In this post, we're focusing on what to do after you've unearthed all the SaaS apps employees are using. SaaS discovery is only part of the process. What happens next is what leads to actual security improvements.
In this post, we're focusing on what to do after you've unearthed all the SaaS apps employees are using. SaaS discovery is only part of the process. What happens next is what leads to actual security improvements.
SaaS is exploding and making employees more productive than ever. If your security strategy relies on simply blocking all SaaS that hasn’t been sanctioned by your security team, you’re also blocking your coworkers from all the productivity gains that SaaS brings to the table. Not only that, but blocking through official channels doesn’t effectively stop employees from accessing the SaaS apps they want to use – you just can’t see it because they may have turned off the endpoint agent you’re using to manage SaaS policies, bypass the proxy, or change proxy settings. And now you’ve got a “Shadow IT problem!” *Dread ensues*
Some folks even choose to block or turn off app stores to limit SaaS adoption by employees. The issue with this is that you’re blocking them from using productivity tools they want to do their work. You think you’re preventing risk (though we know employees find ways to adopt and use SaaS regardless of your controls), but you’re also restricting employees from being productive, flexible, and, frankly, you’re ticking them off. These kinds of actions widen the divide between security and the rest of the company, which is never a good thing.
Stay cool, stay calm, we’ve got this. To manage SaaS, you need some sense of control over what employees are using and how they’re using it, right? By working with employees and doing the legwork to understand their needs, you can start to repair relationships there, which makes your job much easier in the long run.
However, before we go down the path of understanding how employees are using SaaS, you first need to know which apps they’re using.
How do I find the SaaS apps employees are actually using?
You can discover the apps employees are using in a couple ways: 1) manually, using the data you already have access to or, 2) using a pre-existing tool (oh hey, we have one you can use for free). We wrote a guide about how you might do the manual approach for SaaS discovery, though fair warning… this manual effort isn’t for the faint of heart.
For the purposes of this guide, we’re going to assume you’ve taken care of the SaaS discovery process already and you’re now facing a list of SaaS - potentially a very large one - you didn’t know employees were using.
If you haven’t discovered the unknown SaaS in your organization, we suggest you sign up, let us do the heavy lifting for you to discover SaaS, then use that list as a starting point for this next phase of the process…
I’ve found some SaaS apps I didn’t know about. Now what?
You’ve found the apps (hooray!), so now you’re on the hook to figure out what risks those apps might pose to the company (wasn’t ignorance bliss?). Does it help to know that most organizations find a large list of unknown apps so you’re not alone? A report from G2 Crowd stated that the average company has 975 unknown cloud services and that 67% of teams have introduced their own collaboration tools into an organization.
Even though you’re not alone, you still need to protect employee and company data from unnecessary third-party risk. Here’s a quick rundown of what you need to do next to get a handle on SaaS without restricting its use.
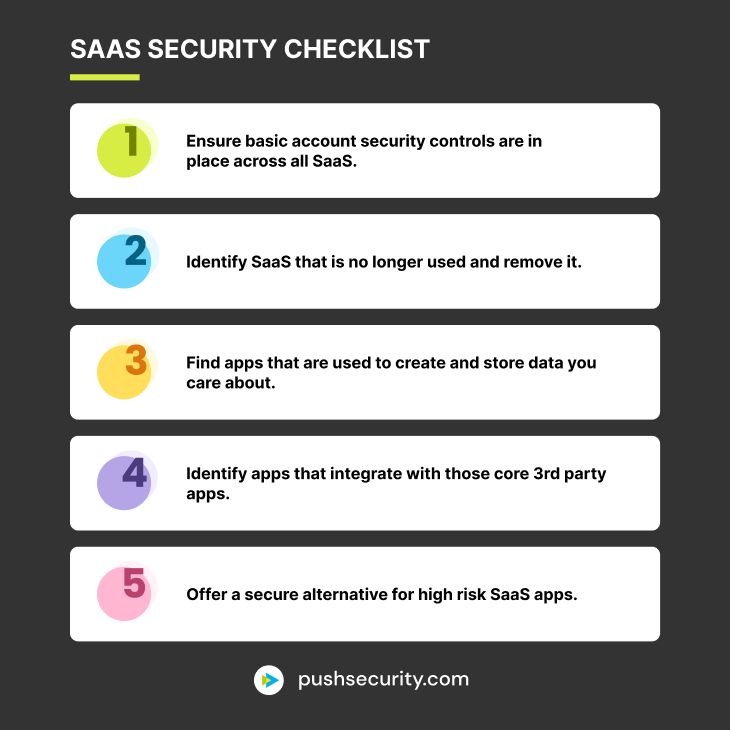
Ensure basic account security controls are in place across all SaaS. To get at this information, you’ll need either a tool (we got you!) or you’ll need to go directly to employees to get necessary information about how they’re accessing and using SaaS. You’ll need to know:
Are employees using multi-factor authentication (MFA) or two-factor authentication (2FA) where available?
