How does Push determine if a password is weak, leaked, or reused?
Push can identify when an employee is using a weak, leaked, or reused password to log into apps.
Weak passwords are easily guessable, based on a list of common base words, in addition to any words explicitly restricted by an administrator. Leaked passwords have been exposed in a data breach. Reused passwords are being used on more than 1 app.
If Push has identified a password finding, you’ll see a finding type of Weak password, Leaked password, or Reused password when viewing the employee’s details in the Push admin console. These findings also appear on the Accounts page for individual app accounts.
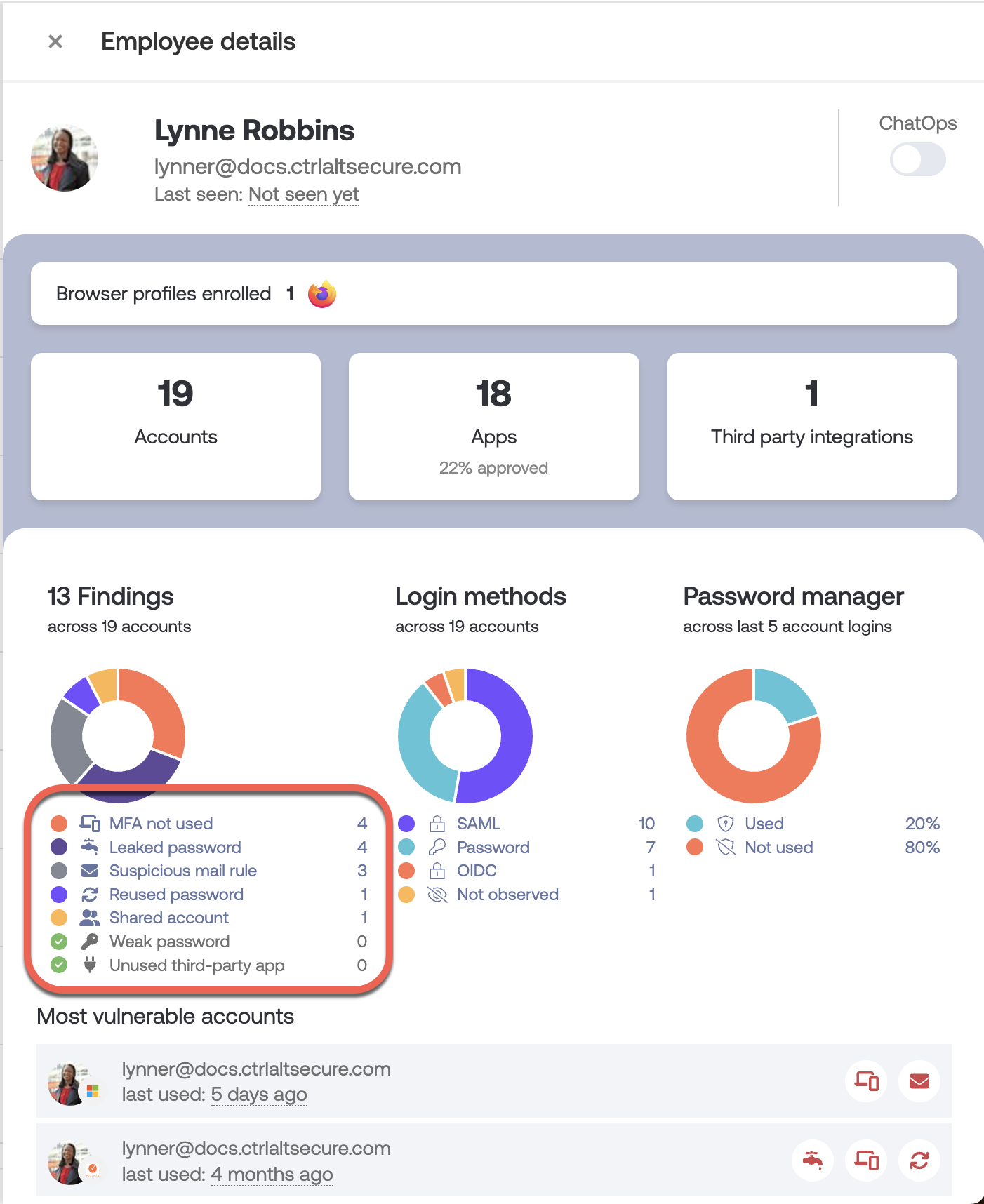
How Push identifies weak passwords
To determine if a password is weak, the Push browser extension checks the password against:
A list of top 10,000 weak base passwords
Number and special character variations on these weak base passwords, for example: Password1!, January2022
Variations on these weak base passwords that replace letters with numerals (1337), for example: P455w0rd.
Whether the weak password contains words restricted by an administrator.
This type of password security check occurs automatically as the browser extension observes logins for your monitored domains. You can find the list of top 10,000 weak base passwords used in the Push browser extension on Github.
