With our latest feature release, MFA enforcement, Push administrators can configure a control to prompt employees to enroll in MFA whenever Push detects that they’re not registered — even on apps that don’t natively provide any administrative enforcement option for MFA.
With our latest feature release, MFA enforcement, Push administrators can configure a control to prompt employees to enroll in MFA whenever Push detects that they’re not registered — even on apps that don’t natively provide any administrative enforcement option for MFA.
There are two things every security operations engineer can agree on:
Get MFA on every account on every app.
This is stupidly harder to achieve than it seems.
The penalties for failing to solve this hard simple problem are abundantly clear. Stolen credentials accounted for roughly half of the initial access methods observed this year across 30,000+ attacks, according to Verizon’s 2024 Data Breach Investigations Report. And in a review of 30 publicly disclosed breaches involving identity attacks in 2024, we found that 73% (almost three-quarters) were the result of compromised credentials, with the rest the result of phishing.
Three-quarters of publicly disclosed breaches involving identity attacks in 2024 involved compromised credentials and missing MFA.
In the case of the Snowflake incident earlier this year, a lack of MFA meant the difference between an enormous and murky firefight to clean up accounts breached with legitimate credentials, and a decent night’s sleep. The result was hundreds of millions of breached customer records, nine publicly named victims, and at least one ransom paid.
“Do you know how many accounts we have on this third-party service, who owns them, how many tenants, whether those creds are shared elsewhere, and their security posture?” is not a fun question to answer on a Friday.
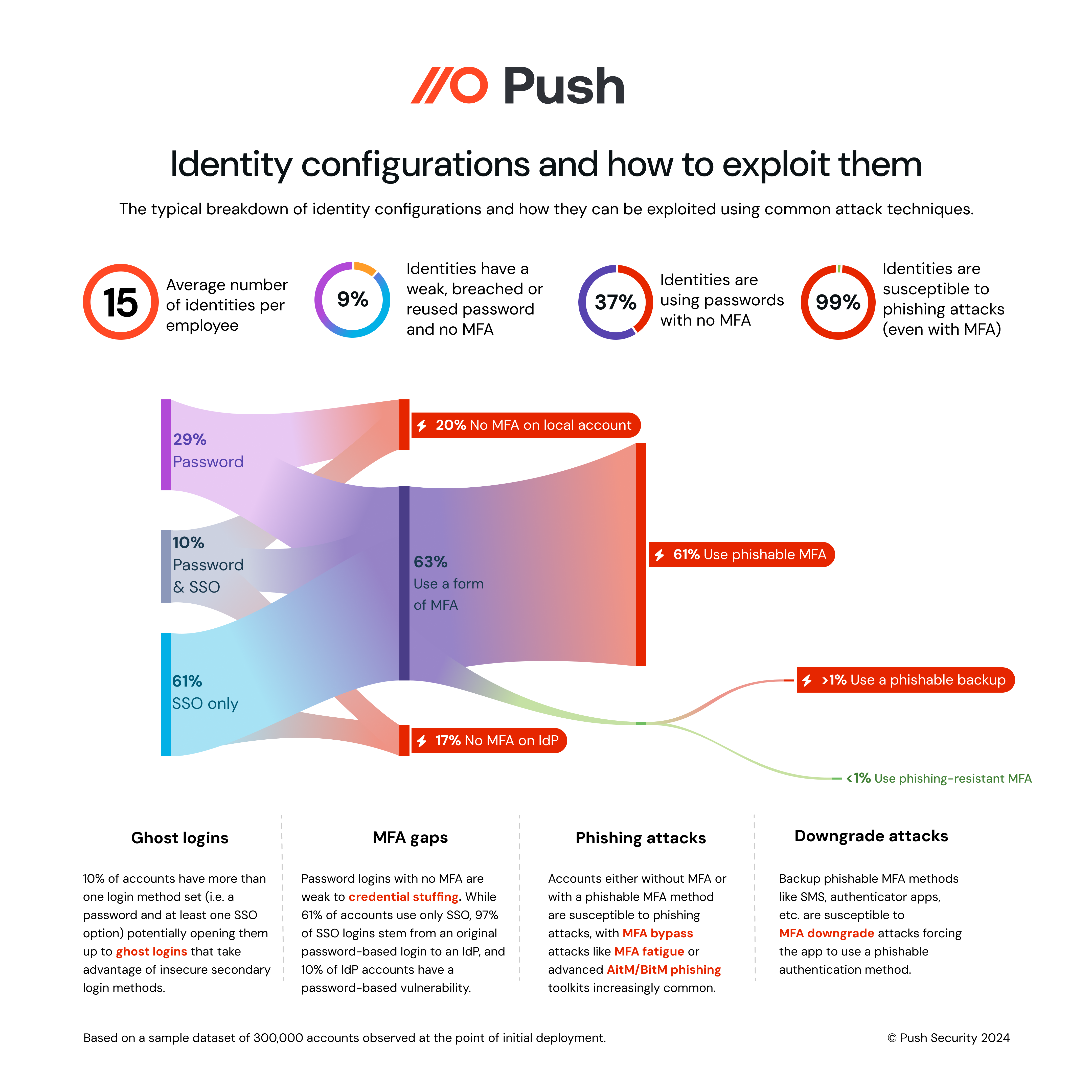
Typically, 37% of logins observed by Push upon initial deployment into a new customer environment do not use any form of MFA.
For SecOps teams we’ve helped here at Push that responded to incidents affecting third-party apps (like Snowflake), the first item on the recovery plan is to finally solve that hard simple problem: No more MFA gaps.
With our latest feature release, MFA enforcement, this is so much easier. With MFA enforcement, Push administrators can configure a control to prompt employees to enroll in MFA whenever Push detects that they’re not registered — even on apps that don’t natively provide any administrative enforcement option for MFA. This capability is made possible by the Push browser extension, which uses in-browser messaging and simple workflows to guide users right where they work.
