Guide to reviewing and classifying SaaS apps
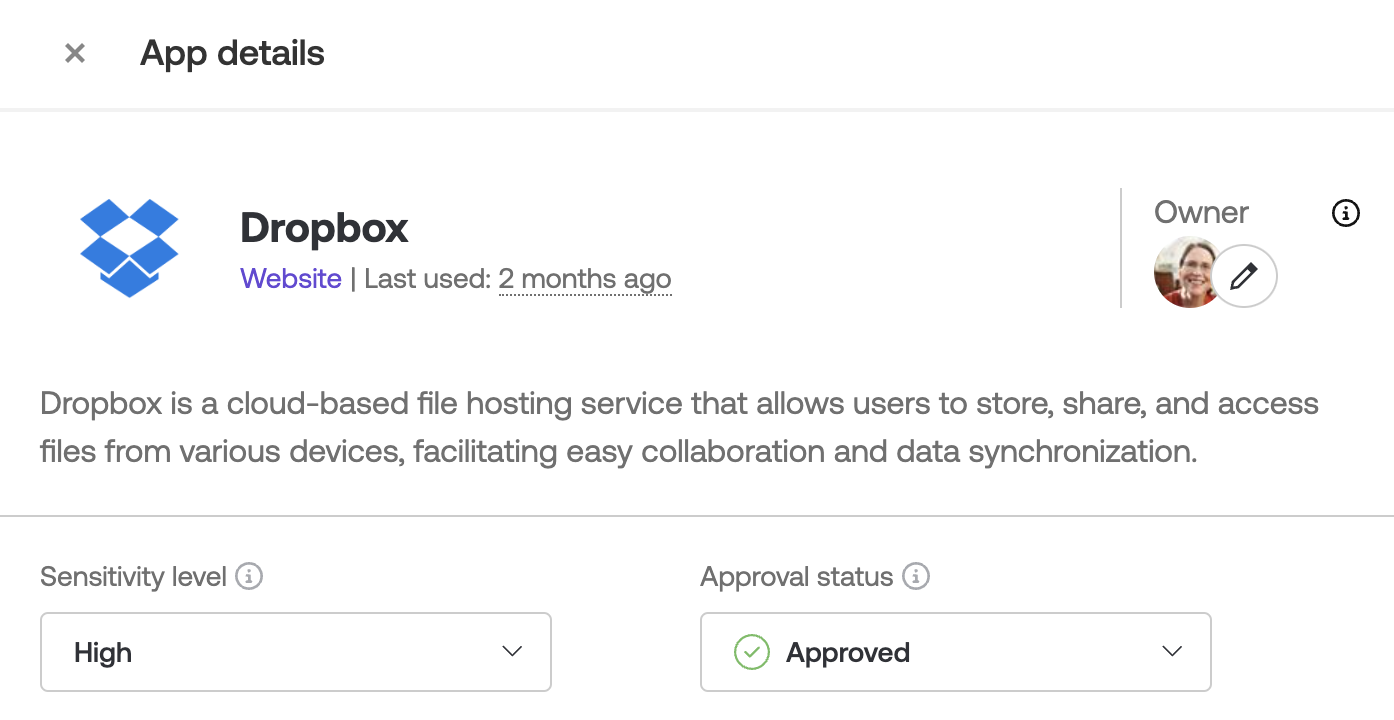
You can use Push to classify the sensitivity level of individual apps and capture app approval decisions directly in the admin console by using the Sensitivity level and Approval status fields for an app.
Note: Categorizing an app does not currently trigger any automatic actions in Push.
Here are a few tips on approaching an app review and classification exercise.
Overview
Of course, you can use these app classifications however you like. We think a useful way is to think about app risk assessments in two stages.
First: When Push discovers a new app in your environment, you can quickly capture its sensitivity level based on the data in the app, and the permissions the app needs in order to work.
This should be a quick estimate or gut check.
