What is Conditional Access?
Conditional Access is about more than MFA. Conditional Access is, quite literally, a number of conditions you define to permit access. One of those conditions can be requiring MFA. But, it could also include where a user is logging in from, what the user is trying to access, the device they are using, group membership, or any combination you choose.
If your users have Azure AD Premium P1 licenses, we recommend you use Conditional Access. Although setting it up requires a few extra steps, it's quite straight forward to make a sensible baseline configuration and you'll have the flexibility to make exceptions and extensions as necessary.
This means you could build up very complex Conditional Access policies if you choose to. However it is commonly used to simply mandate MFA except in certain scenarios e.g. accessing a non-sensitive app, or using a break-glass accounts.
Microsoft continues to invest in Conditional Access and it is clearly their preferred route for you to take if you can. For more information, read a more in-depth overview of Conditional Access from the official source.
If you choose Conditional Access we will show you how to prepare the necessary parts of your environment and guide you to sensible starter policies, which you can initially set to audit mode. While using the Push platform's automations to encourage users to register for MFA, you can monitor audit logs to have complete assurance no one will be impacted when you switch to enforce mode.
See Microsoft documentation: Common problems with two-factor verification and your work or school account
Let's get started!
Configuring your environment
Before using Conditional Access to enforce MFA, you'll need to do the following:
Block legacy authentication is one of the Conditional Access policies we recommend at a minimum. This is because, even if you are using MFA elsewhere, legacy authentication can't use MFA so, if it is still enabled, attackers will take aim at legacy protocols to bypass MFA.
Before you can block legacy authentication, you must make sure no one in your organisation is using it. For example, does anyone use Office 2010 or 2013 still? Office 2010 doesn't support modern authentication and Office 2013 doesn't use it by default. Blocking legacy authentication without first modernising any legitimate use will likely break things in your team.
Depending on the age of the your Azure AD tenant, you might need to also enable modern authentication.
Follow the official Microsoft documentation on blocking legacy authentication that includes steps to find accounts that still use legacy authentication, and instructions to enable modern authentication.
If you are curious about what legacy and modern authentication is and want more background, read this blog post by the Microsoft Identity team.
With the many options of Conditional Access, designing policies can be overwhelming.
However, to start, Microsoft has a number of "Common Conditional Access Policies" (see below) that we recommend you implement at a minimum.
Each policy should be put into "Report-only mode" initially, such that it isn't enforced, but only audited. This allows you to safely check the impact of a policy before moving to enforcing later in the process.
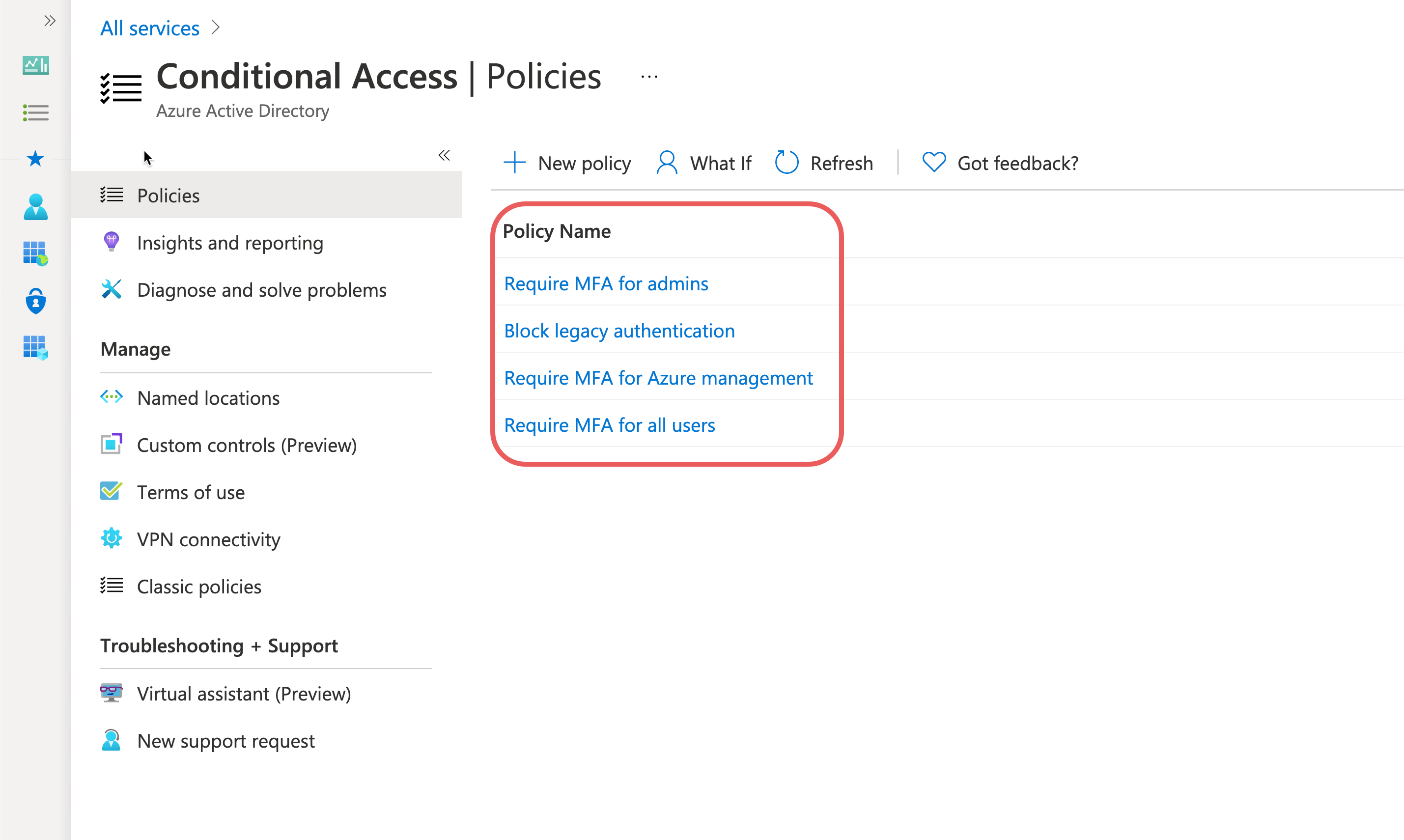
The Common Conditional Access Policies we recommend are:
Depending on your requirements, you could permit only certain MFA methods. Microsoft defaults to sensible and secure options: app notification, app code or hardware token. We recommend keeping these defaults unless you have a good reason.
