We’re excited to announce our $4M seed round, led by Decibel. In this blog, we’re going to share why we started Push, our plans for the future, and how we’re building technology that allows organizations to allow employees to freely and securely adopt and use SaaS.
We’re excited to announce our $4M seed round, led by Decibel. In this blog, we’re going to share why we started Push, our plans for the future, and how we’re building technology that allows organizations to allow employees to freely and securely adopt and use SaaS.
Blocking SaaS isn’t working
tl;dr: The traditional way of just blocking apps that haven’t been vetted or approved by the security team isn’t working now and absolutely won’t scale as businesses now value flexibility as much as productivity and security. You don’t have to choose one anymore. Empower your employees to be productive and move fast, securely, and partner with them to secure SaaS.
It’s common for organizations to have hundreds of SaaS apps in use at all times and we expect that number to continue to rise. Most companies accept SaaS use because it helps employees be productive and get their work done, but each SaaS app does introduce risk to the company because they require access to business data, employees input data into each app, and the app becomes a part of your larger corporate attack surface.
Simply blocking SaaS use hasn’t worked to date and, as more and more apps are built, with more and more functionality employees need, blocking and restricting just can’t scale and will widen the divide between security and employees.
But to secure SaaS, security teams need visibility. There are some newer tools on the market built specifically to discover cloud and SaaS adoption (SaaS discovery and shadow IT discovery tools), but they tend to be focused exclusively on knowing what employees are using so that security and IT can enforce rules and controls on that SaaS use in order to keep company data out of the hands of the bad guys.
Instead of focusing on using that SaaS visibility to create and enforce new policies to restrict SaaS use, what if we could leverage SaaS visibility to help employees actually adopt and use SaaS how they want to?
We’re trying a different approach that puts more trust in employees’ desire and ability to keep themselves secure.
Introducing a user-centric approach to securing SaaS
The user-centric movement has been successfully adopted by industry leaders like Slack, Netflix, Github, Duo Security. For endpoint security, those user-centric approaches were spot on. They engaged employees to make decisions about their devices that would inform security teams about employee devices. We even developed our own user-centric solution for endpoint devices when working together at MWR (acquired by F-Secure).
When it comes to securing SaaS, working directly with users (employees) is not just a huge value add, it's essential. That's because the SaaS apps employees are using are giant unknowns - they’re not known entities or endpoints like employee devices - so you can't find out about or address security issues in SaaS apps without working with employees who are using those apps.
SaaS is owned by users, so needs to be secured by users
Scared yet? We get it, and we don’t expect you to relinquish all control of security and hand it off to employees. But stick with us for a second… There’s a stat making the rounds that suggests that more than two-thirds of SaaS is owned by employees. They’re self-adopting SaaS, integrating it with your business data, and using those tools to work faster, smarter, and generally be more productive. So, while it may not make sense to give up and just let employees continue doing what they’re doing with zero oversight, there’s a scalable way to meet in the middle.
We decided to focus on improving the security of SaaS use by equipping employees to help. If this approach lets employees freely adopt and use SaaS, then it’s a win for both employees and security teams.
Could user-centric security concepts be used to secure SaaS and cloud application usage - not just securing access to SaaS, but restricting excessive app permissions, removing unused cloud apps and shadow IT, and so on?
SaaS is user-powered. They’re adopting it and using it on their own already. Trying to secure SaaS by either completely restricting its use or only allowing employees access to a handful of corporate-sanctioned apps won’t scale. It would be naive to ignore the fact that SaaS introduces risk. Each app requests access to business data, employees have to integrate the apps into your systems and they’ll be inputting business data into the app. Which means that each app becomes a part of the attack surface security teams must protect.
The old way of dealing with this was just to block SaaS as soon as the security team discovers an app in use, or requiring administrator approval before integrating with other SaaS - keeping the security team in the role of the enforcer or blocker to employee SaaS use. Everyone hates that way - employees and security teams. But leaving SaaS adoption wide open is a security nightmare. So where do you start when it comes to securing SaaS use? With the owners of SaaS - the users.
