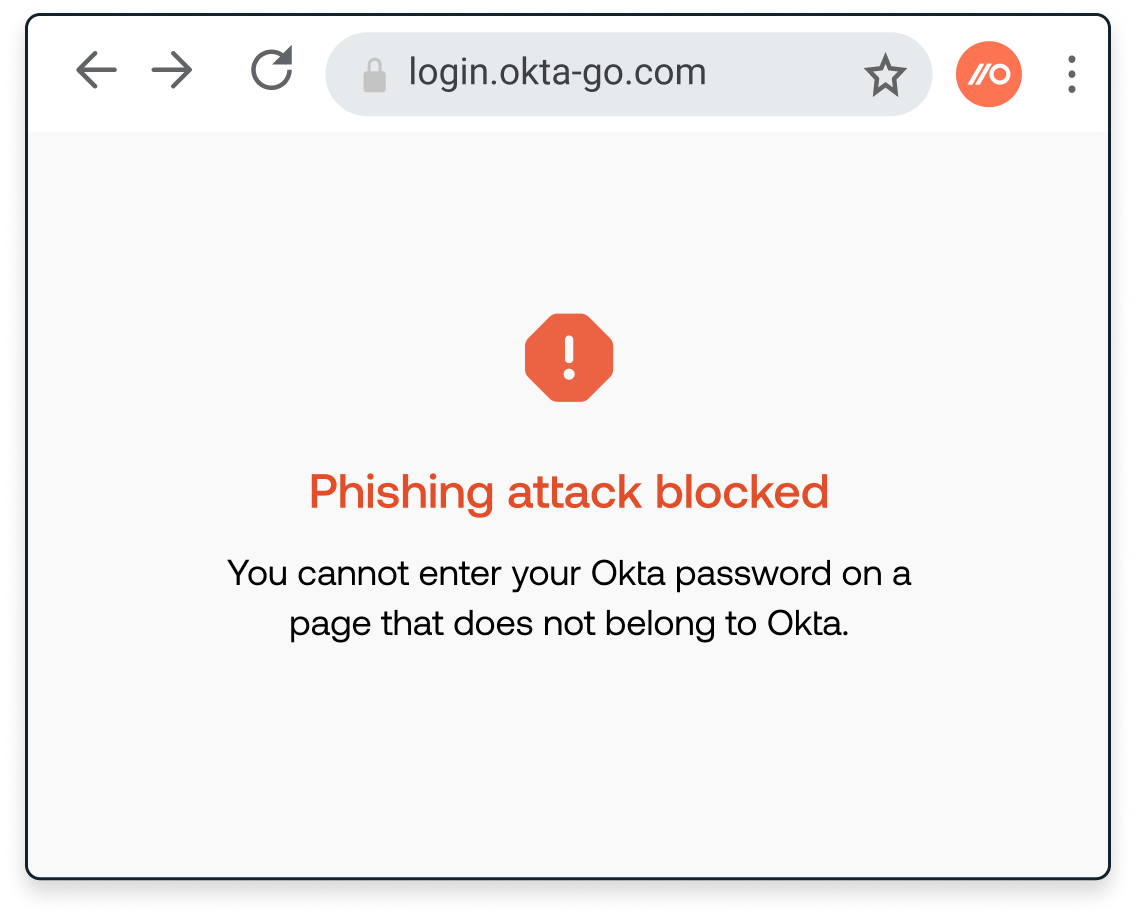
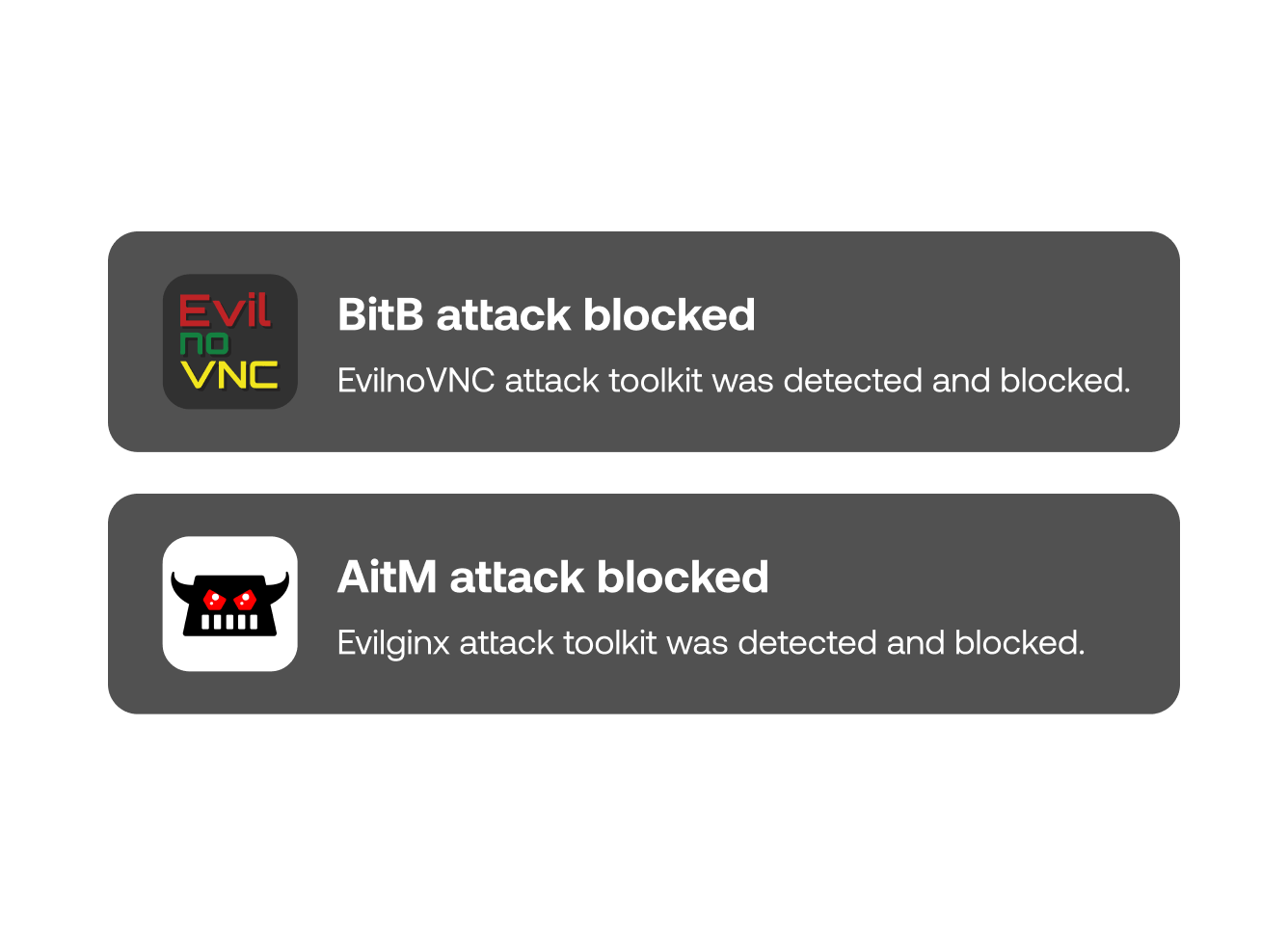
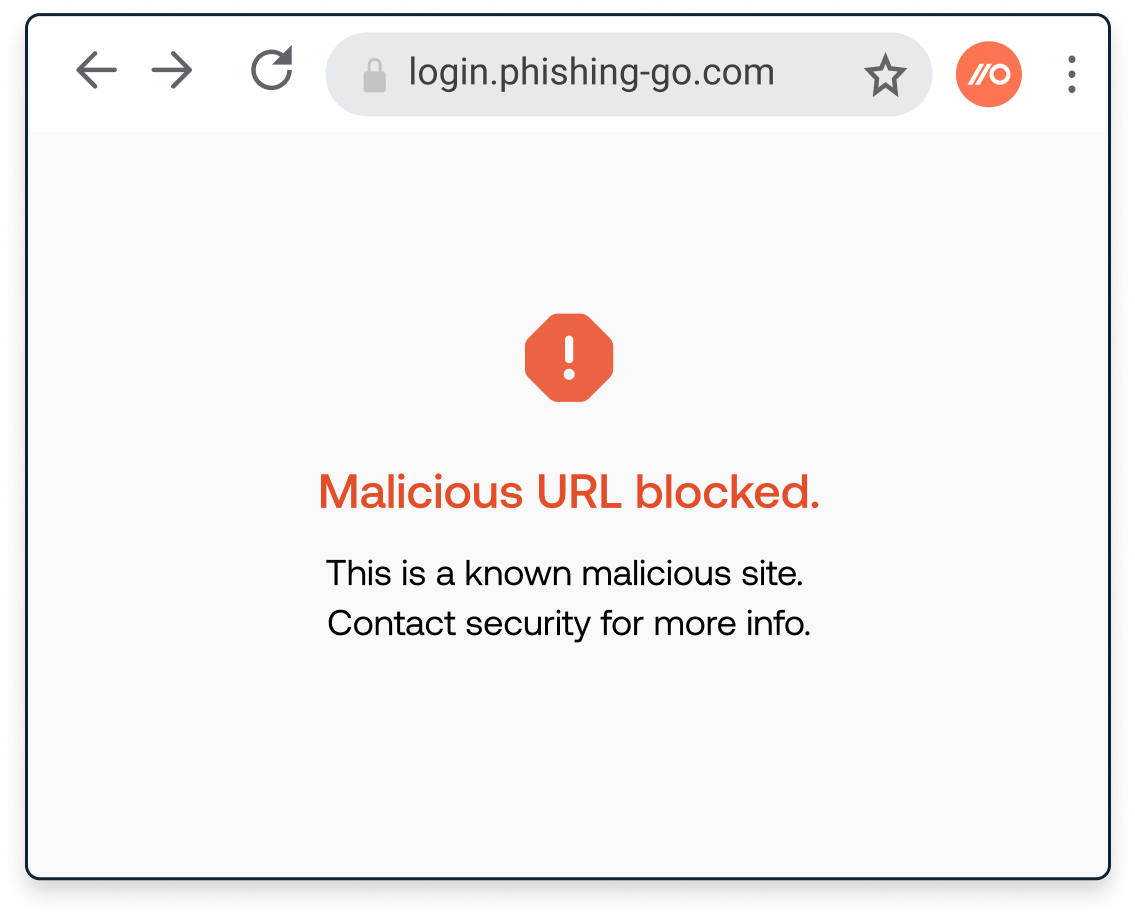
