Third-Party Risk Management (TPRM) is the process of identifying, assessing, and mitigating potential risks associated with third-party relationships, such as suppliers, vendors, service providers, or subcontractors. These external entities play integral roles in a company's operations, making it essential to manage the risks they may introduce.
Third-Party Risk Management (TPRM) is the process of identifying, assessing, and mitigating potential risks associated with third-party relationships, such as suppliers, vendors, service providers, or subcontractors. These external entities play integral roles in a company's operations, making it essential to manage the risks they may introduce.
Introduction
Companies often rely on third-party relationships to improve their operational efficiency and expand their capabilities. While these partnerships can bring numerous benefits, they also introduce a critical element of risk. Organizations often employ a strategic approach known as "Third-Party Risk Management"(TPRM) to try to manage third-party risk. In this article, we'll delve into the concept of third-party risk management at a high level, highlighting its importance and key components.
We’ll also explore alternative approaches that can help manage third-party risk, which may not yet be on your radar.
What is Third-Party Risk Management?
Third-Party Risk Management (TPRM) is the process of identifying, assessing, and mitigating potential risks associated with third-party relationships, such as suppliers, vendors, service providers, or subcontractors. These external entities play integral roles in a company's operations, making it essential to manage the risks they may introduce.
Why is TPRM Important?
Protecting Reputation: A third-party's failure to protect your data and meet agreed-upon standards can tarnish your company image and brand, potentially leading to a loss of trust among customers, stakeholders, and the public.
Compliance: Regulatory bodies worldwide have heightened their scrutiny of third-party relationships. If both parties don’t comply with these regulations, they may have to pay hefty fines and face legal consequences. TPRM is meant to ensure adherence to these legal requirements.
Data Security: Third-party partners, applications, and services often have access to sensitive data, so it’s crucial that they follow standard security measures and adhere to data compliance regulations.
In the case of third-party applications, even if they don’t have direct access to company data, they may have access to it depending on what permissions were granted to the app upon sign up.
You may not also realize that even if an application doesn’t contain data you consider sensitive or high-risk, the app itself can be used by an attacker to gain access to that sensitive data stored elsewhere in your systems.
Operational Resilience: If a critical third-party vendor experiences disruptions, your whole business can be disrupted. TPRM helps mitigate this risk by identifying potential vulnerabilities and developing contingency plans.
Key Components of Third-Party Risk Management
Identification: The first step in TPRM is identifying all third-party relationships within the organization. This includes both existing and potential partnerships.
Risk Assessment: Each third-party is assessed for various risks, including financial, operational, compliance, and reputational risks. This process helps prioritize risk mitigation efforts.
Due Diligence: Due diligence involves conducting background checks, audits, and reviews to gather information about a third-party's history, financial stability, and adherence to industry standards.
Contractual Agreements: Contracts with third parties should clearly define roles, responsibilities, and expectations, including risk-sharing agreements and penalties for non-compliance.
Monitoring and Reporting: Continuous monitoring of third-party activities is essential. Any deviations from agreed-upon standards or indicators of potential risks should be reported promptly.
Risk Mitigation Strategies: Based on risk assessments, organizations should develop mitigation strategies that may include risk transfer, contingency plans, or risk-sharing mechanisms.
Exit Strategy: You need to plan for the termination of a third-party relationship, which should include data retrieval, transitioning responsibilities, and ensuring minimal disruption to operations.
You can see why these TPRM strategies are so important! Since they’re so critical from an IT and Security perspective, a good TPRM strategy will also benefit from treating each third-party commodity separately.
Take, for example, a third-party technology partner. You may have a TPRM strategy specifically for this group, which focuses on all those elements listed above. But one specific third-party “group” to consider focusing on as party of your TPRM plan is SaaS and identity security.
