Employees are self-adopting SaaS apps and creating new cloud identities without IT approval. Consider a solution with built-in features to find and secure identities your employees have created and guide them to harden their accounts against attacks.
Employees are self-adopting SaaS apps and creating new cloud identities without IT approval. Consider a solution with built-in features to find and secure identities your employees have created and guide them to harden their accounts against attacks.
Introduction
SaaS vendors have changed how software is adopted into a business. Now, the majority of SaaS vendors use a product-led growth model - which simply means they want users (your employees) to self-adopt their apps, start using them (with real data), and become a useful tool for the employee.
Vendors want to bypass the security and IT software-onboarding processes we’d all gotten used to in the past. They know if they prove their tool is valuable with the user from the start, it’s much easier and quicker for them to gain traction and customers than it was waiting for security and IT teams to audit (and potentially refuse) their software.
The result of this...
Employees are self-adopting SaaS apps and creating new cloud identities on their own, without IT approval
This self-adoption has turned the product-adoption process on its head - leaving security and IT teams blind to which apps sensitive company data is flowing into.
Now that IT and security have to not only find these accounts, identities and apps, but keep sensitive corporate data secure across all cloud services, where do you start?
You could consider a solution like Push, which has built-in features to find and secure identities your employees have created and guide them to harden their accounts against attacks.
Push gives you complete visibility, helps you identify risks, and works with employees to secure accounts
It probably won’t come as a surprise to find out that we’ve designed Push so security teams can get a handle on employee-adopted SaaS apps without needing to block them.
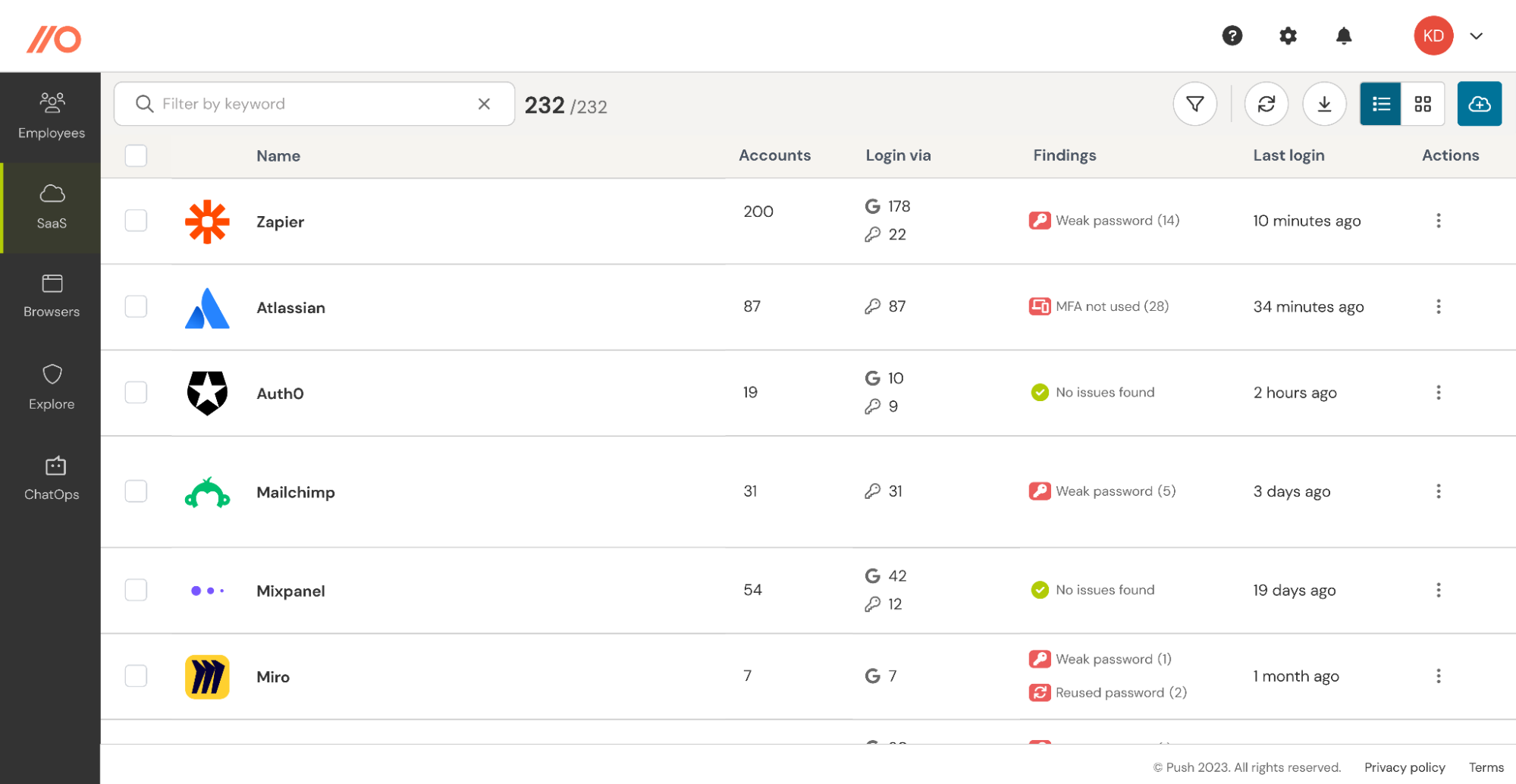
1. Get visibility of shadow SaaS apps and shadow identities
