Is logging in with Google or Microsoft secure? Yes, with a few caveats. Known as "social logins," they're good for business use for third-party SaaS platforms, not just for personal use. They save time and bring many security benefits in most cases too.
Is logging in with Google or Microsoft secure? Yes, with a few caveats. Known as "social logins," they're good for business use for third-party SaaS platforms, not just for personal use. They save time and bring many security benefits in most cases too.
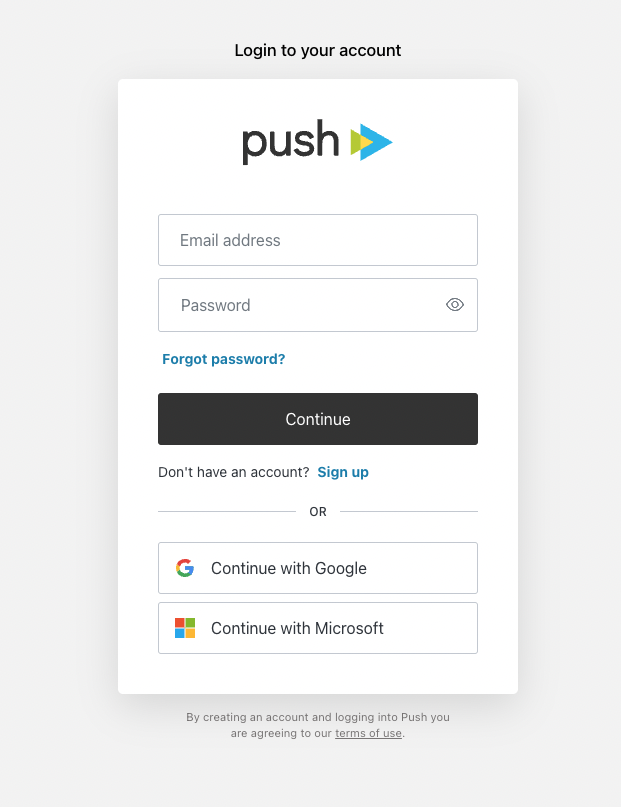
We have all seen the option on websites to login using a variety of different tech giant accounts (“Login with Google, Login with Microsoft”), instead of creating a new account or using username and password. This is known as a social login and, less often, social sign-in or social sign-on.
Normally, this is more associated with personal use than business use, but it’s just as possible for employees to log into a SaaS platform using a business Google Workspace account - but should we be encouraging or discouraging this behavior? We’ll answer that question in this article but, spoiler alert, at Push Security we encourage it in most cases and we’ll explain why in this article.
We've created a quick and dirty video demo of a social login to help explain the concept:
What is a social login?
So what actually happens when you click to login with Google? Aren’t you just giving your Google password to some random website? That’s a security concern many people have but, thankfully, that isn’t the case.
Social logins actually work using OAuth 2.0, which stands for “Open Authorization.” It’s a standard to allow third-party apps to access your data. OAuth is actually for a much broader set of use cases than just social logins, but that’s for another article.
Let’s focus on what happens when you click to sign-in with Google. You’re actually redirected to Google’s own servers and asked to authorize the website to be granted any access to your data that it has requested. In a simple social login case, the website should only be asking for minimal access to view simple details, such as your email address and full name in order to verify your identity.
If this is the case, Google does not even specifically ask you to accept those permissions, it just verifies which Google account you would like to use. If you are already logged in with Google then you won’t even need to enter your password.