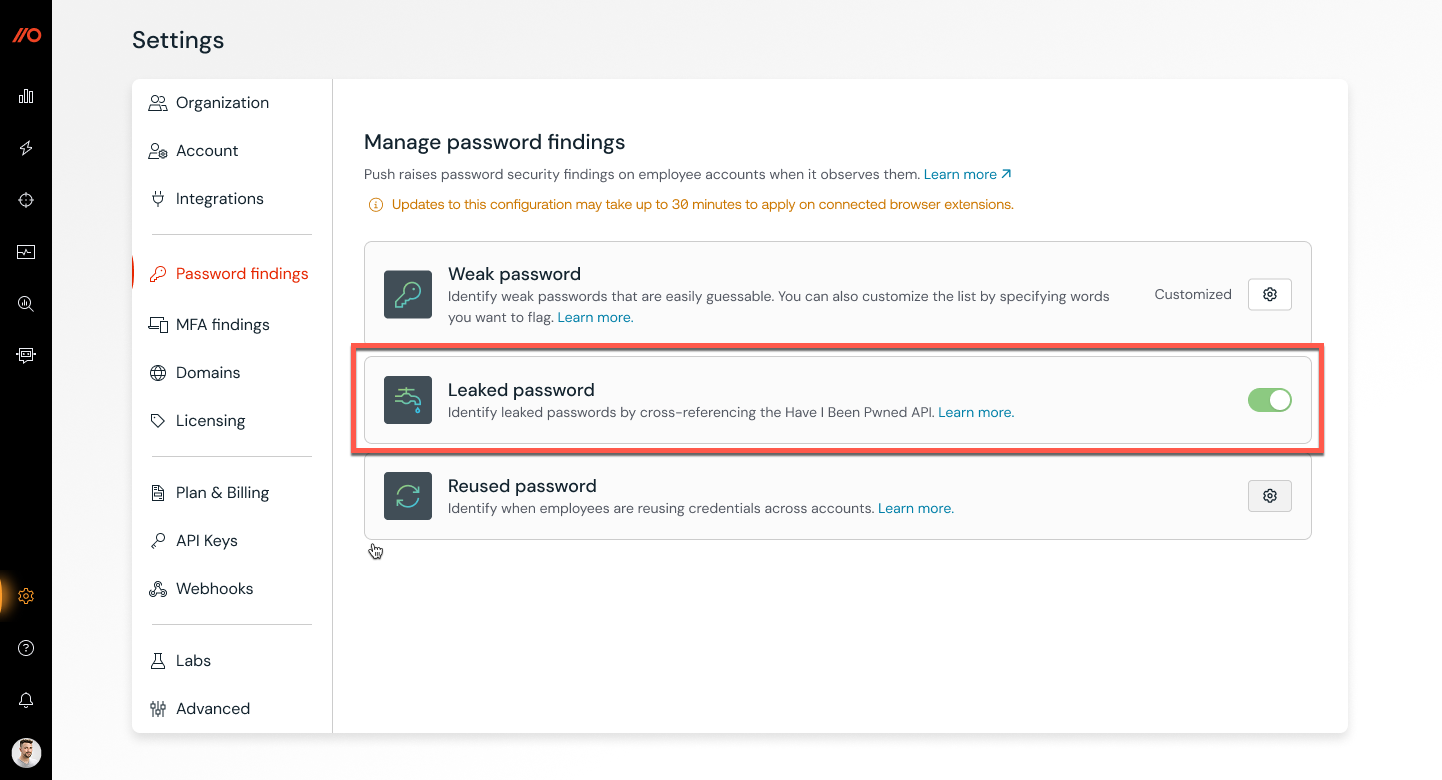
You can add your own custom list of restricted terms in the admin console by going to Settings > Password findings and configuring the Weak password finding type.
How Push identifies leaked passwords
To determine if a password has been exposed in a data breach, the Push browser extension queries the Have I Been Pwnd (HIBP) API. You can enable this feature in the admin console by going to Settings > Password findings > Leaked passwords.
Push creates a hash of the passwords it observes (e.g. fingerprints) and then sends the first few characters of the password hash to the Have I Been Pwned passwords API. The API returns all leaked password hashes that begin with those initial characters, and then Push checks for matches. This ensures HIBP never sees the full hash that is being checked. Learn more about the process in this article.
If the Push browser extension observes the use of a leaked password, we flag it for remediation. This essentially means that the account is using a password that has previously been exposed in a data breach, but not necessarily for that email address.
Push also provides a stolen credential detection feature to raise detections when a compromised password for a given account is discovered. This feature correlates threat intelligence feeds consisting of stolen username and password combinations for sale on criminal marketplaces with accounts actively being used by an employee.
How Push identifies reused passwords
Push compares password fingerprints to those it has previously observed. If a match is found, Push generates a reused password finding for that employee and their relevant accounts.
Note that Push can also prevent employees from reusing passwords for important apps with the Password protection control. Refer to this help article for more information.
Configuring exceptions
If you wish to exclude apps from raising a Reused password finding in Push, you can configure an exception. This is useful if you purposefully sync passwords between systems, such as an app and your identity provider.
For instructions on configuring exceptions, refer to this help article.