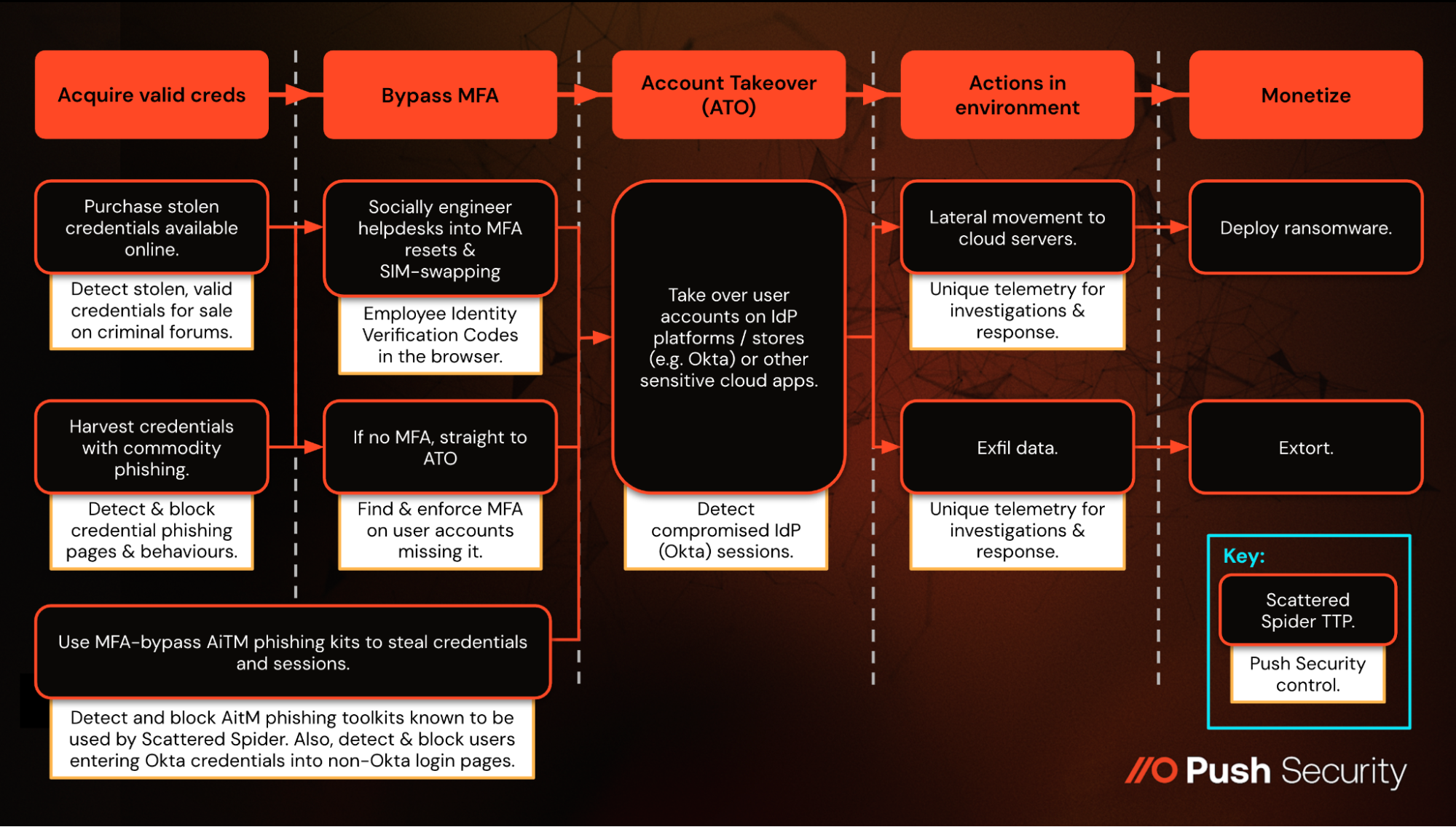
How the notorious Scattered Spider cyber criminal group are evolving their TTPs in 2025 to bypass security controls like MFA and take over accounts on internet applications and services.
How the notorious Scattered Spider cyber criminal group are evolving their TTPs in 2025 to bypass security controls like MFA and take over accounts on internet applications and services.
