Easier management of app banners, learn which password managers employees use, and more
Easier management of app banners, learn which password managers employees use, and more
What's new this month:
Easier management of app banners at scale
Identify where unapproved password managers are in use
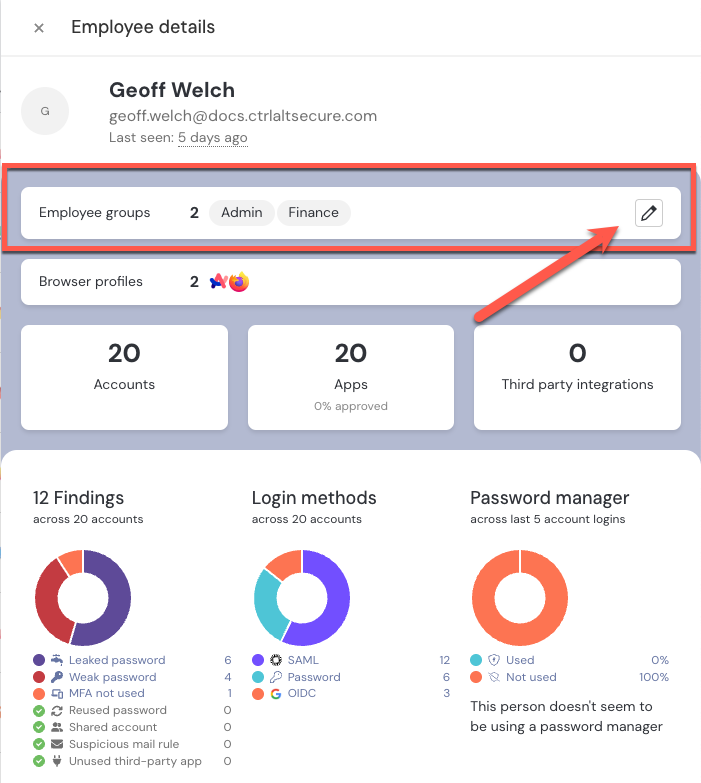
Organize employees into groups
Easier management of app banners at scale
You can now set app banners based on nuanced criteria such as employee groups, approval status, custom labels, and more using our rules feature.
With rules, you can do powerful things like:
Block a compromised app while you investigate.
Block all unapproved apps.
Restrict app usage for specific employee groups while allowing it for others.
Test new banner modes for a small group before deploying more widely.
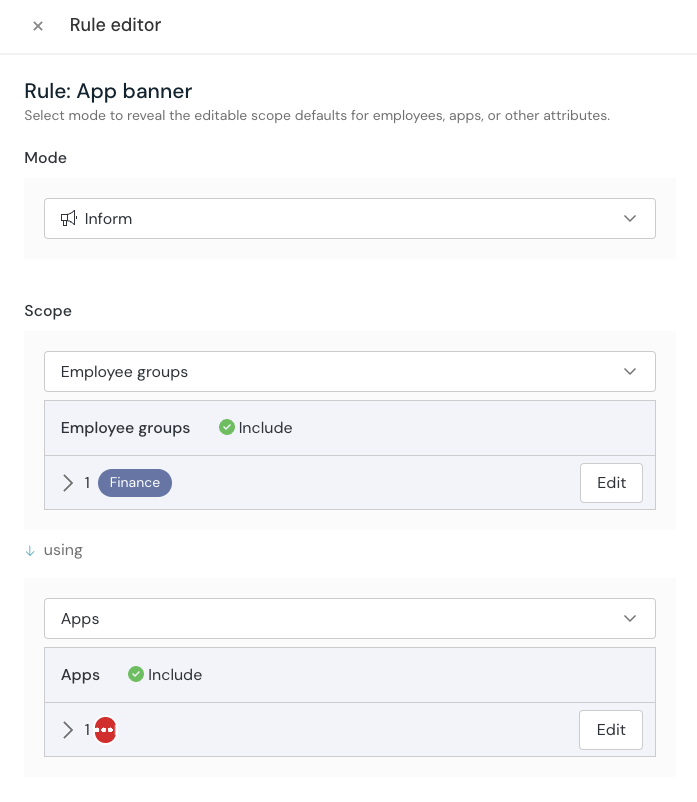
If you already use app banners, you don’t need to do anything — we’ve already moved over your configurations to the new rules model.
Identify where unapproved password managers are in use
Ensure employees are storing corporate credentials only in approved password managers with our new password manager identification feature.
