We recently detected and blocked Push users from interacting with a malicious Attacker-in-the-Middle (AitM) phishing site using the phishing kit ‘Evilginx’ targeting Onfido, the digital identity platform. Here’s what we found.
We recently detected and blocked Push users from interacting with a malicious Attacker-in-the-Middle (AitM) phishing site using the phishing kit ‘Evilginx’ targeting Onfido, the digital identity platform. Here’s what we found.
What happened
On April 11th our browser-based phishing detection controls were triggered for a user with the Push extension installed.
The user had visited the url dashboard[.]onfido[.].us[.]com after entering a Google search for ‘onfido’, a site they had previously accessed for work and had an account on. A convincing looking Google ad duped the user into clicking the fake link.
Although the page was not the official login page for Onfido, it appeared legitimate enough at first glance to trick the user.
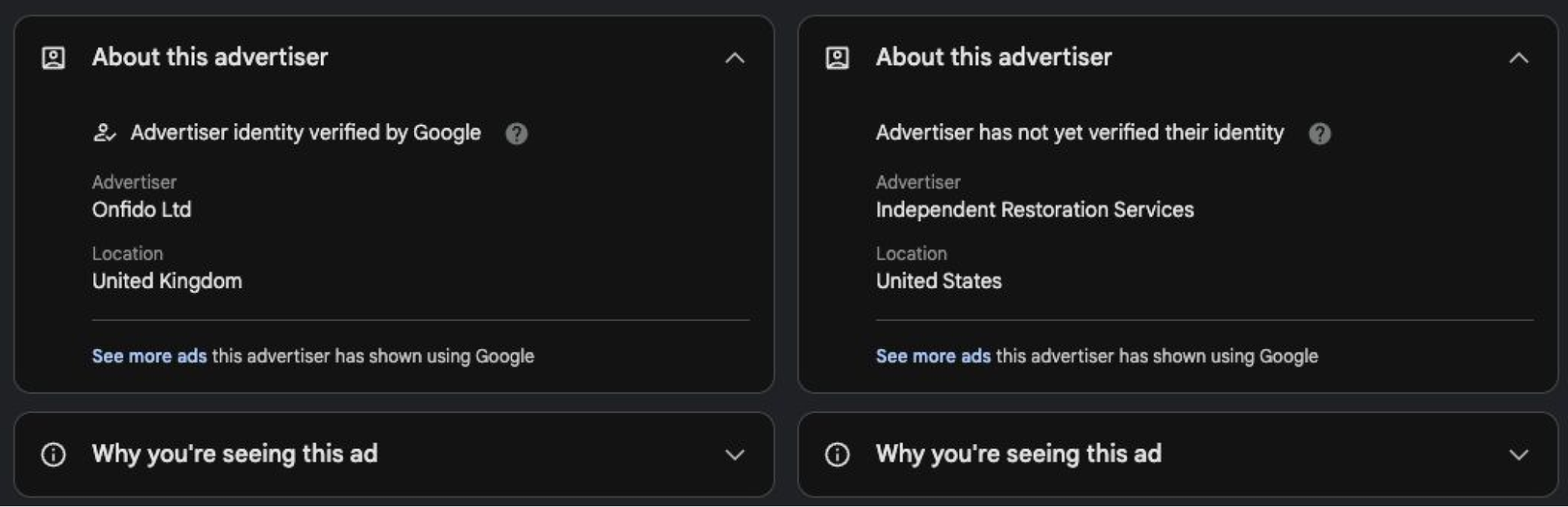
After clicking the link, the user was blocked from interacting with the malicious page running Evilginx by Push. We then took action to identify other Onfido users within the Push customer base and notify them accordingly of the campaign.
There are a few interesting elements worth exploring. Let’s dive in.
Why Onfido?
Onfido is an interesting choice. It’s not your typical phishing target, which points to an interesting trend we’ve observed where attackers are diversifying their phishing targets.
There are two main reasons for this:
People are becoming increasingly suspicious of phishing attacks targeting core apps such as Microsoft, Google, Okta, etc. and are much more likely to spot real vs fake pages.
Because highly targeted apps like IdPs and enterprise cloud platforms are becoming increasingly hardened from an identity perspective, attackers have a lower chance of success relative to accounts on the long tail of internet apps used by an organization — many of which simply cannot be securely configured in the same way (e.g. no passkey/WebAuthn support, limited admin controls to discover and remediate identity security gaps, etc.).
