaining access to IdP systems and sensitive apps.
As so often is the case, the answer was staring us right in the face - we can use our browser extension. By placing a verification code in the details tray of every employees’ Push extension, they can use that to verify their identity with their help desk team.
Get started today!
Employee verification codes is a Labs feature, which means it’s available on an early-access basis. We're particularly interested in hearing your feedback on how to develop this feature further.
You can enable Labs features by going to the Settings page of the Push admin console and choosing the Labs tab.
We're also offering this feature as a free tool for security teams that aren't currently Push customers, but want to start using this browser-based verification code as part of their help desk caller identification process.
If you’d like to find out more about this feature, and the other ways Push is stopping identity attacks in the browser, book a demo with one of our team.