What about strong passwords and password policies?
Are they sharing passwords across multiple apps?
Are they sharing login credentials as a team - some teams will do this to stay on a free or trial tier by only having a “single” user.
Try to identify SaaS that is no longer needed/used and remove it. You won't believe how quickly you build up SaaS baggage as users move to the newest hottest thing.
Identify apps that are used to create and store data you care about. Then prioritize them for some additional scrutiny.
Identify apps that integrate with those core apps. They’re also processing that same data you care about. These are usually called OAuth applications or third-party integrations like apps and bots that add functionality and features to the core app.
Where your additional scrutiny identifies risks you can't live with, stop new users adopting those apps (by giving them a better alternative) and migrate existing users over to that alternative, approved app.
To do this, you’ll need to look for secure alternatives to the SaaS employees are using that you have deemed too risky. This is important, albeit time-consuming. Offering an alternative sweetens the process for using more secure platforms before you outright block the bad ones. It also lets your colleagues know you’re considering their needs and not just restricting their work.
Beyond just the security of the technology itself, you need to ensure employees are doing their part in using the app securely.
How to prioritize which apps require additional scrutiny
There’s no right or wrong approach for how to prioritize the apps you find during the discovery process, but we’ve found that most our customers prioritize apps based on if the app is:
used by many people in the company, and
requesting access to highly sensitive data to work or integrating with SaaS that have data you don’t want exposed. This might be a cloud drive containing all sorts of documents, a CRM that uses customer data inputs, a billing platform, an app that’s used for signing legal documents, an HR platform, etc.
one you’ve never heard of before. Larger SaaS apps built for businesses (Salesforce, Microsoft, Google, etc.) are more likely to be secure than some of the smaller, newer SaaS apps who haven’t gone through the same levels of security reviews before going to market.
used by high profile employees or employees with access to very sensitive corporate information (C-level executives, finance, legal, HR, etc.).
For example, if you have a whole team using a single app that you’ve never heard of, add that app to the top of your priorities list for investigation. It’s likely business critical and serving a need for that team, so taking it away won’t be a good idea if you’re trying to build bridges between security and employees. Plus, more users probably means more data is stored within the app. Those users might also have integrated a lot of third-party apps or bots (OAuth) to that core application.
Once you’ve determined which apps need investigation and prioritized them, head over to the National Cyber Security Centre’s lightweight approach to cloud security article. They offer some great guidance for how to reasonably access the risk of a SaaS app with limited time and resources.
A big missing piece most companies have in their SaaS security strategy, though, is that they’re not working with employees to understand how they’re using SaaS. Before you roll your eyes, hear us out…
Secure SaaS by working with employees
Remember, employees are the owners of SaaS in your company - they’ve adopted and used SaaS tools in your environment, so they know better than anyone else how they’re using it, if they’re still using it, what the additional integrations in the app offer, and what it does for them. You, as their security lead, know how to determine if they’re logging in securely, if the data the app is requesting access to is an acceptable risk, if they’ve enabled built-in common sense security features like 2FA/MFA, and if the third-party integrations they’ve added are too high risk or requesting excessive permissions.
By working with employees, you can get the full picture of SaaS use within the company and understand what your colleagues need and coach them to improve the security of how they’re accessing and using the tools they prefer. The problem is that it’s really difficult to do manually in a real world environment because it’s just so time-consuming to reach out to each employee and ask a series of questions to get the context you need.
If an entire team is using an app you weren’t aware of, you can talk to the technical owner or administrator of the app to understand how they’re using it. What doesn’t work at scale with manual outreach, however, is understanding how securely employees are logging in and accessing SaaS.
You can automate this process with the right tool, using things like ChatOps and browser notifications, and just sit back and watch as employees improve their own security over time. This is particularly useful when it comes to some of the security hygiene basics, like using strong passwords and enabling MFA, which make a significant impact on overall security posture for very little effort.
What will I gain from working with employees?
