SaaS Security is focused on securing sensitive data that’s stored in or integrated with the SaaS applications the company and its employees use.
SaaS Security is focused on securing sensitive data that’s stored in or integrated with the SaaS applications the company and its employees use.
SaaS security is a common phrase, but what does it mean? There are several categories of security products that do bits of “SaaS security,” but the phrase means different things to everyone, and there’s a lot of jargon to demystify in this space.
A quick Google search for “SaaS security” pulls in all types of security solutions and platforms, including those under these categories: cloud access security brokers (CASB), SaaS security posture management (SSPM), cloud security posture management (CSPM), and a few others.
When you’re on the hook to secure SaaS use in your company, it can be hard to even know where to start and where to focus. We hope this article helps you get some clarity about where you should focus and how to manage the risk in a sustainable way with your limited resources.
Let’s start with a quick, high-level definition.
What is SaaS security?
SaaS Security is focused on securing sensitive data that’s stored in or integrated with the SaaS applications the company and its employees use.
When it comes to managing the risk SaaS security introduces, people are really talking about two things:
Managing supply chain risk - Do you trust the vendors of the applications you’re using?
SaaS account security and access controls - Are you using those applications securely?
Where should I focus my efforts?
We hear about the supply chain side of SaaS security more often than the account security aspect, likely because supply chain attacks have a much wider blast radius and are therefore the attacks that are getting detected and disclosed to the press.
These are the far-reaching attacks that might start with a platform that many organizations use for business (Salesforce, for example). If that SaaS platform is compromised, every company’s data is compromised, including your own. These things aren’t something you can directly prevent from happening.
SaaS account security, however, is something you have control of and you can lock down.
Focus on SaaS security at the account level, but don’t ignore supply chain risk
As a security leader, you need to deal with both halves of SaaS security. On the supply chain side, you need to investigate whether you trust the SaaS providers themselves and the security measures they use to look after your data. The SaaS vendor is best suited to manage the risk of their own app itself, but you do need to do due diligence on the supplier to ensure they’re doing enough to comply with your organization’s risk tolerance level.
The bit you have direct control over, however, is the account security aspect of SaaS security. That’s a great area to focus on when it comes to SaaS security. You can enforce strong access controls and security basics like making sure employees use multi-factor authentication (MFA) and strong, unique passwords - or, better yet, social logins - to access their SaaS applications.
Let’s break down how a SaaS security program could work in your organization. Keep in mind, this may be closely tied to your cloud security program, but they’re two unique areas to focus on if you’re a SaaS-native or hybrid company that’s moving away from centralized infrastructure to the cloud and SaaS applications.
How do I build a SaaS security program in my organization?
The National Cyber Security Centre produced a shared responsibility model that does a great job of demonstrating the split between the SaaS provider’s responsibility when it comes to securing their app and the sensitive data put into it by their customers and the responsibility of the “customer” (you).