If you’re going to get a handle on employee-adopted SaaS apps, you need to get visibility of them first. Push uses data from our browser extension to find SaaS apps that employees sign into with usernames and passwords and SSO (OIDC). This gives you complete visibility of your SaaS environment, including shadow SaaS apps and cloud accounts that are not managed by IT.
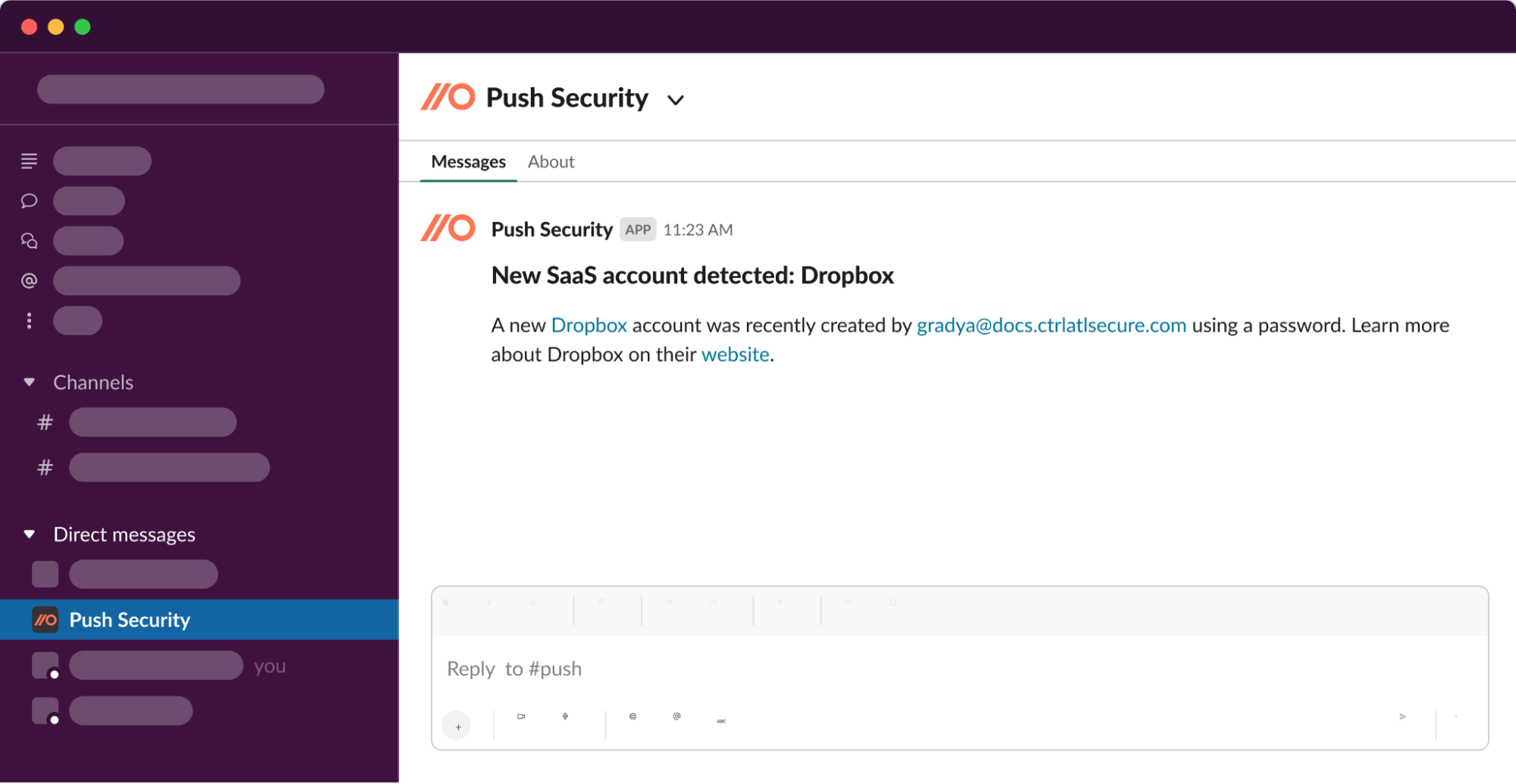
2. Detect the new apps, integrations and identities in real time
Push detects employees signing up to new apps, or integrating third-party apps to your core work platforms in real-time. That allows you to step in at the earliest opportunity to check out the app and guide the employee through the appropriate app onboarding steps.
3. Avoid wasting time on false-positives
You need to trust your data if you want to take action to manage risks. Email and network data all infers SaaS usage from indicators such as emails from vendors and website visits. But as you can imagine, that won’t always point to usage, and so false positives are inevitable. Doing risk assessments or chasing employees about apps employees are not actually using wastes time and burns goodwill.
