Free and trial SaaS accounts are often invisible to security teams and interact with real corporate data.
Free and trial SaaS accounts are often invisible to security teams and interact with real corporate data.
The way we’ve adopted software in our businesses has shifted dramatically over the years due to the rise of the product-led growth (PLG) movement.
What is PLG and how does it lead SaaS sprawl?
In PLG, SaaS providers offer free trials and free versions to entice employees to sign up and immediately start using and testing their SaaS applications. SaaS vendors know they can close deals quicker if they can prove the value of their tool with their users - your employees - and “become sticky” with those users.
If vendors can make their cloud apps useful enough for employees to rely on them, it’s much harder for IT and security teams to swoop in and force a move to a more secure or similar SaaS application that another team in the company is already using.
This isn’t malicious, mind you - it’s just that vendors know that SaaS security audits and due diligence can extend their sales cycles and complicate their deals. Their quickest win is to get in with your employee and turn them into their champion within your company. Here’s a quick visual for how software onboarding typically flows in this PLG-ruled world:
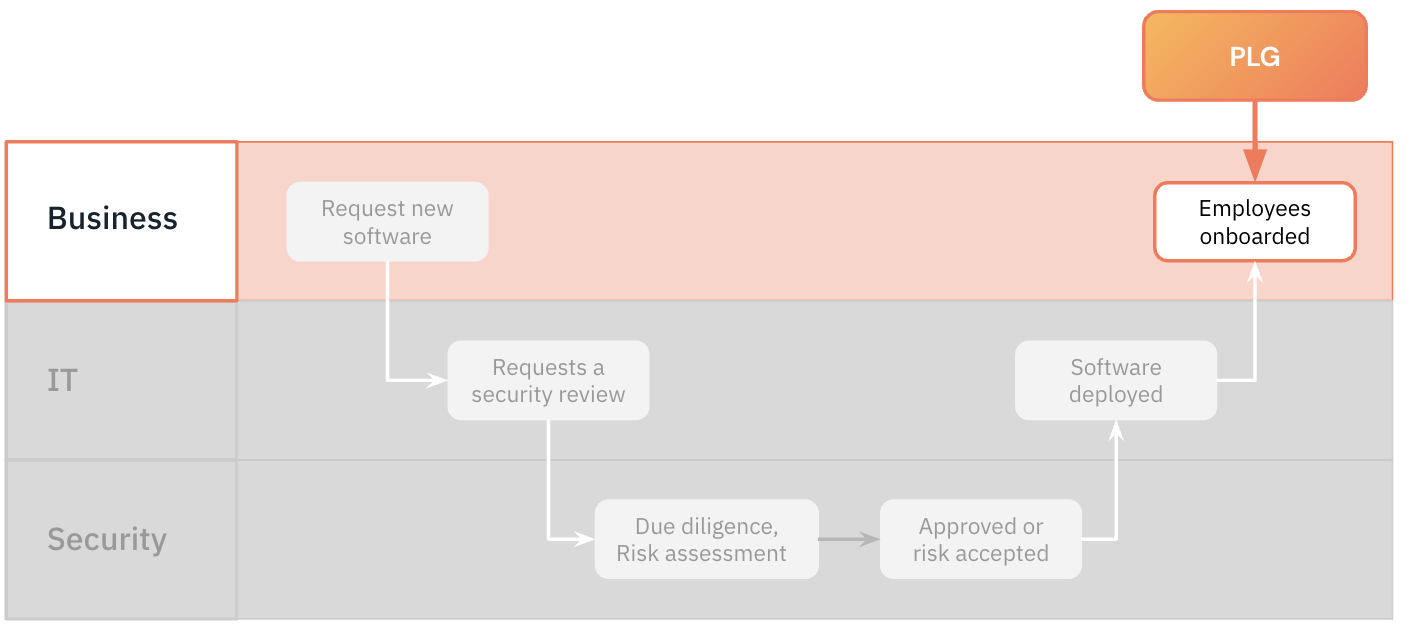
Because of this shift to adoption or free trials as the first step of a “software onboarding process,” Security and IT are left with huge visibility gaps, with shadow SaaS and shadow IT growing exponentially with each employee sign up. Those shadow apps are what we’re talking about when we discuss SaaS sprawl and the risks these unmonitored accounts introduce.
The impact on SaaS security
This Saas provider shift toward pushing employees to sign up for SaaS apps without your oversight has already been happening and it’ll continue to grow in the years to come. That’s because PLG works! It’s helping SaaS vendors grow their businesses exponentially and more and more SaaS providers are going to start following suit.
How big of a problem is this, really?
Back in 2015, Forrester reported that 75% of B2B buyers prefer a no-sales-rep buying process. Product-led growth (PLG) is now the norm for SaaS companies, with around 60% of SaaS companies using this model now.
Here are just a few examples of common business SaaS applications sold via the PLG model, which you’ll definitely recognize. One thing you’ll quickly notice is that most of these apps are built for sales, marketing, and customer support:

SaaS sprawl: A massive increase in the number of SaaS applications businesses use
Adding to the shadow SaaS and SaaS sprawl storm, the sheer number of apps in use has increased dramatically over the years, and will continue to do so. There are a couple reasons for this:
The big old monolithic on-prem software is being replaced not by a single SaaS app, but an ecosystem of specialized apps.
Since apps are virtually zero-maintenance these days, the operating cost of running multiple apps is almost the same as running one giant on-prem or SaaS platform. This further multiplies the number of apps and vendors used in your business.