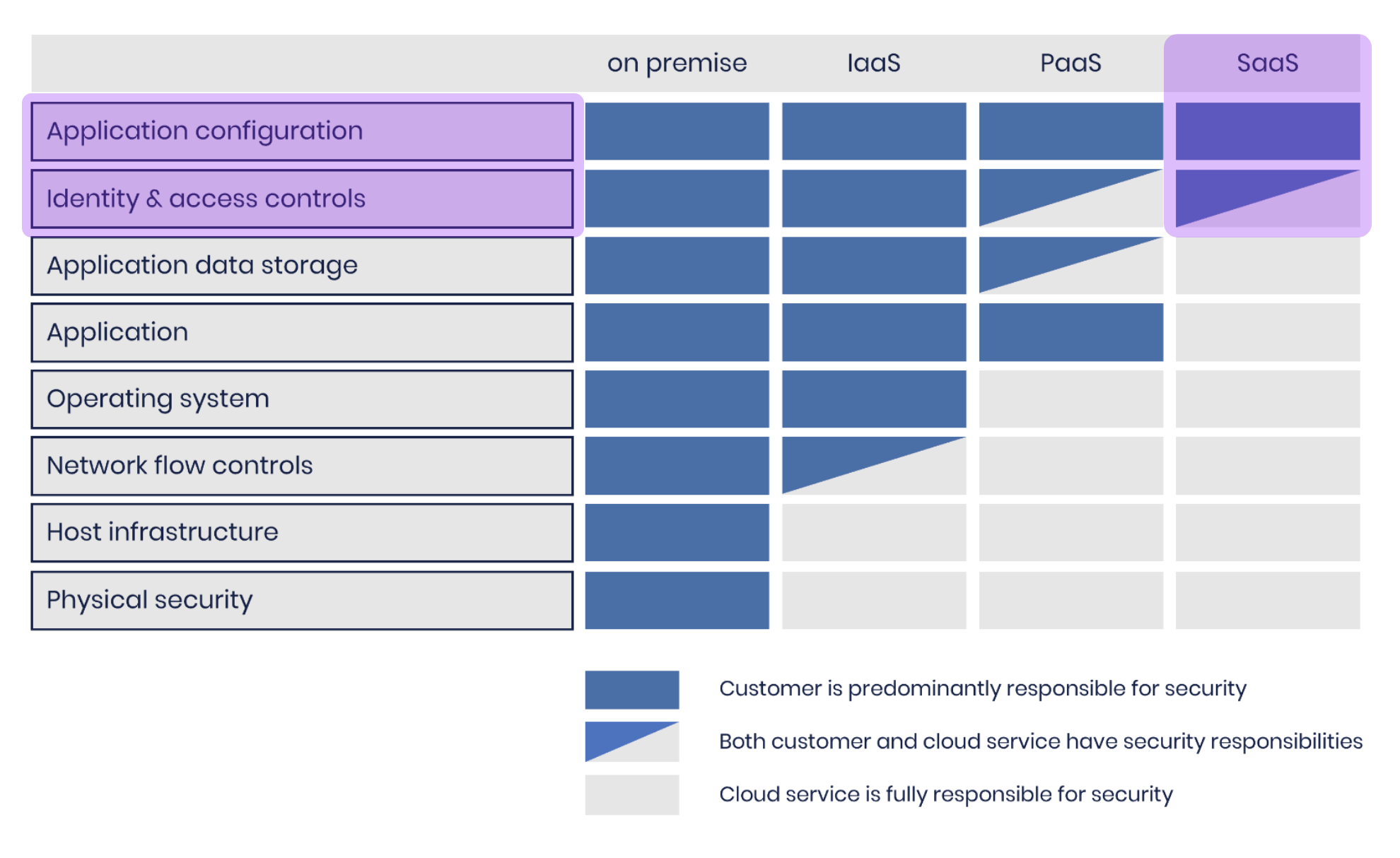
We’ve highlighted in purple the areas we’re focused on in this article. Let’s save on-prem, IaaS and PaaS for another article.
This bears repeating - What the model above shows is that you as the customer are responsible for security at the SaaS account level and you must also configure the application securely. When it comes to SaaS applications, however, your configuration options are usually very basic, especially compared to larger cloud platforms.