You can’t secure SaaS without involving the user
To secure SaaS, you need to:
1) know what SaaS employees are using and how they’re using them
2) know what data the app has access to and what it requires
3) find out if security controls are missing and then chase employees to enable them improve
The most logical way to get this information is to talk to your employees directly, but that can’t scale. Let’s say you have 200 employees and each is using a dozen SaaS apps in their role. Are you going to go to each employee (through Slack or Teams, over the phone, via email?) and ask what they’re using, how they’re accessing it, what they’re using it for, if they’re still using it, who the admin is, and so on? Even if you could do that, would they even remember all the SaaS apps they’ve started trials with or what they’re using for free? What else would fall under your radar?
To satisfy the three SaaS security requirements we listed above, we’ve decided to focus our initial product efforts on SaaS discovery and getting business context from SaaS users (your employees) to ensure they’re using SaaS securely.
But knowing is just the start - what’s the point of getting visibility if you’re not using it to fix security issues or remove high-risk or dodgy apps?
Guide employees to fix security issues and use SaaS securely
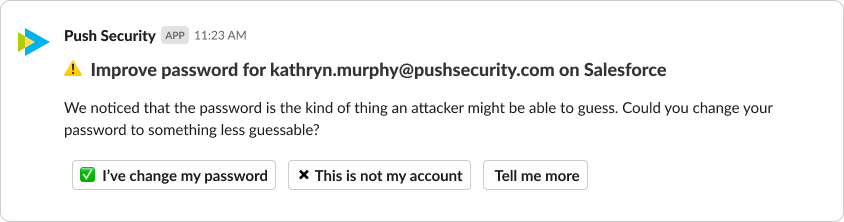
That’s where the user-centric approach to securing SaaS comes in. We believe employees want to do the right thing and don’t want to be the one responsible for a breach. As long as we make it as easy and quick as possible for them to help and to take action, they will.
To make this work at scale, we use ChatOps to engage directly with the employee, and a browser extension to prompt users and help them fix SaaS security issues. By helping them self-remediate issues, we offload the more mindless security hygiene work from security and IT, while enabling employees to use the SaaS tools they want.
We can also use this technology to get relevant business context about how they’re using each app and if they’re even still using it. If they say they aren’t using it anymore, we can help them remove it from your attack surface.
But I can’t trust employees to own security!
There’s an old trope in the security world that users are the weakest link. So, how can we expect “the weakest link” in a company to actually secure the company? We’d like to challenge that old adage and suggest that employees shouldn’t be expected to become security experts in order to secure a business. That’s not their job.
What employees can do really well is provide context for the security team and to self-remediate the more mundane security issues by using stronger passwords, enabling MFA for SaaS apps, and so on.
We believe the key to making the user-centric approach work is to give users clear, easy to follow instructions and asking them questions they can answer without Googling for more information. We ask questions to get useful context and then enrich SaaS usage data for admins so they can make decisions about what SaaS is appropriate for their business.
Making user-centric security work in the real world
Getting user-centric security to work well requires a near-perfect user experience - it must be quick and easy or they won’t engage with it. We need to understand employees, speak their language, empathize with them, respect their busy schedules, and help them when they’re ready to work with us. One truth remains: If employees aren’t responding to prompts, assume we’re the problem. We’ll be optimizing continuously based on employee engagement rate.
Users aren’t the problem, they’re part of the solution
Engaging users to self-remediate SaaS security issues just makes sense and it's by far the most scalable way to secure SaaS. Securing SaaS while balancing the needs of employees and security teams requires that we work together and share the responsibilities. To do this, we need to stop insisting that users are the problem and remember that attackers are the bad guys, not employees.
Follow us on social media and subscribe to our blog if you’re interested in hearing about what we’re learning from users along the way. We’d also love your feedback so we can keep improving!