Ensure your TPRM strategy can keep up with the explosion of third-party cloud services
Now that most companies are reliant on third-party cloud and SaaS applications to operate efficiently, TPRM strategies must include solutions that focus on reducing the risk of those third-party apps and identities. So, in addition to the governance risk and compliance (GRC) tools you’re using as part of your TPRM strategy, you should strongly consider how this fits into your overall cloud security strategy. To manage third-party cloud services, you’ll likely first encounter solutions lumped into a few categories, including cloud access security brokers (CASBs), SaaS security posture management (SSPMs), and cloud security posture management (CSPMs).
In this section, we’ll be discussing third-party risk specifically when it comes to SaaS and the integrations that are added to core SaaS platforms. Note that some call these SaaS integrations “fourth-party risk,” but we think the risk can be managed similarly across both types of SaaS apps, so we’re going to talk about both.
What is SaaS third-party risk?
SaaS third-party risk refers to the potential dangers and vulnerabilities associated with using third-party SaaS providers for software and services in terms of security, compliance, and operational continuity.
Why does it deserve special attention in your TPRM program?
Due to the scale and expansion of how many SaaS apps are used within a business. SaaS has exploded, with new apps hitting the market every day, and employees continue to self-adopt SaaS apps that have the features and functionality they need to do their jobs and make things easier. The trouble is that in order to work, most SaaS apps require access to other business apps, company data, or employee/user data to work.
With employees self-adopting apps for work all the time, IT and Security are left trying to manage the risk without even having visibility into what apps and identities are being created.
So, the first step is getting that visibility so you know which third-parties to focus on, what data they have access to, and if they’re doing anything that might indicate that they’re malicious or simply too high risk for the company.