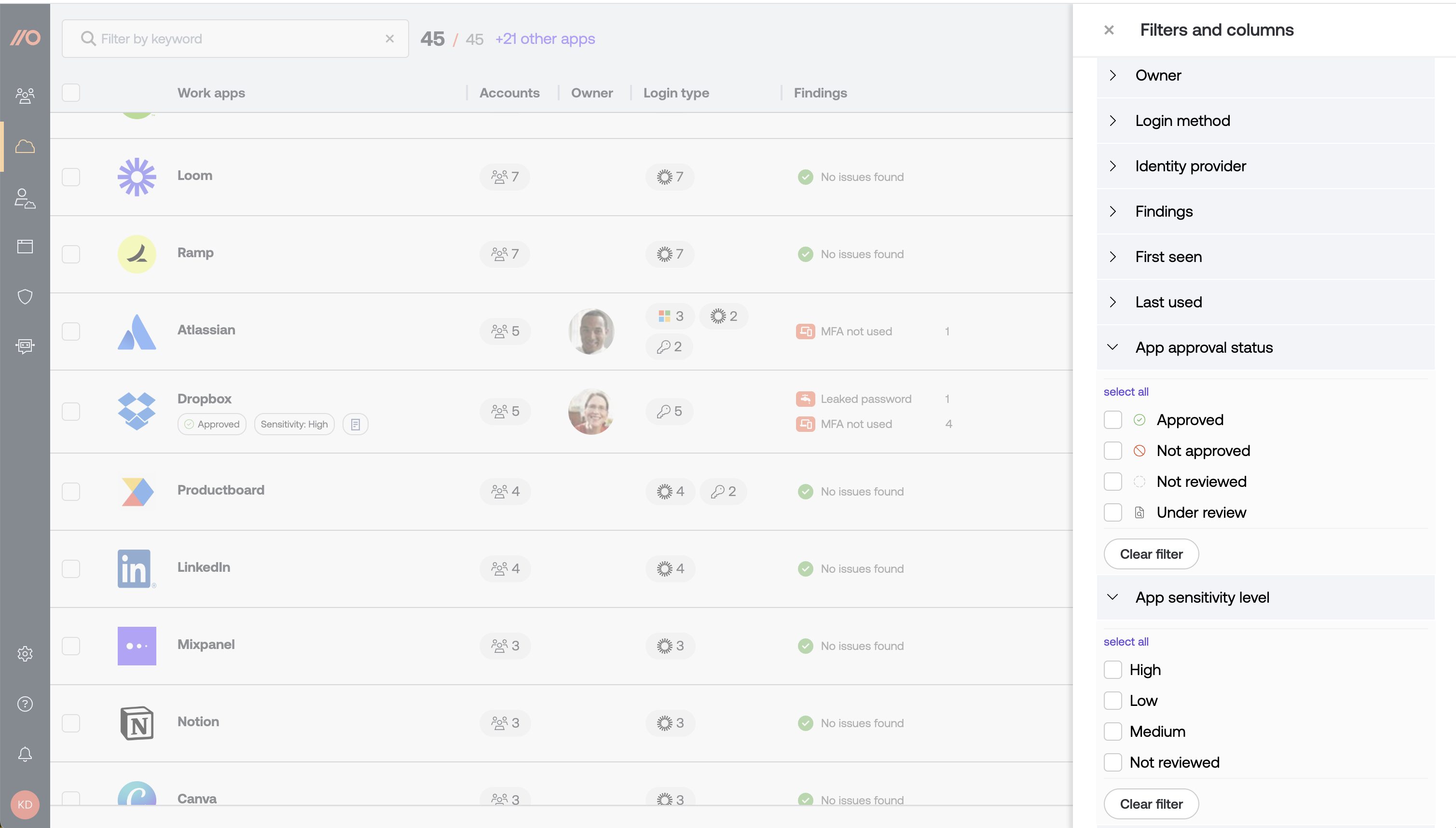
Second: Use the app sensitivity information to prioritize your risk assessment process. You can use the filters in Push to sort the SaaS page by apps that are Under review or Not reviewed, then sort by the Sensitivity level to find the most sensitive apps that are still in use. Use the Last used field on the SaaS details panel to find apps that are actively in use.
Once you’ve completed your risk assessment or due diligence and have decided whether an app is approved for use, you can capture your decision with the Approval status field.
Here is a step-by-step approach following this method:
Set up channel notifications
If you haven’t already, we recommend setting up notifications in Slack or Microsoft Teams so you can see when Push discovers a new app in your environment.
Reviewing an app is easier when it has just been adopted rather than waiting until it’s established and may be more difficult to deprecate, should you decide to get rid of it.
Assess the sensitivity level
For each newly discovered app, take a look at the app’s homepage to get a sense of the data in the app. Think about whether the app will likely contain customer data, financial data, API keys, code, or other valuable assets.
You might also check to see if a third-party integration was created to give this app other permissions through an integration. You can see this in Push by going to Investigate > OAuth apps.
Do a quick assessment of the sensitivity level of this data for your organization— Low, Medium, or High — and then set the level.
Plan your risk reviews
When you’re ready to review each app in more detail, sort the list by high-sensitivity apps that haven’t been reviewed yet.
You might also consider the last used date to choose where to start. Highly sensitive apps that are still actively used are a good place to start.
Set the approval status
When you’ve completed your risk assessments, capture your decision about an app by setting an approval status of Approved or Not approved.
If you’re still reviewing an app, you can mark it Under review.
Decide on next steps
You can now use your classifications to prioritize resolving security findings on high-sensitivity apps. From the Apps page, use the filters to see apps with a Sensitivity level of High and that have accounts with security findings.
You can also filter by apps with an Approval status of Not approved and a Last used date in the recent past to find unapproved apps that are still being accessed. Use an app banner in the Push platform to communicate that an app is not approved for use directly to your end-users.