Push uses a browser extension to accurately identify the SaaS apps employees are using and any security issues that attackers can exploit to compromise your data through common attacks like credential stuffing and brute forcing.
Push is the only identity security solution that can directly observe all SaaS use and detect account vulnerabilities - completely automatically. No need for API support, no need for an admin account. It just works.
4. Identify account security risks and discover shadow SaaS at the same time
Supply chain risk is important, but we’d argue the risk of identity-based attacks are greater for most organizations. 49% of the incidents in the 2023 Verizon DBIR involved credentials, and Crowdstrike have reported that 80% of the attacks they detected used identity-based attack techniques. Push can identify account security issues that make it possible for attackers to compromise your employees accounts using credential stuffing, brute forcing and consent phishing attacks. These include:
Compromised passwords
Guessable passwords (and not using a password manager for storing complex passwords)
Account-sharing between multiple employees
Reusing passwords across multiple accounts
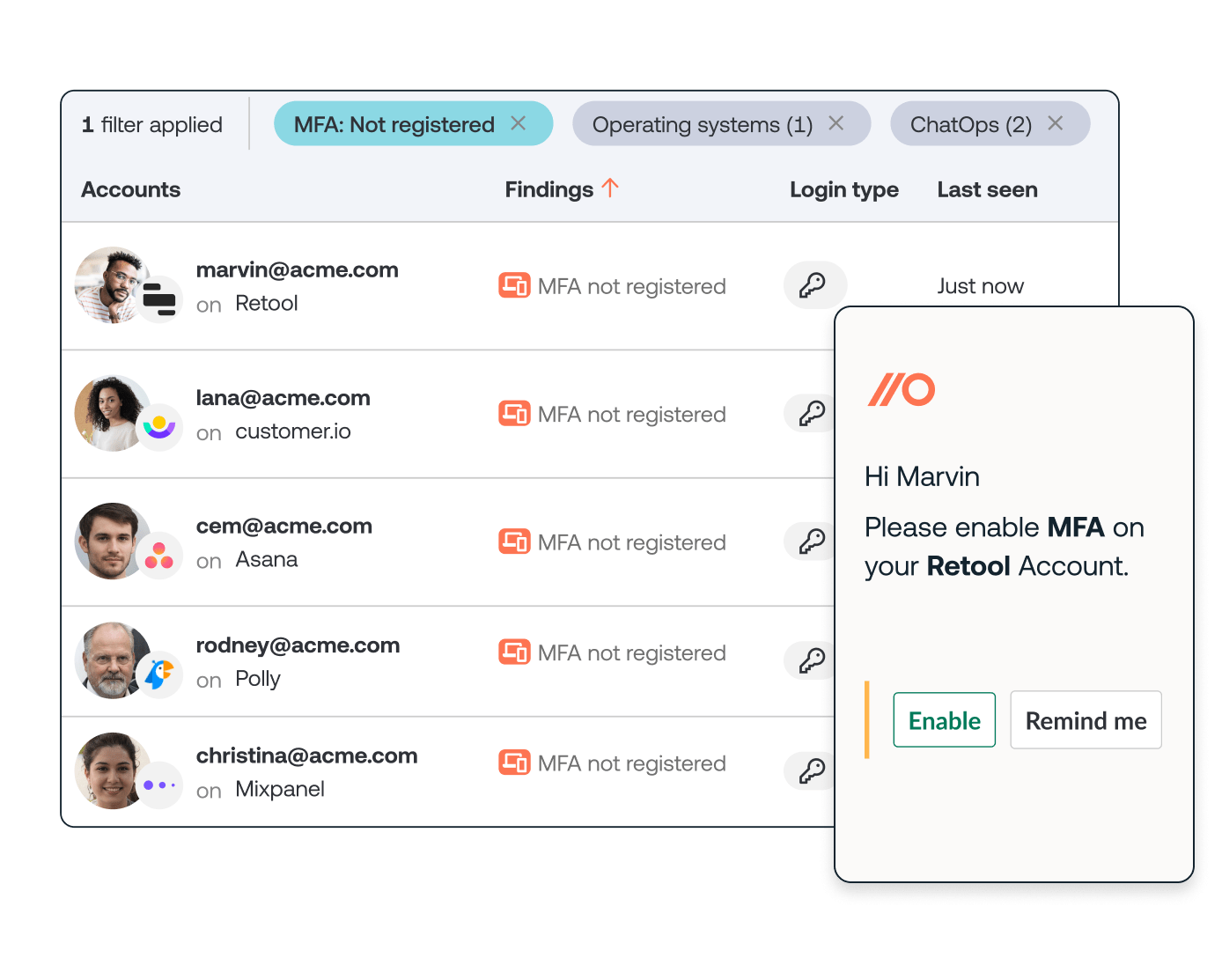
Missing MFA
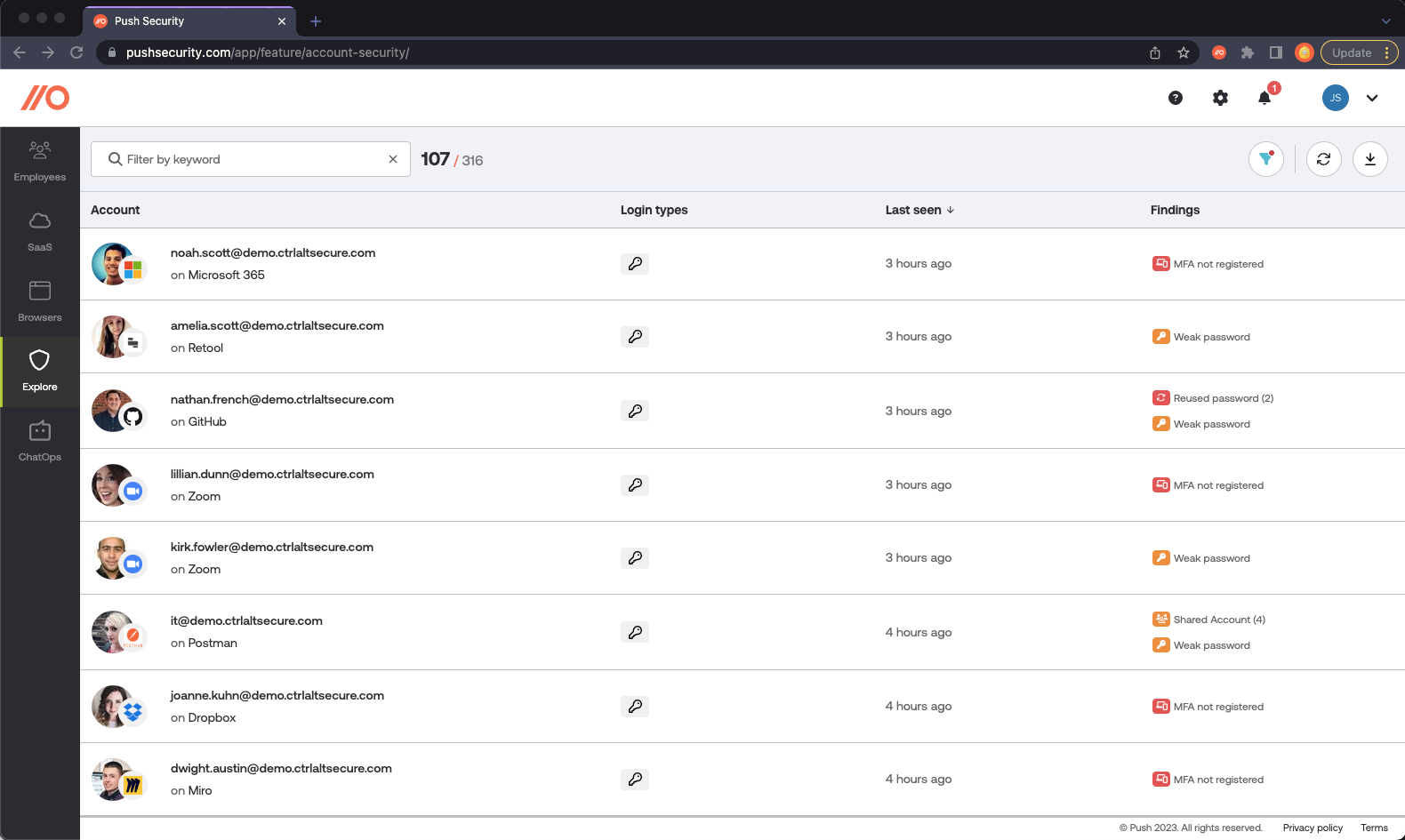
We identify these issues at the same time we discover shadow SaaS apps, so you can tackle identity-based attack risks at the same time as supply chain risk to reduce your overall risk exposure faster.
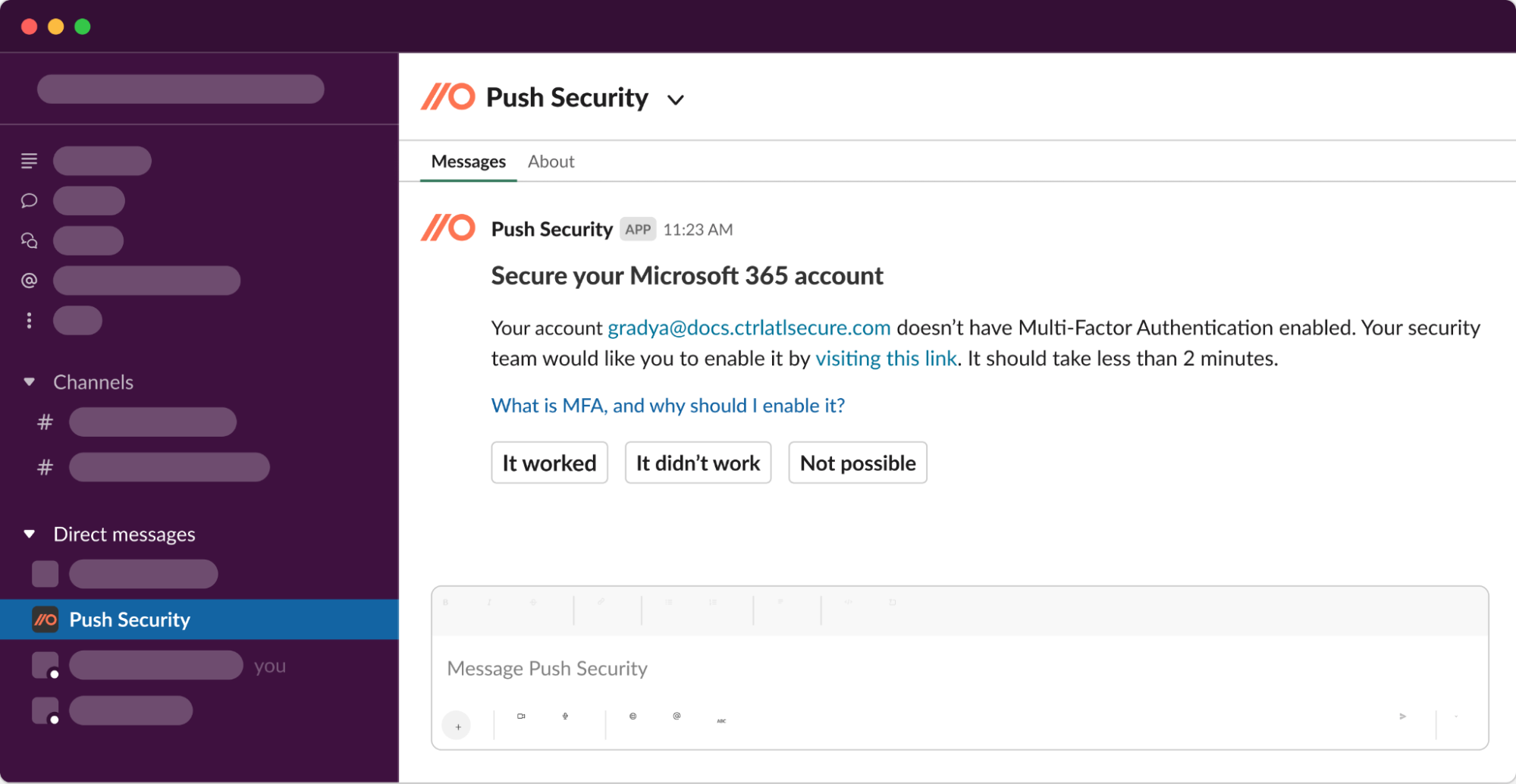
Push can help you reduce these risks by engaging employees directly via Slack or MS Teams, explain the account security issue we’ve identified in a way they’ll understand, and guide them on how to fix it.
5. Use Push to secure accounts that aren’t behind SSO
In an ideal world, you could stick all your SaaS apps and accounts behind your SSO solution. With SAML SSO, there’s just one identity, just one password, and you can centrally deprovision accounts when employees leave the organization. You’re probably already paying for a SAML IdP (Identity Provider) like Google Directory or Azure AD. Many others are using tools like Okta.
Unfortunately, SSO is only available on around 31% of work apps we explored.

So, with SSO unavailable for most apps, you can rely on Push to ensure strong access controls on non-SSO accounts, things like:
using strong, unique passwords, and
utilizing multi factor authentication (MFA).
These authentication controls, when used in conjunction with one another, are very effective in protecting SaaS accounts from identity-based attack techniques. When Push detects that these controls are not in place, we automatically engage users via Slack or Teams and guide them to fix the issues.
Prevent new identity vulnerabilities being created
Once you’ve been able to fix the security issues on all your existing cloud accounts, you want to make sure that new vulnerabilities don’t creep back in.. When Push detects an employee creating a new account in their browser, we’ll guide them to set up strong access controls on their account.