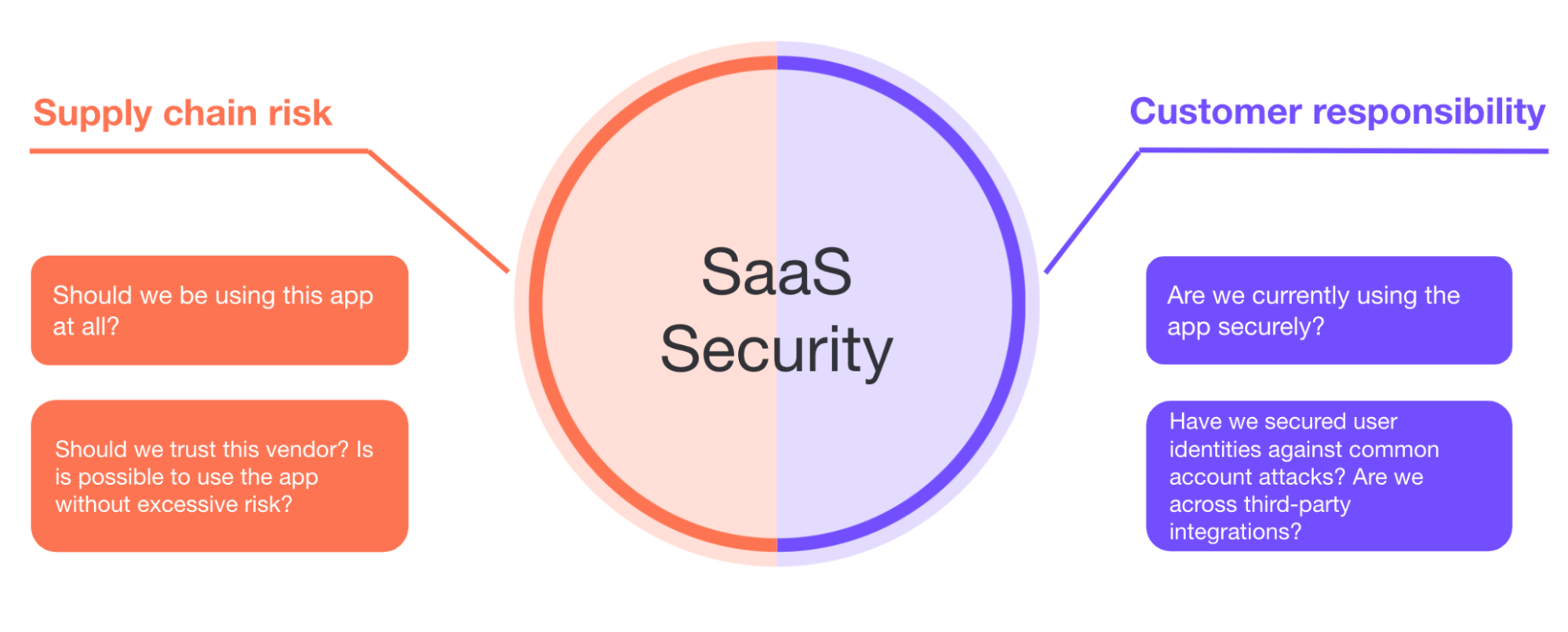
A successful SaaS security program must address both these questions.
We can’t spend all our time doing risk assessments and due diligence exercises on our supply chain while dropping the ball on account security.
Similarly, we can’t just focus on making sure all accounts have MFA in place when the vendor is leaving the back door open.
Make the biggest impact by securing SaaS accounts and identities
For the vast majority of SaaS applications in the organization, your responsibility will be:
Account security, i.e. making sure MFA and SSO (where available) is in place.
Ensuring employees are using strong passwords, especially if MFA and/or SSO aren’t available.
Removing external accounts (and accounts for those that have left the company) when no longer needed.
