Push analyzes behavioral attributes of malware to identify advanced phishing tools like Evilginx and NakedPages in use on websites and immediately block end-users from visiting them.
Push analyzes behavioral attributes of malware to identify advanced phishing tools like Evilginx and NakedPages in use on websites and immediately block end-users from visiting them.
Is the golden era of MFA protection over? Watch a demo of an EvilNoVNC phishing attack and you may be left sweating a little and whispering “FIDO2” like a protection spell.
With the widespread adoption of MFA, attackers are increasingly turning to more sophisticated methods of credential theft as their initial point of entry.
Newer phishing approaches include reverse proxies as well as tools that mimic legitimate login pages by rendering the webpages and then displaying those renders to the unsuspecting end-user. While these tools are not always common knowledge among blue teams, their use is on the rise, an unsurprising response to the broad use of multi-factor authentication in many organizations.
What sets this generation of Adversary-in-the-Middle (AitM) phishing tools apart?
They act as a proxy between the user and a legitimate web login page, allowing the attacker to bypass MFA and harvest credentials and session tokens.
They give off little scent to end-users, because the end-user is logging into the legitimate site, just by taking a detour via the attacker’s device.
These AitM tools are also difficult to detect — unless you have eyes in the browser.
Powered by the Push browser agent, Push now offers a preconfigured set of detections for phishing tools like Evilginx and others, informed by our threat detection team’s research into their behavior. This phishing tool detection feature will automatically prevent users from accessing a site that’s running one of these malicious tools, and display a custom warning message to your end-users.
While Push already provides strong phishing protection by preventing SSO password use on non-IdP webpages (in other words, it stops you from using your Okta password on any page that isn’t an Okta login page), this new feature allows us to sharpen our anti-phishing capabilities by detecting malware on a site before a user even interacts with the page.
In this article, we’ll describe our approach to detecting these newer phishing tools, including how we’re borrowing techniques from the world of EDR, and how you can combine phishing tool detection with other Push controls for a defense-in-depth strategy that covers both the user and the application sides of the equation.
Taking a page from EDR
Most phishing prevention solutions rely on lists of known-bad sites as the source of intelligence. These are always going to be a step behind reality because they rely on ever-shifting secondary attributes such as domain names (though we won’t be disabling Chrome Safe Browsing anytime soon, and we’re not trying to replace it).
As veterans of the EDR world, we’re drawn to think in analogous terms. With detecting AitM phishing tools, that means expanding on the concept of dynamic analysis on the endpoint. EDR allows you to dynamically analyze the behavior of malware live and at scale, rather than focusing on easy-to-change indicators like file hashes or domain names.
Applying this idea to malware that runs in the browser requires a solution that is in the browser, like the Push browser agent.
So we’re expanding the attributes that are traditionally analyzed to spot indicators of compromise (IoCs) beyond domains, file names, file hashes, IP addresses, etc., to also include behavioral attributes of malware that are much harder to change, such as Javascript calls being made or data structures saved to local storage.
By performing behavioral analysis on AitM automated proxy tools, we can directly analyze the application for a precise and immediate identification.
Push researchers are regularly identifying and adding detections for new toolkits — think of this like Push’s database of threat research in action.
How it works
If you’re new to Push, a bit of context may be useful. Push uses a browser agent deployed to employee browsers (we support all major browsers) to prevent, detect, and block identity attacks.
By directly observing user behavior at the login event, Push provides broad and actionable context across all the apps your employees are using, how they are accessing them, their MFA methods, and where they’re using insecure and reused passwords. With this context as the foundation, Push enforces your desired security controls, including preventing SSO password reuse, blocking malicious websites, or steering employees to approved apps only.
Once configured by an administrator, phishing tool detection will immediately check for the fingerprints of these toolkits as end-users visit websites and then display your custom warn or block message.
