Identities have quickly become the new perimeter, leading attackers to target identities as the primary way to access sensitive corporate data. A recent report found that 68% of companies say identity-related attacks directly impacted their business in 2023.
Identities have quickly become the new perimeter, leading attackers to target identities as the primary way to access sensitive corporate data. A recent report found that 68% of companies say identity-related attacks directly impacted their business in 2023.
Identity Defined Security Alliance (IDSA) recently released their 2023 report: Trends in Securing Digital Identities, which had some interesting data to consider as you think about securing identities in the cloud for your organization.
Identities have quickly become the new perimeter, leading attackers to target identities as the primary way to access sensitive corporate data. Organizations and security professionals are considering identity security top of mind, as a result. The report found that 68% of companies say identity-related attacks directly impacted their business in 2023.
1. Passwords are (still) the weakest link
It’s no surprise that this survey found that phishing is the most common identity security-related attack, reported by 57% of survey respondents. Poor password hygiene like employees reusing passwords across work and personal accounts was often reported (by 37%) as a weakness that could lead to identity-based attacks..
Further exacerbating this issue, employees often reuse passwords across many the cloud and SaaS applications they’re using, and 31% reported that employees share login credentials with their colleagues for work cloud and SaaS apps.
The risk of these security shortcomings is real and a concern today, not just a future problem. Our recent open-source research on SaaS attacks demonstrated how attackers will take advantage of those weak and/or reused login credentials as an entry point for attack chains, allowing them to move laterally within the organization and across apps to get to the data they’re targeting.
None of these finds are shocking for anyone in security. However, what may be new is where identities start and end. Let’s dig into that.
2. Identity security sprawl makes it a challenge to manage digital identities and data sprawl
Many readers may think of identity as an employee’s SSO identity first, but it’s important to consider identity sprawl - anytime an employee signs up to a cloud application with a password, they’ve created a new account and a new identity on that app.
This happens because they’re using a username and password to sign up, which has created a new identity that only exists on that app. If, on the other hand, they clicked “Signup with Google” or “Signup with Microsoft,” they would have created a new account, but used their Google and Microsoft identity that already exists and is managed by the organization they work for.
3. More SaaS = More identities = More opportunities for attackers
Another finding from the survey is that 52% of respondents said the adoption of more cloud applications is driving an increase in the number of identities. As employees sign up for SaaS and cloud applications on their own, they’re adding more assets and identities to your attack surface. They’re also adding more third-party vendors to your supply chain.
You can see how quickly identity management can become difficult to manage and a really juicy new attack surface for attackers. On average, teams use 40-60 apps for work. If they’re not using a social login (“Signup with Google” or “Signup with Microsoft”), it’s not just the SaaS accounts that are exploding but also the number of identities security and IT have to track, monitor, and secure. Add in sharing credentials across the team and password reuse that was mentioned earlier, and the scope of the problem explodes pretty quickly.
Doesn’t SSO solve this?
SSO is the ideal, gold standard solution for managing your SaaS security risks. The big issue is that very, very few apps, particularly the smaller ones most of the employees in your company will be signing up for, offer SSO integrations.
When we looked at the apps we cover, only 30% of them offered SAML SSO integrations. For the other 70% of apps, SSO isn’t even an option.
Making things worse, of those few apps that did offer SAML SSO as a feature, they offered it as a paid feature that you can only access at a high pricing tier, typically Enterprise or the highest pricing tier. This is known in the industry as the “SSO tax.” So, at the moment, this means SAML SSO isn’t a practical option for most apps. We wrote much more on this here as well.
Many more apps offer social logins (“Login with Google” - aka OIDC SSO), and while this isn’t quite as good as SAML, it’s a far better option than local passwords for each SaaS app. Our advice is you should prefer social logins over usernames and passwords wherever possible. Read more about that here.
4. Organizations know they need to secure identities, but struggle to stay ahead of the sprawl
In the IDSA report, survey respondents were asked to consider how they would improve identity security going forward, after experiencing damage to the business from attack(s).