In this article, we’ll cover how Push helps you identify and close MFA gaps, how our new enforcement feature is one part of that solution, and how you can test the platform yourself.
Shining a light on MFA gaps
There’s no question that the rise of ubiquitous multi-factor authentication has been an enormous advance for defenders in cybersecurity.
Yet several years into this journey, the problem of verifying and enforcing MFA coverage across an organization remains a bit of a puzzle box.
Why is this?
Complex overlapping (and occasionally contradictory) configurations for enterprise MFA solutions can result in entire employee groups not registered for MFA, and other critical missing pieces.
With a sprawling ecosystem of both SSO-managed and unmanaged self-adopted SaaS, MFA coverage ends up looking more like a patchwork than a unified layer of protection. Security teams lack visibility of freemium and self-purchased apps, and when signup is simple, many users will naturally skip MFA registration to remove a layer of friction. The end result is often a suite of core apps managed via SSO that enforce MFA — and a lot of other unmanaged apps that don’t (true nightmare fodder).
Another annoying piece of the puzzle box: Even in organizations with a high adoption rate of phishing-resistant MFA methods, having backup MFA methods (and a lack of total visibility into all of those registered methods) can create situations where MFA downgrade attacks are still possible. In MFA downgrade attacks, backup MFA methods that are less secure such as SMS or TOTP can be exploited, effectively bypassing more phishing-resistant methods.
The challenges of solving this puzzle are evident.
A recent review by Push Security researchers of a 300,000-account dataset found that 37% of accounts used a password and had no MFA. Meanwhile, 99% of the accounts with MFA used at least 1 phishable method.
To shine a light on MFA gaps, then, security teams need three things:
A full accounting of their identity attack surface, including accounts on unmanaged and freemium apps not on SSO.
A trustworthy out-of-band method for verifying MFA coverage, beyond the tangle of conditional access rules.
Visibility into which MFA methods are registered to a given account.
You can get all three with the Push platform. The missing piece we’ve now added is a way to automatically prompt employees to add MFA wherever it’s missing. Enter MFA enforcement.
How Push helps you ensure MFA coverage
Let’s take a look at a hypothetical incident response scenario to see how Push’s identity visibility and security controls help you ensure MFA coverage.
We’ll assume that prior to this incident, you had already deployed the Push browser extension, which you can install and enforce using any MDM solution, on all major browsers.
