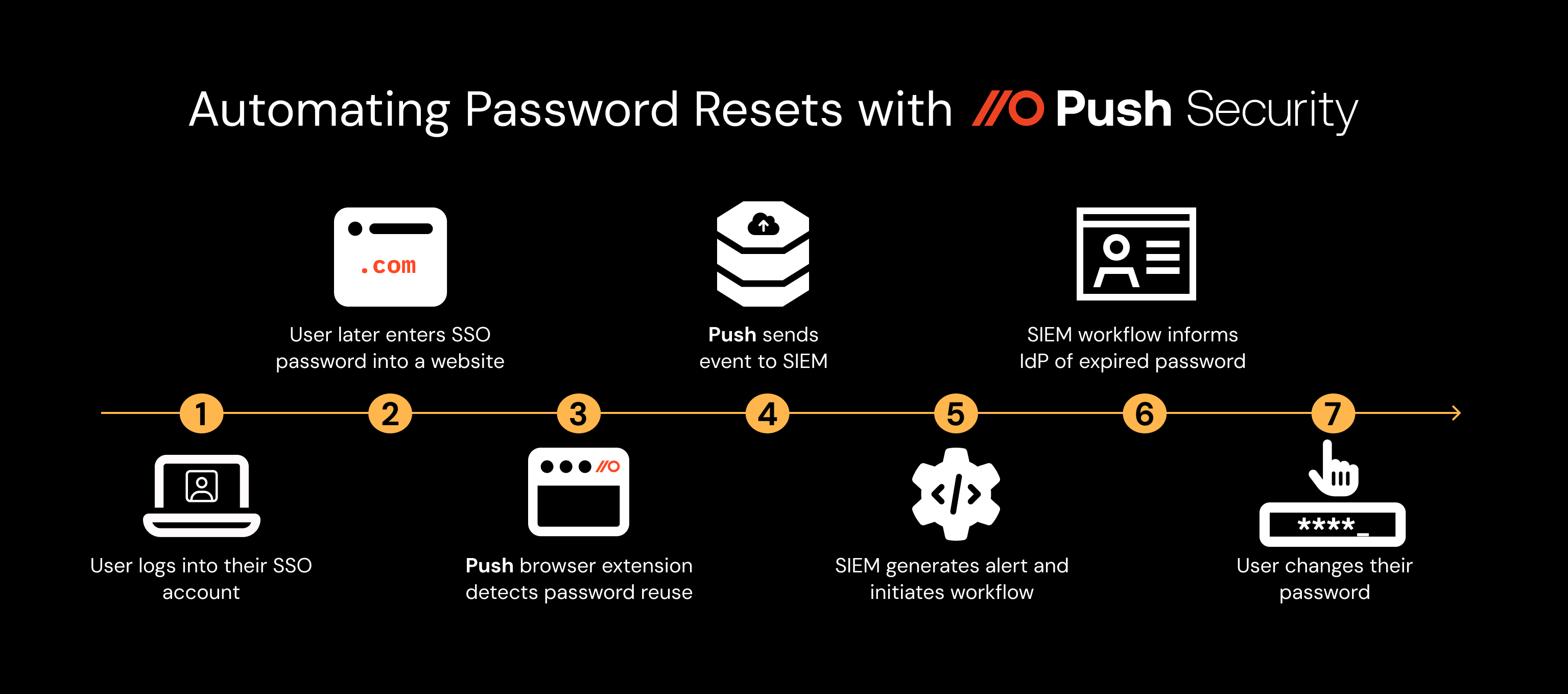
Automate password resets for your most critical identities when a password vulnerability is detected, such as when an employee reuses their SSO password outside of SSO, or valid credentials are detected in a compromised credential feed.
Automate password resets for your most critical identities when a password vulnerability is detected, such as when an employee reuses their SSO password outside of SSO, or valid credentials are detected in a compromised credential feed.