It's been a busy year for cyber criminals! This article has now been superseded with the rise to infamy of "Scattered Lapsus$ Hunters". The guidance and TTPs in this blog post still apply, but check out our new post for the full picture of Scattered Spider-linked breaches dating back to 2021.
Background: Who are Scattered Spider?
Scattered Spider (also tracked as 0ktapus, Octo Tempest, Scatter Swine, Muddled Libra, and UNC3944) is a native English speaking, financially motivated criminal collective known for high-profile cyber breaches in recent years, including MoneyGram, Transport for London, Caesars, MGM Resorts, Clorox, DoorDash, Twilio, Reddit, Coinbase, MailChimp, Okta, HubSpot, Cloudflare, Activision, Pure Storage, and the ongoing Marks & Spencer, Co-op, and Harrods incidents.
Scattered Spider shares similar characteristics and TTPs with a number of named threat groups such as Lapsus$, Yanluowang, Karakurt, and ShinyHunters (behind the Snowflake attacks in 2024).
With criminal hacker collectives being fluid in nature, Scattered Spider has also been associated with the Snowflake attacks attributed to the ShinyHunters group, which resulted in hundreds of millions of breached records from 9 public victims including AT&T, Ticketmaster, and Santander (with the full impact suggested to be around 165 organizations), monetized through ransom payments, extortion of individual victims, and resale of the data on criminal forums.
Case study: MGM Resorts
One of Scattered Spider’s most notorious and well-documented attacks was that affecting MGM Resorts. Scattered Spider socially engineered MGM Resorts helpdesk personnel bypass MFA and log into accounts for which they had acquired valid login credentials for via credential phishing and historical infostealer compromises. They specifically targeted accounts with Super Administrator privileges within MGM Resorts’ Okta tenant, which they then used to register a second, attacker-controlled IdP via inbound federation, which enabled them to impersonate any user within the Okta tenant. This then enabled them to abuse SSO access to downstream apps and platforms from various accounts, culminating in deployment of ransomware to around 100 ESXi servers and data exfiltration.
The breach resulted in a 36-hour outage, a $100M hit to its Q3 results, one-time cyber consulting fees in the region of $10M, and a class-action lawsuit later settled for $45M.
Caesars was also hit at the same time as MGM Resorts. Less is known about the Caesars attack, except that a ransom of $15M was paid to Scattered Spider in an attempt to prevent stolen data being leaked online.
Case Study: Snowflake
Members of Scattered Spider have been affiliated with ShinyHunters, the group behind the Snowflake breaches in mid-2024. ShinyHunters associates targeted ~165 organizations that were subjected to account takeover attacks using stolen credentials harvested from historical infostealer infections dating back as far as 2020, according to Mandiant’s investigation. In total, 9 public victims were named following the breach, collectively impacting hundreds of millions of people. Snowflake was a watershed moment that signalled the significant opportunity presented by identity attacks on cloud services. It demonstrated how comparatively unsophisticated methods (logging in to user accounts with stolen credentials and dumping the data) can have the same or greater impact as a traditional network or endpoint based cyber attack involving vulnerability exploitation, malware deployment, ransomware, etc.
Arrests haven’t slowed Scattered Spider
In late 2024 following the Transport for London attacks (which resulted in prolonged disruption to key online services underpinning London’s public transport network, theft of 5,000 users bank details, and all 30,000 staff members having to reset their online credentials in person) a series of arrests were made in the UK and USA.
It's worth thinking about Scattered Spider less as a neatly identified group of individuals, but more as a pattern of activity and behaviors. For this reason, it's unlikely that arrests will have a definitive impact — the TTPs exhibited will continue to be used and refined by newcomers.
However, this doesn’t seem to have impacted Scattered Spider’s ability to operate, with the ongoing campaign against UK retail companies including Marks and Spencer, Co-op, and Harrods being strongly linked to Scattered Spider. Beginning on Easter weekend, the Marks and Spencer attack has had the biggest impact so far, resulting in severe disruption to the retailer with agency staff told not to come into work, online shopping services being taken offline, stores running low on products, £300M in lost profits, and almost £1B wiped off the company’s stock market valuation at one stage.