Customer responsibility for apps employees have adopted
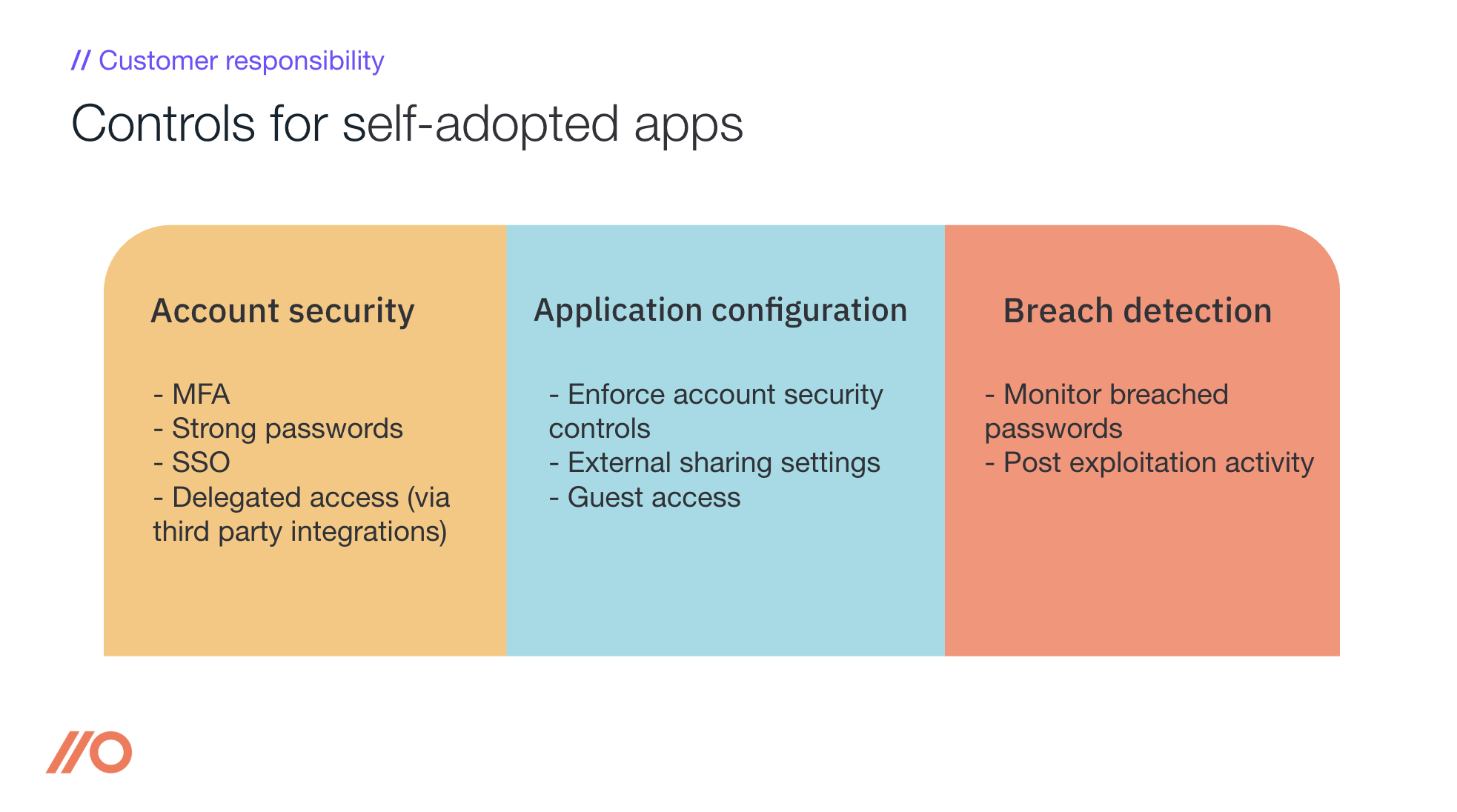
While most organizations think of the supply chain aspect (“Should we be using this app?”) as the majority of the problem, or at least the first problem to solve - account security is ultimately at the heart of the problem.
A developer or support engineer with a weak password or missing MFA is all it takes for them to get phished, kicking off a string of attacks.
The mistake many security professionals make, is that they focus their efforts only on securing the critical apps that are known to the organization. However, it is possible to compromise what would be considered as a non-critical SaaS application and use that to move laterally to the critical ones. See our research project discussing the various SaaS attacks.
Luckily, unlike the complex SaaS application supply chain risk audits, account security issues are straightforward to fix.
Right, but how do I also manage supply chain risk?