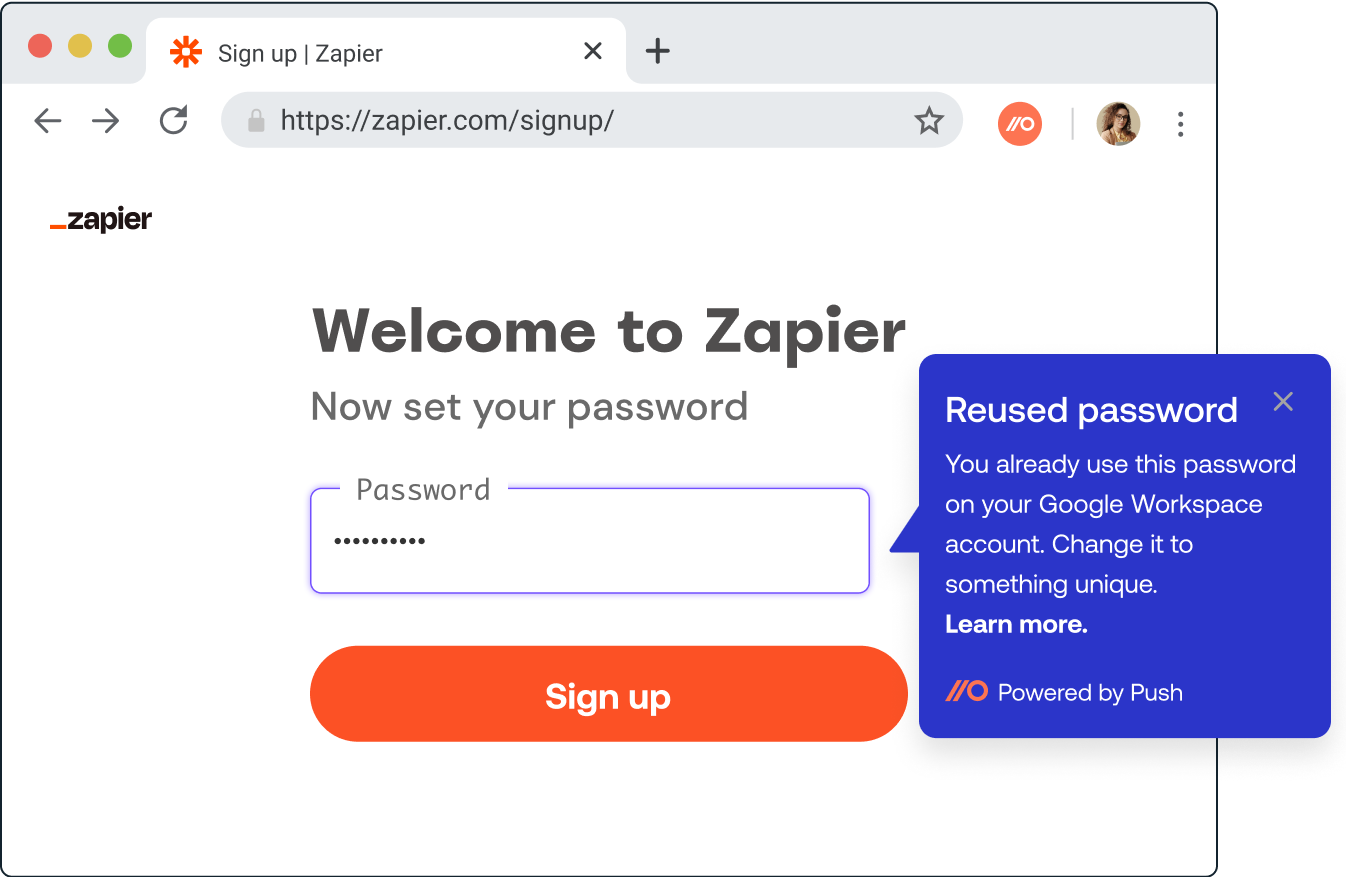
6. Get a handle on employee-adopted apps without being a blocker
By using Push, you gain complete visibility of all SaaS apps in your environment, including those adopted by employees without the oversight of IT and Security. We’ll automatically find the security issues that put your data at risk and guide employees to fix them. This allows you to embrace app self-adoption and adopt a default allow approach that enables your business while scaling security so you don’t lose control of SaaS security risks.
Push’s free tier gives you 10 licenses for free forever and all the features are baked into that free version. This is a great way to see if it’ll work for you, so jump in and start playing with it!