The Push browser agent can now fingerprint commonly used password managers to identify which ones are being used across your environment. With the rise of infostealer malware, many security teams are defending against scenarios where users’ personal password managers get compromised, allowing attackers to pivot to corporate environments and assets.
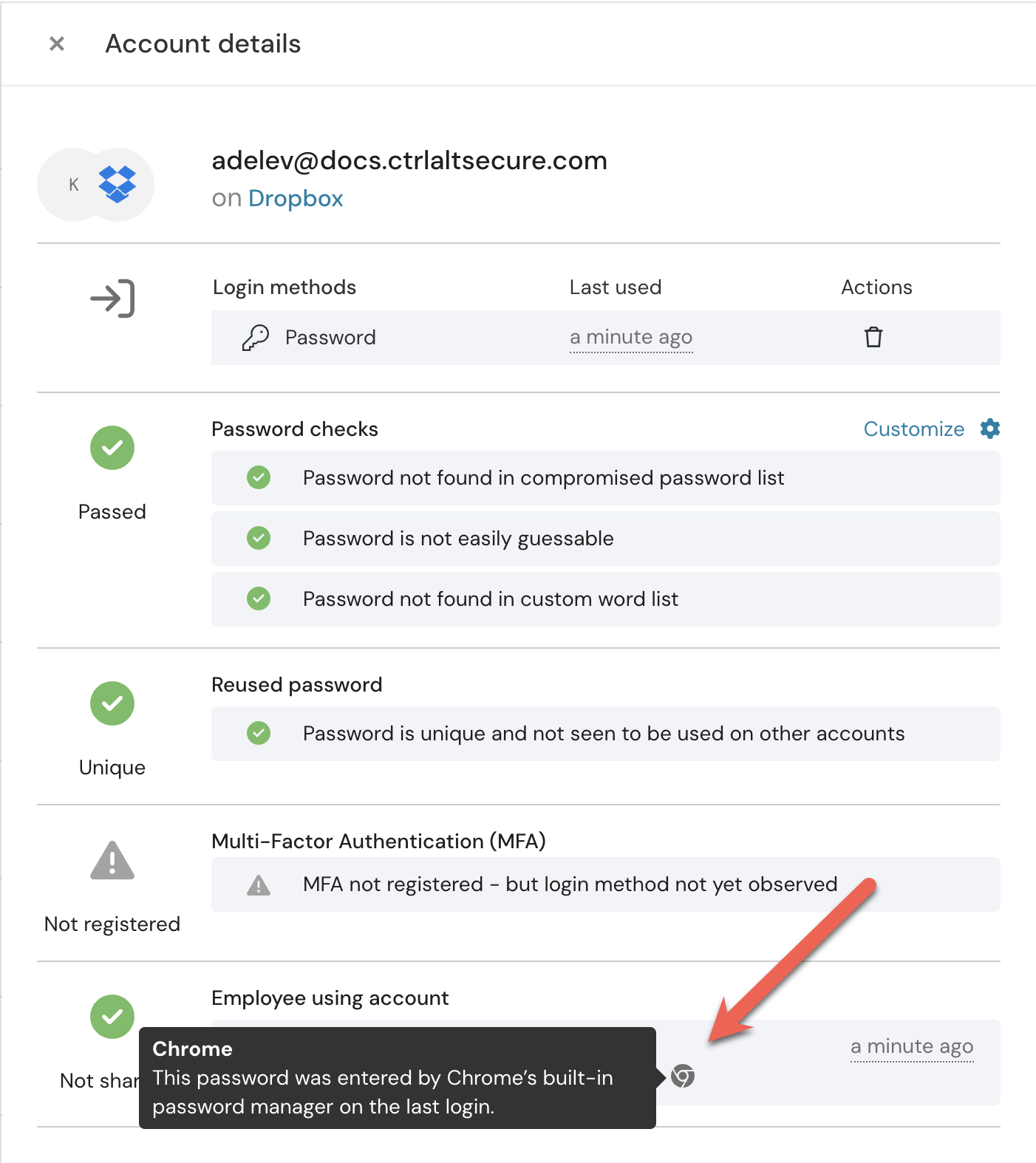
Now you can use Push to know exactly where corporate creds are stored and address unauthorized usage.
Organize employees into groups
You can now add group assignments to employee records in Push and then filter employees, apps, and accounts by group information to give you better context on your identity attack surface.
Groups can be synced in via the Push REST API from your identity provider, or added manually.
Then use groups to drive other Push features, like rules for app banners, mentioned above.