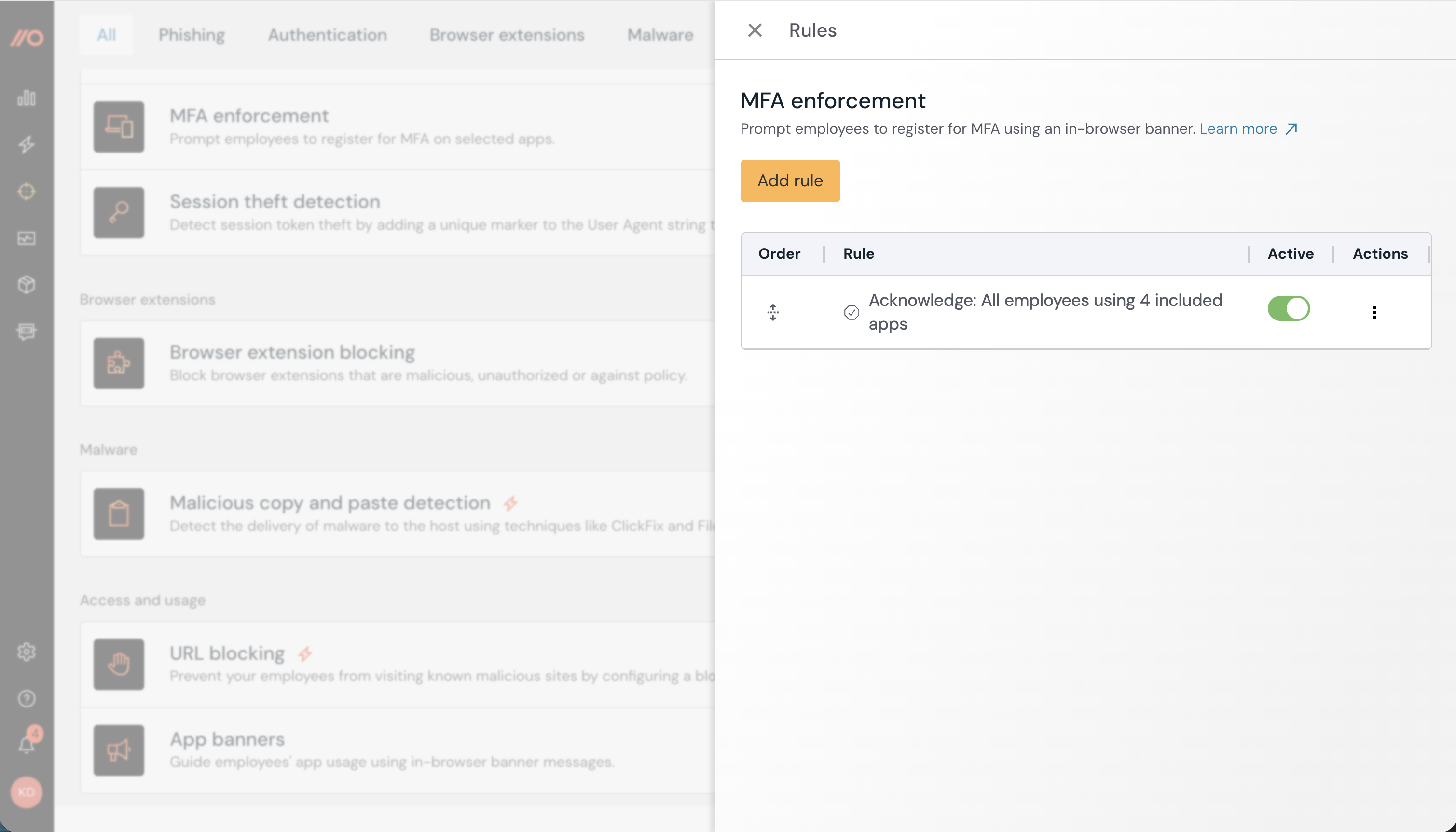
How does MFA enforcement work?
Using Push’s MFA enforcement control, you can prompt end-users to register for MFA on apps where they lack it.
When an employee’s browser is enrolled in Push, the Push browser extension uses their active session to check whether they’re registered for MFA. If they’re not registered, the user will see an in-browser banner instructing them to sign up for MFA.
How it works
As soon as the Push extension observes an active session on an app where MFA enforcement is applied, it uses the logged-in user’s existing session to query the app’s API and check their MFA registration status.
If the employee is not registered for MFA, the extension displays an in-browser banner message. The message and button text are customizable by a Push administrator.
Note: For apps that Push has just observed (such as new signups to apps), the MFA enforcement banner will only display after several minutes. This is designed to avoid blocking users who haven't yet had a chance to add MFA to a new app.