A series of attacks against retailers worldwide soon followed, at an unprecedented rate. Dior, The North Face, Cartier, Victoria’s Secret, Adidas, Coca-Cola, and United Natural Foods were among the retailers to suffer a breach between May-June 2025. More recently, Scattered Spider has targeted U.S. insurance giant Aflac, Philadelphia Insurance Companies, Erie Insurance, Hawaiian Airlines, WestJet, and Qantas.
Scattered Spider TTP analysis
Along with a clear MO (financial gain via data exfiltration and extortion) Scattered Spider has demonstrated a pattern of go-to TTPs over recent years.
Social engineering, help desk scams, and SIM swapping
The public breaches associated with Scattered Spider have predominantly featured social engineering heavy initial access, mainly through help desk scams where the attacker contacts support personnel specifically to bypass MFA for accounts where they have acquired valid credentials via credential phishing or infostealers, but cannot access the account due the additional layer of protection. They have similarly used SIM swapping, smishing and MFA fatigue/push bombing to achieve account takeover.
Learn more about how Scattered Spider conducts help desk attacks in our recent blog post or by checking out our on-demand webinar — available to stream now.
Impersonating and targeting SaaS services
Scattered Spider have also been known to target SaaS applications and cloud services — both as part of their phishing strategies by impersonating app providers, as well as in their lateral movement and exploitation when an identity has been compromised. This has included applications such as vCenter, CyberArk, SalesForce, Azure, CrowdStrike, AWS, and GCP.
When conducting phishing campaigns, they’ve created custom domains for their phishing sites based on the organizations they are targeting:
Accenture, Aflac, Allstate, Ally Bank, Amica, Apple, AT&T, Athene, Audemars Piguet, Ballet Crypto, BCB Group, Bell, Bitcoin Suisse, Blockdaemon, Blockstream, Charter Communications, Chik-fil-A, Cincinnati Financial, Comcast Corporation, Core Scientific, Costco, Credit Karma, DoorDash, Fireblocks, Forbes, Gemini, Grayscale, H&R Block, Hanover Insurance, Harrow Health, Iliad, Instacart, Jackson Hewitt, Kemper, Louis Vuitton, Luno, Marsh, Mercury, Morningstar, Mutual of Omaha, Nansen, NGRAVE, New York Digital Investment Group, New York Life Insurance, News Corporation, Nike, Orange, P.F. Chang’s, Paxos, PNC Bank, Revolut, RiteAid, 7-Eleven, Singtel, Stargate Industries, Synchrony Bank, Synovus, T-Mobile, Telstra, TIAA, Transamerica, Twitter/X, UScellular, Verizon, Vodafone, WINDTRE, and Xapo Bank.
And they have impersonated many software brands — either as targets themselves, or as convincing third-parties to lure their targets to interact with.
ActiveCampaign, Ada CX, Alchemy, Asurion, Bandwith, Bird CRM, Campaign Monitor, Concentrix, Constant Contact, Corporate Tools, CTS, eClerx, Expedia Group, FalconX, FICO, Five9, Foundever, Freshworks, Genesis Trading, Givebutter, GoDaddy, HubSpot, Incode, Intercom, iQor, Iterable, Jumio, Klaviyo, LinkedIn, Mixpanel, Nuance Communications, Onfido, OnSolve, Podium, Pure Storage, Ripple, Roblox, Salesforce, Shipbob, Sinch, Socure, SPOC, Squarespace, TaskUs, TriVista, Twilio, Ulta Beauty, Upland Software, Wix, Workday, Ziff Davis, and 247[.]ai.
(Shout out to the excellent analysis by the folks at Silent Push).
Targeting identity providers to abuse OAuth and SSO
A key part of this approach is abusing OAuth by targeting identity providers (IdPs) such as Okta and Microsoft Entra. By compromising IdP accounts with administrator privileges, Scattered Spider has leveraged techniques such as inbound federation to gain unrestricted access to the identities within the target IdP tenant (the equivalent of a full Active Directory compromise on-premise).
Encryption of cloud servers and data theft for extortion
When executing the final stages of an attack, Scattered Spider first exfiltrates data through a variety of methods, even using SaaS services such as DropBox and FiveTran to extract copies of high-value service databases, such as SalesForce and ZenDesk, using API connectors.
In a typical "double-extortion" style, they then deploy ransomware by targeting cloud server environments such as VMWare ESXi (specifically to avoid security tools by targeting the hypervisor layer). Scattered Spider have been known to act as affiliates for various ransomware operations, including RansomHub, Qilin, and DragonForce.
