Add app banners to custom URLs, self-service SAML, and more
Add app banners to custom URLs, self-service SAML, and more
What's new this month:
Add app banners to custom URLs
Self-service SAML for the Push platform
Support for Island enterprise browser
Landing page browser enrollment option
Improved filters for apps, accounts, and more
Add app banners to custom URLs
You can now add app banners to a custom-defined URL or URL pattern. Previously, app banners displayed only on login and signup pages for configured apps. With this update, you can put them on any page you like.
That means you can:
Remind employees not to store credentials or sensitive information on internal wikis.
Require acknowledgement of your security policies when using high-value GitHub repos.
Ask employees not to share sensitive information when using GenAI tools during an unauthenticated session.
Or anything else you can think of!
Self-service SAML for the Push admin console
It’s now easier to set up SAML for the Push admin console so your Push admins can log in using your SSO provider, such as Okta or Microsoft Entra ID. Once you’ve created the Push app in your identity provider, you can manage admin access via your IdP.
You can set up SAML yourself from the admin console by going to the Settings page and following the steps in the setup wizard.
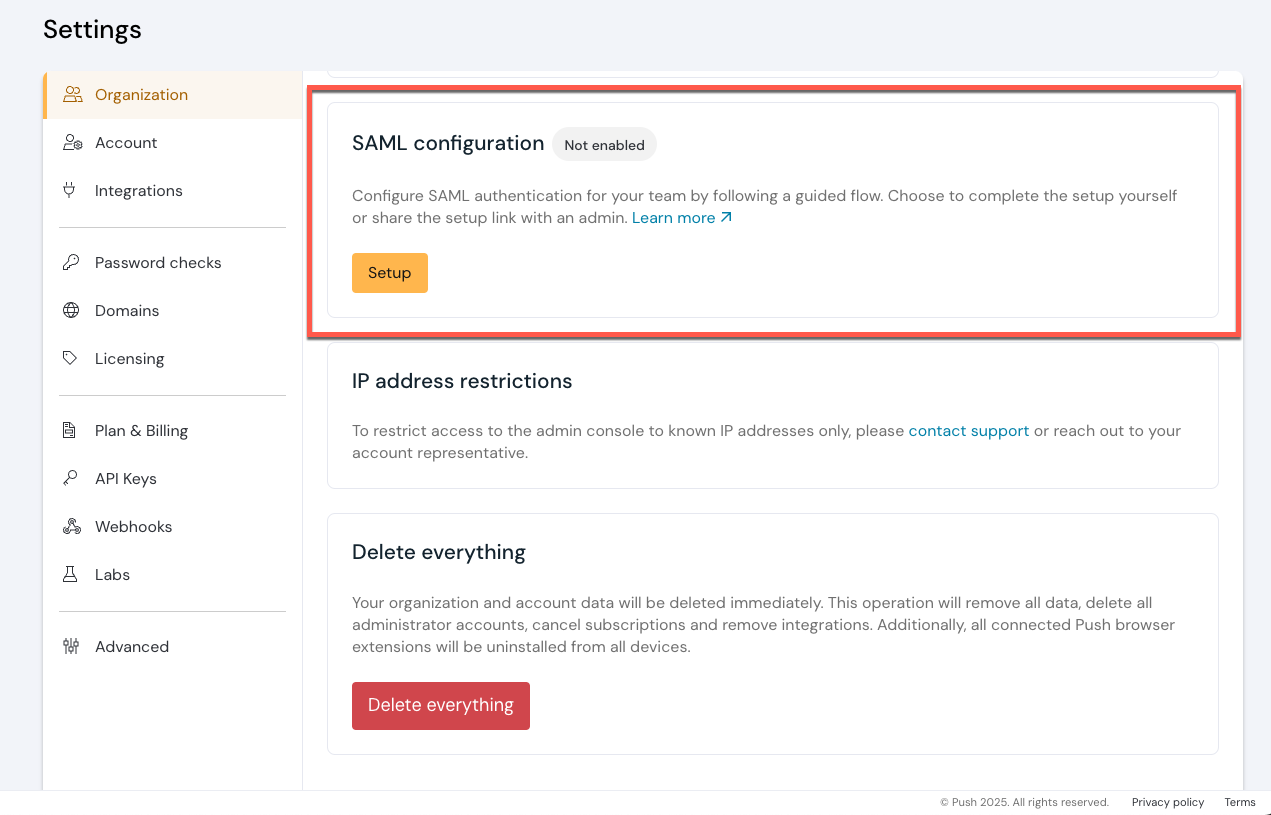
SAML for the Push platform is available at no additional cost.
Push now supports Island enterprise browser
You can now install the Push browser agent on Island, adding a powerful, complementary set of identity security controls to the enterprise browser.
With Island, you can deploy and activate the Push agent seamlessly without any end-user interaction.
Push already provides managed deployment support for other major browsers, including Chrome, Edge, Firefox, Brave, Safari, and Arc.
New landing page browser enrollment option
As an alternative to Push’s email self-enrollment option for end-users, you can now invite employees to self-enroll and install the Push browser extension themselves by directing them to a landing page.
Once employees visit the page, they’ll be prompted to verify their identity via OIDC login using your identity provider. Once confirmed, they’ll be prompted to install the Push extension and enrolled in Push.
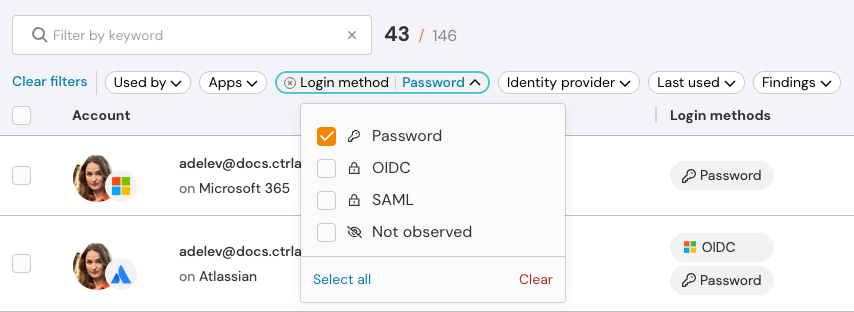
Improved filters for apps, accounts, and more
We’ve improved the visibility and function of filters on pages in the Push admin console that help you explore and manage employees, apps, and accounts. You can also pin the filters you use the most and Push will remember your selection.
You’ll find the new filters under the keyword search on all the data tables in Push, including the Employees, Apps, Accounts, and OAuth apps pages. Combine multiple filters to pinpoint useful data trends, such as:
Which accounts are accessing SAML apps using passwords.
Which accounts are using verified stolen credentials.
Which employees do not have the Push browser extension.
And many more.