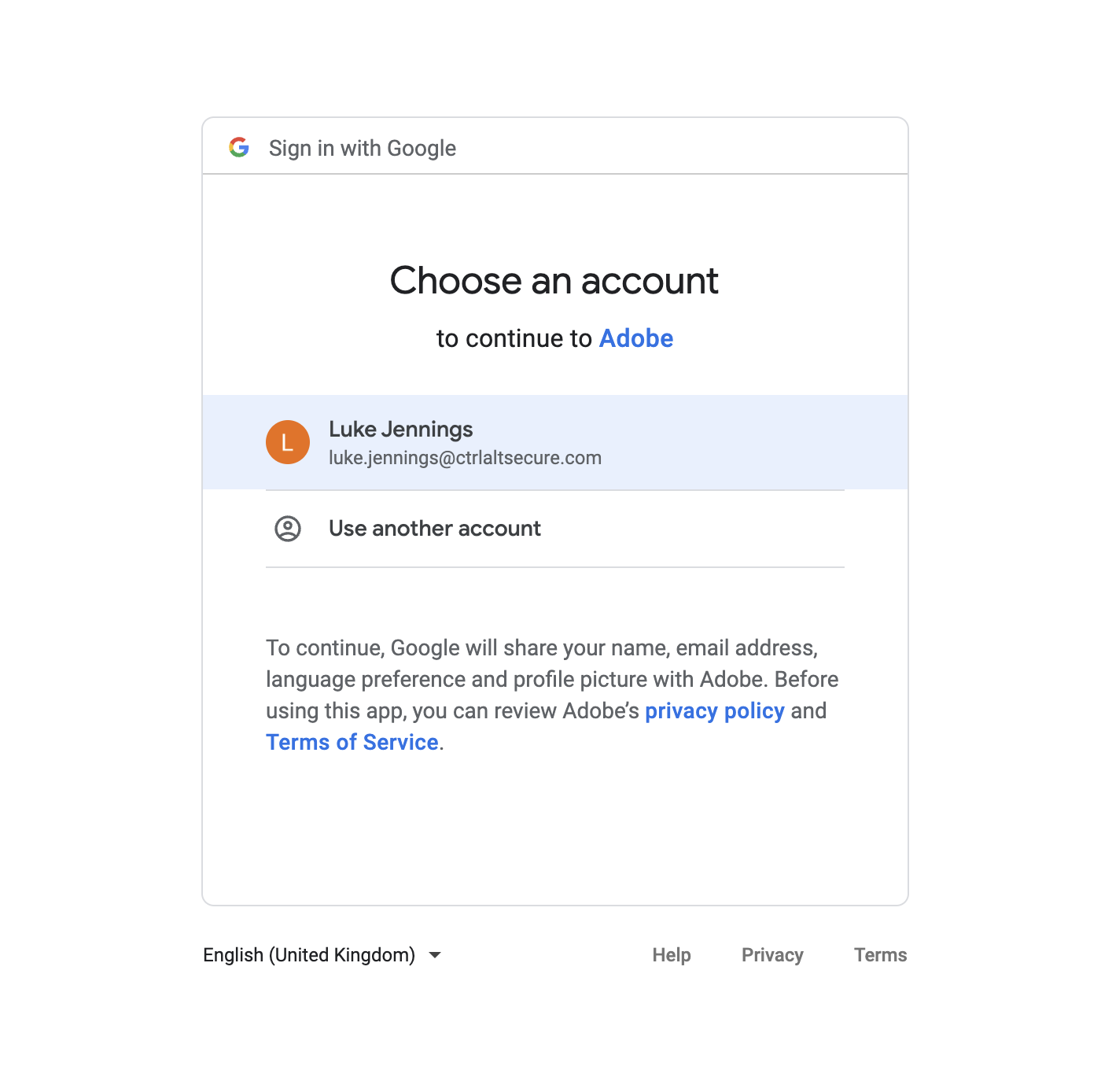
…and that’s it, you’ve just socially logged in to a website using your Google account. You didn’t need to create an account, set a password, use a password manager or even enter your Google password. It was so easy! But is it secure?
Security Benefits
The short answer is - yes, it is secure, and there are actually many security benefits. Let’s consider some of them:
Multi-Factor authentication (MFA) everywhere! - You’ve followed good security practice and enabled MFA for all of your Google accounts, right? Great, well then every other SaaS platform that your employees use social logins just inherited MFA protection for free! Not only does the platform not even need to support MFA on its own (most don’t), but you don't even need to set it up!
Easy password resets - Ok, so one of your employees gets their (commonly shared) password phished. All those SaaS accounts could be immediately compromised and how many password resets now need to be performed? Oh, they use a password manager? Ok, what if their laptop is compromised with malware? You need to assume the password manager is compromised too. That’s still a lot of password resets. On the other hand, if you use social logins for everything you only have one password to change. If you have MFA too, it probably would have been tough for the attacker to make use of that password during the compromise window before the change, too.
Easy offboarding - When an employee leaves the company, it’s not so hard to delete their core business accounts, but it’s much more painful to have a process for removing all old SaaS accounts too. If social logins are well implemented by the SaaS provider then the removal of a Google workspace account automatically means the corresponding SaaS accounts are no longer accessible either.