Scattered Spider TTP evolution in 2025
In 2025, security researchers have observed a significant increase in Scattered Spider phishing activity, particularly in the form of MFA-bypassing Attacker-in-the-Middle (AiTM) phishing pages.

Along with this shift, a number of TTPs have been observed relating to detection evasion measures implemented on these phishing pages.
Rapid phishing domain rotation
According to researchers Scattered Spider have been observed using phishing pages hosted on short-lived domains that included specific keywords such as “okta,” “sso,” “help,” “hr,” “corp,” “my,” “internal,” “sso,” or “vpn,”, which were quickly operationalized within minutes of registering a domain. After a couple of hours, the domain would often be taken down by the registrar. However, as we’ve discussed in various blog posts, this is to be expected. Domains are highly disposable by nature and attackers plan to get through them in large numbers. They don’t need their phishing pages to live indefinitely — just as long as it takes for someone to be successfully phished.
You would expect these kinds of untrusted links to be flagged by enterprise security tools, but through clever use of obfuscation methods such as using legitimate apps to host the phishing link, using an initially benign link to a document or other source with the malicious link, or avoiding email as the delivery vector altogether, network and email-based controls are being routinely bypassed.
Using custom subdomains that allow public registrations
Scattered Spider have been observed registering their malicious domains on publicly rentable subdomains such as it[.]com. This limits the information that can be gathered about the domain (for example, preventing WHOIS information from being accessed)
This is incredibly deceptive to the user and will fool many people glancing at the link. It doesn’t look as obviously suspicious as the typical .xyz or .biz, and has the feel of a legitimate domain. As these convincing rentable subdomains start to appear online more frequently, it becomes easier for attackers to pick up convincing domain names with fewer obvious deviations from the real one, without needing to resort to special characters or other tactics that might be spotted.
This is strikingly similar to an attack we investigated recently, where an attacker was using the us[.]com domain to impersonate Onfido, the digital identity platform. These malicious links were actually distributed via malicious advertising on Google, which is an increasingly popular tactic to evade email and network detection controls for phishing links and pages.

This comparison is also interesting when you consider…
Using commercial AiTM toolkits like Evilginx to bypass MFA and evade detection
Scattered Spider have been observed frequently using Evilginx as their phishing kit of choice. Evilginx is a great choice for attackers looking to target non-standard web apps because it is capable of emulating a range of domains — it’s designed to be flexible and work for any page without generating a load of custom JavaScript that might stand out to security tools/analysts. See an example of Evilginx being used to phish a user below.
By default, Evilginx redirects any site visitor not following the correct url path or supplying the correct parameters to the YouTube video for Rick Astley’s “Never Gonna Give You Up” (aka “Rickrolling”). This behavior has been observed on Scattered Spider phishing sites. Interestingly, we also observed this in the Onfido malvertising example above, while members of the infosec community are increasingly seeing phishing attacks with this behavior. (This example also features use of consent phishing to prevent analysis of the malicious link by hiding it behind a legit Microsoft app consent page, another detection evasion tactic).
Pre-populating victim information using targeted phishing links
A general trend that we’re seeing in the wild, also utilized by Scattered Spider, is phishing attacks becoming increasingly targeted. This includes using redirects to legitimate apps unless specific parameters are supplied, only loading malicious content for specific usernames (and redirecting to benign sites otherwise) implementing the use of one-time phishing links (essentially magic links that work once for the victim, preventing security teams or tools from accessing the page to analyse it later), and pre-populating the victim information on the page to make it feel more genuine (you would expect a website you have visited and logged into before to pre-populate some of your details, like your username/email).
See an example of this (along with a few of the detection evasion techniques we've mentioned) below.
Varying login pages to evade cloned page detections
Attackers are routinely using a combination of visual and DOM-based obfuscation techniques to create convincing phishing pages that are different enough from the real page being impersonated so that detections based on cloned pages do not fire.