It’s a Friday afternoon (sorry).
News breaks that there’s been a suspected breach at a popular enterprise SaaS service.
You’re familiar with the service, but you don’t believe it’s a core managed app at your organization. Unfortunately, that does not mean you don’t have accounts (sorry again).
Using Push, you can:
Immediately check whether the Push extension has observed employee usage of the breached app. It will appear on the Apps table. From this overview, you can see how many accounts Push has seen on that app and how they are accessing it (SSO vs. other methods, such as local password login).
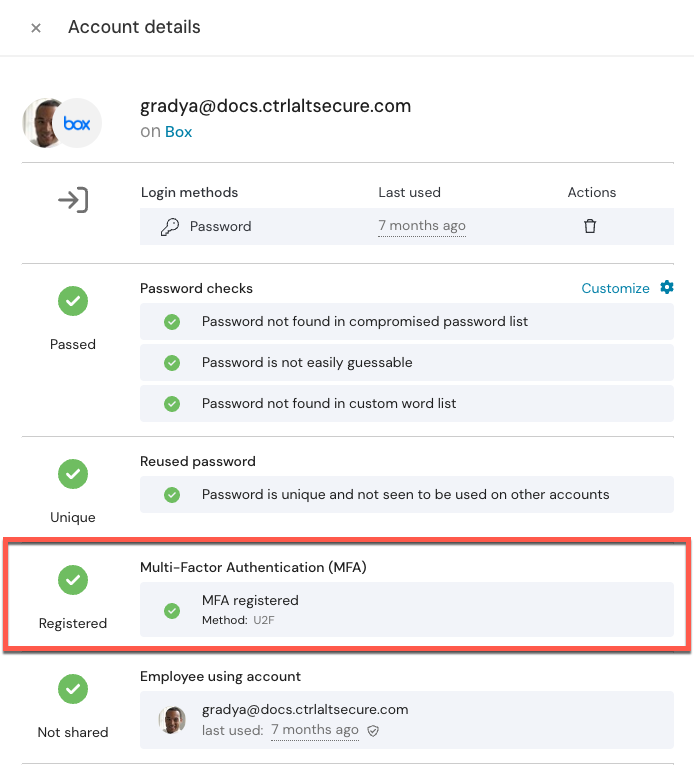
For those accounts on the breached app, you can quickly see whether they have MFA, and which methods are registered. To determine MFA status, the Push extension uses the existing user’s active session on an app to query that account’s MFA registration status using the app’s own API, providing a trustworthy verification.
You can also see whether the users’ passwords have any security issues, such as a verified stolen credential, or a password that’s weak or reused by filtering the Accounts list for Findings.
For accounts that lack MFA, you can then configure the MFA enforcement control from the Controls page. This will prompt employees who lack MFA to set it up whenever they next use the app. In parallel, you can reach out to affected employees through your preferred comms channel and ask them to immediately register for MFA and change their password on the app.
Then use Push’s webhooks to monitor for MFA registrations and password changes to roll in, by querying the Login event.
By combining visibility of your workforce identities — including granular context on their MFA registration status, MFA methods, and password security, even on unmanaged apps — with in-browser controls like MFA enforcement, Push helps security teams respond quickly and with assurance that they have the right information and tools to remediate the issue.
A closer look at MFA enforcement
With the in-browser MFA enforcement control, we chose this approach to close the loop on missing MFA issues because:
It meets users where they are, in the most relevant context where they can successfully address the issue.
It solves the problem of enforcing MFA on apps that are outside of administrative control — or that don’t provide any administrative controls to enforce MFA registration natively.
It’s tenant-agnostic. That means that you can enforce MFA for a given app on all tenants of that app, even those free-tier or test tenants that you don’t know about and have no control over.
As a happy side effect, your compliance team will thank you for finally allowing them to attest to where MFA is actually enforced — with verified results, visible at the account level in Push’s admin reporting — across your environment.
Here’s a closer look at how it works:
To enable MFA enforcement, use the configuration tile on the Controls page of the Push admin console and select which apps should require MFA registration. The control currently works with ~90 high-value apps, including Postman, Retool, Datadog, Atlassian, Okta, and others.