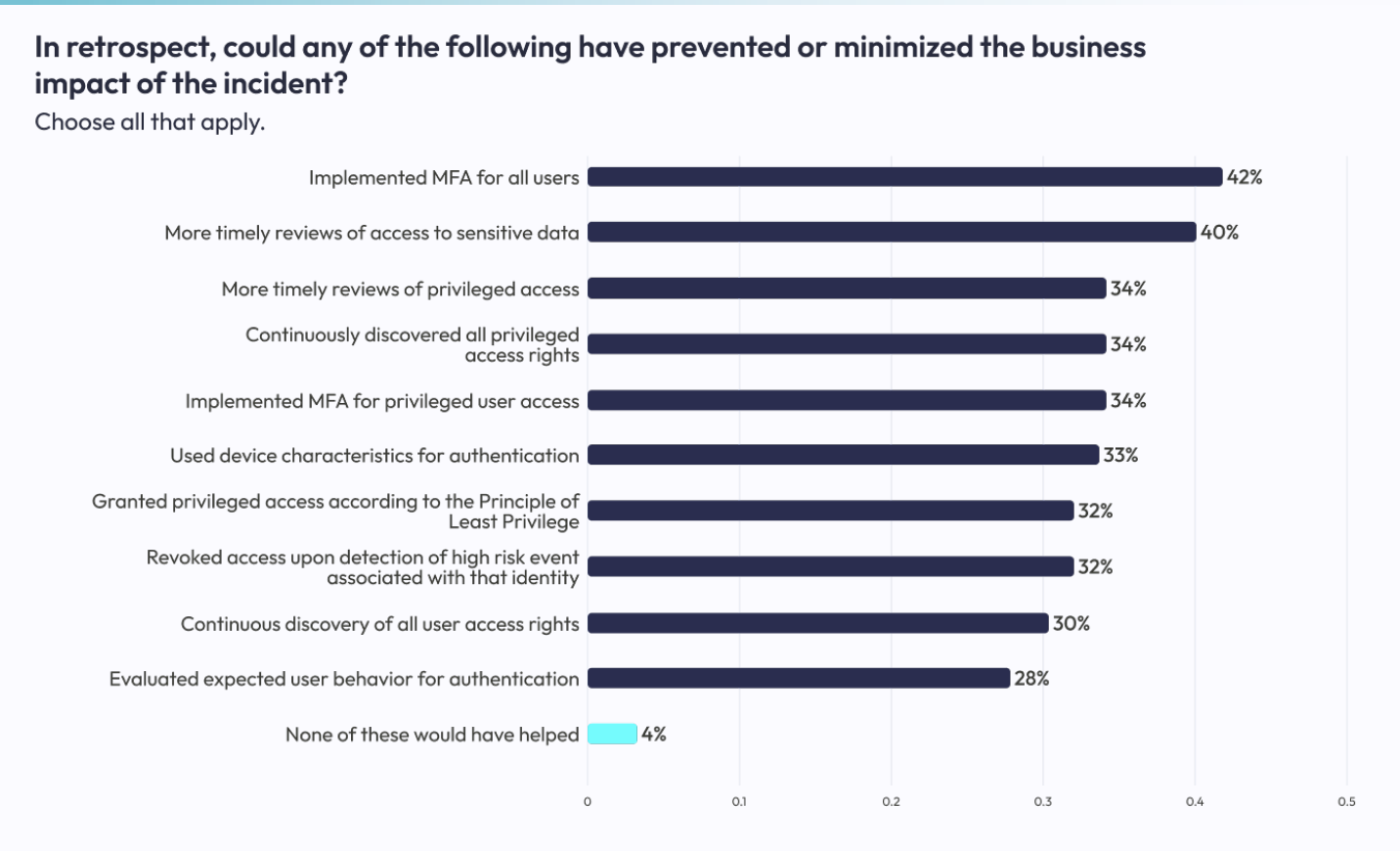
Source: https://www.idsalliance.org/white-paper/2023-trends-in-securing-digital-identities/
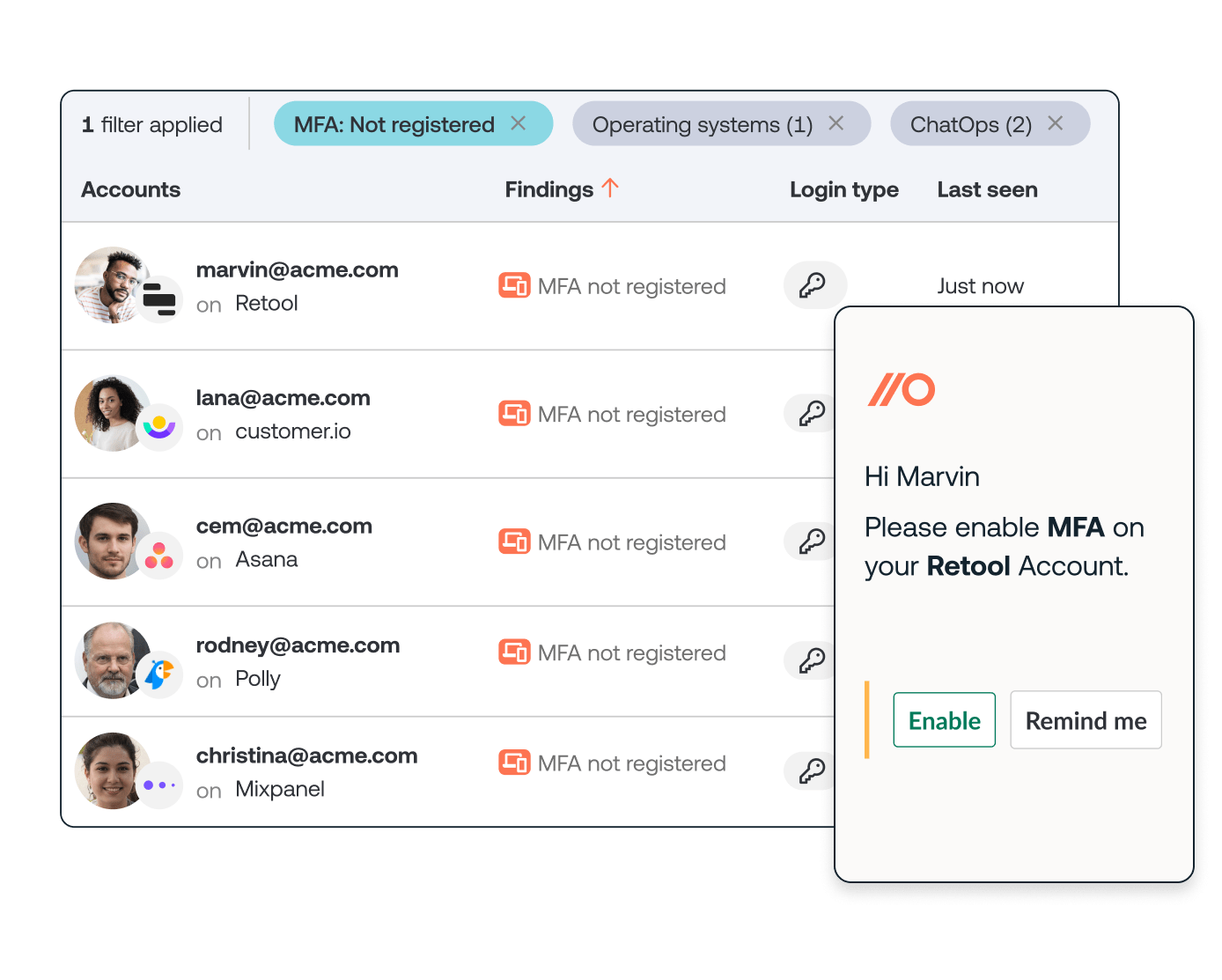
At the top of that list (42%) was basic multi-factor authentication (MFA) implementation for all employees. That sounds like a simple task, but when you’re staring down a list of all of your IT-managed cloud apps and adding all those work apps that employees have signed up for on their own (each of these unmanaged employee-adopted SaaS applications are known as a shadow identity, more on that here), it can feel like an impossible task.
That’s where tools (like Push) can help. We work directly with employees via ChatOps to help them harden their identities by turning on MFA and creating stronger, unique passwords for the apps they’ve signed up for with credentials.
Read more about this feature here.
5. Reviewing who and what can access corporate data is a top concern
The next priority on that list of how to mitigate identity-related attacks was “more timely reviews of access to sensitive data.”
Each SaaS app, cloud app, and OAuth integration needs to interact with business data and systems in some way, either by the employee granting access in initial permissions consent flows during signup or by administrators consenting as part of onboarding centralized cloud platforms for the organization.
Similar to MFA adoption across all the apps, tracking and managing all the accounts, applications, and integrations to your core work platforms can feel overwhelming.