While Okta accounts remain a key target for Scattered Spider, they are using a range of customized landing pages to target Okta accounts for various organizations at URLs like:
corp-hubspot[.]com – HubSpot
morningstar-okta[.]com – Morningstar
pure-okta[.]com – Pure Storage
signin-nydig[.]com – New York Digital Investment Group
sso-instacart[.]com – Instacart
sts-vodafone[.]com – Vodafone

Defend your organization from Scattered Spider
Scattered Spider have proven to be a highly creative and adaptable threat group, using a range of identity-centric TTPs and evolving (or rather, adding to) their repertoire over time.
Although Scattered Spider have a number of telltale actions and behaviors, like targeting and leveraging SaaS services, utilizing AiTM phishing kits like Evilginx to target IdP accounts like Okta, and deploying ransomware to cloud servers, they are able to flex their approach to take down their targets.
Scattered Spider’s behavior demonstrates that they are extremely cloud-conscious (as many modern threat actors are) and are leveraging modern TTPs designed to evade traditional security controls and exploit blind-spots in enterprise security visibility. For example, by constantly rotating their phishing domains and pages, Scattered Spider (and many threat actors like them) are routinely evading common phishing detection controls, taking advantage of the limitations of blocklist-driven approaches to phishing detection.
Aligning Push Security’s capabilities against Scattered Spider’s TTPs
Push provides a multi-layered set of detections and controls for defending against the TTPs known to be used by Scattered Spider.
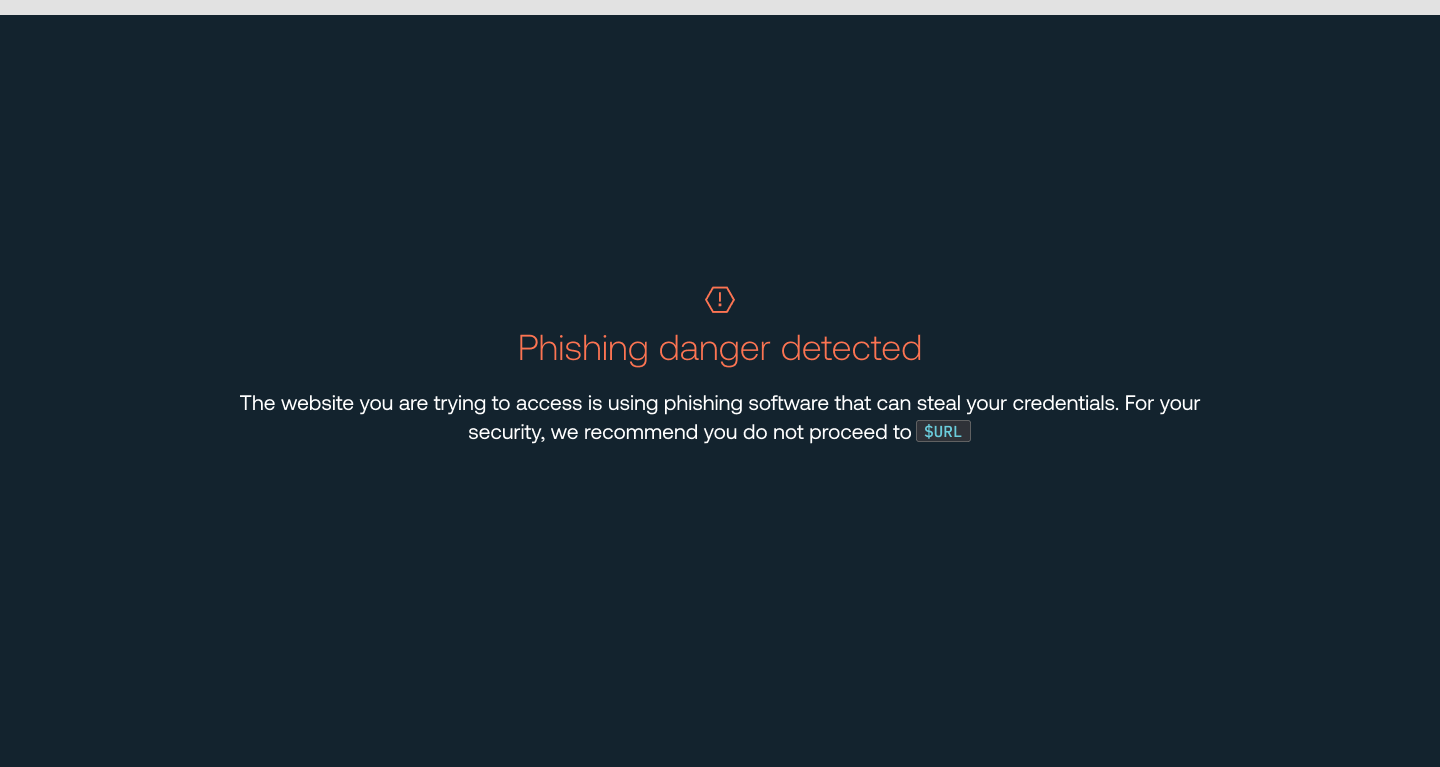
Detect and block AiTM phishing toolkits
The Push browser agent will detect when employees visit websites running MFA-bypassing phishing toolkits such as Evilginx.
