Reviewing public breaches that stemmed from identity attacks in 2024.
Reviewing public breaches that stemmed from identity attacks in 2024.
2024 was an unprecedented year in terms of the impact of identity-based attacks. Or that’s what it felt like anyway, so I decided to trawl through a year of news to see if reality stacked up.
My main obstacles here were the ever-disappointing levels of public information disclosure for cyber breaches. Even where breaches are disclosed, it’s rare that any public information contains the nature of the initial access vector (though I can’t say I’m surprised — it’s hard to argue the ‘highly sophisticated’ nature of a breach that involved stolen credentials and no MFA).
Publicly disclosed breaches are just the tip of the iceberg, and with the rise in data theft and extortion over more disruptive attacks (e.g. ransomware), there is often no obvious service interruption indicating that an incident has taken place. This makes it more likely that these situations can be settled quietly or smoothed over, without hitting the headlines.
That said, the requirement that US companies submit a Form-8K for breaches of a material nature does appear to have increased the number of voluntary declarations (inside the US, at least) and the growing willingness of the SEC to prosecute negligent or misleading behavior is also a considerable motivator, such as the recent prosecution of companies for misleading investors about the impact of the 2020 SolarWinds Orion hack.
Despite all this, I totalled 30 breaches that were the result of an identity-based initial access vector, such as phishing, credential stuffing, social engineering, session hijacking, etc. To make the list, it had to have appeared in the public domain, confirmed by the victim or an authoritative source, and the breach vector had to have been named.
Public identity-related breaches in 2024 resulted in hundreds of millions of breached customer records (with the final impact of many still yet to appear in the public domain).
What is an identity attack?
First, what do we mean by identity attack?
An identity attack is any attack (regardless of the steps that follow) involving identity-based techniques, such as phishing, credential stuffing, and session hijacking, to log into an account/service. Basically, where identity is the initial breach vector.
The length and complexity of the overall attack chain will vary. For example, a SaaS-based account takeover where the attacker logs in and dumps the data from the app is naturally going to be more direct than a scenario in which an identity-based compromise leads to the takeover of an endpoint or device in a traditional networking environment.
In 2024, we’ve seen examples of both SaaS-based account takeover as well as identity attacks being used for initial access to more traditional networks, often resulting in ransomware deployment.
Breakdown of public identity breaches in 2024
It’s always tricky to gauge the impact of a cyber breach, particularly when considering the limited information typically shared. Different types of breach are easier to assess than others — for example, any breach involving extortion/ransom payment has a clear cost associated. Regulator fines and penalties are also clear cut. But aside from these, you’re looking at the extent of any disruption/downtime, recovery costs, and the like. Long term, indirect impacts such as the loss of customer confidence are naturally tricky to estimate.
However, many identity breaches don’t even have these metrics to go by. The general shift toward data theft only (as opposed to ransomware deployment) continued in 2024, and many of the public identity breaches reflect this. In these attacks, attackers steal data to extort a ransom payment, blackmail end-customers, and/or sell the data via underground criminal marketplaces.
The one consistent metric we do have is the number of breached records, which is available in many (but not all) cases. Some organizations have attempted to calculate the financial impact per breached record. Most notably IBMs annual ‘Cost of a Data Breach’ report estimates the average data breach to cost $4.88m, and the cost per compromised record to be $169. But when applied to the sheer magnitude of 2024’s biggest attacks (in the region of hundreds of millions of breached records) the figures quickly reach unbelievable levels.
All this is to say: It’s hard to pin down the relative impact of data breaches. But with the information available (profile of the victim organization, type of data impacted, number of customers impacted) it’s possible to provide a finger-in-the-air assessment — which is what I’ve attempted to do below. Here, we can see the overall month-by-month impact of public identity breaches, dated from when they were first reported (or using dates provided in said reports).