In order to access risk and review access to sensitive data, you need an automated way to:
Find the work apps employees are using because they interact with corporate data and,
Quickly understand what data each app or integration can access
With this information, you can make better decisions about whether to accept the risk these apps and integrations present to their business - balancing security risk and internal resources for auditing, monitoring and hardening these identities, while not becoming a blocker to the overall business.
6. Organizations perceive internal hurdles to secure identities
One of the more telling takeaways from the report is that respondents don’t feel that they’re armed and ready to secure identities. They cited the following concerns:
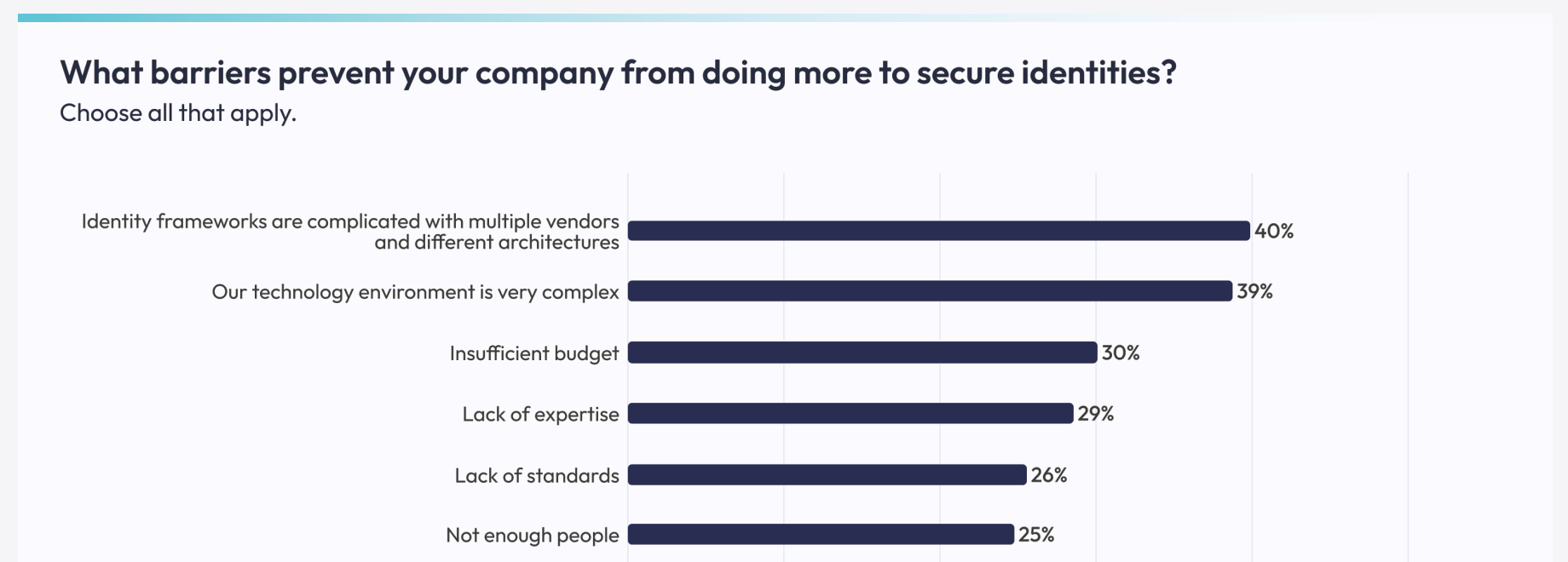
The top two issues identified were issues of complexity, both in the identity frameworks themselves and with the organization’s technology stack.
The other issues are concerns we hear fairly often in this industry: no budget, not enough internal expertise, and not enough manpower and time.
In the next section, we’ll explore how Push can help address each of these barriers to securing identities.
Overcome these barriers with Push
Barrier #1: Identity frameworks are complicated with multiple vendors and different architectures
Push tracks where your identity providers (IdPs) are being used across your cloud environment, including popular managed IdPs like Google, Microsoft and Okta that use SAML and OIDC (aka “social login”) SSO, as well as custom or self-hosted IdPs like Active Directory Federation Services (ADFS).
Barrier #2: Our technology environment is very complex
Push gives you visibility of all your cloud identities, no matter how decentralized or interconnected your cloud environment is.