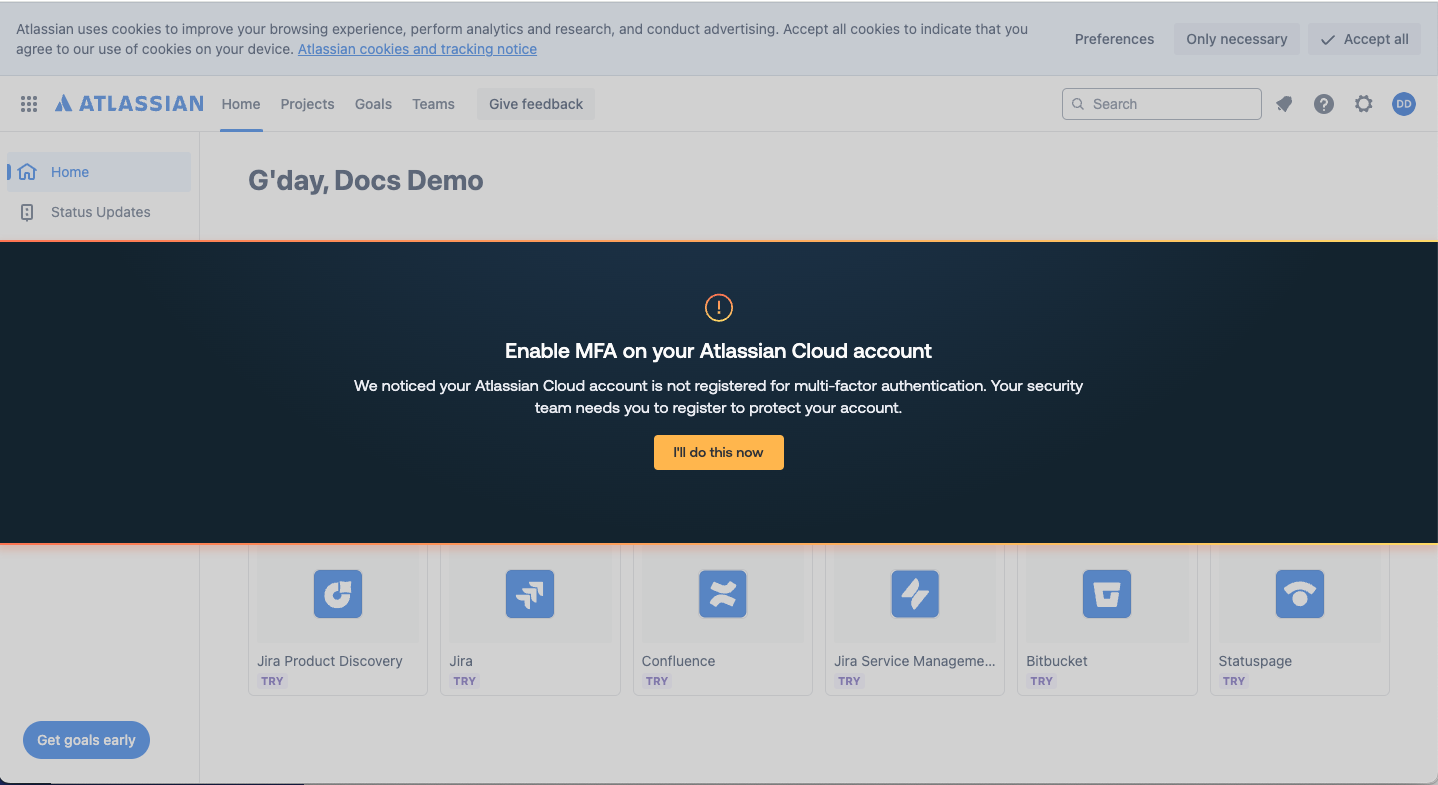
Once the banner is triggered, the extension then checks for the employee’s MFA status every 5 seconds. Once the extension detects that MFA registration is complete, the banner disappears.
If the employee closes the banner, they won’t see it again for at least 12 hours, or whenever they next use the app.
If an app supplies a distinct MFA registration page, the banner button will take the user directly there to complete the process.
Note: When enabled, this control will enforce MFA registration across all tenants (instances) of the selected app. This means you can enforce MFA even on test or unmanaged tenants.
How to create a configuration rule
You can configure this control to apply to all employees, employee groups, or just specific individuals. You can also create an exception for specific employees or employee groups who will be exempted from this control. Finally, you can enforce MFA based on all apps, specific apps or app attributes.
When you enable the control, you’ll create a configuration rule that sets the Mode (Off or Acknowledge), the Scope (all employees, specific groups, or specific individuals) and Apps (all apps that the control applies to, specific apps, or app attributes). App attributes allow you to set a banner based on app labels, sensitivity level, and approval status. Note that attributes are a Boolean AND operation.