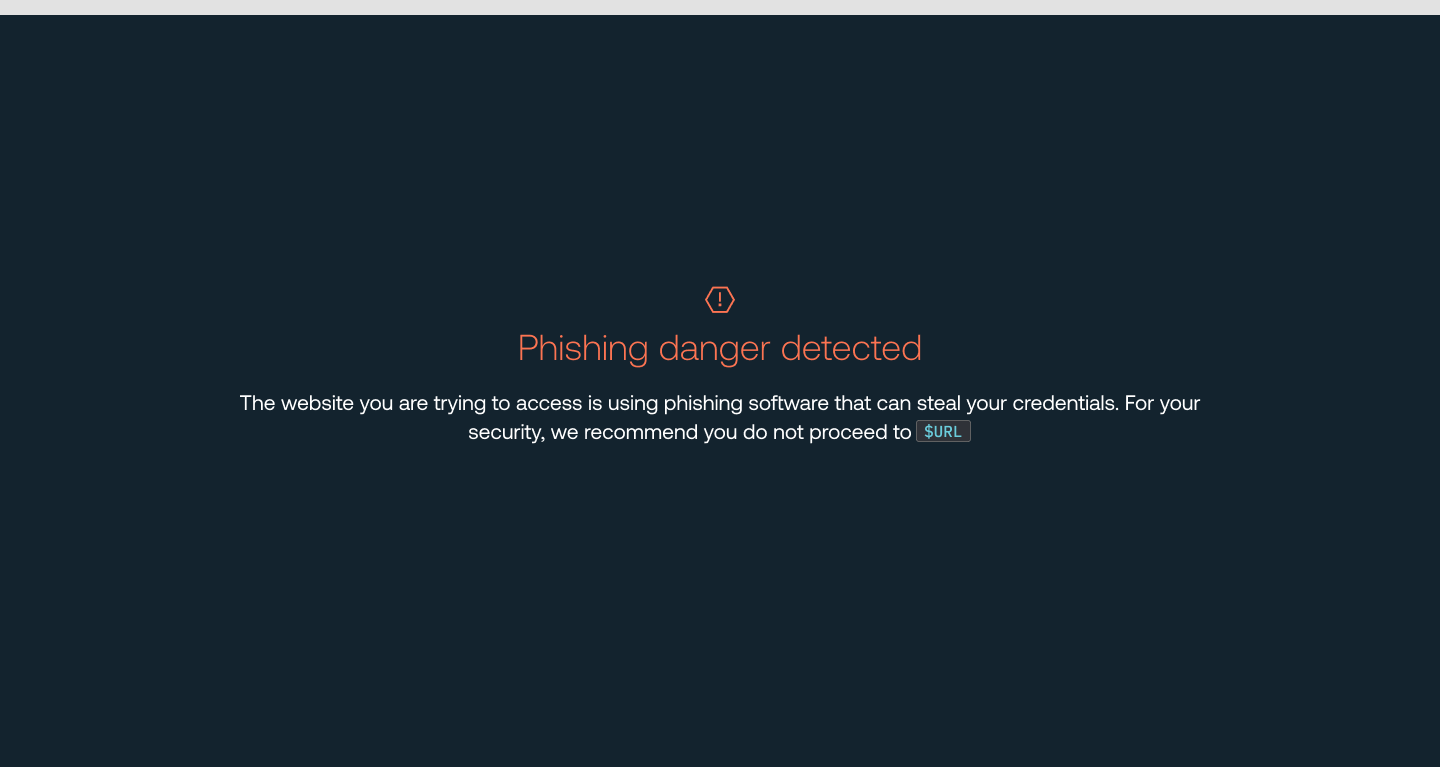
In Block mode, users cannot proceed to the site where malicious software has been detected. In Warn mode, users can choose to proceed if they are sure it’s not a phishing site.
In both cases, users do not need to interact with a page (by typing, clicking, etc.) for Push to trigger the custom message.
Administrators can also consume phishing tool detection events via the Push REST API into their SIEM or use Push’s webhooks to alert when a warn or block event has occurred.