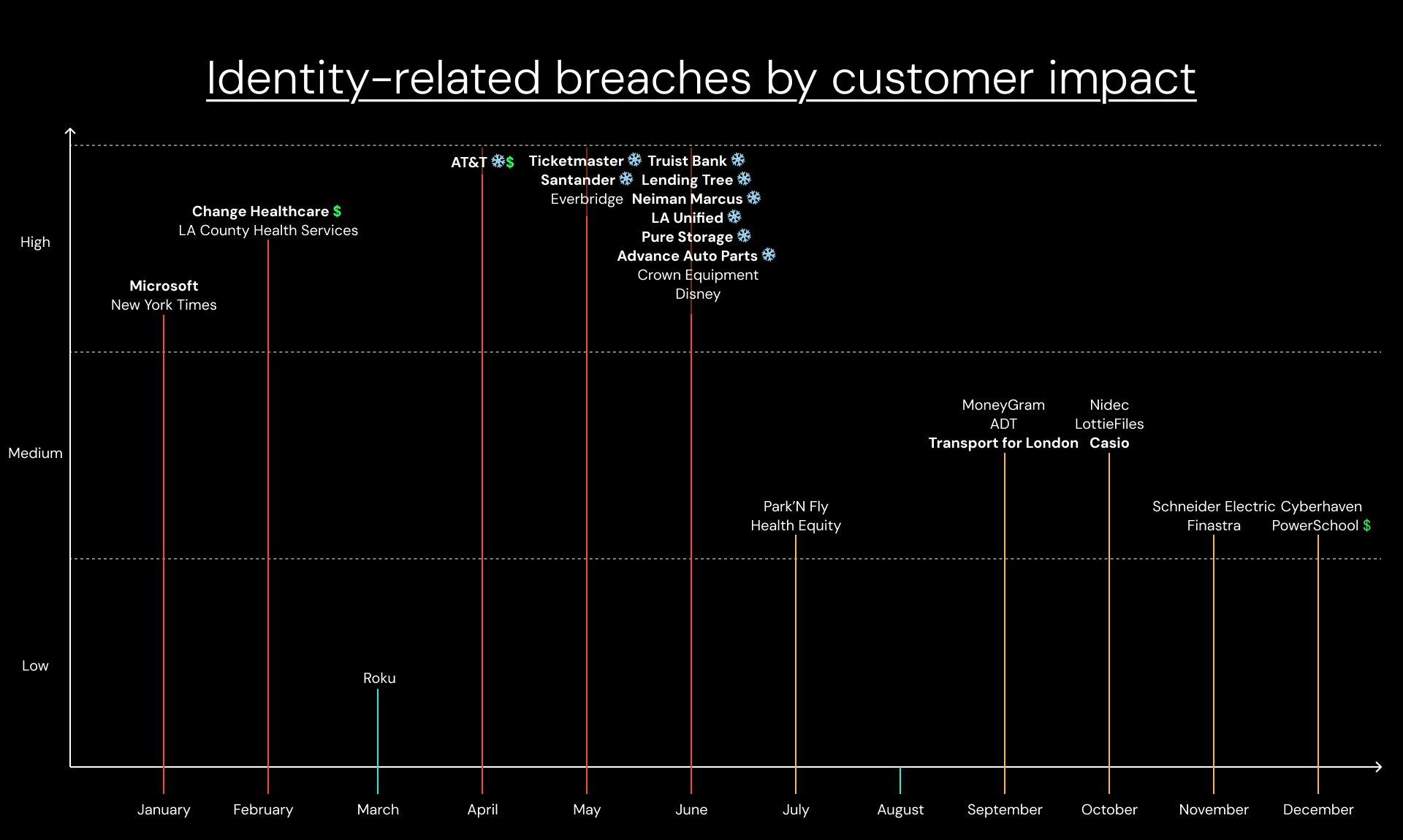
Let’s take a closer look at the most notable breaches (and why they were especially significant).
Top 3 public identity-related breaches in 2024
#3: Microsoft — January 2024
The threat group known as APT29, associated with the Russian SVR intelligence service, utilized password spray attacks that successfully compromised a non-production tenant account that did not have multi-factor authentication (MFA) enabled. They then leveraged this account to compromise a ‘test’ OAuth application that had elevated access to the Microsoft corporate environment. This was then used to access the email accounts of Microsoft employees.
The attacks then continued throughout the year using information stolen from Microsoft mailboxes, with password spraying attacks increasing tenfold since the initial attack, resulting in the further compromise of source code repositories.
Microsoft has shared limited information about the breach, but despite this it caused a significant stir. We can expect the number of email accounts compromised to be significant, given that it was later suggested that at least 100 external organizations had been contacted by Microsoft regarding their communications being breached (we only know this because 100-ish organizations reported the email as spam). The list of companies impacted included both public and private sector organizations, from major enterprises to government agencies in the US and other countries.
Microsoft’s challenges with credential management didn’t end here either, with bug bounty hunters able to use stolen credentials from a TI platform to breach Microsoft’s ServiceNow tenant, accessing 1,000s of support ticket descriptions and attachments, and 250k+ employee emails.
#2: Change Healthcare — February 2024
In February, attackers stole 6TB of data from UnitedHealth subsidiary Change Healthcare as part of a severe ransomware attack that caused massive disruption to the US healthcare industry. This impacted a wide range of critical services used by healthcare providers across the U.S., including payment processing, prescription writing, and insurance claims, and caused financial damages estimated at $872 million. The attack impacted the personal medical data of over 100M customers.
The attacker used stolen credentials to breach the company's Citrix remote access service, which did not have multi-factor authentication enabled, as the initial breach vector for the attack.
Following the attack, the organization's IT team replaced thousands of laptops, rotated credentials, and completely rebuilt Change Healthcare's data center network and core services.
The UnitedHealth Group admitted to paying a ransom demand to receive a decryptor and for the threat actors to delete the stolen data. The ransom payment was allegedly $22 million, according to the BlackCat ransomware affiliate who conducted the attack.