To detect modern, sophisticated phishing kits like those used by Scattered Spider, organizations need to be able to detect and block phishing pages in real-time. Push’s browser-based approach intercepts phishing attacks as they happen — in employee browsers. Being in the browser delivers a lot of advantages when it comes to detecting and intercepting phishing attacks. You see the live webpage that the user sees, as they see it, meaning you have much better visibility of malicious elements running on the page. It also means that you can implement real-time controls that kick in when a malicious element is detected.
The Push browser agent analyzes the behavioral attributes of phishing tools, e.g. “something the toolkit does” vs. just a static signature like a URL path or domain.
Based on your configuration, Push can then warn or block employees from accessing those phishing sites using a customisable blocking page or banner.
Detect cloned login pages
The Push browser agent will detect when employees visit websites using cloned login screens to steal credentials - i.e. a cloned Okta login page.
Push does this by fingerprinting the page structure and resources of your legitimate login pages and monitoring for pages that are very similar.
Push will then emit a webhook event when it detects that an employee has visited a page that appears to be a clone of a legitimate login page.
Pin your sensitive passwords to specific sites
The Push browser agent will detect when employees attempt to enter their IdP password (such as Okta) into webpages that do not belong to that IdP.
When observing logins, the Push browser agent generates a salted partial hash of the user’s password, known as a fingerprint. This fingerprint is then stored locally in the browser to allow Push to perform password comparisons. You can read more about how the extension securely observes passwords in this help article.
To detect phishing attempts against Okta (and other identity providers), the Push browser agent compares the observed Okta password fingerprint to the known Okta fingerprint that already exists in local storage.
If an employee has entered their valid Okta password on a webpage that does not belong to Okta — i.e. a phishing page — Push will enforce the SSO password protection settings set by an administrator (block or warn). This serves as a second layer of defense when used in conjunction with AiTM and cloned login page detections.

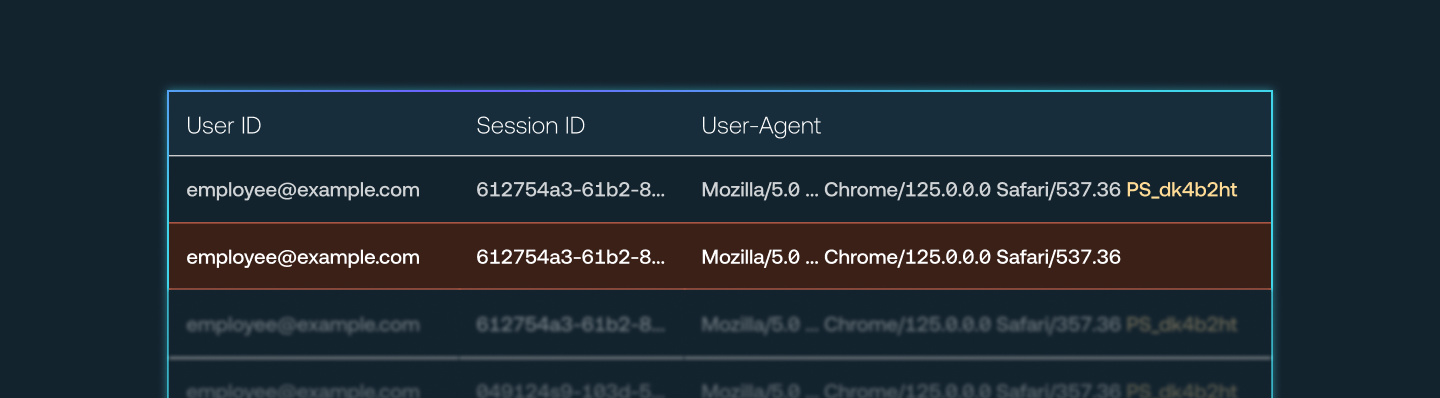
Detect compromised sessions
By correlating Push telemetry with Okta logs, Push can detect compromised Okta sessions originating from outside employees’ supported browsers.