Helpful resource
We’ve written a guide about how to choose the right SaaS security and identity security solution for your company and your specific needs that should be a good introduction to solving this visibility and SaaS third-party risk challenge.
Push could be the solution you need to get started and it’s free to use and sign up. In these next sections, we’ll cover how we can help.
Push provides visibility into all third-party cloud services employees are using and creating
Push uses data from our browser extension to find SaaS apps that employees sign into with usernames and passwords and SSO (OIDC). This gives you complete visibility of your SaaS environment, including shadow SaaS apps and cloud accounts that aren’t managed by IT.
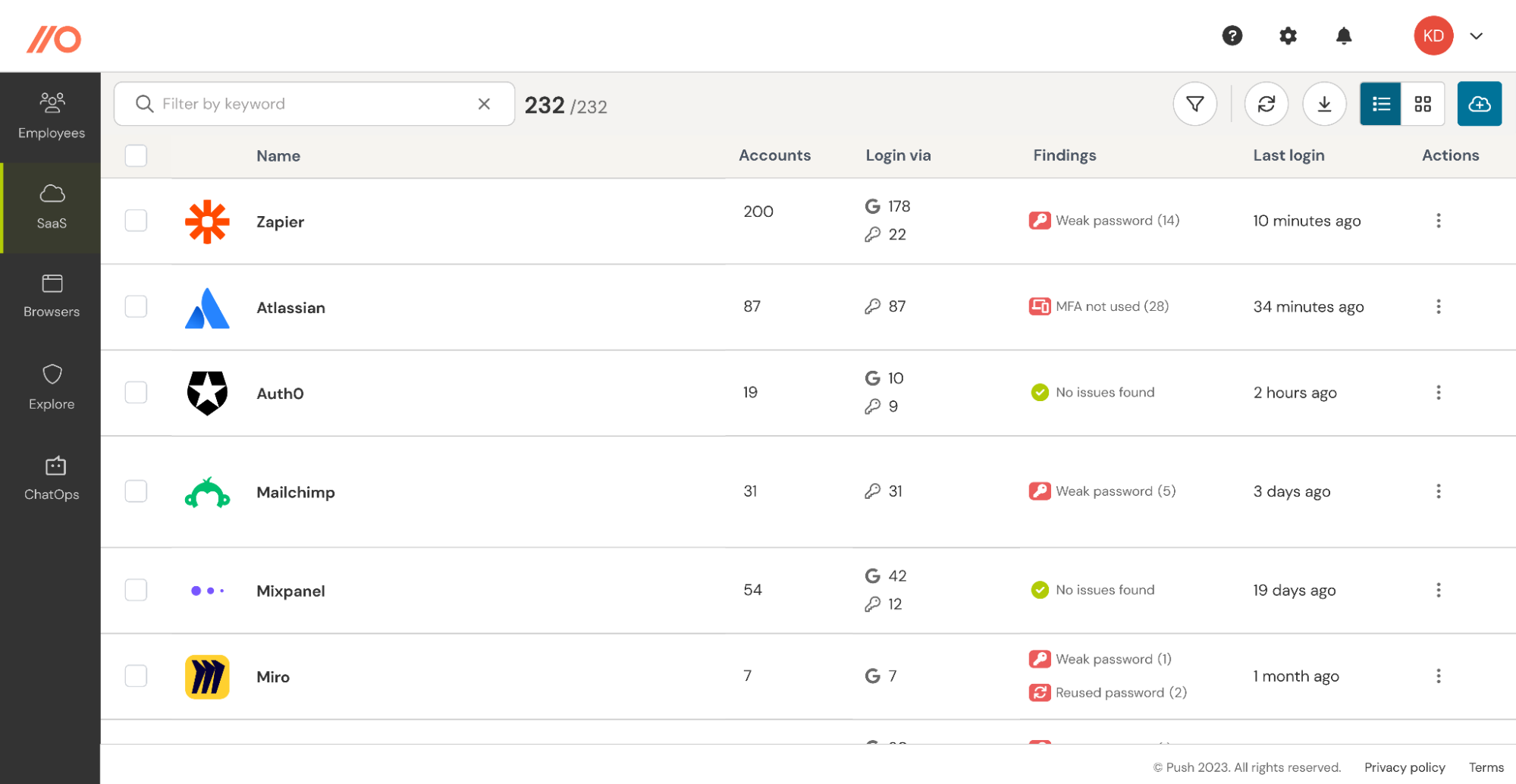
Detect the new apps, integrations and identities in real time