#1: Snowflake — April-June 2024
165 organizations around the world were targeted using stolen credentials gathered from infostealer infections dating back to 2020. The impacted accounts lacked MFA, meaning successful authentication only required a valid username and password. As the Snowflake credentials found in infostealer malware credential dumps had not been rotated or updated, they remained valid and could be used to authenticate to user accounts on Snowflake tenants belonging to various customers. It has been touted by some news outlets as ‘one of the biggest breaches ever’.
In total, nine public victims were named following the breach, collectively impacting hundreds of millions of their respective customers. Data was put up for sale on criminal forums for fees ranging from $150k to $2m per organization, while AT&T was also confirmed as paying an undisclosed ransom fee.
Identity attacks vs. other attacks in 2024
In many ways, 2024 was a year of identity attacks. The attacks on Snowflake customers was unarguably one of (if not the most) significant cyber security event of the year (at least, if you exclude CrowdStrike causing a worldwide outage in July) — certainly, it was the largest perpetrated by a criminal group against commercial enterprises.
Arguably the biggest non-identity story of the year was the Chinese state-sponsored “Salt Typhoon” campaign against global telecommunications firms, with at least nine major providers compromised — including AT&T, Verizon, and T-Mobile. The group reportedly focused on infiltrating telecommunications infrastructure to steal text messages, phone call information, and voicemails from targeted people. The threat actors also targeted the wiretapping platforms used by the US government, raising serious national security concerns.
Undoubtedly this was one of the biggest intelligence compromises in US history and is of major significance. But it’s also arguable that identity attacks had a more widespread commercial impact in 2024 when we look at the big picture.
Attacks on edge networking devices were also incredibly prominent, as were very much interlinked with the targeting of telecommunications infrastructure. A barrage of 0-days generated a huge amount of concern about the software security practices of many vendors.
But despite these honorable mentions, the runaway threat of the year was an identity-based one…
Threat of the year: Infostealers
2024 saw an unprecedented rise in the role of infostealers. The played a huge role in the attacks on Snowflake customers, where 80% of the accounts were targeted using credentials found in infostealer infections.
News relating to new infostealer variants and distributions campaigns came thick and fast in 2024, as attackers sought to harvest credentials from victims to use as part of their own malicious campaigns, or to sell on to other criminals on underground marketplaces for compromised credentials. Attackers leaned into alternative distribution channels, branching away from email-based campaigns to target victims via gaming forums, Facebook ads, and YouTube video descriptions. GitHub was also continuously targeted as a malware distribution mechanism throughout the year — and the majority of the time it was to push infostealers.
Infostealers are the weapon of choice for attackers looking to harvest credentials at scale. Compared to credential harvesting phishing campaigns, infostealers target a much broader range of credentials, taking everything saved in the victim’s browser (and often also from local apps, including password managers).
Infostealers are nothing new, but have historically been seen as a problem affecting less secure personal devices and accounts. But 2024 has demonstrated that infostealers are finding ways to harvest business data — by finding ways around controls like EDR, and because of the ways that personal and business identities and accounts are converging in the modern workplace. For example, it’s not uncommon for employees to log into their personal Google account on their work device (and vice versa), inadvertently saving corporate credentials to their personal password store — which is later compromised through an infostealer infection on a personal device.
The impact of infostealers (and the resulting stolen credentials and session cookies) is underlined by various figures:
79% of web application compromises were the result of breached credentials (Verizon).
Infostealer activity increased by 266% in 2023, while the number of attacks featuring valid credentials saw a 71% increase year-over-year (IBM).
Nearly half of the malware detected last year targeted victims’ data specifically, and the majority of that malware was classified as infostealers (Sophos).
39,000 session token attacks are detected per day (Microsoft).
Attacks on session cookies happen at the same rough order of magnitude as password-based attacks (Google).
And of the confirmed identity-based breaches in the public domain that we identified, a whopping 73% were the result of compromised credentials (the rest were phishing attacks).
As the primary source of compromised credentials, it’s fair to say that infostealers deserve the top spot for 2024.
Defend against infostealers with Push
As a browser-based identity security platform designed to stop identity attacks, Push helps organizations to defend against the rise in infostealers by:
Alerting you whenever the valid credentials your employees are using appear in a compromised credential data feed, which can be leveraged to trigger automated password resets whenever an event fires and is received by your SIEM tool.
Detecting session hijacking attacks using stolen cookies to identify when an attacker logs into an app from an unmanaged device without the Push browser extension — this can also be used to detect suspicious access in general!
Enabling you to enforce MFA the next time an employee logs into an app (even when the app itself doesn’t allow you to enforce mandatory MFA) — particularly handy if a weak, breached, or reused password is detected for their account!
And much, much more.
If you’d like to explore the platform yourself and discover more of our great features, you can request a demo.