Using the Push browser agent, you can inject a unique marker into the User Agent string of Okta sessions that occur in browsers enrolled in Push.
By then comparing against Okta logs, you can identify sessions that both have the Push marker and those that lack the marker, the latter indicating the session is being used from a machine without the Push extension and therefore the session token may have been stolen.
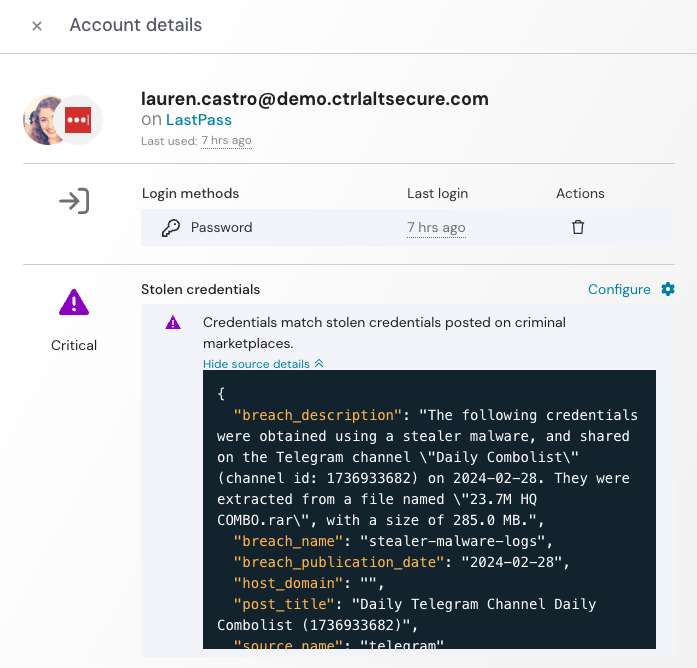
Detect when employee credentials are stolen
Push will detect when valid credentials appear for sale on criminal forums.
The Push platform detects valid, stolen credentials on criminal forums by ingesting threat intelligence data and then verifying which credentials flagged by TI sources are still being used by employees.
When suspected stolen credentials for the corporate domain are present, Push hashes and salts the passwords and then sends those fingerprints to the relevant browser agents for comparison. If the stolen credential fingerprint matches a known credential fingerprint observed to be in use by the Push browser agent, the platform returns a validated true positive alert.
You can choose to receive alerts for this detection via webhook, ChatOps notification, or in the Push admin console.
Map login methods and remove ghost logins
Push maps all the identities used by employees to access workforce apps, including local, non-Okta identities. This data can be used to migrate more apps and accounts to Okta SSO and reduce the overall identity attack surface.
The Push browser agent observes employees using their corporate identities to access work applications. Push customers gain accurate visibility across all Okta and non-Okta identities, the employees that are using them, the apps they are accessing and the authentication methods being used.
Armed with this data, security teams can get more workforce apps and accounts behind SSO to reduce the overall identity attack surface, while removing any ghost logins that enable attackers to circumvent MFA by logging in directly to the app/page.

Verify help desk caller identities with in-browser verification codes
To help combat help desk scams, we recently released Employee Identity Verification Codes — a simple, browser-based identity check that gives your help desk a reliable way to confirm they’re talking to someone from your organization.