Visibility - If employees use custom logins for all their SaaS platforms, you’ll have no idea what SaaS platforms are in use (unless you use the Push browser extension ;)). With social logins, you can see exactly which platforms your employees are using across the organization. (https://support.google.com/a/answer/7281227?hl=en#zippy=)
Simplicity - Complexity is often the enemy of security and, let’s face it, getting all your employees to use password managers with different passwords for large numbers of accounts, creating new accounts every time, handling password changes for all of them, etc., is the definition of complexity. On the other hand, social logins are just so simple. You login to Google once, then any other SaaS platform you want to access that supports them you just click “login with Google”, select your account and you’re done. That’s it - simplicity benefits security.
No shared passwords - Let’s face it, it’s difficult to get employees to use password managers for everything and commonly people end up using the same one or two passwords for everything. Then all it takes is for any one platform to be compromised and that account is compromised for any other platforms where the password is shared. Therefore, your security is dependent on the security of the weakest platform you use of many. On the other hand, if you use social logins for everything, there is only ever one strongly protected account, which is much less likely to be compromised.
Our view is that it’s better to have one account that you put all your focus on securing as best as possible than many accounts that individually have a lower level of security.
But why would I want everything in one account, protected with one password?If your Google account is used to access everything then all your eggs are in one basket right? If your Google account is compromised, or even Google themselves are compromised, then everything else you use is compromised too. Pretty concerning, right? This is true and it does remain a risk.
However, if you’re a Google Workspace user then you’re trusting Google with most of your key data anyway - all your email, documents, calendar appointments etc are stored with Google and accessed using Google accounts. Also, if your Google email gets hacked that can generally be used to password reset all your other accounts anyway! Plus, using a password manager could be argued to also be putting all your eggs in one basket too.
We’ll go into some of the potential concerns of using social logins in this next section because there may be some valid use cases where you won’t want to use them.
Security Caveats
Ok, we said at Push Security that we encourage the use of social logins. But we aren’t going to wave our hands and cover up any downsides - as always, there are always some. We consider some of the following to be key drawbacks:
Giving away sensitive data - This article has been entirely focused on social logins, but we said at the start that OAuth was for more than that. When a user logs in using Google, the website can ask for permissions far beyond what is needed for a simple social login. These can be sensitive, such as allowing access to emails, calendars, Google Drive documents etc and the user will be prompted separately to accept or refuse this. In most cases, you’ll probably find websites do not request additional permissions for a simple login/signup but may do if you enable more advanced integrations. However, some websites may just ask for the kitchen sink from the first login. It’s possible your employees may then start giving away sensitive access to third parties without a second thought.
There are also malicious apps created simply to exploit permissions so they can gain access to an employee’s or company’s data by requesting excessive permissions and requesting the employee to opt into them by default. This is called consent phishing and we’ve written up a quick guide here about what the risk is, how it works, and how to handle it.
You can always see what access has been given by your employees to different platforms and review accordingly and you can even configure more sensitive permissions as restricted so your employees can’t accept them on their own. However, this risk remains, whereas it’s not as easy for an employee to inadvertently open up significant data access with a custom login for a website.
Privacy and Anonymity - if you use social logins for everything, then every SaaS platform your employees use will have at least some access to basic personal information for your employees that use them. Google will also probably have more information about what SaaS providers you are using than they would otherwise, too.
Maybe you just wanted to try out a new SaaS service without getting spammed by their sales team for the next 12 months? For that, you might want to go with an anonymous, disposable email address. Whatever the case, social logins will always give away basic personal details at a minimum and there might be times where this isn’t desirable. But for most companies, we’ve found those to be edge cases.
You may not necessarily want the public (or your adversaries) to know what SaaS apps employees are using. If an attacker gained access to your Google or Microsoft account that you were using for social login, they would be able to see the apps that are accessed with social login. On the other hand, if an attacker gets access to your primary core business platforms, this is likely going to be the least of your concerns.
Conclusion
Social logins are good for business use for third-party SaaS platforms, not just for personal use. They save time and bring many security benefits in most cases too. As long as you understand the residual risks that remain and are happy managing those risks, you should consider encouraging your users to use social logins.