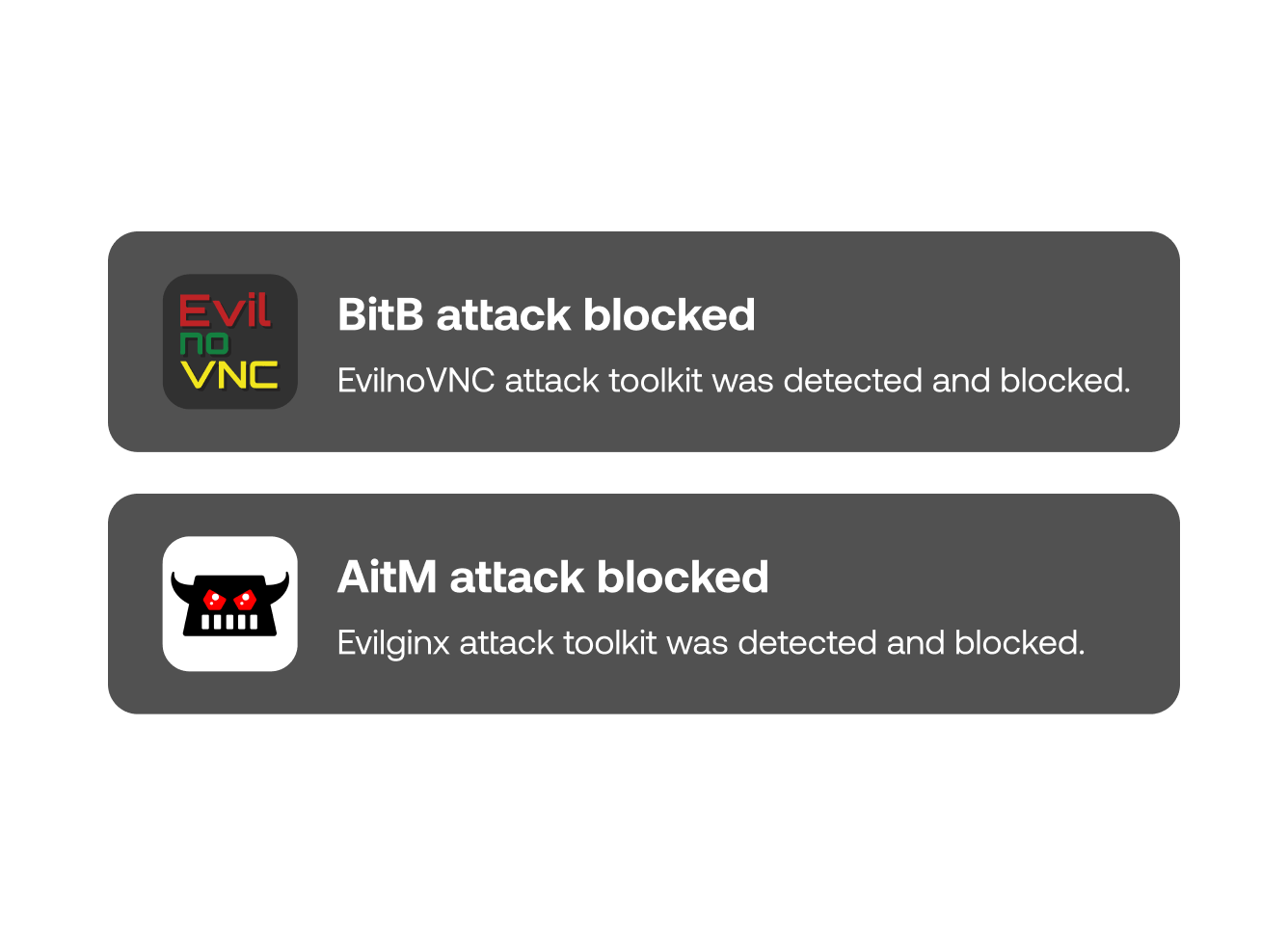
Pairing this phishing detection capability with Push’s SSO password protection feature provides a strong defense-in-depth strategy for stopping credential theft.
SSO password protection works by analyzing user behavior — namely, is a user entering their SSO password onto a page that does not belong to the legitimate identity provider.
Phishing tool detection adds in the application-level behavioral analysis. In addition, when Push identifies a new, previously unknown phishing tool in the wild via blocked SSO credential theft, we add its fingerprints to the browser agent’s detective capabilities.
Looking ahead
We’re just scratching the surface on this approach and are exploring how Push can identify and block other web-delivered malware and Javascript-based attack types beyond AitM tools. Think HTML smuggling, tabnabbing, and the like.
Got feedback? We’d love to talk.
Find out more
To see Push in action, book a demo. We’ll be happy to show you this feature, along with how we discover all the apps your employees are using, even the ones not behind SSO, and how we detect vulnerable identities and stop identity attacks with browser-based controls.