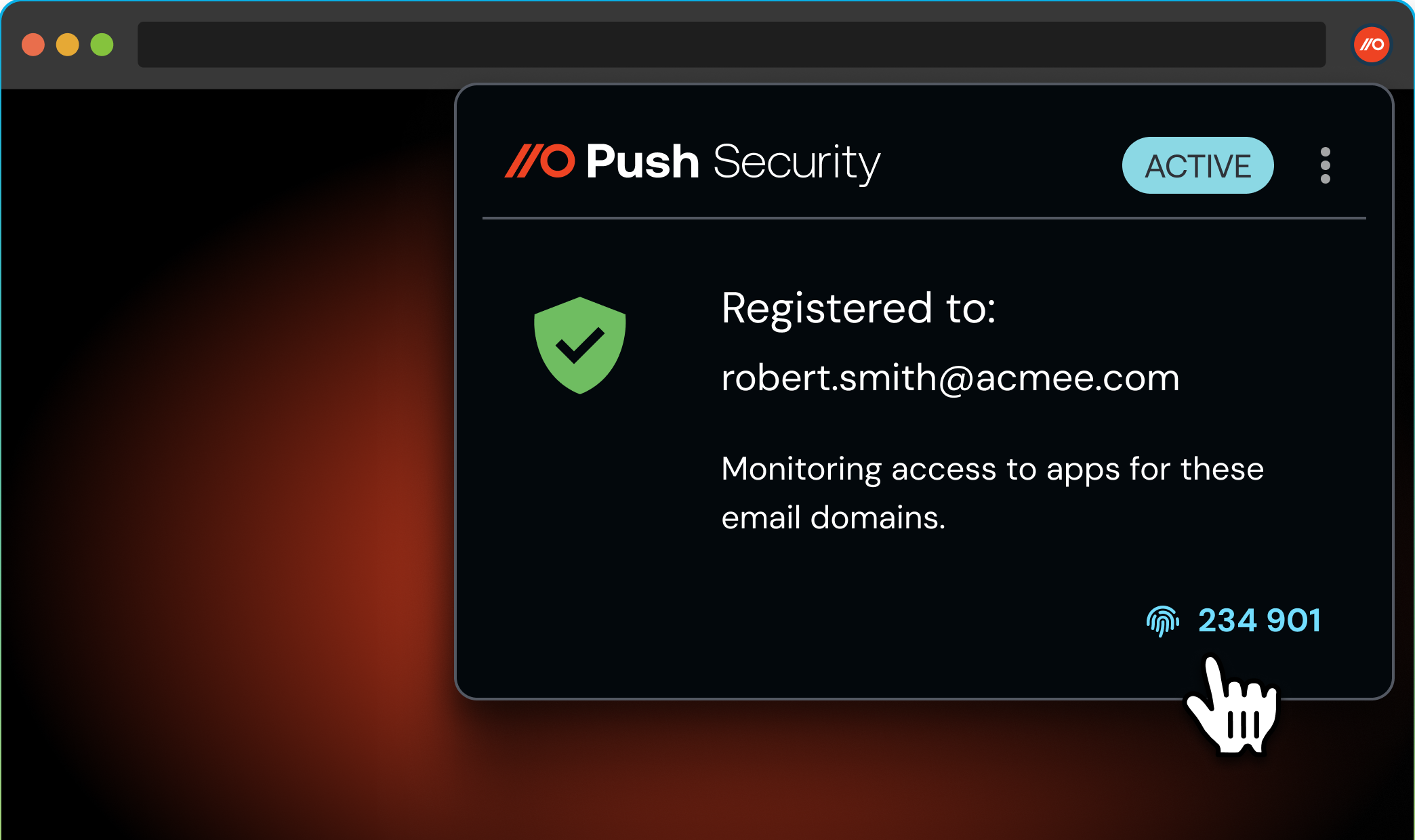
It enables legitimate help desk callers to quickly verify that they’re in possession of their primary device (i.e. laptop) by relaying a rotating 6-digit verification code in their browser via the Push extension. This is a great way to securely confirm caller identity and sniff out fraudulent callers, and can be used as part of a phishing-resistant help desk process.
You can use Employee Verification Codes as a free tool by installing the Push browser extension. Simply sign up for a trial account and you can deploy the extension organization-wide to make use of this feature. While you’re at it, you can trial Push’s full features for up to 10 users for free.
Learn more
It doesn’t stop there — Push provides comprehensive identity attack detection and response capabilities against techniques like credential stuffing, password spraying and session hijacking using stolen session tokens. You can also use Push to find and fix identity vulnerabilities across every app that your employees use like: ghost logins; SSO coverage gaps; MFA gaps; weak, breached and reused passwords; risky OAuth integrations; and more.
If you want to learn more about how Push helps you to detect and defeat common identity attack techniques, book some time with one of our team for a live demo.