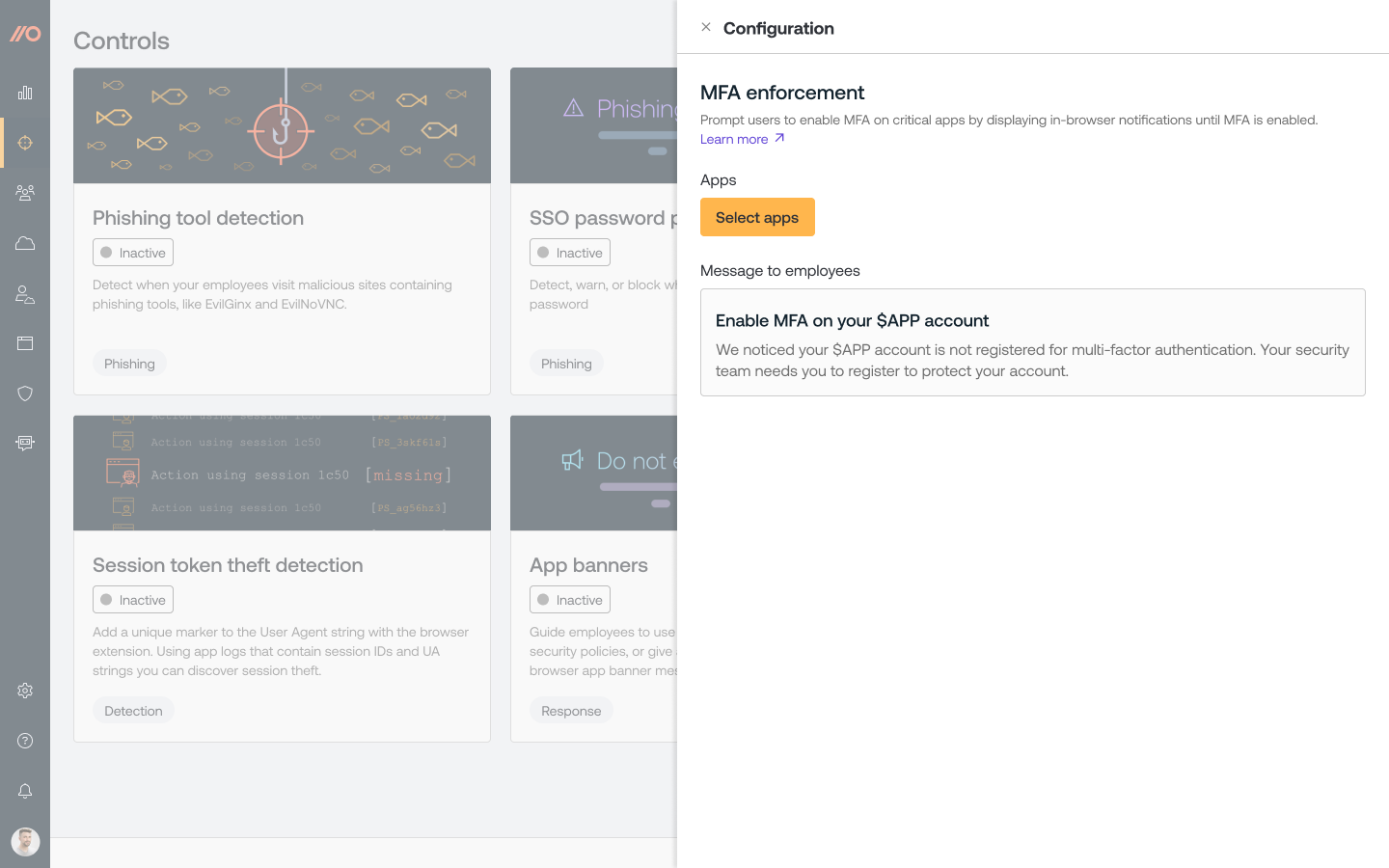
You can then customize the message the employees will see.
On the end-user side, employees will see a banner with your message as soon as they use an app where they lack MFA.