Barrier #3: Insufficient budget
Push is cost effective for organizations of all sizes. You pay per employee, regardless of how many identities they have or apps they use. Many organizations have purchased Push before getting an IdP like Okta because it is a more cost effective way of securing identities.
Barrier #4: Lack of expertise
Push is surprisingly simple to use. Roll out the browser extension using MDM, Push will give you instant visibility. You just need to decide which automated remediation workflows you want to turn on.
Barrier #5: Not enough people
Push doesn’t just find more issues, it also fixes them. When Push detects a security issue, it automatically engages the identity owner and guides them to self-remediate the issue. This makes Push totally scalable and frees-up your security team.
Learn more about how we can help!
Push helps you see which third parties have access to your data
To manage both identity and data sprawl, lean on a good identity security solution like Push to:
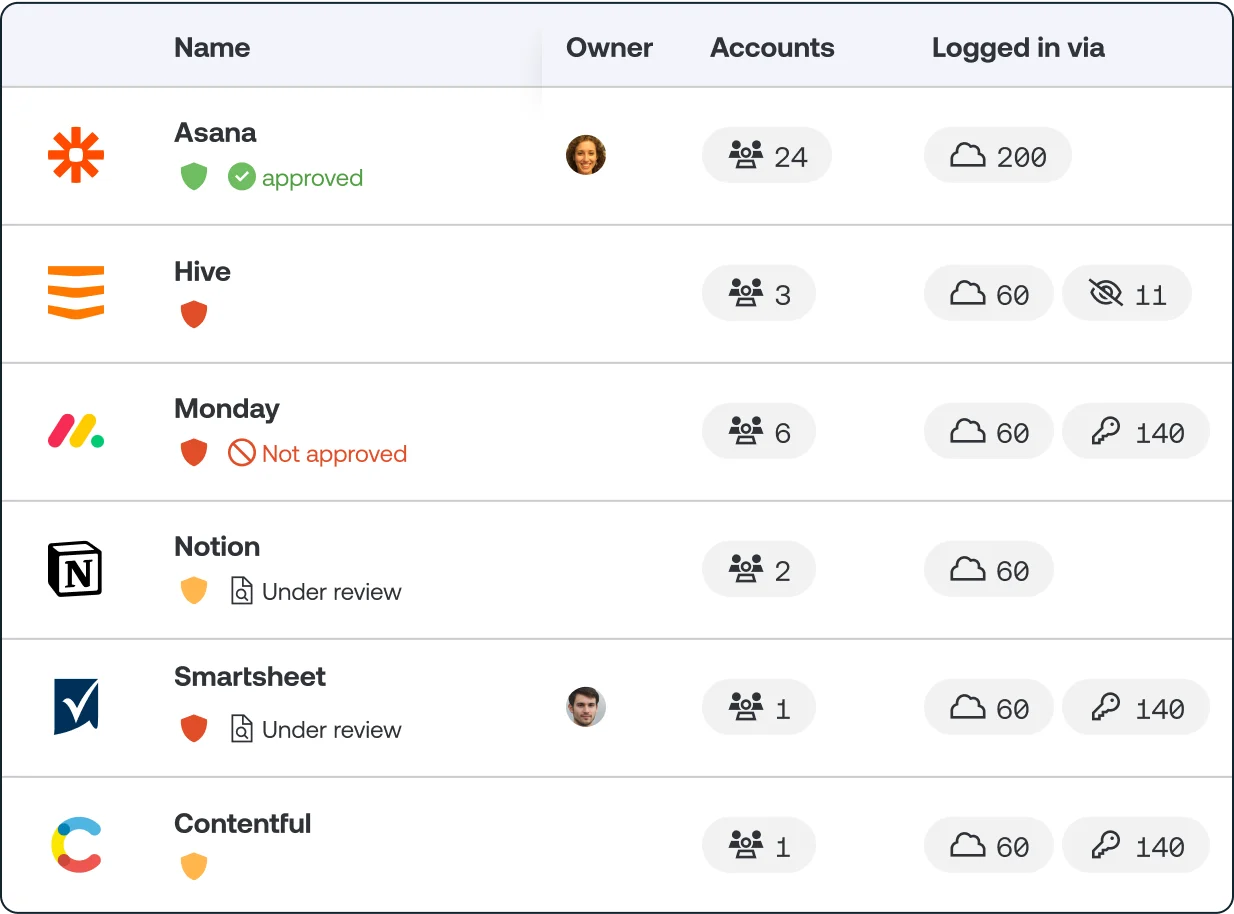
Track which apps have access to your corporate data
Find the apps your employees are using, testing, or trialing and the associated digital identities they’ve created, and then see what data those apps were given access to by the employee:
Detect new apps employees sign up for
By catching these signups early, you can quickly check out the third-party app vendor before employees give those apps even more corporate data than they did just by signing up and testing the app:
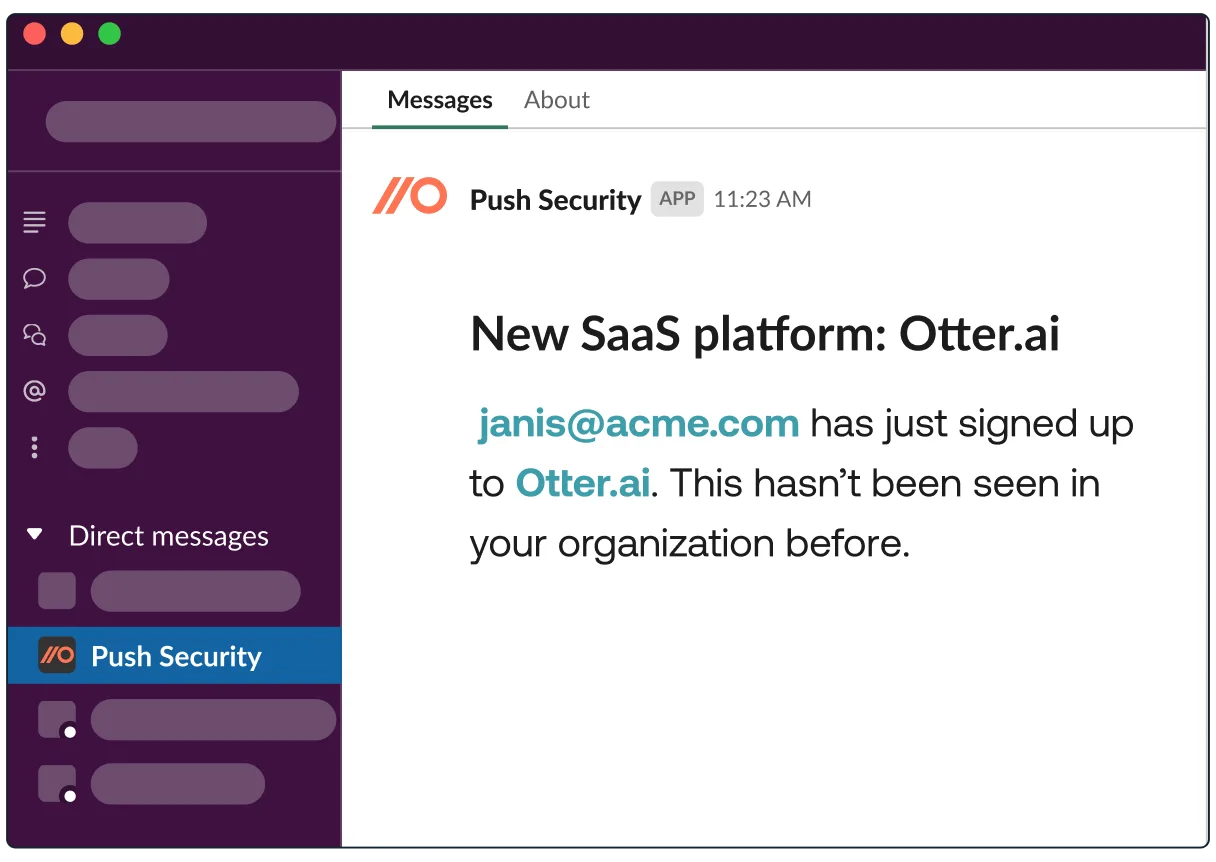
You can then also use Push to work automatically with your employees to harden their accounts. Much more information on there here.
Give Push a try (we have a forever free tier!) to see if it’ll work for you. Better yet, grab a spot in our calendars so we can run through how Push can help with your specific needs and requirements by booking a quick demo.