If you do need to change these settings, you must do so via the legacy MFA portal, as described here.
Want to learn more about MFA methods and choosing the right option for you? Read more on our blog.
Get your users registered for MFA with minimal effort using the Push platform
Before enforcing MFA, you should aim to get most users registered for MFA to avoid disruption but figuring out who needs to register and engaging with each of them is a hugely time-consuming process.
Use the Push platform to quickly see who hasn't registered for MFA yet and use ChatOps to engage with them automatically to get it done with ease.
Enforcing MFA
Now you've defined your policies and your users are mostly registered, all that's left to do is to turn them on. Follow these steps to enable a Conditional Access policy:
Step 1
Go to the Conditional Access blade in Azure Active Directory admin center.
Step 2
Select the Conditional Access policy you want to enable:
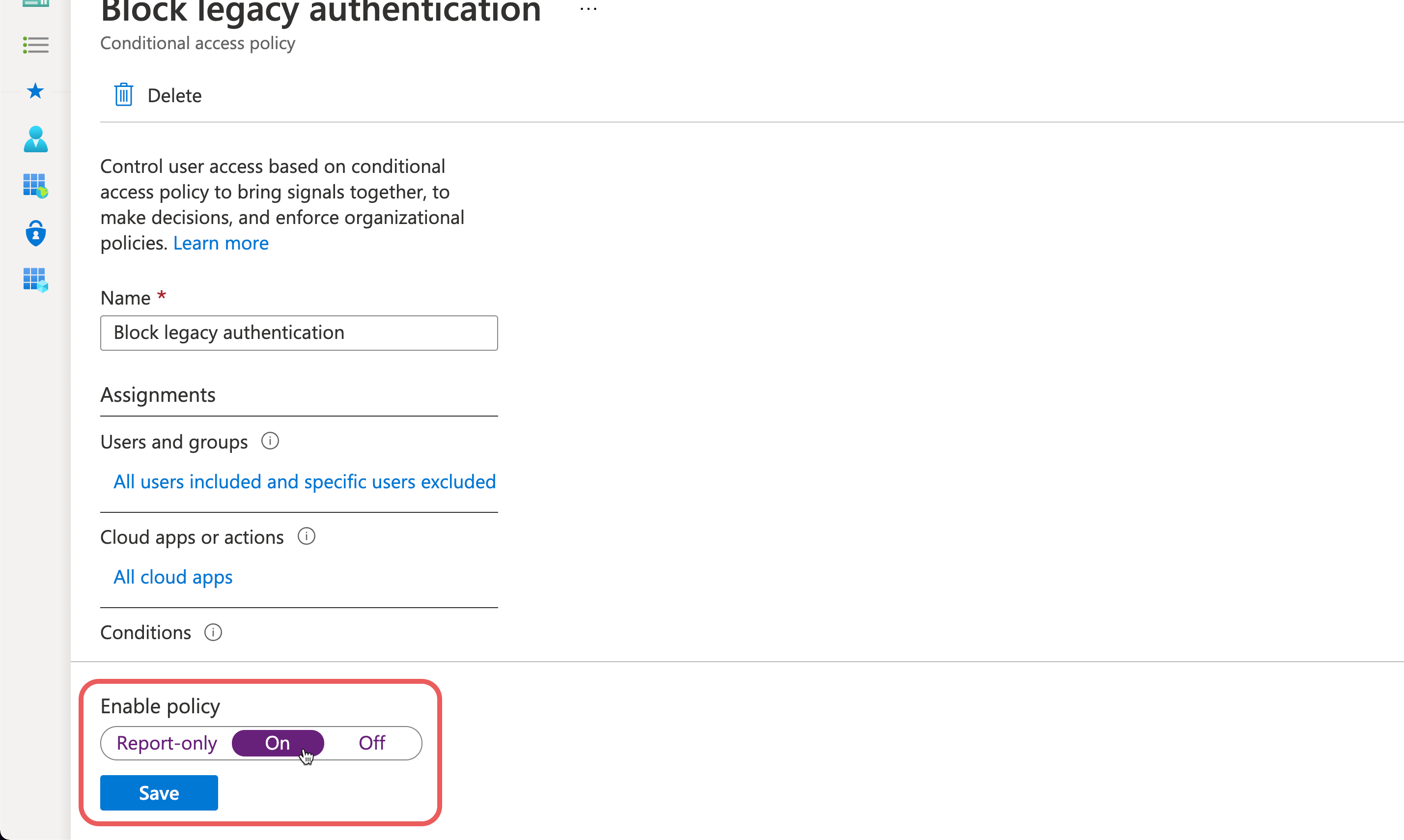
Step 3
At the bottom of the screen, under "Enable policy" select "On".
Hit Save.