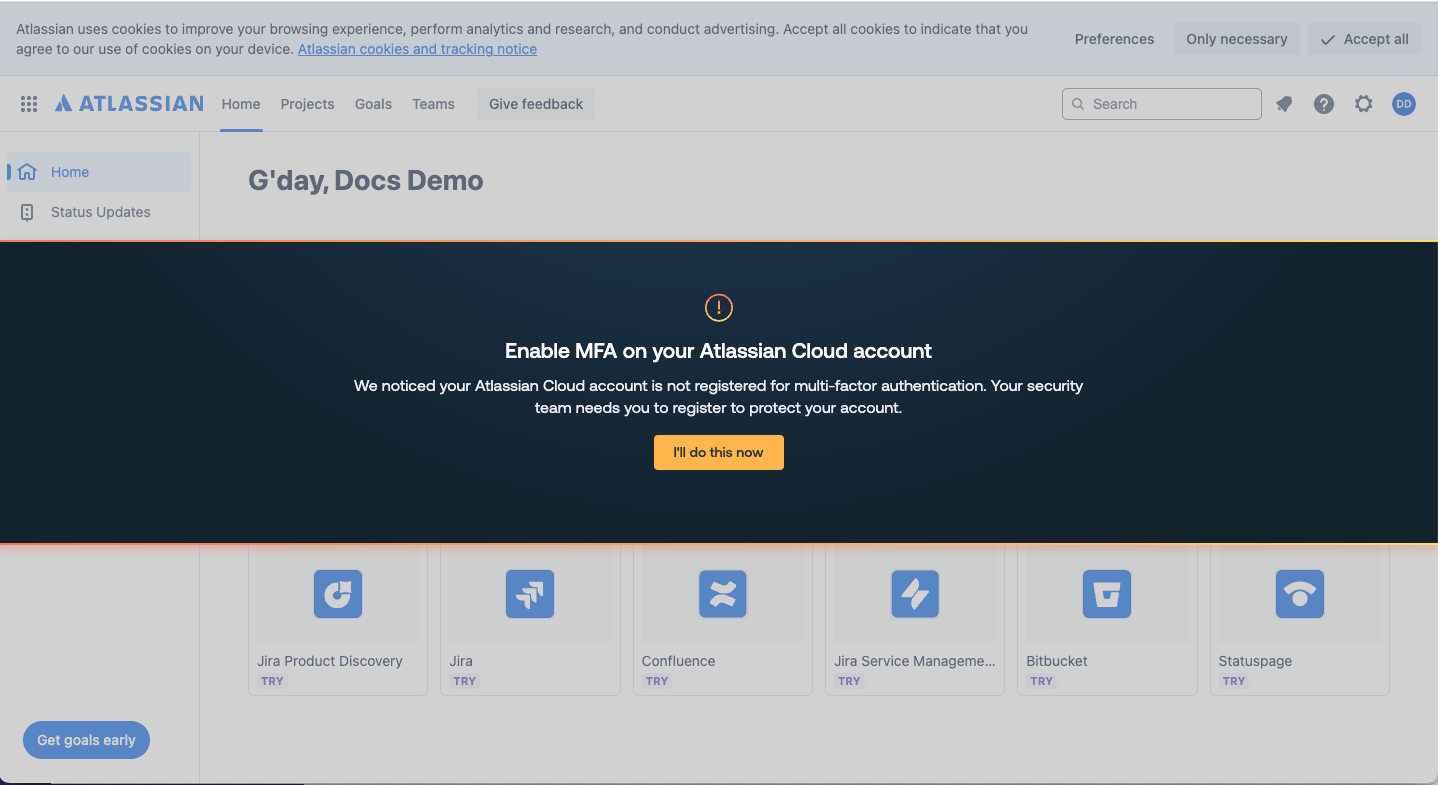
To complete MFA registration, the user can go directly to the app’s MFA registration page from a link in the banner (Push provides this link automatically, where one exists). The extension will query the user’s MFA status regularly in the background and when MFA registration is completed, the banner will disappear and the Push platform will clear the “No MFA” security finding for that account.
Find out more
To test our MFA visibility and control features, request a demo from our team. We look forward to helping you finally turn the challenge of MFA coverage into a simple problem, easily solved.

