After a successful phishing campaign against Office 365 and Google Workspace users, a malicious mail rule can be automatically created in the user’s mailbox that forwards sensitive emails to an external address. Learn the best way to protect your company.
After a successful phishing campaign against Office 365 and Google Workspace users, a malicious mail rule can be automatically created in the user’s mailbox that forwards sensitive emails to an external address. Learn the best way to protect your company.
Mail rules are a handy feature found in most email clients. You might have used them to forward emails to your teammates while you’re off sipping Piña coladas, or to move incoming email from that spammy colleague to the ‘don’t read’ folder.
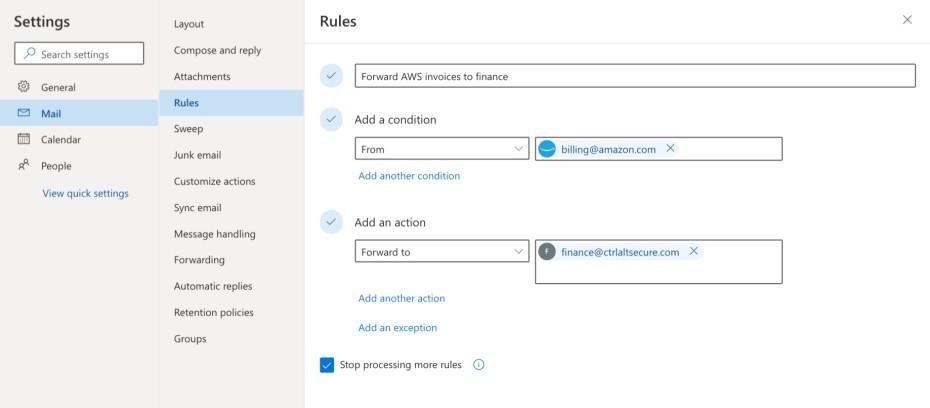
Sadly for us defenders, they’re just as useful for attackers. After gaining access to a victim's account, attackers will often create a mail rule inside their mailbox as a way to maintain stealthy access. This mail rule can do anything a normal mail rule could but is usually used to forward emails matching sensitive keywords, like ‘invoice’ or ‘payment’, to an external email address controlled by the attacker.
This gives the attacker persistent access to the mailbox. Even if the victim's password is changed, they turn on MFA, or their workstation is completely rebuilt - as long as the rule stays in place, it remains effective.
As another example, in this Reddit thread the author describes how mail rules were used to delete any emails the affected user received from the company’s Chief Finance Officer (CFO) so that the attacker could pretend to be the CFO, sending them fake emails to convince them to transfer out company funds.
Business Email Compromise (BEC) like this is the most popular type of attack at the moment, causing damages well into the billions according to the FBI. Here are just a few publicly documented breaches involving mail rules:
FBI report: BEC involving malicious mail rules costs company $175k
Reddit thread: Hacker created forwarding rule for user's account
You can read this case study of a how a real Business Email Compromise (BEC) attack played out at an engineering firm that we interviewed.
How likely is this to actually happen?
MITRE lists threat groups that have been known to use mail rules in this way as part of targeted attacks. However, most often, this technique is used opportunistically.
Attackers run phishing campaigns containing thousands of harvested emails from multiple companies. A classic scenario is to trick a user into logging in to a fake Office 365 or Google Workspace login screen, stealing their credentials. Those credentials are then used to create a malicious mail rule inside the compromised user's mailbox. For scale and speed, this process is completely automated.
Similarly a mail rule could be created automatically as the result of a user’s workstation becoming infected with malware.
How to defend against this type of attack?
The first step is to check your mailboxes to make sure no malicious mail rules have already been created. On Office 365, this will require rolling some PowerShell; on Google Workspace, you'll need to query the APIs (we discuss some detail of these options in this post). Or you can save yourself some pain and use the free tool linked above, which we built for this very purpose. If you find rules that don't look right, follow these guides for what to do next on Office 365 or Google Workspace.
It's also possible to stop users from creating auto-forwarding rules altogether. If no one is using the feature, this is probably a good idea - you might as well reduce risk. However, there are plenty of situations where teams benefit from the automation and efficiency mail rules bring. Security works best when it enables the business to work securely, rather than constraining it - leaving the feature available whilst managing the risk through detection is a good option as well.
We discuss more about the pros and cons of disabling mail rules and some options for some security controls you can implement so that you can keep them enabled in this blog post.
If you'd like, try Push for free and we'll spot any suspicious mail rules, then work with employees to make sure the mail rule wasn't something they created for a legitimate use. If they haven't, we'll notify you to take action and investigate a potential incident. Find out more here.
Learn more
It doesn’t stop there — Push provides comprehensive identity attack detection and response capabilities against techniques like credential stuffing, password spraying and session hijacking using stolen session tokens. You can also use Push to find and fix identity vulnerabilities across every app that your employees use like: ghost logins; SSO coverage gaps; MFA gaps; weak, breached and reused passwords; risky OAuth integrations; and more.
If you want to learn more about how Push helps you to detect and defeat common identity attack techniques, book some time with one of our team for a live demo.