Push detects employees signing up to new apps, or integrating third-party apps to your core work platforms in real-time. That allows you to step in at the earliest opportunity to check out the app and guide the employee through the appropriate app onboarding steps.
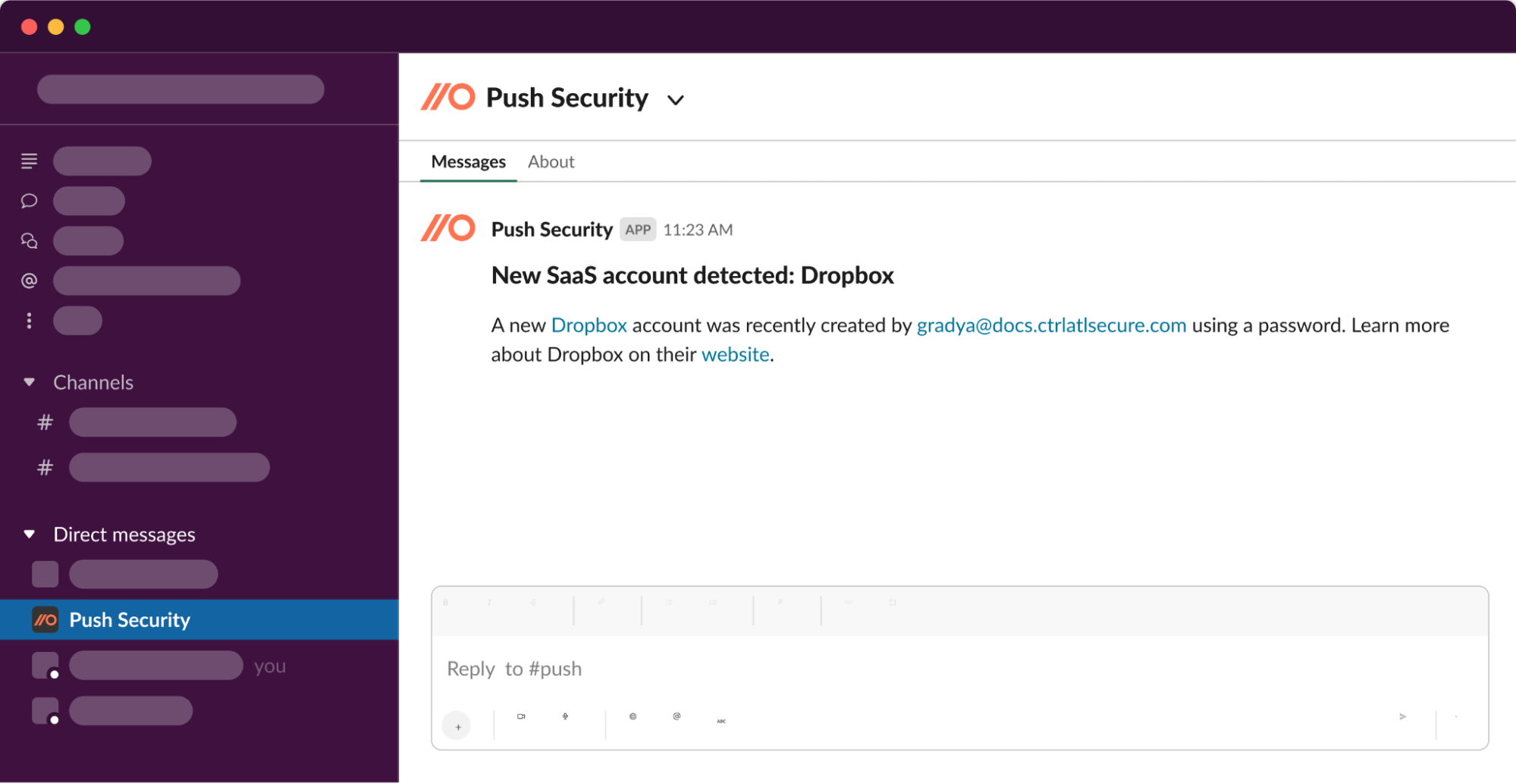
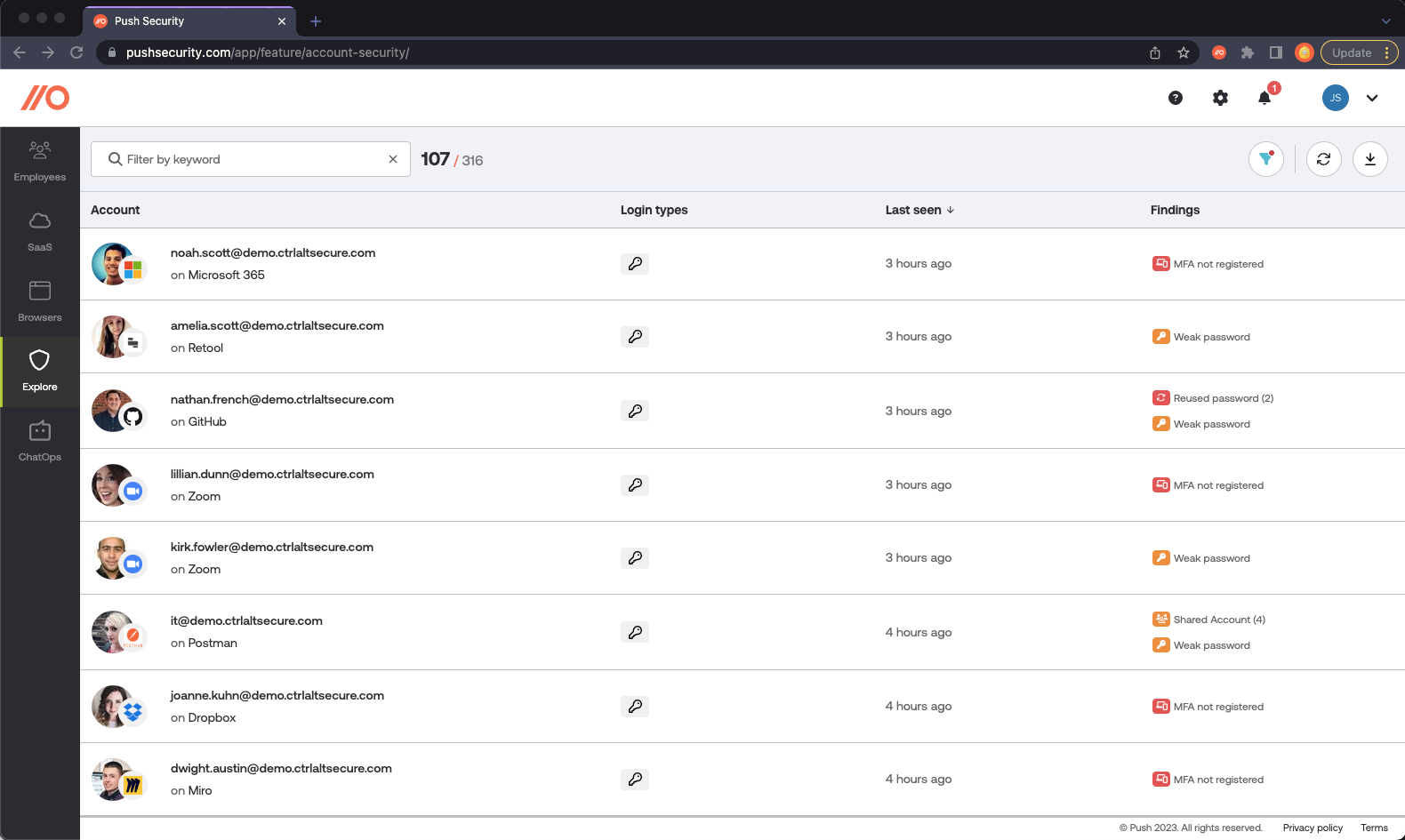
Identify account security risks and discover shadow SaaS at the same time
Supply chain risk is important, but we’d argue the risk of identity-based attacks are greater for most organizations. 49% of the incidents in the 2023 Verizon DBIR involved credentials, and Crowdstrike have reported that 80% of the attacks they detected used identity-based attack techniques. Push can identify account security issues that make it possible for attackers to compromise your employees accounts using credential stuffing, brute forcing and consent phishing attacks. These include:
Compromised passwords
Guessable passwords (and not using a password manager for storing complex passwords)
Account-sharing between multiple employees
Reusing passwords across multiple accounts
Missing MFA
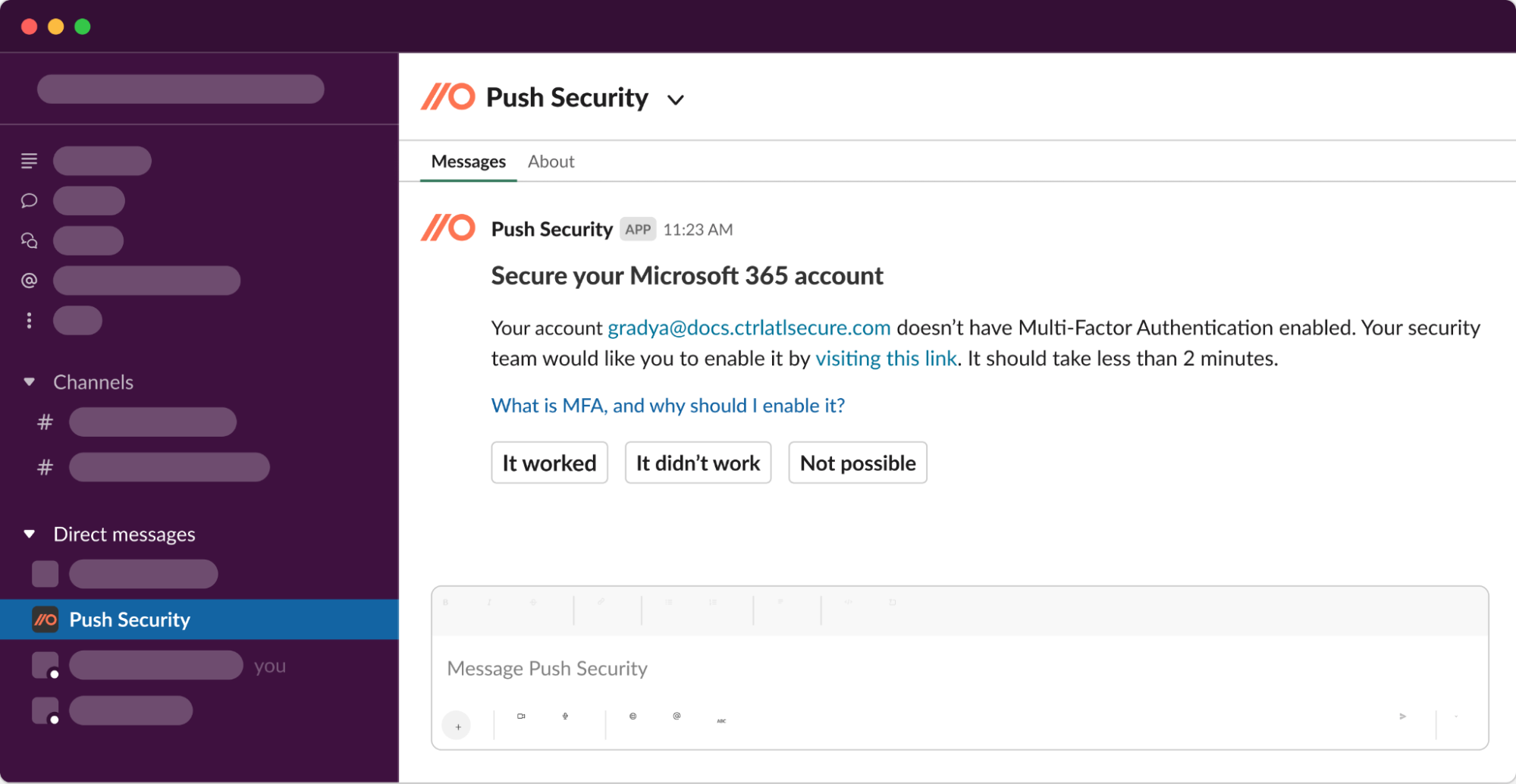
We identify these issues at the same time we discover shadow SaaS apps, so you can tackle identity-based attack risks at the same time as supply chain risk to reduce your overall risk exposure faster.
We engage employees directly via Slack or MS Teams, explain the account security issue we’ve identified in a way they’ll understand, and guide them on how to fix it.
Regain control of all the third-party cloud services employees sign up for on their own
By using Push, you gain complete visibility of all SaaS apps in your environment, including those adopted by employees without the oversight of IT and Security.
We’ll automatically find the security issues that put your data at risk and guide employees to fix them. This allows you to allow app self-adoption and adopt a default allow approach that enables your business while scaling security so you don’t lose control of SaaS security risks.
Push’s free tier gives you 10 licenses for free forever and all the features are baked into that free version. This is a great way to see if it’ll work for you, so jump in and start playing with it!