Security SaaS applications don’t use PLG
IT & security folks are usually ahead of the curve when it comes to technology shifts, but in this case many might have missed the scale or speed of the change.
That’s because IT and security tools are among the least product-led of any sector. Most of our industry’s tools require heavy integrations, complicated setup, agent deployments, and so on.
Note the difference between these common SaaS platforms for security and the ones for the rest of the company above:

Notice how all those “Sign up now” buttons have morphed into “Get a demo” buttons? This is the “old-school” way of procuring software. You work with sales and get a live demo with the sales rep, rather than signing up and trying it for yourself. Then you do still have to do your due diligence and work directly with the vendor to vet whether they’ll responsibly protect your corporate and/or customer data, that they’re SOC2 compliant, and so on.
Unfortunately, few security companies are making products as easy to set up and use as new tools for marketing, sales, finance, development, engineering design, legal, HR, and basically every other sector.
This leads to a misconception that self-adopted apps are rare and don’t contain sensitive data.
Free trials interact with real, live corporate data
It’s not just the paid, fully-adopted apps that introduce third-party, supply-chain and SaaS application security risks to your organization. Even those free trials before an app is officially “adopted” can pose a significant security risk.
For PLG to work, users need to experience meaningful value during that initial experience. To do that, users/your employees almost always need to connect the app to your live environment where it interacts with real data.
Security and IT only see a few of the apps employees are testing and signing up for
To make matters worse, only a small subset of those apps ever get submitted to finance or any official app-onboarding process. Typically, this happens when an employee outgrows the free or trial tier and needs to upgrade to a paid account.
The freemium and trial versions of apps are unlikely to ever be presented to IT and security.
Most agree that only about 2-5% of folks on freemium/free tiers become paying customers. With conversions from free to paid happening only at a very very low rate, it’s very likely that a lot of your employees are using a lot of free tier apps for at least some significant timeframe.
As mentioned earlier, real live data is often still input into those free apps. So, if you’re relying on finance records to tell you which apps employees are using, you’re going to miss all those free apps, which may never reach finance. And those free apps present just as much risk as the paid apps, more if you consider that you have no visibility into the majority of them.
Losing direct visibility into SaaS apps means Security is getting in too late
Though security teams have lost direct visibility, they’ve not lost complete visibility. Many are finding out about at least a fraction of these apps, though things like:
Pulling expense reports once employees need to move from a free to paid tier of an app
Scanning employee email inboxes for key phrases like, “Thanks for signing up for [app]”
And, unfortunately, when something has already gone wrong and they’re asked to respond to an incident on a SaaS platform
In both cases, security is getting visibility too late to be of much value. As I mentioned earlier, once a team has been using an app (even on a free tier) for a year, it’s a huge challenge for Security to convince them to move to a more secure app or to consolidate apps when they find multiple teams using very similar apps.
This intervention needs to happen very early - long before finance is involved - in order to make a positive impact.
Incident Response is necessary, of course, when a SaaS account is breached, but cannot recover the lost data after a successful attack.
All of this obviously poses a problem from an IT and security standpoint. Don’t sound the alarms yet, though, there’s a way to regain some control over your corporate data without having to play bad cop with your entire company.
First steps to reclaiming control
This is a very high-level take on where to start when it comes to SaaS sprawl and security and building out a strong SaaS and cloud security program. But, it’s a start!
1. Shift your perspective
To regain visibility and control, you need to work with employees, rather than focusing on blocking them from their favorite tools.
You can rein this in, but you must shift from the old way of thinking - you can no longer be the “Department of No” and have to shift to becoming the “Department of Yes, Unless….”
2. Get in early
Do yourself a favor and buy yourself time to do due diligence on the multiple SaaS applications employees sign up for on their own.
Getting involved before an employee or team are fully reliant on an app is the best way to make a positive impact on your SaaS security posture.
To do this, you need…
3. Get real-time visibility into the SaaS and cloud apps your employees are signing up for
This can be a noisy mess, but it doesn’t have to be. Look for solutions with options that work with your existing workflow. Tools that send a ChatOps message to security whenever an employee signs up for a new app is a great start.
To cut through the noise, rely on a SaaS security solution that also provides security-relevant information that tells you when you should dig into an app further or when an app only poses minimal risk and can be ignored.
4. Find and fix account security issues at the same time
We suggest you focus on account security issues since this is where the attacks are happening - at the account level.
Getting SaaS visibility is crucial, but it’s not useful if the data leads to false positives. Tracking down cloud apps that aren’t actually in use is a massive waste of your time.
To get the most accurate visibility into shadow SaaS, consider a browser extension. Why, yes, we are biased! But we built our product on top of a combo of API data and browser data because that’s where employees are accessing and signing up for their SaaS and cloud apps.
We dig into this SaaS discovery data source topic in much more detail here, so that’s worth a read when you’re ready to start prioritizing SaaS security and evaluating solutions.
5. Work with employees to reduce the burden on your security team
No, you don’t want employees making security decisions, but you will need to find a way to help them secure the SaaS accounts they have at a user-level.
To keep up with the scale of SaaS adoption and SaaS sprawl in your attack surface, which will continue to grow weekly, you’ll need to automate the information-gathering part of the process.
When possible, equip employees to self-remediate issues and complete tasks (like signing up for MFA in the app) that your team would otherwise have to do.