Now that you know that working directly with employees to secure SaaS isn’t a pipe dream, nor does it have to be a manual effort or a one-off security campaign, what impact should you expect from these efforts? And how do you measure that impact?
Here are some of the most obvious wins…
Reduce your attack surface
Say you discover your marketing team is using Trello to manage projects, while the sales team is using Asana. Once you have this information, you can talk to the heads of each department to see if they’ll agree on a single solution.
Without management, you’re likely to wind up using multiple (often dozens) of chat, project management, calendar-sharing apps and so on within your company. The issue with this is that it opens you up to unnecessary risk, with your data being held on the systems of hundreds of third parties outside of your traditional perimeter. By connecting users to each other and consolidating the SaaS apps in your company, you can dramatically reduce your attack surface.
Similarly, removing dormant apps and accounts can have a huge impact. In a recent report by Productiv, they found that on average only 45% of the apps an organization or its employees have an account with are regularly engaged with. That means that potentially half of your SaaS attack surface is totally unnecessary.
Working with employees to find out what apps they are using (and which they are no longer) will allow you to eliminate attacker opportunities to access your data or steal employee account credentials.
Reduce supply chain risk
Every third-party SaaS app that your employees use is a supplier and therefore contributes to your overall supply chain risk exposure. Traditionally all technology and software providers will have been reviewed by security teams to ensure that they do not present excessive risk to your organization. However, the explosion in SaaS use has made this more challenging; 1) Most organizations have a large number of SaaS suppliers and its growing, 2) SaaS suppliers are now responsible for more aspects of security than on-prem software suppliers ever were (such as infrastructure security) so there is more to review and assure.
Every time a duplicate or dormant SaaS app is removed, you’re removing a supplier whose security practices and posture need assuring. This saves your security team bags of time and reduces your overall cyber risk exposure.
However, for the third-parties you need to continue to work with, you’ll want to perform due diligence to make sure you aren’t exposing yourself to the risk of a supply chain attack.
Before you can trust a SaaS vendor with your data, you have to be assured the vendor is committed to maintaining an appropriate security standard and has the resources and capabilities to deliver against it. And you need to know how the vendor will secure your data when it is in transit, use and at rest. Understand how the vendor secures their network, monitors for malicious activity, what they’ll do in the event of an incident, and whether they have an adequate business continuity and disaster recovery plan.
To speed up the due diligence process, you might rely on the vendor providing certification of a recognized standard, such as ISO27001, which demonstrates a solid security baseline.
Establish security as a business enabler
One thing to note, if you’re removing an app, it’s always a good idea to notify the employee(s) using it and suggest secure alternatives. Security teams are often seen as a blocker to be avoided and worked around. During that conversation, you can ask them what they were using the app for and then do some research to offer an alternative option that isn’t as risky to the company.
Being able to recommend useful tools that can help your colleagues with their jobs (as opposed to just saying no or blocking unsanctioned apps) is the difference between being seen as a business enabler rather than a business blocker. Once your security team is known for promoting innovative new technology as well as managing risk, employee engagement will increase.
Greater productivity and competitiveness
SaaS has empowered employees to self-adopt the tools that will help them do their jobs better. This is something that should be harnessed, not resisted. A more productive workforce creates a more competitive company. Security’s job is to manage the risks it introduces to a level that the business can accept, not to eliminate those risks altogether.
Balancing productivity returns with cyber risk requires employees and security to work together to understand the trade-off and make the best decision for the whole organization. If you can facilitate this collaboration to make better decisions, faster as to what technology and tools your organization can safely take advantage of, then your organization will be more competitive and more successful.
You can secure SaaS without pissing off employees
We’ll end this blog with a single key takeaway:
To keep employees happy and productive while still securing corporate data, you need to work with them to understand what they need and point them at the most secure SaaS alternative.
One of the big wins that’s really hard to measure or quantify is that by working with employees, you position yourself as a business enabler. The more you know about the tools employees are choosing to use, the more you understand their needs and desires so that you can find a balanced solution.
We would never recommend that you just open the gates to SaaS and leave employees to sign up with wild abandon, but strictly locking down SaaS clearly doesn’t work. With more SaaS apps coming to market daily, the only approach that can scale and keep up with employees’ needs for productivity and flexibility is one that makes them part of the conversation. You’ve got to work with the SaaS users and empathize with their needs. Only then can you really create a cloud security strategy that’s going to work in the real world. With new tools that can do the heavy lifting for you, a user-powered approach finally makes sense. You got this.