Security due diligence or app risk assessments are typically how you answer the question - Should we use this app?
These are standard processes for most organizations as part of a software procurement process.
However, security no longer fully controls software adoption - employees are self-adopting the tools they want without oversight.
So, you need to work to find serious security risks as soon as possible once the self-adoption process begins (normally by the first employee creating an account on the app).
Ultimately, how much you care about any of the above comes down to the risk of the data in the application (is there sensitive customer data in it?) or the level of access you grant this application into the rest of your infrastructure (often through integrations with other SaaS apps).
Therefore, a useful first step is to understand the sensitivity of the data and access granted to the app (or that will likely be granted by employees in future to make the app work as expected). This will help you prioritize reviews.
Tips for SaaS app and SaaS provider risk assessments
The security relevant areas of this risk assessment can typically be broken into:
Product risk
Does the product have the necessary security features (MFA, SSO, etc.) to protect our data, and
Has the product security been technically verified (e.g. through a third party penetration test)?
Vendor risk
Does the vendor have the resources to secure the product?
Have they invested in a security team and implemented appropriate security processes?
Have those processes been independently audited (e.g. SOC2)?
Does the vendor operate in a high risk region?
Does the vendor have a history of repeated security incidents?
Vendor sub processors - the majority of SaaS applications are built on other *-as-a-Service platforms. These vendors are also part of your supply chain. Just because you don’t directly use a tool or app doesn’t mean you’re not affected when they’re popped.
Realistically, you’re probably not going to be able to go very deep here, but when you’re wondering whether you’re affected by a breach in the news, you may want to know whether your vendors are using the affected SaaS app.
How to quickly assess security risks of employee-adopted SaaS applications
For employee-adopted SaaS platforms (those neither you nor the IT team had a hand in procuring and officially adopting on behalf of the company) you’re typically stuck doing your usual software procurement tasks after the app is adopted.
These include things like:
legal agreements (terms and conditions, master service agreements etc.)
spend (through licensing cost etc.)
uptime and availability (SLAs etc.)
Often, this comes up once employees need to upgrade to a paid account or higher license tier, or once it makes financial sense to commit to longer term agreements.
For that reason, I recommend you keep the security risk assessment focused on the direct security aspects initially, so you reduce the work required to determine if there’s a security reason to stop employees from using this app right now.
Managing SaaS account security for employee-adopted SaaS
Shifting the focus back to SaaS user account security, the very first step before you can even begin securing these accounts is to get visibility into all the apps your employees have adopted on their own. There are a few tools on the market to help with this. We’re obviously biased, but we feel that detecting SaaS use within the employees’ browser - where they’re accessing the app in the first place - is the most sensible and offers accurate visibility without a load of noisy false-positives. Read more about how we do this here.
I’ve got visibility, now what?
Once you’ve found the accounts, you’ll want to ensure that you’re:
Enabling MFA for all accounts
Encouraging employees to use strong passwords (ideally through a password manager)
Using SSO, where possible and practical
Reviewing access delegated to third-parties (through e.g. OAuth integrations)
These tasks are tricky to do at scale, where you’re likely to find hundreds of SaaS apps you didn’t know about. Most SaaS security solutions - those focused on security rather than just keeping an up-to-date inventory - will provide some insight into how employees are logging into SaaS apps and whether they’re using MFA and strong passwords. When you’re looking for a solution, this is the kind of actionable data you’re going to want if you want to make a real impact on SaaS security.
Choose the solution that works best for your company and team
The increase in employee-adopted apps has led to employees creating more accounts, on more apps. Without the guiding hand of security to make sure strong identity and access controls are in place, you’ll need a SaaS security solution that can give you that level of visibility so you can take action. Manage SaaS risks by leveraging a SaaS security platform that offers you not just visibility, but can also provide security relevant information about the SaaS app and the SaaS provider to help you quickly perform due diligence so you can keep up.