Onfido is also an interesting example in that it definitely contains valuable data that attackers can take advantage of. As a digital identity solution, it presents a significant risk from both a personal and company perspective if compromised, with plenty of PII that can be leveraged to extort a victim — and clear bad press (and possible regulator scrutiny) if the data is leaked!
Why Google ads?
The attack is a form of malvertising where attackers distribute malicious links via ads — in this case, via Google. This is just one example of the many non-email phishing channels that attackers have at their disposal today.
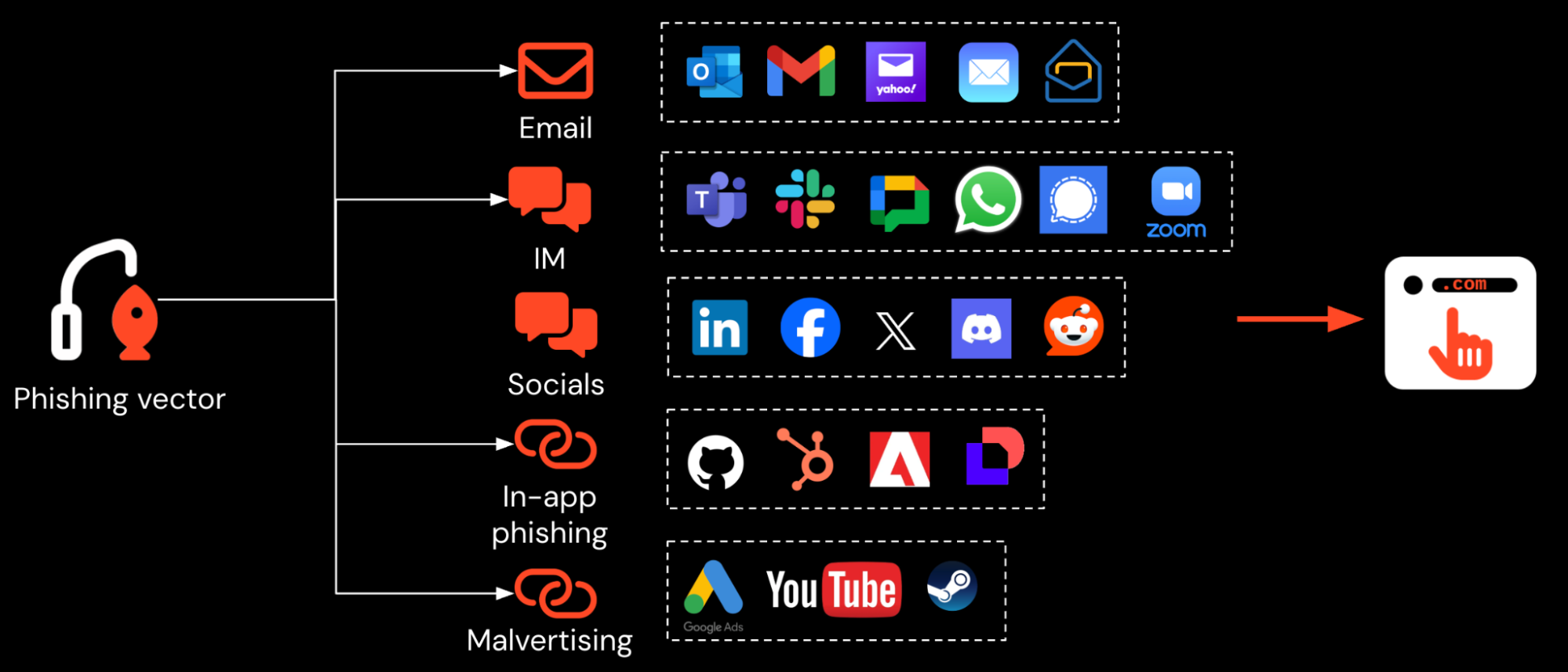
The use of malvertising has a couple of notable advantages here. Namely, because Google ads do not use the same reputation-based checks as an email security provider does, the attacker can use freshly created domains to conduct the attack. Usually, attackers would aim to take over existing domains with a reputation already built up, or spend 6-12 months bedding in their domains so that they pass mail filters.
This is one of the reasons that phishing attacks that bypass email like malvertising are so appealing. Many organizations rely exclusively on phishing controls deployed at the email level. But these are sidestepped entirely by attacks taking place over alternative channels.
But in this case, the domain was registered only shortly before being used. We detected it only a few hours after it had been registered — and it’s already been taken down since (no doubt to be replaced with the next one). This means it’s easy for attackers to spin up these malvertising campaigns at will, without any real forward planning.
