What is consent phishing?
Consent phishing is a technique that tricks a user into granting a malicious third-party app access to their account. Since this technique preys on users that are already logged in, it is effective against users with strong passwords, multi-factor authentication, or even passwordless setups.
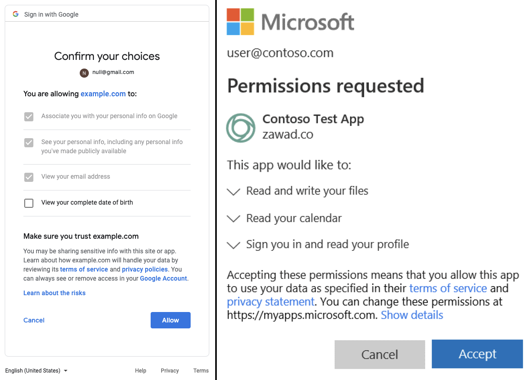
To execute a consent phishing attack, an attacker first registers an OAuth 2.0 app with the target platform (e.g. Microsoft 365 or Google Workspace). The requirements to do this vary platform-to-platform but they are often minimal.
Users are then lured to grant the app access to their account using common phishing tactics, such as an invitation to edit an interesting-sounding document.
The user is then taken to a legitimate consent screen for the target platform detailing the access requested. If the user consents, the app is able to access their account as specified on the consent screen.
The user is often then told something innocuous, like the invitation no longer exists, and they are unaware they have been compromised.
You can read a detailed description and walkthrough of a consent phishing attack on our blog.