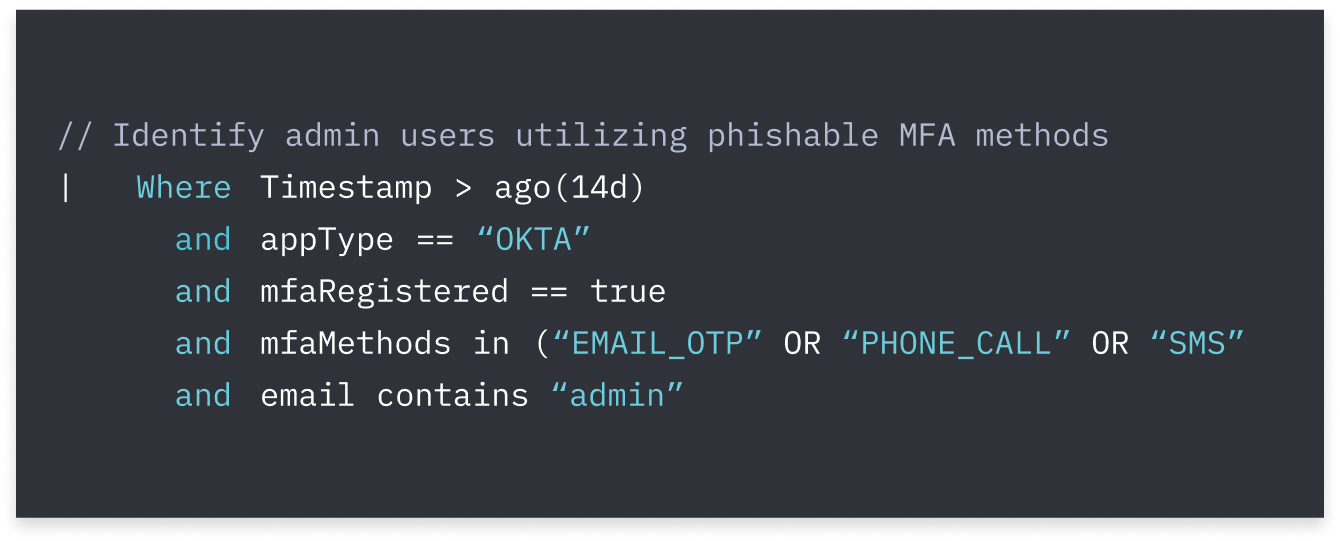
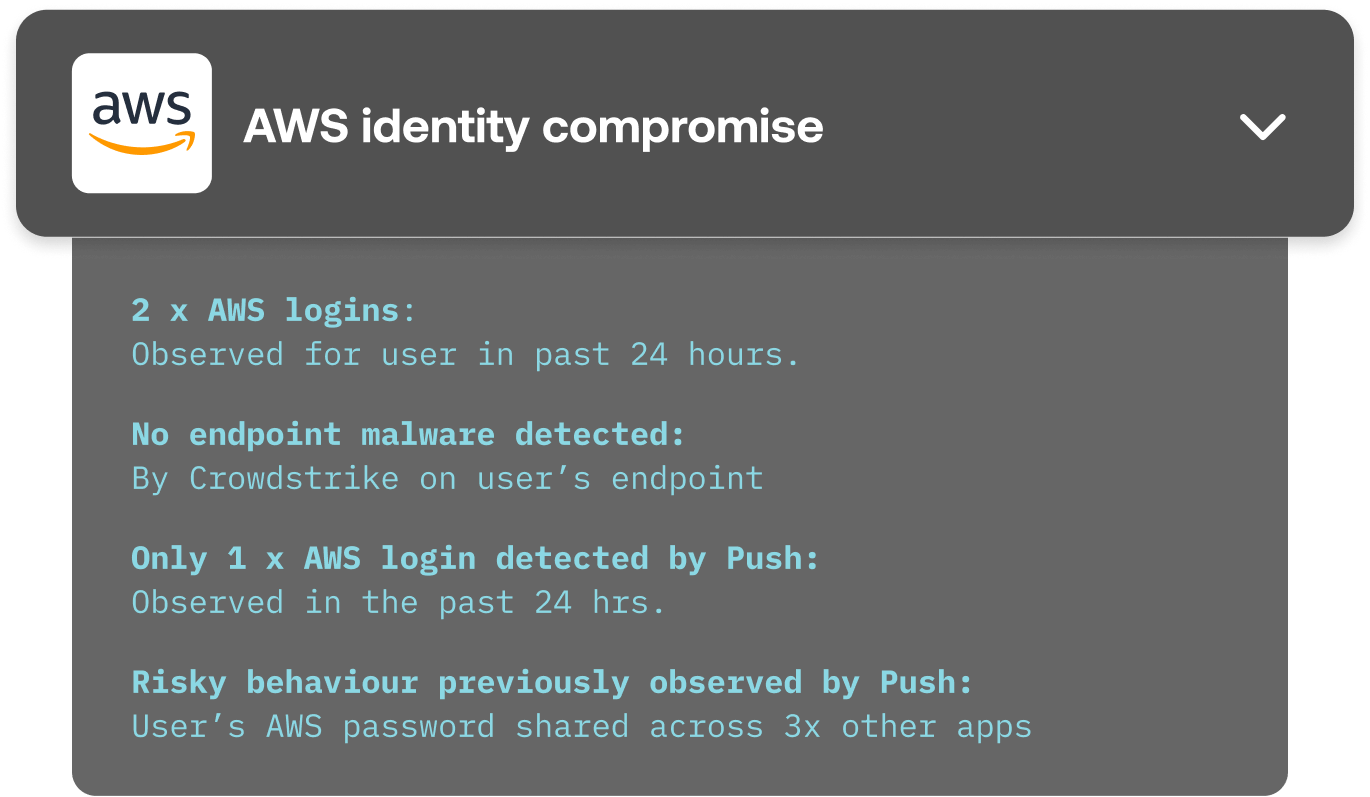