In fact, malvertising doesn’t require much effort on the attacker’s part whatsoever. As a watering hole, you put the link up and wait for the clicks to roll in. Unfortunately, many people Google search for sites that they frequently use rather than accessing via bookmark, opening them up to these kinds of malvertising attacks.
No frills
Unlike many of the other campaigns using MFA-bypass phishing kits we’ve seen in the wild, the attacker put very little effort into obfuscating the malicious page. We’ve seen some using things like Cloudflare Turnstile, CAPTCHA, or even Consent Phishing for OIDC scopes to break sandbox detections and prevent security tools from reaching the malicious content to analyze it.
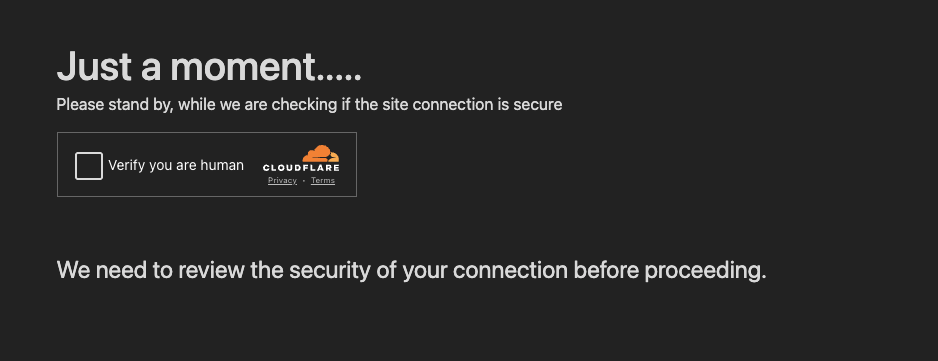
That said, there was evidence to suggest that the domain required a specific URL path — namely, the page must be accessed via Google ads to load. When the page was accessed without the correct parameters set, we were forwarded to a nonexistent page within the legitimate onfido.com domain, resulting in a 404 error.
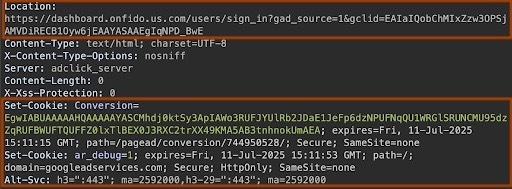
What’s interesting about the domain?
One of the things that really stood out to us was the hosting domain — us.com. Unlike the official government TLD .us, us.com is designed to look and feel legit but does not require any US affiliation or evidence of a US presence. This isn’t a TLD, it’s just a domain selling subdomains within their domain. This means there’s no WHOIS information available on the domains.

This is incredibly deceptive to the user and will fool many people glancing at the link. It doesn’t look as obviously suspicious as your .xyz or .biz and has the feel of a legitimate domain. It’s also incredibly cheap to pick up .us.com domains right now.
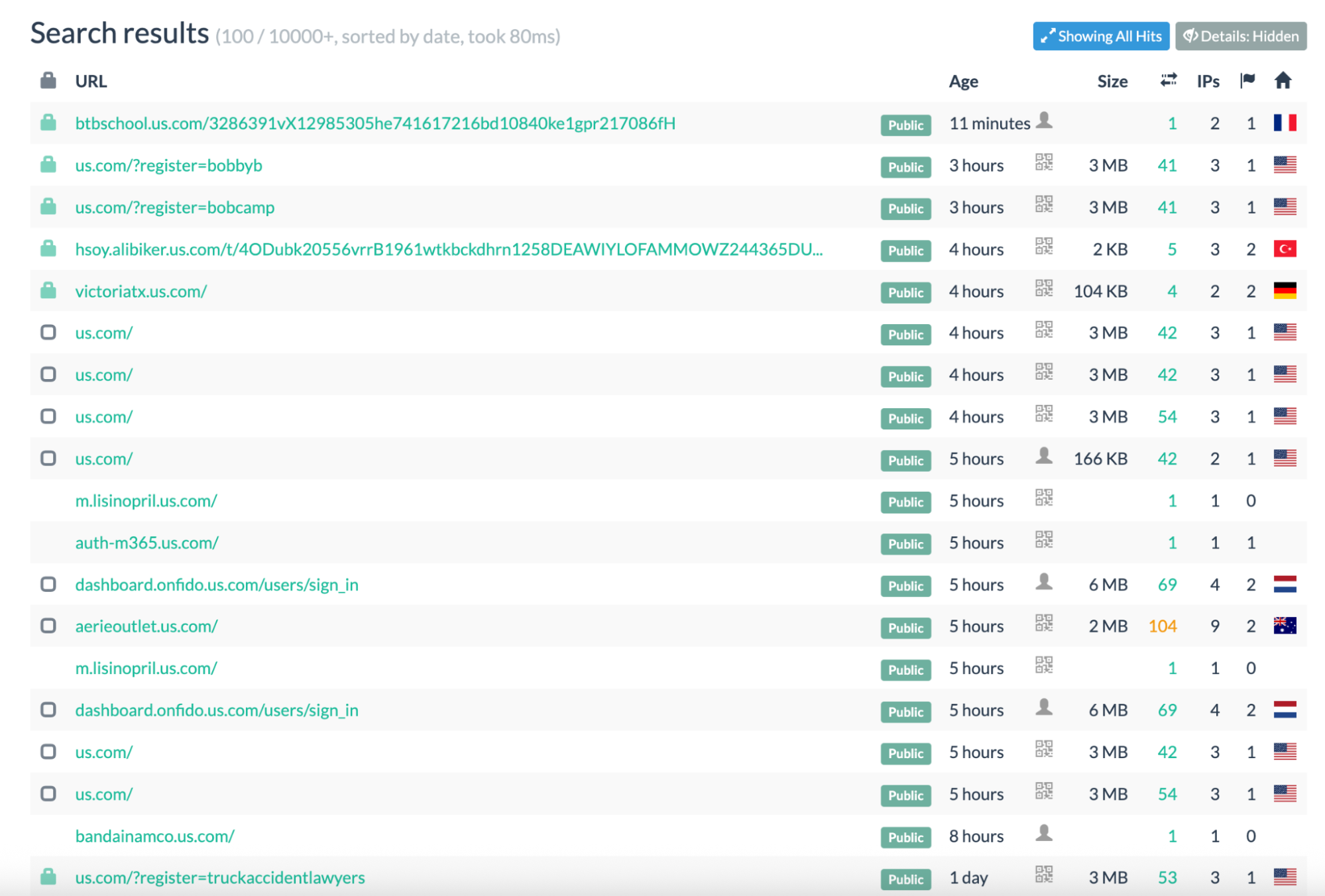
You can find additional information on urlscan here.
![urlscan entry for dashboard[.]onfido[.]us[.]com](https://images.ctfassets.net/y1cdw1ablpvd/6qZbv6gjlctB9vJ9eO4oca/ef26bbdfd01919f2422a77c73064d186/image2.png)
Isn’t Evilginx a red team tool?
Evilginx is nominally a red team tool, but we frequently spot it being used in phishing campaigns against our customers. Evilginx is a great choice for attackers looking to target non-standard web apps because it is capable of emulating a range of domains — it’s designed to be flexible and work for any page without generating a load of custom JavaScript that might stand out to security tools/analysts.