To exempt an individual or group, create a rule where the Mode is set to Off and then choose the group or people who should be exempted.
You can control the order in which rules are applied by setting the rule order on the configuration slideout. Rules are executed from the top down. Use the handlebars in the Order column to drag and reorder rules.
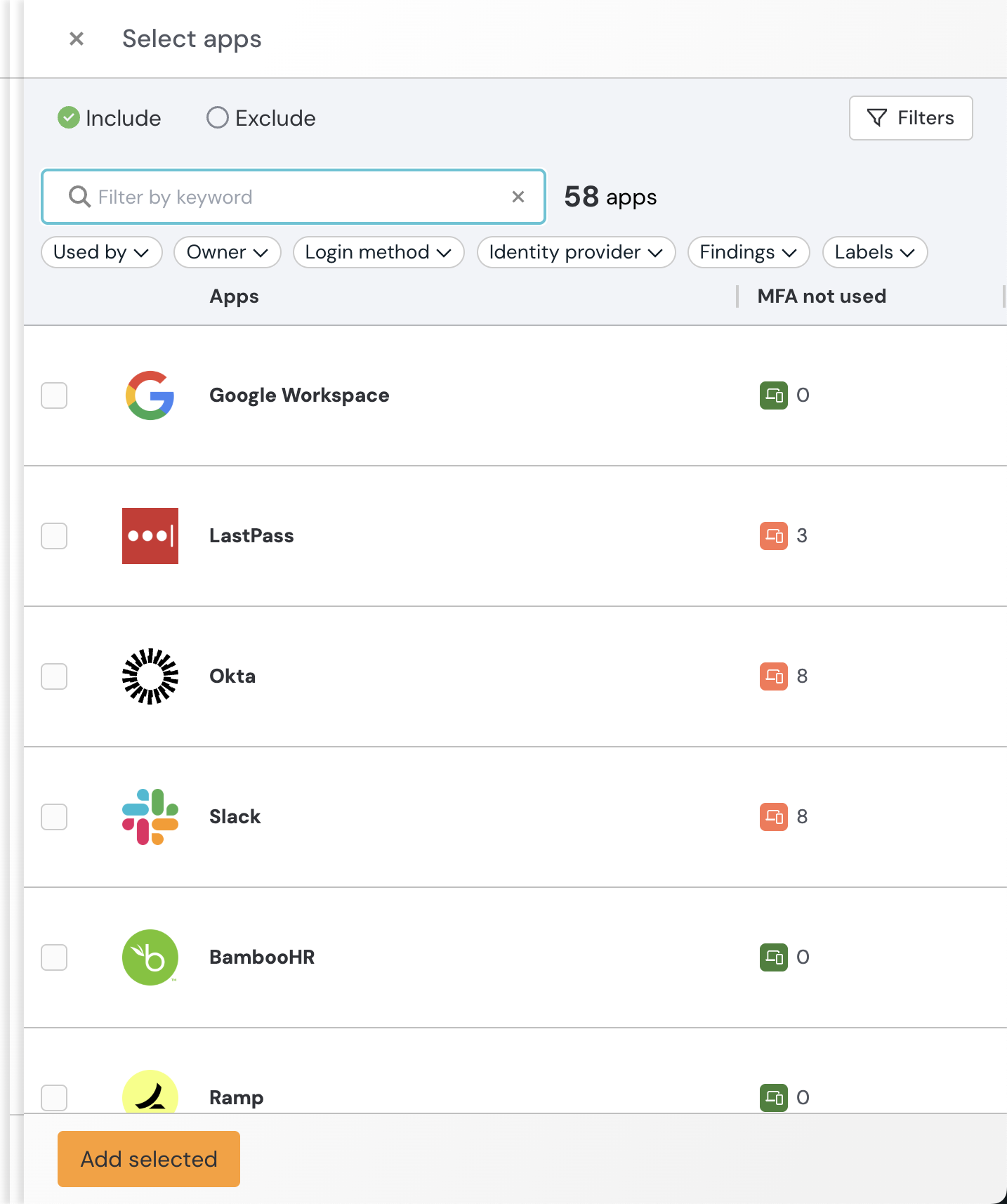
Supported apps
You can see the list of supported apps when configuring the control in the admin console. Check the MFA not used column of the app selection slideout to see where Push has identified missing MFA on accounts in your environment.
Markdown for styling custom message
The custom message field supports link and email syntax using markdown, but no other formatting.
Example markdown:
[Push Security](https://pushsecurity.com)
[Steph](mailto:steph@ctrlaltsecure.com)
You can also use the Push-supplied variable $APP in the custom message field (title and subtext). $APP will be replaced with the name of the application.