Password expirations don’t work. Try these best practices instead.
Password expirations lead to more predictable passwords. Use password managers, MFA, to prevent password theft.
Password expirations lead to more predictable passwords. Use password managers, MFA, to prevent password theft.
Passwords and policies surrounding them are perhaps not the sexiest topic to discuss. Even though there are many security vendors shouting "passwords are dead!" so that they can sell you their latest 0-touch-magic-super-secure authentication solution, the reality is that the world still runs on passwords. Especially in a world where employees can adopt SaaS themselves without help from IT, there will likely be loads of services in your organization where users are using passwords, rather than social logins or SSO. We wrote up some guidance about why you should encourage employees to use social logins, but many will still use username and password to log in.
Recently, Microsoft blogged about their updated password policy guidance. We highly recommend that you read the full article, but we want to zoom into one aspect here around password expirations.
Password expirations are harmful to the quality of the passwords that people choose. There has been some commentary from security industry figures on this, but we think that Chris Wysopal really hits the nail on the head here.
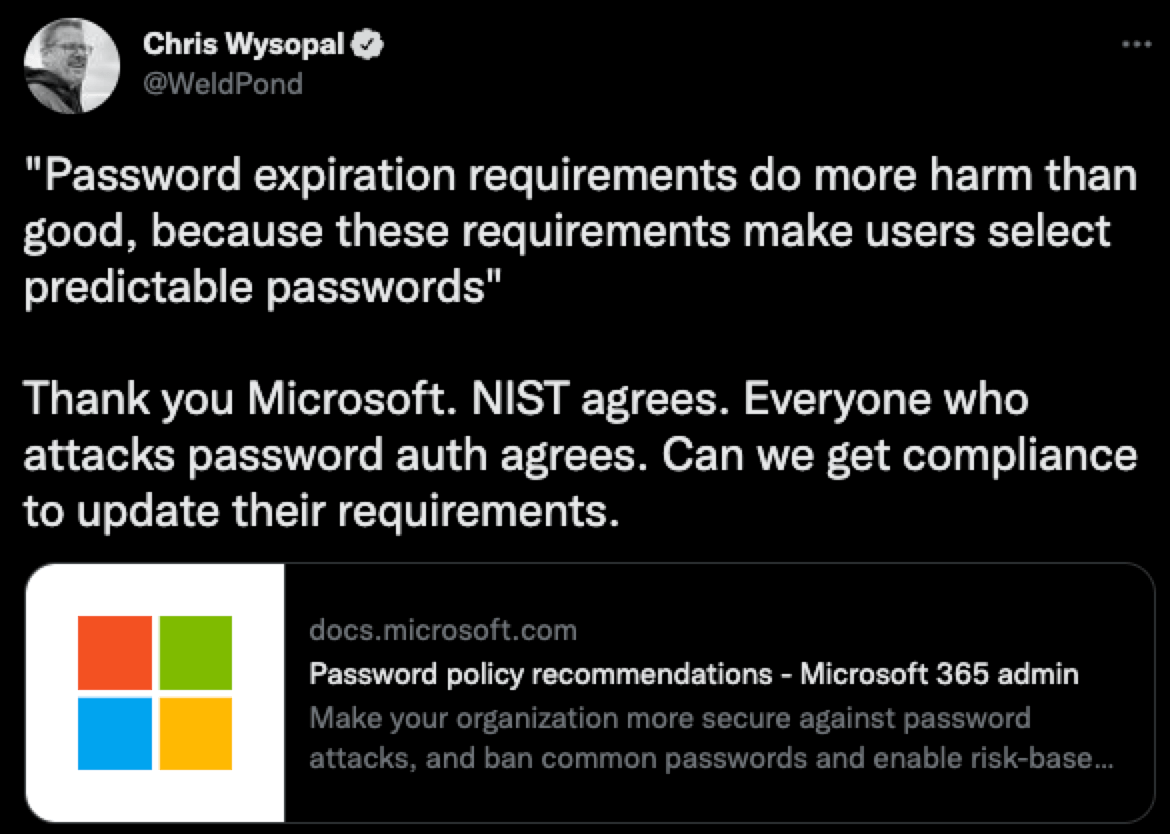
The hacking community has long known that password expirations and forced rotations cause predictable passwords. If you had to dump password hashes for any organizations that have a password expiration in their policy you will find the following passwords in use:
Password1! to Password9!
Summer2022!
Winter2022!
January2022! to December2022!
CompanyName1! To CompanyName9!
Why is this? If you make passwords a pain for people, they will do whatever it takes in order to remember their passwords. Some would call this “bad behavior,” but winning at security requires an understanding of human nature. If you make security hard, expect bad results.
Password policies have been a hotly debated topic over the years, especially because various compliance frameworks bake in some questionable practices like password expirations.
Try these tips for helping employees choose strong passwords
Here at Push, we believe the following about password policies:
Don't enforce arbitrary specials/numbers requirements, only length requirements.
Don't allow certain common words in passwords, like "password" or your company name.
Remove mandatory password rotations - it seems like a good idea but it's not.
For your employees:
Make password managers a part of your culture. Roll them out and make them prominent. Generating random passwords that require no extra brainpower can be easy.
Don't re-use passwords between sites. This becomes very difficult without a password manager
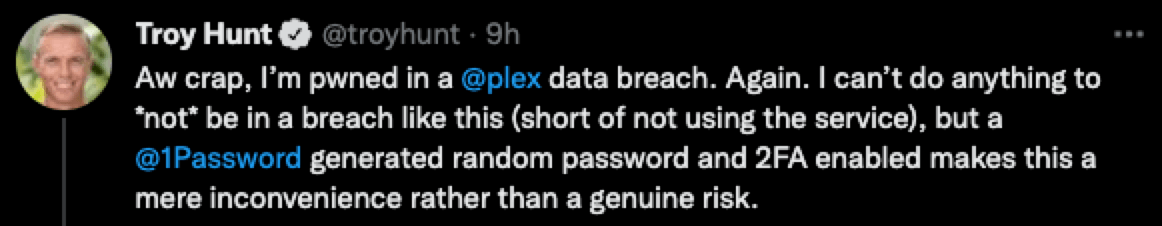
If your account is in a breach, change that password immediately. HaveIBeenPwned is an excellent (free) service that can be used to discover breaches.
Enable MFA on your accounts, it makes password breaches an inconvenience rather than an issue.
Of course, we can help your employees log into SaaS apps and services securely by giving them just-in-time guidance and reaching out via ChatOps (Slack or Teams) to help them fix weak or shared password issues. Learn more about how we can help.