If you want to see an example of Evilginx being used to phish a user, check out the example below.
What can you do about it?
There’s not a huge amount of impartial advice to give here unfortunately. With malicious Google ads not going away anytime soon, response action is limited. If you are an Onfido user, be sure to block the URL and any related patterns (we noticed that after appearing to have been taken down initially, the site has reappeared at dashboard[.]onfido[.]us[.]com/users/sign_in and no longer appears to require the same URL path). However, it goes without saying that this is a temporary measure and the attacker will no doubt rotate the domain in the near future.
One good option is to encourage your users to bookmark their links rather than Google searching for the page. If you’re using an IdP with an application dashboard like Okta, Microsoft, or Google, this provides a convenient way to find all your apps in one place.
Bonus: How Push stopped the attack
Interested in how we stopped the attack?
When the user visited the page, Push detected Evilginx running on the page and blocked the user. Check it out.
Using our browser-based security platform, you can also see all users with an account on Onfido across your workforce. Using Push, you can:
Quickly identify which users have a password-based login set for their account (and therefore could be phished).
Identify users to enable them to be contacted about the attacks targeting Onfido.
Set an app banner for Onfido warning users of the attacks and guiding them to access and login to the app via your SSO solution.
We don’t just stop phishing attacks
It doesn’t stop there — Push provides comprehensive identity attack detection and response capabilities against techniques like credential stuffing, password spraying and session hijacking using stolen session tokens. You can also use Push to find and fix identity vulnerabilities across every app that your employees use like: ghost logins; SSO coverage gaps; MFA gaps; weak, breached and reused passwords; risky OAuth integrations; and more.
If you want to learn more about how Push helps you to detect and defeat advanced identity attack techniques in the browser, book some time with one of our team for a live demo.