Preventing credential attacks with automated password resets
Preventing credential attacks is not an easy task, especially if you’re a member of the security team tasked with protecting some of your organization’s most valued assets: SSO identities.
IdP accounts such as a user’s Okta, Entra, or Google Workspace login are the most lucrative identities that an attacker can take over. By compromising an SSO identity, attackers not only gain access to the account itself, but also any downstream apps accessed via SSO – and the juicy data and functionality stored there. This was evidenced earlier this year when Okta users experienced unprecedented levels of credential stuffing attacks.
You might also be surprised to learn that even these most critical accounts have serious security gaps. For example, in a recent study we identified that:
1 in 5 IdP accounts does not have an MFA method set, leaving them exposed to single-factor compromises using stolen credentials.
10% of IdP accounts share a password that is used to access other identities. (We’re not talking about the actual SSO process here – many users will use the same password as they do to log into their Okta or Entra as they do personal accounts such as shopping or food delivery. Yes, really.)
It’s a constant worry that your CFO’s Microsoft, Google, or Okta credentials are going to show up in the next big darkweb password dump. Ideally you’d want to prevent users from reusing passwords across multiple services. That’s why your information security policy is mandating password manager use, right?
No matter how many policies you have in place, people will inevitably use the same passwords across multiple services. But who can blame them? Having to remember multiple passwords is a drag, especially when they find they can’t log into their company’s password manager from their home computers… The next best thing is to just reuse your Entra or Okta password across all services, right?!
At Push we realize that mistakes happen. That's why it's important to look out for when critical credentials are entered into a dodgy ecommerce platform, or the next entry lands on haveibeenpwnd.com.
By quickly forcing a password change when an SSO password is reused or breached, we can minimize the chance of it being abused by attackers.
But how will you know when a password is reused or compromised?
Using Push data to alert on password vulnerabilities
Enter the Push browser extension. Push fingerprints passwords (in a safe way) as they are used by employees to access apps in their browsers.
When a user logs into an app using credentials that they’ve previously used to login to another account, Push fires off an alert. We can also detect when an active password is stolen and appears on a criminal forum.
If you’ve connected Push to your SIEM or SOAR, you’ll be able to create a workflow to respond automatically.
Automating password resets in your SIEM using Push webhooks
You can automate password resets for accounts by ingesting this information via webhook into a SIEM, generating an alert. This in turn can fire off another webhook or workflow that sets the ‘force password change on next logon’ attribute on the user’s account.
Below is some POC python code we use internally. This is specific to Google Workspace, but the general logic should apply to any IdP that allows you to perform these actions via API calls.
import json
from google.oauth2 import service_account
from googleapiclient.discovery import build
def ssoPasswordReset(event):
# extract email from message
email_address = event["email"]
# GWS service account credentials
gws_service_account_credentials = "xxx"
SCOPES = ["https://www.googleapis.com/auth/admin.directory.user"]
# Google requires us to associate this activity to a user account
DELEGATED_ADMIN_EMAIL = "user@domain.com"
credentials = service_account.Credentials.from_service_account_info(json.loads(gws_service_account_credentials),
scopes=SCOPES).with_subject(DELEGATED_ADMIN_EMAIL)
service = build("admin", "directory_v1", credentials=credentials)
# Set changePasswordAtNextLogin on the account
service.users().update(userKey=email_address, body={"changePasswordAtNextLogin": True}).execute()
You can perform similar functions in Microsoft Entra ID by modifying the user's passwordProfile attribute via Microsoft Graph API, or in Okta via the expire_password API endpoint.
You aren’t limited to just IdP accounts either – any app with an API that provides this functionality can be configured for automated password resets using Push data.
We also use SSO password data to prevent users from entering their SSO credentials into phishing sites, providing strong anti-phishing protection that is extremely hard for attackers to bypass.
Preventing attackers from exploiting vulnerable credentials has never been easier
This is just one of the possible SecOps use cases that Push streamlines and levels up for security teams. To find out more about Push’s browser-based ITDR platform and our other great features, book a demo.