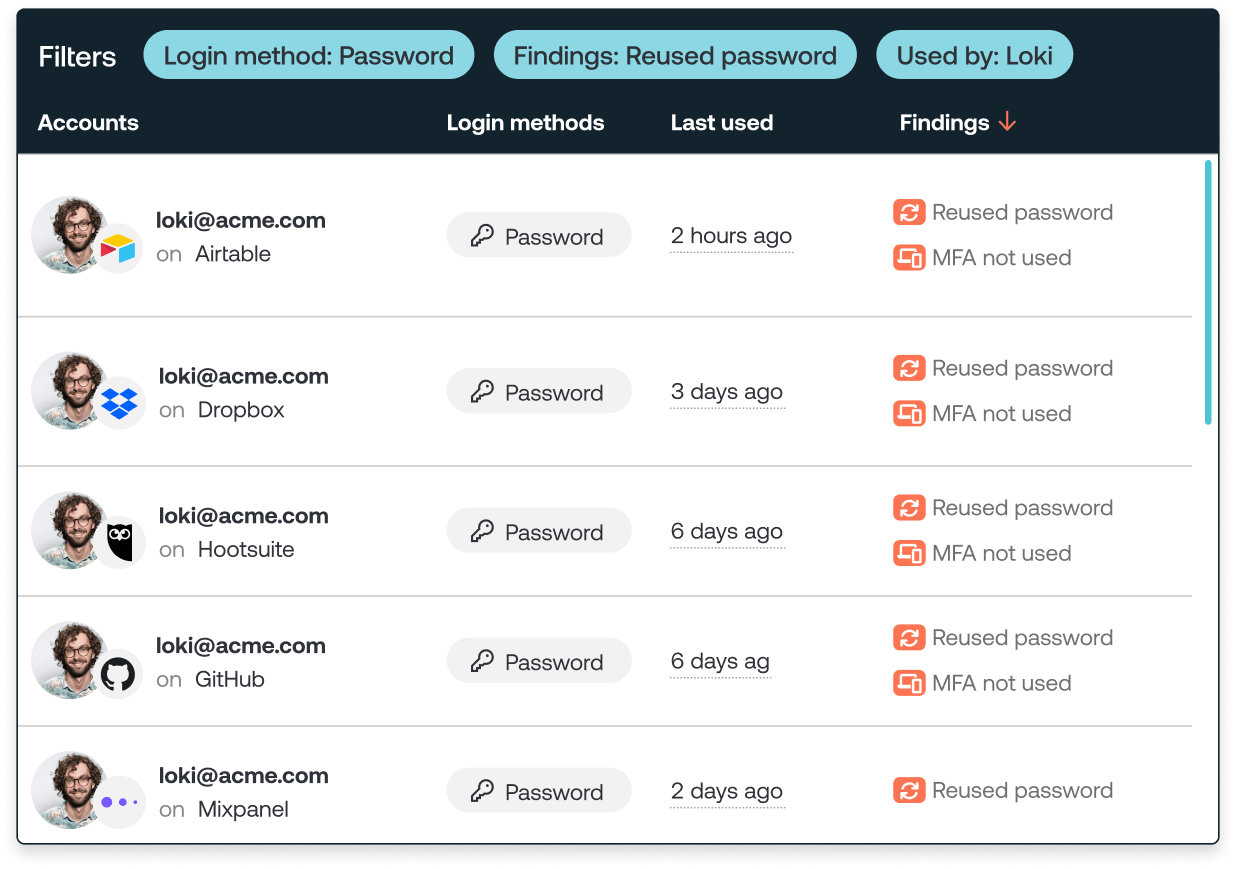
Stop employees having their credentials stolen. Instead of relying on known-bad signatures, Push dynamically inspects user behavior and attributes of the web page.
This means that even if you’re the first person to get phished using a new attacker site, Push still detects it and blocks it.